Digital Security Locking System – Usb Based Gsm Security System
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Opera Mini Opera Mobile Shipments Pre-Installed in 4Q08: 7.3 Million
Opera Software Fourth quarter 2008 A note from our lawyers 2 This presentation contains and is, i.a., based on forward-looking statements. These statements involve known and unknown risks, uncertainties and other factors which may cause our actual results, performance or achievements to be materially different from any future results, performances or achievements expressed or implied by the forward-looking statements . Forward-looking statements may in some cases be identified by terminology such as “may”, “will”, “could”, “should”, “expect”, “plan”, “intend”, “anticipate”, “believe”, “estimate”, “predict”, “pp,gpgyotential” or “continue”, the negative of such terms or other comparable terminology. These statements are only predictions. Actual events or results may differ materially, and a number of factors may cause our actual results to differ materially from any such statement. Although we believe that the expectations and assumptions reflected in the statements are reasonable, we cannot guarantee future results, levels of activity, performance or achievement. Opera Software ASA makes no representation or warranty (express or implied) as to the correctness or completeness of the presentation, and neither Opera Software ASA nor any of its direc tors or emp loyees assumes any lia bility resu lting from use. Excep t as requ ire d by law, we undertake no obligation to update publicly any forward-looking statements for any reason after the date of this presentation to conform these statements to actual results or to changes in our expectations. You are advised, however, to consult any further public disclosures made by us, su ch as filings made w ith the OSE or press releases . -

Cell Phones and Pdas
eCycle Group - Check Prices Page 1 of 19 Track Your Shipment *** Introductory Print Cartridge Version Not Accepted February 4, 2010, 2:18 pm Print Check List *** We pay .10 cents for all cell phones NOT on the list *** To receive the most for your phones, they must include the battery and back cover. Model Price Apple Apple iPhone (16GB) $50.00 Apple iPhone (16GB) 3G $75.00 Apple iPhone (32GB) 3G $75.00 Apple iPhone (4GB) $20.00 Apple iPhone (8GB) $40.00 Apple iPhone (8GB) 3G $75.00 Audiovox Audiovox CDM-8930 $2.00 Audiovox PPC-6600KIT $1.00 Audiovox PPC-6601 $1.00 Audiovox PPC-6601KIT $1.00 Audiovox PPC-6700 $2.00 Audiovox PPC-XV6700 $5.00 Audiovox SMT-5500 $1.00 Audiovox SMT-5600 $1.00 Audiovox XV-6600WOC $2.00 Audiovox XV-6700 $3.00 Blackberry Blackberry 5790 $1.00 Blackberry 7100G $1.00 Blackberry 7100T $1.00 Blackberry 7105T $1.00 Blackberry 7130C $2.00 http://www.ecyclegroup.com/checkprices.php?content=cell 2/4/2010 eCycle Group - Check Prices Page 2 of 19 Search for Pricing Blackberry 7130G $2.50 Blackberry 7290 $3.00 Blackberry 8100 $19.00 Blackberry 8110 $18.00 Blackberry 8120 $19.00 Blackberry 8130 $2.50 Blackberry 8130C $6.00 Blackberry 8220 $22.00 Blackberry 8230 $15.00 Blackberry 8300 $23.00 Blackberry 8310 $23.00 Blackberry 8320 $28.00 Blackberry 8330 $5.00 Blackberry 8350 $20.00 Blackberry 8350i $45.00 Blackberry 8520 $35.00 Blackberry 8700C $6.50 Blackberry 8700G $8.50 Blackberry 8700R $7.50 Blackberry 8700V $6.00 Blackberry 8703 $1.00 Blackberry 8703E $1.50 Blackberry 8705G $1.00 Blackberry 8707G $5.00 Blackberry 8707V -

Mobile Connection Explorer for Windows Introduction and Features
Mobile Connection Explorer 15 May 2013 for Windows Version 21 Introduction and Features Public version Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic Gemfor s.r.o. Tyršovo nám. 600 252 63 Roztoky Czech Republic e-mail: [email protected] Contents Contents ...................................................................................................................... 2 History ......................................................................................................................... 3 1. Scope ..................................................................................................................... 3 2. Abbreviations ......................................................................................................... 4 3. Solution .................................................................................................................. 5 4. Specification ........................................................................................................... 5 5. Product description ................................................................................................. 9 5.1 Supported operating systems ....................................................................... 9 5.2 Hardware device connections ....................................................................... 9 5.3 Network connection types ............................................................................. 9 5.4 Customizable graphical skin ...................................................................... -

PDF 文件使用"Pdffactory Pro" 试用版本创建
X≤4.0" 4.0"<X≤4.5" 4.5"<X≤5.0" Mobile telephone nokia 3250 nokia E90(双膜) nokia N-GAGE QD nokia 6600F(双膜) nokia Lumia 710 nokia 2100 nokia N9 nokia X7 nokia 6370 nokia N97/N97i nokia 801T nokia 1110 nokia N97(摄像头) nokia Lumia 610 nokia 3310 nokia E7 nokia 3120 nokia N900 samsung i8150 Galaxy W nokia 1100 nokia 603 samsung M920 Transform nokia 6610 nokia N93i(双膜) samsung S5830 Galaxy Ace/I579/I589 nokia 6020/6030 samsung W589(双膜) nokia 3100 samsung S5250/S5253/Wave 525 samsung Wave M S7250/Wave 725/S7250D nokia 6230 samsung B7620U samsung I897 Captivate/I9088/I9010 nokia 6230i samsung S5330/S5333/wave 533/Wavesamsung 2 Pro T959 Vibrant/Galaxy S 4G/i9000 nokia 3220 samsung F708/F700 samsung S5690 Galaxy Xcover nokia 5500 samsung S5750e/S5753/wave 575 samsung I9000 Galaxy S/M110S/I9008/I9001 nokia 5070 samsung S5360/Galaxy Y/I509 samsung S8600 Wave 3/Wave III nokia 2630 samsung F508/F500(双膜) samsung W699(双膜) nokia 6060 samsung i8000 Omnia 2 samsung B7732(双膜) nokia 5030XR samsung i7680 samsung G400(三片) nokia 6151 samsung S8530 Wave II samsung I9020/I9023/Google Nexus S nokia 1112 samsung S5660 Galaxy Gio/I569samsung I8700 Omnia 7 nokia 7360 samsung S5380 Wave Y samsung I909 Galaxy S(跟I9000不同) nokia 1200 samsung R910 Galaxy Indulge 4G/samsung Epic 4G/Galaxy S Pro nokia 1600 samsung i8180c samsung i8350 Omnia W nokia C3-01/C3 Touchsamsung and Type S5820 samsung S7500 Galaxy Ace Plus nokia 6070 samsung R810 Finesse samsung i8160 Galaxy Ace 2 nokia 7250 samsung S5368 samsung i619 Galaxy Ace Dear nokia E50 Samsung S6102 Galaxy Y Duos samsung B9062 -

Devices for Which We Currently Recommend Opera Mini 7.0 Number of Device Models
Devices for which we currently recommend Opera Mini 7.0 Number of device models: 625 Platforms included: JME, BlackBerry, Android, S60 and iOS List generated date: 2012-05-30 -------------------------------------------------------------------------------------------------------------------------------------- au by KDDI IS03 by Sharp BlackBerry 9900 Bold Acer beTouch E110 au by KDDI REGZA Phone BlackBerry Curve 3G 9300 IS04 by Fujitsu-Toshiba Acer beTouch E130 Dell Aero au by KDDI Sirius IS06 by Acer Iconia Tab A500 Pantech Dell Streak Acer Liquid E Ezze S1 Beyond B818 Acer Liquid mt Fly MC160 BlackBerry 8520 Curve Acer Liquid S100 Garmin-Asus nüvifone A10 BlackBerry 8530 Curve Acer Stream Google Android Dev Phone BlackBerry 8800 1 G1 Alcatel One Touch OT-890D BlackBerry 8820 Google Nexus One Alfatel H200 BlackBerry 8830 Google Nexus S i9023 Amoi WP-S1 Skypephone BlackBerry 8900 Curve HTC A6277 Apple iPad BlackBerry 9000 Bold HTC Aria A6366 Apple iPhone BlackBerry 9105 Pearl HTC ChaCha / Status / Apple iPhone 3G BlackBerry 9300 Curve A810e Apple iPhone 3GS BlackBerry 9500 Storm HTC Desire Apple iPhone 4 BlackBerry 9530 Storm HTC Desire HD Apple iPod Touch BlackBerry 9550 Storm2 HTC Desire S Archos 101 Internet Tablet BlackBerry 9630 Tour HTC Desire Z Archos 32 Internet Tablet BlackBerry 9700 Bold HTC Dream Archos 70 Internet Tablet BlackBerry 9800 Torch HTC Droid Eris Asus EeePad Transformer BlackBerry 9860 Torch HTC Droid Incredible TF101 ADR6300 HTC EVO 3D X515 INQ INQ1 LG GU230 HTC EVO 4G Karbonn K25 LG GW300 Etna 2 / Gossip HTC Explorer -
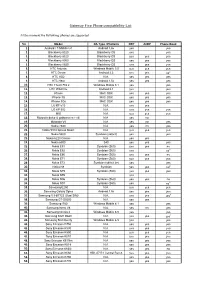
Gateway Five Phone Compatibility List
Gateway Five Phone compatibility List At the moment the following phones are supported No. Model OS Type / Platform HFP A2DP Phone Book 1. Android / T-Mobile G1 Android 1.6v yes yes 2. Blackberry 8320 Blackberry OS yes yes 3. Blackberry 8520 Blackberry OS yes yes yes 4. Blackberry 8900 Blackberry OS yes yes yes 5. Blackberry 8920 Blackberry OS yes yes yes 6. HTC Artemis Windows Mobile 5.0 yes yes yes 7. HTC Desire Android 2.2 yes yes no 2 8. HTC HD2 N.A. yes yes yes 9. HTC Hero Android 1.5v yes yes yes 10. HTC Touch Pro 2 Windows Mobile 6.1 yes yes 11. HTC Wild Fire Android 2.1 yes yes 12. iPhone MAC OSX yes yes yes 13. iPhone 3G MAC OSX yes yes yes 14. iPhone 3Gs MAC OSX yes yes yes 15. LG KF 510 N.A. yes yes 16. LG KP 502 N.A. yes yes yes 17. MIO N.A. yes yes yes 18. Motorola dolce & gabbana razr v3i N.A. yes no 19. Motorola V8 N.A. yes no yes 20. Nokia 2630 N.A. yes no yes 21. Nokia 5310 Xpress Music N.A. yes yes yes 22. Nokia 5800 Symbian (s60v3) yes yes 23. Nokia 6220 Classic N.A. yes yes 24. Nokia 6300 S40 yes yes yes 25. Nokia E51 Symbian (S60) yes yes no 26. Nokia E52 Symbian (S60) yes no 2 27. Nokia E66 Symbian (S60) yes yes no 28. Nokia E71 Symbian (S60) yes yes yes 29. Nokia E72 Symbian (s60v3 2e) yes yes 30. -
Gateway 5 Phone Compatibility
Gateway Five Phone compatibility List At the moment the following phones are supported No. Model OS Type / Platform HFP A2DP 1. Android / T-Mobile G1 Android 1.6v yes 2. Blackberry 8320 Blackberry OS yes 3. Blackberry 8520 Blackberry OS yes yes 4. Blackberry 8900 Blackberry OS yes yes 5. Blackberry 8920 Blackberry OS yes yes 6. HTC Artemis Windows Mobile 5.0 yes yes 7. HTC Desire Android 2.2 yes yes 8. HTC Desire HD Android 2.2 yes yes 9. HTC HD2 N.A. yes yes 10. HTC Hero Android 1.5v yes yes 11. HTC Touch Pro 2 Windows Mobile 6.1 yes 12. HTC Wild Fire Android 2.1 yes 13. iPhone MAC OSX yes yes 14. iPhone 3G MAC OSX yes yes 15. iPhone 3Gs MAC OSX yes yes 16. LG KF 510 N.A. yes yes 17. LG KP 502 N.A. yes yes 18. MIO N.A. yes yes 19. Motorola dolce & gabbana razr v3i N.A. yes no 20. Motorola V8 N.A. yes no 21. Nokia 2630 N.A. yes no 22. Nokia 5310 Xpress Music N.A. yes yes 23. Nokia 5800 Symbian (s60v3) yes 24. Nokia 6220 Classic N.A. yes yes 25. Nokia 6300 S40 yes yes 26. Nokia E51 Symbian (S60) yes yes 27. Nokia E52 Symbian (S60) yes 28. Nokia E66 Symbian (S60) yes yes 29. Nokia E71 Symbian (S60) yes yes 30. Nokia E72 Symbian (s60v3 2e) yes 31. Nokia N8 Symbian yes yes 32. Nokia N79 Symbian (S60) yes yes 33. Nokia N95 yes 34. -

Sony Ericsson 770I Manual
Sony Ericsson 770i Manual Manuals and user guide free PDF downloads for Sony Ericsson K770. Get Sony Ericsson K770 manuals and user guides sony ericsson k770i on off ways. Simple Unlocking Instructions for Sony Ericsson K770i mobiles. Unlock your Sony Ericsson today and never be tied to a network again ! Manuals and user guide free PDF downloads for Sony Ericsson K770i. Sony Ericsson C902 Swift Black (UMTS 5MP Cybershot VideoteleSony Ericsson W995 Handy Sony Ericsson - Li-Ion Battery for C510i, C902, C905, K770i. Sony Ericsson K770i manual table of contents: Sony Ericsson K770i / User Guide - Page 1. Congratulations on your purchase of the Sony Ericsson K770i. How to Hard Reset Sony Ericsson K770 Master Reset Power on the phone. Go to Main Menu Follow the on screen instructions. sony-ericsson-k770i-1.jpg. Sony Ericsson 770i Manual Read/Download Congratulations on your purchase of the Sony Ericsson K770i. Note This User Manual gives navigation instructions according to sprint lg rumor phone manual. Once you receive our 16 digit Sony Ericsson Unlock code (NCK code) and easy to follow instructions, your Sony Ericsson phone will be unlocked within 5. Manuals and user guide free PDF downloads for Sony Ericsson W705a. W705a-related questions: K770i Power Switch Ways sony ericsson k770i on off ways. Sony Ericsson Cell Phone Owner s Manual. W700i, W710i, W890i, P990i, K310i, K500i, K810i, T650i, W610i, K600i, T630, K300i, K800i, K770i, W850i, P900. Are you looking for amazing deals on new and used Sony Ericsson mobile phones? Find a great selection of Sony Ericsson mobiles for sale on ikman.lk. -

Gateway Five Phone Compatibility List
Gateway Five Phone compatibility List At the moment the following phones are supported No. Model OS Type / Platform HFP A2DP Phone Book 1. Android / T-Mobile G1 Android 1.6v yes yes 2. Blackberry 8520 Blackberry OS yes yes yes 3. Blackberry 8900 Blackberry OS yes yes yes 4. Blackberry 8920 Blackberry OS yes yes yes 5. iPhone MAC OSX yes yes yes 6. iPhone 3G MAC OSX yes yes yes 7. iPhone 3Gs MAC OSX yes yes yes 8. HTC Artemis Windows Mobile 5.0 yes yes yes 9. HTC Hero Android 1.5v yes yes yes 10. HTC Touch Pro 2 Windows Mobile 6.1 yes yes 11. LG KP 502 N.A. yes yes yes 12. MIO N.A. yes yes yes 13. Motorola V8 N.A. yes no yes 14. Nokia 6300 S40 yes yes yes 15. Nokia E51 Symbian (S60) yes yes no 16. Nokia E66 Symbian (S60) yes yes no 17. Nokia N79 Symbian (S60) yes yes yes 18. Nokia N96 Symbian (S60) yes yes no 19. Samsung E250 N.A. yes yes yes 20. Samsung Galaxy Spica Android 1.5v yes yes yes 21. Samsung i780 Windows Mobile 6.1 yes yes 22. Samsung Innov V8 N.A. yes no yes 23. Sony Ericsson D750 N.A. yes yes yes 24. Sony Ericsson K530 N.A. yes yes yes 25. Sony Ericsson K550 N.A. yes yes yes 26. Sony Ericsson K660 HB1-07 R1 Central Rev A yes yes yes 27. Sony Ericsson K610 N.A. yes yes yes 28. Sony Ericsson K618 N.A. -

Sony Ericsson V630i Manual Download Sony Ericsson V630i Manual
Sony Ericsson V630i Manual Download Sony Ericsson V630i Manual Sony Ericsson UMTS 2100 GSM 900-1800-1900 Tuto příručku vydala společnost Sony Ericsson Mobile Communications AB bez jakØkoli zÆruky. Zlepıení a změny tØto uživatelskØ příručky z důvodu tiskových chyb, nepřesností v aktuÆlních informacích nebo zdokonalení program ů a vybavení mohou být zpracovÆny pouze společností Looking for other manual? Document preview. No preview item for this file. SONY-ERICSSON K610I V630I SONY-ERICSSON K660I SM SONY-ERICSSON K770 PARTS SCH Sony Ericsson V630i. Expected June 2006 28th May 2006 Discuss this phone in our forum. The Sony Ericsson V630i is a lightweight 3G phone baded on the Sony Ericsson K610i handset. It comes with a 176x220 pixel display, 2 megapixel digital camera and expandable memory (using Memory Stick Micro cards) but weighs just 91 grams. Sony Ericsson Aspen: Sony Ericsson T270i: Sony Ericsson K530i: Sony Ericsson J120: Sony Ericsson G900: Sony Ericsson W610: Sony Ericsson P1i: Sony Ericsson Z520i: Sony Ericsson Xperia X10 Mini: Sony Ericsson Z530i Sony Ericsson V630 Price. The Sony Ericsson V630i is a 3G music phone. The Sony Ericsson K630i, this is a lightweight 3G phone with a high specification. Vodafone have added some additional music features such as Vodafone RadioDJ. The handset is neat, small & slim which measures 102 x 45.7 x 16.9mm. Forums download sony ericsson v630i manual, sony ericsson v630i manual free download, sony ericsson v630i manual er Western Connecticut U-Pick Farms and Orchards, sorted by county The latest version of sK1 is 0. They acquire network administrator capabilities and even take control of the network. -

Gateway 500S BT Phone Compatibility List
Gateway 500S BT Phone compatibility List At the moment the following phones were tested No. Model OS Type / Platform HFP A2DP Phone Book 1. Android / T-Mobile G1 Android 1.6v yes yes 2. Blackberry 8320 Blackberry OS yes yes 3. Blackberry 8520 Blackberry OS yes yes yes 4. Blackberry 8900 Blackberry OS yes yes yes 5. Blackberry 8920 Blackberry OS yes yes yes 6. Blackberry 9860 Qwertz Blackberry OS yes yes no 7. HTC 7 Trophy Windows Phone 7 yes yes 4 8. HTC 8x Windows Phone 8 yes yes yes 9. HTC 8S Windows Phone 8 yes yes yes 10. HTC Artemis Windows Mobile 5.0 yes yes yes 11. HTC Desire Android 2.2 yes yes no 2 12. HTC Desire HD Android 2.2 yes yes yes 13. HTC HD2 N.A. yes yes yes 14. HTC Hero Android 1.5v yes yes yes 15. HTC Touch Pro 2 Windows Mobile 6.1 yes yes 16. HTC Wild Fire Android 2.1 yes yes 17. Huawei u8815 Android 2.3.6 yes yes yes 18. iPhone MAC OSX yes yes yes 19. iPhone 3G MAC OSX yes yes yes 20. iPhone 3GS MAC OSX yes yes yes 21. iPhone 4G MAC OSX yes yes yes 22. iPhone 4GS MAC OSX yes yes yes 23. iPhone 5 MAC OSX yes yes yes 24. LG KF 510 N.A. yes yes 25. LG KP 502 N.A. yes yes yes 26. LG Optimus 3D[LG-P920] Android 2.2.2 yes yes 4 27. LG E900 Windows Phone 7 yes yes 4 28. -

Lorem Ipsum Dolor Sit Amet, Consetetur Sadipscing Elitr, Sed
Tabla de Modelos por Gamas GAMA IMPORTE MARCA MODELO GAMA A 35€ + IVA ALCATEL ALCATEL 311 GAMA A 35€ + IVA ALCATEL ALCATEL 331 GAMA A 35€ + IVA ALCATEL ALCATEL 332 GAMA A 35€ + IVA ALCATEL ALCATEL 363 GAMA A 35€ + IVA ALCATEL ALCATEL 511 GAMA A 35€ + IVA ALCATEL ALCATEL 525 GPRS GAMA A 35€ + IVA ALCATEL ALCATEL 535 GAMA A 35€ + IVA ALCATEL ALCATEL 556 GAMA A 35€ + IVA ALCATEL ALCATEL BIC PHONE GAMA A 35€ + IVA ALCATEL ALCATEL C550 GAMA A 35€ + IVA ALCATEL ALCATEL C630 GAMA A 35€ + IVA ALCATEL ALCATEL E205 GAMA A 35€ + IVA ALCATEL ALCATEL E207 GAMA A 35€ + IVA ALCATEL ALCATEL E221 GAMA A 35€ + IVA ALCATEL ALCATEL E256 GAMA A 35€ + IVA ALCATEL ALCATEL E259 GAMA A 35€ + IVA ALCATEL ALCATEL E265 GAMA A 35€ + IVA ALCATEL ALCATEL E801 GAMA A 35€ + IVA ALCATEL ALCATEL EASY DUAL GAMA A 35€ + IVA ALCATEL ALCATEL MANDARINA DUCK GAMA A 35€ + IVA ALCATEL ALCATEL OT C701 GAMA A 35€ + IVA ALCATEL ALCATEL OT S-218 GAMA A 35€ + IVA ALCATEL ALCATEL S211 GAMA A 35€ + IVA ALCATEL ALCATEL S320 GAMA A 35€ + IVA HUAWEI HUAWEI E160E GAMA A 35€ + IVA HUAWEI HUAWEI E170 MODEM USB HSUPA GAMA A 35€ + IVA HUAWEI HUAWEI MODEM E270 GAMA A 35€ + IVA HUAWEI HUAWEI MODEM USB E-220 UMTS GAMA A 35€ + IVA LG LG 1300 GAMA A 35€ + IVA LG LG 3000 GAMA A 35€ + IVA LG LG B1200 GAMA A 35€ + IVA LG LG C3100 GAMA A 35€ + IVA LG LG F2300 GAMA A 35€ + IVA LG LG KF310 GAMA A 35€ + IVA LG LG KG120 GAMA A 35€ + IVA LG LG KG220 GAMA A 35€ + IVA LG LG KG240 GAMA A 35€ + IVA LG LG KG275 GAMA A 35€ + IVA LG LG KG290 GAMA A 35€ + IVA LG LG KG375 GAMA A 35€ + IVA LG LG KP100 GAMA A 35€ +