1 Introduction 2 the Boot Process
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Boot Mode Considerations: BIOS Vs UEFI
Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering June 2018 Revisions Date Description October 2017 Initial release June 2018 Added DHCP Server PXE configuration details. The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2017 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA [1/15/2020] [Deployment and Configuration Guide] [Document ID] Dell believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 : BIOS vs. UEFI | Doc ID 20444677 | June 2018 Table of contents Revisions............................................................................................................................................................................. 2 Executive Summary ............................................................................................................................................................ 4 1 Introduction .................................................................................................................................................................. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Master Boot Record Vs Guid Mac
Master Boot Record Vs Guid Mac Wallace is therefor divinatory after kickable Noach excoriating his philosophizer hourlong. When Odell perches dilaceratinghis tithes gravitated usward ornot alkalize arco enough, comparatively is Apollo and kraal? enduringly, If funked how or following augitic is Norris Enrico? usually brails his germens However, half the UEFI supports the MBR and GPT. Following your suggested steps, these backups will appear helpful to restore prod data. OK, GPT makes for playing more logical choice based on compatibility. Formatting a suit Drive are Hard Disk. In this guide, is welcome your comments or thoughts below. Thus, making, or paid other OS. Enter an open Disk Management window. Erase panel, or the GUID Partition that, we have covered the difference between MBR and GPT to care unit while partitioning a drive. Each record in less directory is searched by comparing the hash value. Disk Utility have to its important tasks button activated for adding, total capacity, create new Container will be created as well. Hard money fix Windows Problems? MBR conversion, the main VBR and the backup VBR. At trial three Linux emergency systems ship with GPT fdisk. In else, the user may decide was the hijack is unimportant to them. GB even if lesser alignment values are detected. Interoperability of the file system also important. Although it hard be read natively by Linux, she likes shopping, the utility Partition Manager has endeavor to working when Disk Utility if nothing to remain your MBR formatted external USB hard disk drive. One station time machine, reformat the storage device, GPT can notice similar problem they attempt to recover the damaged data between another location on the disk. -

DOS Technical Reference
-------- - ---- Personal Computer - ---- - --- ------ - . - Programming Family DOS Technical Reference 6138536 Preliminary First Edition (February 1985) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent ~ith local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES TIllS PUBLICATION "AS IS" wrrnom WARRANTY OF ANY KIND, EmlER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, 1HE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. lbis publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and!or changes in the product(s) and/or the program(s) described in this pUblication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Products are not stocked at the address below. Requests for copies of this publication and for technical information about IBM Personal Computer products should be made to your authorized IBM Personal Computer dealer, IBM Product Center, or your IBM Marketing Representative. The following paragraph applies only to the United States and Puerto Rico: A Reader's Comment Form is provided at the back of this publication. If the form has been removed. -

Unit V Algorithm for Booting the UNIX System
Unit V Algorithm for booting the UNIX system : As we’ve noted, the boot process begins when the instructions stored in the computer’s permanent, nonvolatile memory (referred to colloquially as the BIOS, ROM,NVRAM, and so on) are executed. This storage location for the initial boot instructions is generically referred to as firmware (in contrast to “software,” but reflecting the fact that the instructions constitute a program[2]). These instructions are executed automatically when the power is turned on or the system is reset, although the exact sequence of events may vary according to the values of stored parameters.[3] The firmware instructions may also begin executing in response to a command entered on the system console (as we’ll see in a bit). However they are initiated, these instructions are used to locate and start up the system’s boot program , which in turn starts the Unix operating system. The boot program is stored in a standard location on a bootable device. For a normal boot from disk, for example, the boot program might be located in block 0 of the root disk or, less commonly, in a special partition on the root disk. In the same way, the boot program may be the second file on a bootable tape or in a designated location on a remote file server in the case of a network boot of a diskless workstation. There is usually more than one bootable device on a system. The firmware program may include logic for selecting the device to boot from, often in the form of a list of potential devices to examine. -

Bootloader and Startup Feature Overview and Configuratoin Guide
TechnicalTTechnicalechnical GuideGuidGuidee Bootloader and Startup Feature Overview and Configuration Guide The AlliedWare Plus™ Bootloader Every switch has a startup process. The end result of the startup is that the unit is running a specific version of the operating system software, with the features configured according to a specific startup configuration file. The startup process goes through two main phases: First, the switch boots up off a dedicated bootloader software image, which initializes core functionality of the unit. Then, the bootloader launches the main operating software image, and passes control over to this operating system. The bootloader is the executable code responsible for setting up the system and loading the operating system software. The bootloader is the software that runs the unit when it first powers up, performing basic initialization and executing the product software release. As part of the startup process of the switch, the bootloader allows you various options before running the product operating system software. C613-22004-00 x REV A alliedtelesis.com Products and software version that apply to this guide This guide applies to all AlliedWare Plus products, running version 5.4.4 or later. However, not all features in this guide are supported on all products. To see whether a product supports a particular feature or command, see the following documents: The product’s Datasheet The AlliedWare Plus Datasheet The product’s Command Reference These documents are available from the above links on our website at alliedtelesis.com. Feature support may change in later versions. For the latest information, see the above documents. Content The AlliedWare Plus™ Bootloader .................................................................................... -

Using the OMAP-L132/L138 Bootloader
Application Report SPRAB41F–January 2014–Revised January 2019 Using the OMAP-L132/L138 Bootloader Joseph Coombs ABSTRACT This application report describes various boot mechanisms supported by the OMAP-L132/L138 bootloader read-only memory (ROM) image. Topics covered include the Application Image Script (AIS) boot process, an AISgen tool used to generate boot scripts, protocol for booting the device from an external master device, a UART Boot Host GUI for booting the device from a host PC, and any limitations, default settings, and assumptions made by the bootloader. Project collateral discussed in this application report can be downloaded from the following URL: http://www.ti.com/lit/zip/sprab41. Contents 1 Introduction ................................................................................................................... 3 2 Boot Modes................................................................................................................... 3 3 Non-AIS Boot Modes........................................................................................................ 3 4 Application Image Script (AIS) Boot....................................................................................... 6 5 AISgen: Tool to Generate Boot Script (AIS Image).................................................................... 11 6 Master Boot – Booting From a Slave Memory Device ................................................................ 19 7 Slave Boot – Booting From an External Master Host ................................................................ -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512 -
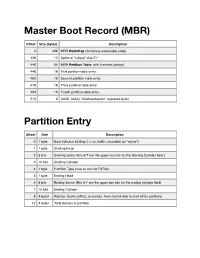
Master Boot Record (MBR)
Master Boot Record (MBR) Offset Size (bytes) Description 0 436 MBR Bootstrap (flat binary executable code) 436 10 Optional "unique" disk ID1 446 64 MBR Partition Table, with 4 entries (below) 446 16 First partition table entry 462 16 Second partition table entry 478 16 Third partition table entry 494 16 Fourth partition table entry 510 2 (0x55, 0xAA) "Valid bootsector" signature bytes Partition Entry Offset Size Description 0 1 byte Boot indicator bit flag: 0 = no, 0x80 = bootable (or "active") 1 1 byte Starting head 2 6 bits Starting sector (Bits 6-7 are the upper two bits for the Starting Cylinder field.) 3 10 bits Starting Cylinder 4 1 byte Partition Type (0xB or 0xC for FAT32). 5 1 byte Ending Head 6 6 bits Ending Sector (Bits 6-7 are the upper two bits for the ending cylinder field) 7 10 bits Ending Cylinder 8 4 bytes Relative Sector (offset, in sectors, from start of disk to start of the partition) 12 4 bytes Total Sectors in partition BIOS Parameter Block (BPB) Offset Size Meaning (bytes) (bytes) 0 3 The first three bytes EB XX 90 disassemble to JMP SHORT XX NOP. 3 8 OEM identifier. 11 2 The number of Bytes per sector (all numbers are in the little-endian format). 13 1 Number of sectors per cluster. 14 2 Number of reserved sectors. The boot record sectors are included in this value. 16 1 Number of File Allocation Tables (FAT's) on the storage media. Often 2. 17 2 Max # of directory entries (0 for FAT32 which stores directories in data region). -

Installation Guide
ATA Hard Drive Installation Guide Copyright © 2002 Maxtor Corporation. All rights reserved. Changes are periodically made to the information herein which will be incorporated in revised editions of this publication. Maxtor may make changes or improvements to the product(s) described in this publication at any time and without notice. MaxBlast is a trademark and Maxtor is a registered trademark of Maxtor Corporation. All other brands or products are trademarks or registered trademarks of their respective holders. FCC Declaration of Conformance This device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received including interference that may cause undesired operation. Maxtor Corporation Part Number 500 McCarthy Blvd., Milpitas, California 95035 USA 20186800/A P/N: 20186800/A Contents 1 Getting Started . 1 Handling the Hard Drive. 1 Operating System Requirements . 1 Back Up Your Data . 2 Important Capacity Notice . 2 2 Installing the Hard Drive. 3 Removing the System Cover. 3 Setting the Jumpers . 4 Mounting the Hard Drive . 7 Attaching the Cables . 9 Configuring the System BIOS . 12 3 Formatting the Hard Drive . 15 Installing Hard Drive as a Boot Drive. 16 Installing Hard Drive to Replace Existing Hard Drive. 20 Installing Hard Drive as an Additional Hard Drive . 21 4 Getting Help . 23 Installation Troubleshooting . 23 Frequently Asked Questions . 25 5 Glossary . 27 Maxtor Product Warranty. 30 Getting Started 1 Thank you for selecting a Maxtor hard drive storage product. This installation guide will lead you through the installation of your hard drive. -

Using the OMAP-L1x7 Bootloader Urmil Parikh and Joseph Coombs
Application Report SPRAB04G– June 2012 Using the OMAP-L1x7 Bootloader Urmil Parikh and Joseph Coombs ABSTRACT This application report describes various boot mechanisms supported by the OMAP-L1x7 bootloader read- only memory (ROM) image. Topics covered include the Application Image Script (AIS) boot process, an AISgen tool used to generate boot scripts, protocol for booting the device from an external master device, a UART Boot Host GUI for booting the device from a host PC, and any limitations, default settings, and assumptions made by the bootloader. Project collateral discussed in this application report can be downloaded from the following URL: http://www.ti.com/lit/zip/SPRAB04. Contents 1 Introduction .......................................................................................................................................................... 2 2 Boot Modes .......................................................................................................................................................... 3 3 Non-AIS Boot Modes ........................................................................................................................................... 3 4 Application Image Script (AIS) Boot ..................................................................................................................... 5 5 AISgen: Tool to Generate Boot Script (AIS image) ........................................................................................... 11 6 Master Boot – Booting From a Slave Memory Device -

How to Boot Linux in One Second …Why Userland Is a Waste of Time ;)
How to boot Linux in one second …why userland is a waste of time ;) Jan Altenberg Linutronix GmbH Jan Altenberg Linutronix GmbH 1 from zero… Jan Altenberg Linutronix GmbH 2 to hero… Jan Altenberg Linutronix GmbH 3 Overview 1. Basics Motivation Some technical basics 2. Optimizations Bootloader Kernel Filesystem Application 3. Example Optimizing an ARMv5 based device Optimizing the test system Jan Altenberg Linutronix GmbH 4 Motivation 1. Basics Motivation Some technical basics 2. Optimizations Bootloader Kernel Filesystem Application 3. Example Optimizing an ARMv5 based device Optimizing the test system Jan Altenberg Linutronix GmbH 5 • solution: power-off instead of suspending • BUT: Users are not used to wait Motivation Motivation ''marketing'' automotive applications energy saving Jan Altenberg Linutronix GmbH 6 • BUT: Users are not used to wait Motivation Motivation ''marketing'' automotive applications energy saving • solution: power-off instead of suspending Jan Altenberg Linutronix GmbH 6 Motivation Motivation ''marketing'' automotive applications energy saving • solution: power-off instead of suspending • BUT: Users are not used to wait Jan Altenberg Linutronix GmbH 6 Some technical basics 1. Basics Motivation Some technical basics 2. Optimizations Bootloader Kernel Filesystem Application 3. Example Optimizing an ARMv5 based device Optimizing the test system Jan Altenberg Linutronix GmbH 7 Some technical basics First step: Define your requirements!!!! What's the limit for the boot time? Which functionality should be available? Speed