Communication Protocol and Management Considerations for Internet of Things Gateways
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Mysql NDB Cluster 7.5.16 (And Later)
Licensing Information User Manual MySQL NDB Cluster 7.5.16 (and later) Table of Contents Licensing Information .......................................................................................................................... 2 Licenses for Third-Party Components .................................................................................................. 3 ANTLR 3 .................................................................................................................................... 3 argparse .................................................................................................................................... 4 AWS SDK for C++ ..................................................................................................................... 5 Boost Library ............................................................................................................................ 10 Corosync .................................................................................................................................. 11 Cyrus SASL ............................................................................................................................. 11 dtoa.c ....................................................................................................................................... 12 Editline Library (libedit) ............................................................................................................. 12 Facebook Fast Checksum Patch .............................................................................................. -

Efficient Parallel I/O on Multi-Core Architectures
Lecture series title/ lecture title Efficient parallel I/O on multi-core architectures Adrien Devresse CERN IT-SDC-ID Thematic CERN School of Computing 2014 1 Author(s) names – Affiliation Lecture series title/ lecture title How to make I/O bound application scale with multi-core ? What is an IO bound application ? → A server application → A job that accesses big number of files → An application that uses intensively network 2 Author(s) names – Affiliation Lecture series title/ lecture title Stupid example: Simple server monothreaded // create socket socket_desc = socket(AF_INET , SOCK_STREAM , 0); // bind the socket bind(socket_desc,(struct sockaddr *)&server , sizeof(server)); listen(socket_desc , 100); //accept connection from an incoming client while(1){ // declarations client_sock = accept(socket_desc, (struct sockaddr *)&client, &c); //Receive a message from client while( (read_size = recv(client_sock , client_message , 2000 , 0)) > 0{ // Wonderful, we have a client, do some useful work std::string msg("hello bob"); write(client_sock, msg.c_str(), msg.size()); } } 3 Author(s) names – Affiliation Lecture series title/ lecture title Stupid example: Let's make it parallel ! int main(int argc, char** argv){ // creat socket void do_work(int socket){ socket_desc = socket(AF_INET , SOCK_STREAM , 0); //Receive a message while( (read_size = // bind the socket recv(client_sock , bind(socket_desc, server , sizeof(server)); client_message , 2000 , 0)) > 0{ listen(socket_desc , 100); // Wonderful, we have a client // useful works //accept connection -

Message Passing and Network Programming
Message Passing and Network Programming Advanced Operating Systems Lecture 13 Colin Perkins | https://csperkins.org/ | Copyright © 2017 | This work is licensed under the Creative Commons Attribution-NoDerivatives 4.0 International License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nd/4.0/ or send a letter to Creative Commons, PO Box 1866, Mountain View, CA 94042, USA. Lecture Outline • Actors, sockets, and network protocols • Asynchronous I/O frameworks • Higher level abstractions Colin Perkins | https://csperkins.org/ | Copyright © 2017 2 Message Passing and Network Protocols • Recap: • Actor-based framework for message passing Send to • Each actor has a receive loop other actors Mailbox Actor Calls to one function per state Queue • Receive Message • Messages delivered by runtime system; Receiver processed sequentially Message Done Message Process • Actor can send messages in reply; Message Dispatcher return identity of next state Dequeue • Can we write network code this way? Request next • Send data by sending a message to an actor representing a socket • Receive messages representing data received on a socket Colin Perkins | https://csperkins.org/ | Copyright © 2017 3 Integrating Actors and Sockets Sending Thread Send to other actors Encoder Network Socket Mailbox Actor Queue Parser Receive Message Receiver Message Done Receiving Thread Message Process Message Dispatcher • Conceptually straightforward to integrate Dequeue actors with network code Request next • Runtime system maintains sending and -
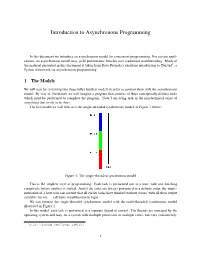
Introduction to Asynchronous Programming
Introduction to Asynchronous Programming In this document we introduce an asynchronous model for concurrent programming. For certain appli- cations, an asynchronous model may yield performance benefits over traditional multithreading. Much of the material presented in this document is taken from Dave Peticola’s excellent introduction to Twisted1, a Python framework for asynchronous programming. 1 The Models We will start by reviewing two (hopefully) familiar models in order to contrast them with the asynchronous model. By way of illustration we will imagine a program that consists of three conceptually distinct tasks which must be performed to complete the program. Note I am using task in the non-technical sense of something that needs to be done. The first model we will look at is the single-threaded synchronous model, in Figure 1 below: Figure 1: The single-threaded synchronous model This is the simplest style of programming. Each task is performed one at a time, with one finishing completely before another is started. And if the tasks are always performed in a definite order, the imple- mentation of a later task can assume that all earlier tasks have finished without errors, with all their output available for use — a definite simplification in logic. We can contrast the single-threaded synchronous model with the multi-threaded synchronous model illustrated in Figure 2. In this model, each task is performed in a separate thread of control. The threads are managed by the operating system and may, on a system with multiple processors or multiple cores, run truly concurrently, 1http://krondo.com/?page_id=1327 1 CS168 Async Programming Figure 2: The threaded model or may be interleaved together on a single processor. -

Memc3: Compact and Concurrent Memcache with Dumber Caching and Smarter Hashing
MemC3: Compact and Concurrent MemCache with Dumber Caching and Smarter Hashing Bin Fan, David G. Andersen, Michael Kaminsky∗ Carnegie Mellon University, ∗Intel Labs Abstract Standard Memcached, at its core, uses a typical hash table design, with linked-list-based chaining to handle This paper presents a set of architecturally and workload- collisions. Its cache replacement algorithm is strict LRU, inspired algorithmic and engineering improvements also based on linked lists. This design relies on locking to the popular Memcached system that substantially to ensure consistency among multiple threads, and leads improve both its memory efficiency and throughput. to poor scalability on multi-core CPUs [11]. These techniques—optimistic cuckoo hashing, a com- This paper presents MemC3 (Memcached with pact LRU-approximating eviction algorithm based upon CLOCK and Concurrent Cuckoo Hashing), a complete CLOCK, and comprehensive implementation of opti- redesign of the Memcached internals. This re-design mistic locking—enable the resulting system to use 30% is informed by and takes advantage of several observa- less memory for small key-value pairs, and serve up to tions. First, architectural features can hide memory access 3x as many queries per second over the network. We latencies and provide performance improvements. In par- have implemented these modifications in a system we ticular, our new hash table design exploits CPU cache call MemC3—Memcached with CLOCK and Concur- locality to minimize the number of memory fetches re- rent Cuckoo hashing—but believe that they also apply quired to complete any given operation; and it exploits more generally to many of today’s read-intensive, highly instruction-level and memory-level parallelism to overlap concurrent networked storage and caching systems. -

Kyffin Williams and Welsh Art
Gareth Lloyd Roderick Kyffin Williams Online at the National Library of Wales: presenting and interpreting art in a digital context. 0 1 Mandatory Layout of Declaration/Statements Word Count of thesis: 82,423 DECLARATION This work has not previously been accepted in substance for any degree and is not being concurrently submitted in candidature for any degree. Signed ....................................................... (candidate) Date .......................................................... STATEMENT 1 This thesis is the result of my own investigations, except where otherwise stated. Where *correction services have been used, the extent and nature of the correction is clearly marked in a footnote(s). Other sources are acknowledged by footnotes giving explicit references. A bibliography is appended. Signed ..................................................................... (candidate) Date ........................................................................ [*this refers to the extent to which the text has been corrected by others] STATEMENT 2 I hereby give consent for my thesis, if accepted, to be available for photocopying and for inter-library loan, and for the title and summary to be made available to outside organisations. Signed ..................................................................... (candidate) Date ........................................................................ 2 Acknowledgements I would like to thank my supervisors, Professor Robert Meyrick and Professor Lorna Hughes for their help, guidance -

A Study on Performance Improvement of Tor Network with Active Circuit Switching
A Study on Performance Improvement of Tor Network with Active Circuit Switching Author Kale, Timothy Girry Doctoral Thesis in Engineering Graduate School of Information System Department of Information Network Systems The University of Electro-communications September 2015 A Study on Performance Improvement of Tor Network with Active Circuit Switching Author Kale, Timothy Girry Approved by supervisory committee: Chairperson: Assoc. Prof. Satoshi Ohzahata Member: Prof. Hiroyoshi Morita Member: Prof. Nagao Ogino Member: Assoc. Prof. Tomohiro Ogawa Member: Assoc. Prof. Shinobu Miwa © Copyright 2015 by Kale, Timothy Girry All Rights Reserved 動的経路切り替えを用いた Tor ネットワークの性 能改善に関する研究 カレ, ティモシー ギリ 概要 Tor ネットワークは分散サーキットスイッチによるアプリケーションレベルオーバ レイネットワークであり、世界中に配置されているオニオンルータによって、匿 名性のある通信を提供する。異なる転送速度を持つサーキットが TCP コネクショ ンに集約されてデータを転送するために競合が起き、Tor はネットワーク輻輳やパ フォーマンスに対して脆弱になっている。Tor では利用可能なネットワークの容量 の大部分はバルクのユーザのトラフィックによって消費されているため、対話性 のある軽量トラフィックの遅延が増大している。サーキットの不公平なトラフィ ックの分配によって、Tor ルータがボトルネックとなり、遅延が増加し、通信品質 も低下する。この問題のため、多くの Tor ユーザが Tor ネットワークを利用する 動機を低下させ、その結果、Tor ネットワークのパフォーマンスと匿名性が大幅に 低下している。 本論文では、まず、Tor ネットワークの遅延の問題を調査する。Tor サーキット のトラフィックと暗号科通信のための計算遅延の詳細の分析をするために測定分 析を行った。測定は研究室内に設置したテストベッドと実際の Tor ネットワーク で行い、遅延がどこで発生し、パケット損失がどのように遅延を引き起こすかを 分析した。Tor ネットワークで遅延増加の原因はサーキットの集約であることを明 らかにした。分析により、Tor ネットワークの設計は、低いネットワーク容量、大 きな遅延、TCP の送信バッファのキュー長の増大に対していくつか性能の問題が あることを明らかにした。 この性能低下の問題を解決するために、動的なサーキットスイッチ方式を用い て、限られたネットワーク容量の問題に対処する。トラフィックの輻輳の監視と より大きな帯域幅をもつ OR へのサーキットを動的に構築するのため、エントリ i OR に提案方式を実装した。提案方式では Tor の現在のアルゴリズムを修正し、バ ッファオーバーフローやソケット書き込み不可のイベントを考慮したメトリック -

VOLTTRON 3.0: User Guide
PNNL-24907 Prepared for the U.S. Department of Energy under Contract DE-AC05-76RL01830 VOLTTRON 3.0: User Guide RG Lutes JN Haack S Katipamula KE Monson BA Akyol BJ Carpenter November 2015 DISCLAIMER United States Government. Neither the United States Government nor any agency thereof, nor Battelle Memorial Institute, nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial product, process, or service by trade name, trademark, manufacturer, or otherwise does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States Government or any agency thereof, or Battelle Memorial Institute. The views and opinions of authors expressed herein do not necessarily state or reflect those of the United States Government or any agency thereof. PACIFIC NORTHWEST NATIONAL LABORATORY operated by BATTELLE for the UNITED STATES DEPARTMENT OF ENERGY under Contract DE-AC05-76RL01830 Printed in the United States of America Available to DOE and DOE contractors from the Office of Scientific and Technical Information, P.O. Box 62, Oak Ridge, TN 37831-0062; ph: (865) 576-8401, fax: (865) 576-5728 email: [email protected] Available to the public from the National Technical Information Service, U.S. Department of Commerce, 5285 Port Royal Rd., Springfield, VA 22161 ph: (800) 553-6847, fax: (703) 605-6900 email: [email protected] online ordering: http://www.ntis.gov/ordering.htm This document was printed on recycled paper. -

Enabling Richer Insight Into Runtime Executions of Systems Karthik Swaminathan Nagaraj Purdue University
Purdue University Purdue e-Pubs Open Access Dissertations Theses and Dissertations Fall 2013 Enabling Richer Insight Into Runtime Executions Of Systems Karthik Swaminathan Nagaraj Purdue University Follow this and additional works at: https://docs.lib.purdue.edu/open_access_dissertations Part of the Computer Sciences Commons Recommended Citation Nagaraj, Karthik Swaminathan, "Enabling Richer Insight Into Runtime Executions Of Systems" (2013). Open Access Dissertations. 96. https://docs.lib.purdue.edu/open_access_dissertations/96 This document has been made available through Purdue e-Pubs, a service of the Purdue University Libraries. Please contact [email protected] for additional information. Graduate School ETD Form 9 (Revised 12/07) PURDUE UNIVERSITY GRADUATE SCHOOL Thesis/Dissertation Acceptance This is to certify that the thesis/dissertation prepared KARTHIK SWAMINATHAN NAGARAJ By ! Entitled! ENABLING RICHER INSIGHT INTO RUNTIME EXECUTIONS OF SYSTEMS Doctor of Philosophy For the degree of Is approved by the final examining committee: CHARLES E. KILLIAN PATRICK T. EUGSTER Chair JENNIFER L. NEVILLE DONGYAN XU RAMANA R. KOMPELLA To the best of my knowledge and as understood by the student in the Research Integrity and Copyright Disclaimer (Graduate School Form 20), this thesis/dissertation adheres to the provisions of Purdue University’s “Policy on Integrity in Research” and the use of copyrighted material. CHARLES E. KILLIAN Approved by Major Professor(s): ____________________________________ ____________________________________JENNIFER L. NEVILLE SUNIL PRABHAKAR 10/10/2013 Approved by: Head of the Graduate Program Date ENABLING RICHER INSIGHT INTO RUNTIME EXECUTIONS OF SYSTEMS A Dissertation Submitted to the Faculty of Purdue University by Karthik Swaminathan Nagaraj In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy December 2013 Purdue University West Lafayette, Indiana ii To my wife Ashwathi, my parents Nagaraj & Rajeswari, and sister Narmadha. -

Patterns of Modern Web Applications with Javascript
Patterns of Modern Web Applications with Javascript Ken Chau This book is for sale at http://leanpub.com/patterns-of-modern-web-applications This version was published on 2015-07-10 This is a Leanpub book. Leanpub empowers authors and publishers with the Lean Publishing process. Lean Publishing is the act of publishing an in-progress ebook using lightweight tools and many iterations to get reader feedback, pivot until you have the right book and build traction once you do. ©2015 Ken Chau Contents Introduction ............................................ 1 Who This Book is For ...................................... 1 Overview ............................................ 1 Acknowledgements ....................................... 2 Help and Support ........................................ 2 Part 1. Javascript Environments and Modularity .................. 3 Chapter One: Javascript Runtime Environments ....................... 4 Versions of Javascript ...................................... 4 Chapter Two: Patterns of Modularity .............................. 11 Introduction Who This Book is For Web development technology has shifted from server to client. This allowed for highly interactive applications to be developed in the style of Single Page Applications (SPA). Traditional server- rendered pages are becoming more and more extinct as Web browsers and hardware are getting faster and faster. As developers develop these complex applications, new patterns are emerging that would solve some problems presented by the “traditional” SPA’s. I have written this book for developers like me. I’m assuming that you come from a background of Web development. This should probably not be the book you use to start learning Web development. I hope to share lessons learned from building large and complex Web applications. This book captures the common design and architecture pattern found in modern Web development today. In this book, I am focusing on the front-end Web development stack written in Javascript. -

Enhancing Quality of Service Metrics for High Fan-In Node.Js Applications by Optimising the Network Stack
DEGREE PROJECT, IN COMPUTER SCIENCE , SECOND LEVEL LAUSANNE, SWITZERLAND 2015 Enhancing Quality of Service Metrics for High Fan-In Node.js Applications by Optimising the Network Stack LEVERAGING IX: THE DATAPLANE OPERATING SYSTEM FREDRIK PETER LILKAER KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF COMPUTER SCIENCE AND COMMUNICATION (CSC) Enhancing Quality of Service Metrics for High Fan-in Node.js Applications by Optimising the Network Stack -Leveraging IX: The Dataplane Operating System FREDRIK PETER LILKAER DD221X, Master’s Thesis in Computer Science (30 ECTS credits) Degree Progr. in Computer Science and Engineering 300 credits Master Programme in Computer Science 120 credits Royal Institute of Technology year 2015 Supervisor at EPFL was Edouard Bugnion Supervisor at CSC wa s Carl-Henrik Ek Examiner wa s Johan Håstad Presented: 2015-10-01 Royal Institute of Technology School of Computer Science and Communication KTH CSC SE-100 44 Stockholm, Sweden URL: www.kth.se/csc Abstract This thesis investigates the feasibility of porting Node.js, a JavaScript web application framework and server, to IX, a data- plane operating system specifically developed to meet the needs of high performance microsecond-computing type of applications in a datacentre setting. We show that porting requires exten- sions to the IX kernel to support UDS polling, which we imple- ment. We develop a distributed load generator to benchmark the framework. The results show that running Node.js on IX improves throughput by up to 20.6%, latency by up to 5.23×, and tail latency by up to 5.68× compared to a Linux baseline. We show how server side request level reordering affect the la- tency distribution, predominantly in cases where the server is load saturated. -

Here to See the Group and Apply for Membership
Building a Digital Portfolio RRCHNM & The Getty Foundation Building a Digital Portfolio DH for Art History Graduate Students 1 Building a Digital Portfolio RRCHNM & The Getty Foundation Table Of Contents About ............................................................... 3 Institute Team ........................................................ 4 July 13: Introductions ................................................... 5 July 14: Surveying Major Digital Art Collections ................................ 7 July 15: Building Digital Collections ......................................... 9 July 16: Modeling and Models ............................................ 11 July 17: Data and Text Analysis ........................................... 13 July 20: Visualizations and Networks ....................................... 15 July 21: Mapping and Spatial History ....................................... 17 July 22: Shared Authority and GLAMs ...................................... 19 July 23: Project Planning & Grant Proposals .................................. 21 July 24: Scholarly Communication, Professionalization, Publications ................. 23 Glossary ............................................................ 24 Bibliography ......................................................... 28 Digital Art History Web ................................................. 41 Art History Collections, Highlights ......................................... 43 Multimedia Sources .................................................... 45 SketchUp Tutorial ....................................................