Verifying Constant-Time Implementations
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

A History of End-To-End Encryption and the Death of PGP
25/05/2020 A history of end-to-end encryption and the death of PGP Hey! I'm David, a security engineer at the Blockchain team of Facebook (https://facebook.com/), previously a security consultant for the Cryptography Services of NCC Group (https://www.nccgroup.com). I'm also the author of the Real World Cryptography book (https://www.manning.com/books/real-world- cryptography?a_aid=Realworldcrypto&a_bid=ad500e09). This is my blog about cryptography and security and other related topics that I Ûnd interesting. A history of end-to-end encryption and If you don't know where to start, you might want to check these popular the death of PGP articles: posted January 2020 - How did length extension attacks made it 1981 - RFC 788 - Simple Mail Transfer Protocol into SHA-2? (/article/417/how-did-length- extension-attacks-made-it-into-sha-2/) (https://tools.ietf.org/html/rfc788) (SMTP) is published, - Speed and Cryptography the standard for email is born. (/article/468/speed-and-cryptography/) - What is the BLS signature scheme? (/article/472/what-is-the-bls-signature- This is were everything starts, we now have an open peer-to-peer scheme/) protocol that everyone on the internet can use to communicate. - Zero'ing memory, compiler optimizations and memset_s (/article/419/zeroing-memory- compiler-optimizations-and-memset_s/) 1991 - The 9 Lives of Bleichenbacher's CAT: New Cache ATtacks on TLS Implementations The US government introduces the 1991 Senate Bill 266, (/article/461/the-9-lives-of-bleichenbachers- which attempts to allow "the Government to obtain the cat-new-cache-attacks-on-tls- plain text contents of voice, data, and other implementations/) - How to Backdoor Di¸e-Hellman: quick communications when appropriately authorized by law" explanation (/article/360/how-to-backdoor- from "providers of electronic communications services di¸e-hellman-quick-explanation/) and manufacturers of electronic communications - Tamarin Prover Introduction (/article/404/tamarin-prover-introduction/) service equipment". -

Detecting and Preventing Active Attacks Against Autocrypt Release 0.10.0
Detecting and preventing active attacks against Autocrypt Release 0.10.0 NEXTLEAP researchers Jan 09, 2020 Contents 1 Introduction2 1.1 Attack model and terminology............................2 1.2 Problems of current key-verification techniques...................3 1.3 Integrating key verification with general workflows.................3 1.4 Supplementary key consistency through ClaimChains................4 1.5 Detecting inconsistencies through Gossip and DKIM................5 2 Securing communications against network adversaries6 2.1 Setup Contact protocol................................7 2.2 Verified Group protocol................................ 12 2.3 History-verification protocol............................. 17 2.4 Verifying keys through onion-queries......................... 20 3 Key consistency with ClaimChains 23 3.1 High level overview of the ClaimChain design.................... 23 3.2 Use and architecture................................. 24 3.3 Evaluating ClaimChains to guide verification.................... 26 4 Using Autocrypt key gossip to guide key verification 28 4.1 Attack Scenarios................................... 28 4.2 Probability of detecting an attack through out of band verification......... 29 5 Using DKIM signature checks to guide key verification 32 5.1 DKIM Signatures on Autocrypt Headers....................... 32 5.2 Device loss and MITM attacks............................ 33 5.3 Open Questions.................................... 34 1 1 Introduction This document considers how to secure Autocrypt1-capable mail apps against active network at- tackers. Autocrypt aims to achieve convenient end-to-end encryption of e-mail. The Level 1 Autocrypt specification offers users opt-in e-mail encryption, but only considers passive adver- saries. Active network adversaries, who could, for example, tamper with the Autocrypt header during e-mail message transport, are not considered in the Level 1 specification. Yet, such active attackers might undermine the security of Autocrypt. -
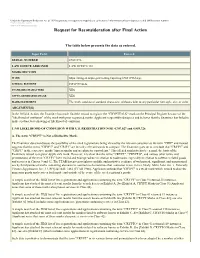
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh
Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy under the Executive Committee of the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2021 © 2021 John Seunghyun Koh All Rights Reserved Abstract Easy Encryption for Email, Photo, and Other Cloud Services John Seunghyun Koh Modern users carry mobile devices with them at nearly all times, and this likely has contribut- ed to the rapid growth of private user data—such as emails, photos, and more—stored online in the cloud. Unfortunately, the security of many cloud services for user data is lacking, and the vast amount of user data stored in the cloud is an attractive target for adversaries. Even a single compro- mise of a user’s account yields all its data to attackers. A breach of an unencrypted email account gives the attacker full access to years, even decades, of emails. Ideally, users would encrypt their data to prevent this. However, encrypting data at rest has long been considered too difficult for users, even technical ones, mainly due to the confusing nature of managing cryptographic keys. My thesis is that strong security can be made easy to use through client-side encryption using self-generated per-device cryptographic keys, such that user data in cloud services is well pro- tected, encryption is transparent and largely unnoticeable to users even on multiple devices, and encryption can be used with existing services without any server-side modifications. This dis- sertation introduces a new paradigm for usable cryptographic key management, Per-Device Keys (PDK), and explores how self-generated keys unique to every device can enable new client-side encryption schemes that are compatible with existing online services yet are transparent to users. -

Smarx OS Compendium 2020 for the CRYPTO-BOX
2020 EDITION Smarx® Compendium d s p . ) r e v o C _ n a M x r a m S ( a s 2 1 v o N 7 2 - www.marx.com 0 2 We highly appreciate and value your comments and suggestions! Suggestions for improvements will be honored with: • Free Business Support for 6 months • Enrollment in our BE !" ester program Software security is a growing challenge and requires constant improving " be part of the process! $lease send sugestions and error report to: • $$%& software/hardware in general and documentation (including this Compendium*: support@mar,.com • WEB and online ordering system related: webmaster+mar,.com Smar, .S )ompendium November 2020 )opyright 1 2002, 2020 2!345 )ryptoTech 6$ 7 Table of Contents 8. What is this Compendium !bout?--------------------------------------------------------------------------------: 8-8. ;ntroduction--------------------------------------------------------------------------------------------------------: 8.2. What is /ew9-------------------------------------------------------------------------------------------------------: 8-7. What to Find Where in this )ompendium--------------------------------------------------------------< 8-=. $rofessional Software $rotection Secures 3evenue----------------------------------------------< 8->. he )3?$ ."BO45@ardware-----------------------------------------------------------------------------88 8->-8. )3?$ ."BOX 2odels--------------------------------------------------------------------------------88 8->.2. echnical Features of the )3?$ ."BO45----------------------------------------------------88 -

Microsoft Opensources Its C Standard Library STL
Microsoft Open-sources Its C Standard Library (STL) 1 / 4 2 / 4 Microsoft Open-sources Its C Standard Library (STL) 3 / 4 Microsoft Visual Studio Team just opened sourced the C++ Standard Library (aka STL) ... The STL (Standard Template Library) was developed separately, and then ... But it was not developed as part of the C++ standard, and for this ... of the C++ Standard Library (also known as the STL) as open source.. That means you'll be able to compile C++ programs against both and it'll work, but it also means reactos can just include the actual C++ standard binary and .... STL, their C++ standard library... http://www.phoronix.com/scan.php?page=news_item&px=Microsoft-STL-Open-Source.. ... our implementation of the C++ Standard Library (also known as the STL) as open source. https://github.com/microsoft/STL is our new repository, containing all of ... As it explains, we're still working on migrating to GitHub.. Microsoft has made its implementation of the Standard Library of C++ open-source on GitHub. The implementation becomes available under .... Microsoft C++ Standard Library wordt open source ... Op de Github site https://github.com/microsoft/STL staat de nieuwe repository, die een .... Last week, Microsoft open-sourced its implementation of the C++ Standard Library, also known as STL. The library is shipped along with MSVC (Microsoft Visual C++ compiler) toolset and the Visual Studio IDE. ... Users can use the C++ library repo for participating in the STL’s .... MSVC's implementation of the C++ Standard Library. ... But if you need parts of your own source code to trigger the STL bug, you need to extract that for us. -

AUTOCRYPT: Enabling Homomorphic Computation on Servers to Protect Sensitive Web Content
AUTOCRYPT: Enabling Homomorphic Computation on Servers to Protect Sensitive Web Content Shruti Tople Shweta Shinde Zhaofeng Chen Prateek Saxena School of Computing National University of Singapore {shruti90, shweta24, chenzhao, prateeks} @comp.nus.edu.sg ABSTRACT attacks can be used to compromise web servers and install malware. Web servers are vulnerable to a large class of attacks which can Despite heightened security concerns [10], stronger data protection allow a network attacker to steal sensitive web content. In this laws [4, 8, 9], and availability of commercial detection tools [6, 7], work, we investigate the feasibility of a web server architecture, server-side data breaches have been persistently high for the last 3 wherein the vulnerable server VM runs on a trusted cloud. All sen- years [25]. sitive web content is made available to the vulnerable server VM in Previous work has proposed partitioning monolithic web servers encrypted form, thereby limiting the effectiveness of data-stealing into multiple pieces, as a second line of defense. For instance, attacks through server VM compromise. separating the web application logic into multiple VMs based on In this context, the main challenge is to allow the legitimate func- roles [49], privilege separating users using OS protections [39], or tionality of the untrusted server VM to work. As a step towards using trusted hardware features to attest the integrity of server VMs [44,45,61]. In this work, we advocate a new approach for building this goal, we develop a tool called AUTOCRYPT, which transforms a subset of existing C functionality in the web stack to operate on a second line of defense: we investigate how to protect sensitive encrypted sensitive content. -

Easy Email Encryption with Easy Key Management
Why Joanie Can Encrypt: Easy Email Encryption with Easy Key Management John S. Koh Steven M. Bellovin Jason Nieh Columbia University Columbia University Columbia University New York, NY New York, NY New York, NY koh@cs:columbia:edu smb@cs:columbia:edu nieh@cs:columbia:edu Abstract subjected to a simple password recovery and reset attack Email privacy is of crucial importance. Existing email encryp- which granted the attacker full access to her personal email tion approaches are comprehensive but seldom used due to account on the Yahoo! Mail website. John Brennan’s AOL their complexity and inconvenience. We take a new approach web email account was compromised via social engineering. to simplify email encryption and improve its usability by im- Adversaries also sometimes seize entire email servers such plementing receiver-controlled encryption: newly received as in the cases of cock.li and TorMail [30, 41], or compromise messages are transparently downloaded and encrypted to a them, such as in the Sony Pictures email leaks [43]. locally-generated key; the original message is then replaced. The common thread is that a compromise exposes the To avoid the problem of moving a single private key between entire history of affected users’ emails after a single breach. devices, we implement per-device key pairs: only public keys With the explosive growth in cloud storage, it is easy to need be synchronized via a simple verification step. Com- keep gigabytes of old emails at no cost. Gmail’s massive promising an email account or server only provides access storage capacity—up to 15 GB for free, or 30 TB for paid to encrypted emails. -

Downloaded from the Same Web Page
Finding short and implementation-friendly addition chains with evolutionary algorithms The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation Picek, Stjepan et al. “Finding Short and Implementation-Friendly Addition Chains with Evolutionary Algorithms.” Journal of Heuristics 24, 3 (June 2017): 457–481 © 2017 Springer Science+Business Media, LLC As Published https://doi.org/10.1007/s10732-017-9340-2 Publisher Springer-Verlag Version Author's final manuscript Citable link http://hdl.handle.net/1721.1/115968 Terms of Use Article is made available in accordance with the publisher's policy and may be subject to US copyright law. Please refer to the publisher's site for terms of use. Journal of Heuristics manuscript No. (will be inserted by the editor) Finding Short and Implementation-friendly Addition Chains with Evolutionary Algorithms Stjepan Picek · Carlos A. Coello Coello · Domagoj Jakobovic · Nele Mentens Received: date / Accepted: date Abstract Finding the shortest addition chain for a given exponent is a sig- nificant problem in cryptography. In this work, we present a genetic algorithm with a novel encoding of solutions and new crossover and mutation opera- tors to minimize the length of the addition chains corresponding to a given exponent. We also develop a repair strategy that significantly enhances the performance of our approach. The results are compared with respect to those generated by other metaheuristics for exponents of moderate size, but we also investigate values up to 2255 − 21. For numbers of such size, we were unable to find any results produced by other metaheuristics which could be used for comparison purposes. -

A NATIONAL STRATEGY to RESTORE COASTAL and ESTUARINE HABITAT Dear Friend
A NATIONAL STRATEGY TO RESTORE COASTAL AND ESTUARINE HABITAT Dear Friend, The rich interplay between the land and the sea creates one of America’s most valuable natural, economic, and cultural res o u r ces—its estuaries and coasts. In this unique nexus— characterized by the dynamic blending of salt and fresh water during tidal cycles—abundant life is created and nurtu re d . Estuaries nurtu r e not only shellfish, fish, and wildlife, but also nourish the human spirit. We ar e from the sea, and we are continually lured back to its edge, rei n f o r cing the kinship we sh a r e with this place as we sail, fish, swim, and relax near a glistening bay or a rocky shore. And yet, no place on earth more directly embodies the challenge of balancing human needs and the needs of other species than estuaries. By 2025, 75 percent of our population will live within 50 miles of the coast. We must learn how to develop our own habitat while also pro- tecting and restoring the very essence of what binds us to our coasts. Re s t o r e America’s Estuaries and the National Oceanic and Atmospheric Administration are pleased to present A National Strategy to Restore Coastal and Estuarine Habitat, and we are grateful to the scores of scientists, restoration practitioners, program managers, and others who contributed their expertise and insights. This National Strategy takes a major step to w a r d reclaiming losses of the past 200 years. We look forwa r d to continued collaboration as we move forwa r d and reinvest in our coastal and estuarine habitats. -

Fourq on ASIC: Breaking Speed Records for Elliptic Curve Scalar Multiplication
FourQ on ASIC: Breaking Speed Records for Elliptic Curve Scalar Multiplication Hiromitsu Awano∗ and Makoto Ikeda† VLSI Design and Education Center, The University of Tokyo Hongo 7-3-1, Bunkyo-ku, Tokyo, Japan, 113–8656 Email: ∗[email protected], †[email protected] Abstract—An ASIC cryptoprocessor for scalar multiplication To reduce the key size without degrading the security level, (SM) on FourQ is proposed. By exploiting Karatsuba multi- elliptic curve digital signature algorithms (ECDSAs) have been plication and lazy reduction techniques, the arithmetic units developed. In comparison to RSA, ECDSA exploits a scalar of the proposed processor are tailored for operations over multiplication, the repetitive additions of a point along an quadratic extension field (Fp2 ). We also propose an automated instruction scheduling methodology based on a combinatorial elliptic curve, to produce a one-way function. ECDSA is optimization solver to fully exploit the available instruction- known to achieve the same security strength with only a 1/10 level parallelism. With the proposed processor fabricated by of key length used in RSA [4], e.g., a 256 bit elliptic curve using a 65 nm silicon-on-thin-box (SOTB) CMOS process, we public key should provide comparable security to a 3072 bit demonstrate that an SM can be computed in 10.1 μs when a typical operating voltage of 1.20 V is applied, which corresponds RSA public key, which drastically reduce the key storage and to 3.66× acceleration compared to the conventional P-256 curve transmission cost and is suitable for embedded applications. -

Compact Variable-Base ECC Scalar Multiplication Using Euclidean Addition Chains
Compact Variable-base ECC Scalar Multiplication using Euclidean Addition Chains Fabien Herbaut1, Nicolas Meloni´ 2 and Pascal Veron´ 2 1INSPE Nice-Toulon, Universite´ Coteˆ d’Azur, Institut de Mathematiques´ de Toulon, France 2Institut de Mathematiques´ de Toulon, Universite´ de Toulon, France Keywords: Elliptic Curves, Scalar Multiplication, Side-channel Protection, Memory Usage, Addition Chain. Abstract: The random generation of Euclidean addition chains fits well with a GLV context (Dosso et al., 2018) and provides a method with decent performance despite the growth of the base field required to get the same level of security. The aim of this paper is to reduce the size of the base field required. Combined with an algorithmic improvement, we obtain a reduction of 21% of the memory usage. Hence, our method appears to be one of the most compact scalar multiplication procedure and is particularly suitable for lightweight applications. 1 INTRODUCTION AND a larger curve as compared to other methods for the CONTEXT same security level. But despite the growth of the base field, it provides decent speed results and very The increasing importance of smart devices such as good memory usage performance. smart cards or sensor networks comes with growing The aim of this paper is to improve the method needs for low cost algorithms in the area of crypto- described in Section 4 of (Dosso et al., 2018). First, graphic primitives. Relevant solutions should involve we obtain an asymptotic reduction of 7.97% of the low memory usage and a compact code which does size of the base field required. Next, we modify the not sacrifice protection against physical attacks.