TOWARDS a GLOBAL DATA PRIVACY STANDARD1 Michael L. Rustad* & Thomas H. Koenig** Abstract This Article Questions the Widespre
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

T H E N E T D E L U S Io N E V G E N Y M O R O Zo V
2/C PMS (BLACK + 809) SOFT-TOUCH MATTE LAMINATION + SPOT GLOSS THE NET DELUSION EVGENY MOROZOV POLITICS/TECHNOLOGY $27.95/$35.50 CAN “ Evgeny Morozov is wonderfully knowledgeable about the Internet—he seems “THE REVOLUTION WILL BE TWITTERED!” to have studied every use of it, or every political use, in every country in the declared journalist Andrew Sullivan after world (and to have read all the posts). And he is wonderfully sophisticated and protests erupted in Iran in June 2009. Yet for tough-minded about politics. This is a rare combination, and it makes for a all the talk about the democratizing power powerful argument against the latest versions of technological romanticism. of the Internet, regimes in Iran and China His book should be required reading for every political activist who hopes to are as stable and repressive as ever. In fact, ALEXANDER KRSTEVSKI ALEXANDER change the world on the Internet.” —MICHAEL WALZER, Institute for authoritarian governments are effectively Advanced Study, Princeton using the Internet to suppress free speech, EVGENY MOROZOV hone their surveillance techniques, dissem- is a contributing editor to Foreign Policy “ Evgeny Morozov has produced a rich survey of recent history that reminds us inate cutting-edge propaganda, and pacify and Boston Review and a Schwartz Fellow that everybody wants connectivity but also varying degrees of control over their populations with digital entertain- at the New American Foundation. Morozov content, and that connectivity on its own is a very poor predictor of political ment. Could the recent Western obsession is currently also a visiting scholar at Stan- pluralism... -

June 10, 2021 President Joseph R. Biden the White House 1600
June 10, 2021 President Joseph R. Biden The White House 1600 Pennsylvania Ave. NW Washington, DC 20500 Dear Mr. President: We, the undersigned civil rights, civil liberties, privacy, government accountability, and consumer rights organizations, urge your Administration to ensure that any new transatlantic data transfer deal is coupled with the enactment of U.S. laws that reform government surveillance practices and provide comprehensive privacy protections. The United States’ failure to ensure meaningful privacy protections for personal data is the reason that a growing number of countries are concerned about trans-border data flows. Until the United States addresses this problem, concerns about data transfers to the United States will remain, and data flow agreements are likely to be invalidated. Recent history demonstrates that any transatlantic data transfer agreement will be subject to litigation to determine whether it provides adequate protection for personal data. In 2015, the Court of Justice of the European Union invalidated the U.S.-EU Safe Harbor agreement. And in July 2020, the successor agreement, Privacy Shield, was also invalidated by the same court. Without reform of U.S. surveillance and privacy laws, any new transatlantic data transfer deal will likely face a similar fate. The only way to fully address these issues and enter into a lasting transatlantic agreement is to harmonize data protection standards between the European Union and the United States. There have been calls for the United States to strengthen and modernize its privacy laws since long before the European Union’s General Data Protection Regulation came into effect in 2018. The modern concept of the right to privacy was invented in the United States – but now we lag behind many other nations on privacy protections. -

Survey on Privacy Preserving in Social Networks
International Journal of Science and Research (IJSR) ISSN (Online): 2319-7064 Index Copernicus Value (2015): 78.96 | Impact Factor (2015): 6.391 Survey on Privacy Preserving in Social Networks S. Mayil1, Dr. M. Vanitha2 1Research scholar, PG & Research Department of Computer Science, JJ College of Arts and Science (Autonomous), Pudukkottai, Tamil Nadu, India 2Assistant Professor, Ph.D. and Research Department of Computer Application, Alagappa University, Karaikudi , Tamilnadu. Abstract: The development of online social networks and the release of data network resulting in the risk of leakage of personal confidential information. This requires privacy protection before the data network is published by the service provider. Data privacy online social networks are important in recent years. Therefore, this research is still in its infancy. This article describes the generalization techniques of anonymous social networking data with sufficient privacy for harsh environments while preserving the validity of the data. The loss metric information, iloss, is used to check the information due to the loss of the generalized amount. While these networks make frequent data sharing and intercommunication between users can instantly and privacy problems that may arise are very explicable with their obvious immediate consequences. Although the concept of privacy can take different forms, the ultimate challenge is how to prevent the invasion of privacy when personal information is available. Basic social networks, co-statements, and their associated primary motivations. The following describes how to protect privacy, relying on technical analysis and link social networks to disclose sensitive user information. Keywords: Data Privacy, Data Publishing, Privacy Preserving, Social Network, Service Provider. 1. Introduction data may affect the privacy of individuals. -

CJEU Ruling on Facebook Action on January 25, 2018: Class Action, Model Case Or No Jurisdiction?
CJEU ruling on Facebook action on January 25, 2018: Class action, model case or no jurisdiction? In August 2014, lawyer and data protection expert Max Schrems filed a lawsuit against Facebook with his competent court in Vienna, as previous complaints in Ireland have not been decided by the Irish Data Protection Commissioner since 2011. Now the CJEU decides on the admissibility of the lawsuit against Facebook. Previously, in 2015 Schrems brought down the EU-US “Safe Harbor” system through a case against Facebook at the CJEU. Dispute solely on jurisdiction and on two questions Facebook has submitted various grounds with the court in Vienna, why the procedure should not be heard at all. The majority of these attempts to prevent the procedure have already been rejected by the Austria courts over the past three years. What remained, were two questions: (1) whether Mr Schrems is a "consumer" or has lost this status through his pro bono work as a privacy advocate; and (2) whether he can bring claims of other users jointly in a "class action". The class action is financed by ROLAND Prozessfinanz AG. Facebook wants each of the 25,000 other users to have to sue in a separate procedure - which would make the legal costs skyrocket and a case against Facebook financially impossible for most users. In Facebook’s view, the same legal and factual issues should therefore be trailed 25,000 times in front of thousands of European courts and judges (“divide and conquer”). These two questions were submitted to the Court of Justice of the European Union (CJEU) for a preliminary ruling by the Austrian Supreme Court. -

Facebook: Where Privacy Concerns and Social Needs Collide
Edith Cowan University Research Online Theses: Doctorates and Masters Theses 2020 Facebook: Where privacy concerns and social needs collide Sonya Scherini Edith Cowan University Follow this and additional works at: https://ro.ecu.edu.au/theses Part of the Communication Technology and New Media Commons, Mass Communication Commons, and the Social Media Commons Recommended Citation Scherini, S. (2020). Facebook: Where privacy concerns and social needs collide. https://ro.ecu.edu.au/ theses/2331 This Thesis is posted at Research Online. https://ro.ecu.edu.au/theses/2331 Edith Cowan University Copyright Warning You may print or download ONE copy of this document for the purpose of your own research or study. The University does not authorize you to copy, communicate or otherwise make available electronically to any other person any copyright material contained on this site. You are reminded of the following: Copyright owners are entitled to take legal action against persons who infringe their copyright. A reproduction of material that is protected by copyright may be a copyright infringement. Where the reproduction of such material is done without attribution of authorship, with false attribution of authorship or the authorship is treated in a derogatory manner, this may be a breach of the author’s moral rights contained in Part IX of the Copyright Act 1968 (Cth). Courts have the power to impose a wide range of civil and criminal sanctions for infringement of copyright, infringement of moral rights and other offences under the Copyright Act 1968 (Cth). Higher penalties may apply, and higher damages may be awarded, for offences and infringements involving the conversion of material into digital or electronic form. -

A Collaborative Framework: for Privacy Protection in Online Social Networks
A Collaborative Framework: for Privacy Protection in Online Social Networks 4 4 Yan Zhu1,2, Zexing Hu1, Huaixi Wang3, Hongxin Hu , Gail-Joon Ahn 1 Institute of Computer Science and Technology, Peking University, Beijing 100871, China 2Key Laboratory of Network and Software Security Assurance (Peking University), Ministry of Education, China 3School of Mathematical Sciences, Peking University, Beijing 100871, China, 4Laboratory of Security Engineering for Future Computing (SEFCOM), Arizona State University, Tempe, AZ 85287, USA Email: {yan.zhu.huzx.wanghx}@pku.edu.cn. {hxhu,gahn }@asu.edu Abstract-With the wide use of online social networks (OSNs) , Although some new techniques were introduced in these the problem of data privacy has attracted much attention. solutions, it is still necessary for a centralized server to Several approaches have been proposed to address this issue. enforce access control, which cannot protect the privacy of One of privacy management approaches for OSN leverages a key users against the centralized server. Also, some solutions management technique to enable a user to simply post encrypted contents so that only users who can satisfy the associate security implemented access control at client-side but their approach policy can derive the key to access the data. However, the key should be synchronous, requiring multiple users to be online management policies of existing schemes may grant access to simultaneously. unaurhorized users and cannot efficiently determine authorized One of efficient ways for enforcing access control in OSN users. In this paper, we propose a collaborative framework is to allow users to put the encrypted data on the server and which enforces access control for OSN through an innovative key management focused on communities. -

Surveillance by Intelligence Services: Services: Intelligence by Surveillance
FREEDOMS FRA Surveillance by intelligence services – Volume II: field perspectives and legal update II: field perspectives – Volume services intelligence by Surveillance Surveillance by intelligence services: fundamental rights safeguards and remedies in the EU Volume II: field perspectives and legal update This report addresses matters related to the respect for private and family life (Article 7), the protection of personal data (Article 8) and the right to an effective remedy and a fair trial (Article 47) falling under Titles II ‘Freedoms’ and VI ‘Justice’ of the Charter of Fundamental Rights of the European Union. Europe Direct is a service to help you find answers to your questions about the European Union Freephone number (*): 00 800 6 7 8 9 10 11 (*) The information given is free, as are most calls (though some operators, phone boxes or hotels may charge you). Photo (cover & inside): © Shutterstock More information on the European Union is available on the internet (http://europa.eu). Luxembourg: Publications Office of the European Union, 2017 FRA – print: ISBN 978-92-9491-766-9 doi:10.2811/15232 TK-04-17-696-EN-C FRA – web: ISBN 978-92-9491-765-2 doi:10.2811/792946 TK-04-17-696-EN-N © European Union Agency for Fundamental Rights, 2017 Reproduction is authorised provided the source is acknowledged. For any use or reproduction of photos or other material that is not under the European Union Agency for Fundamental Rights copyright, permission must be sought directly from the copyright holders. Printed by Imprimerie Centrale in Luxembourg Neither the European Union Agency for Fundamental Rights nor any person acting on behalf of the European Union Agency for Fundamental Rights is responsible for the use that might be made of the following information. -

Report Data Privacy and Data Security 2015
DATA PrivAcy AnD DATA securiTy rePorT 2015 upDates inDustry 4.0 Botnet seCurity poliCy interConneCtivity seCret CoDe CyBerwar regulation rules CryptograpHy Big Data CyBerspaCe Data proteCtion integrity CyBer DeFense Center Firewall virus proteCtion BasiC rigHts Digitization enCryption Control meCHanism DDos attaCk Data proteCtion oFFiCer rules it seCurity aCt inFormational selF-Determination passworD rules it seCurity HaCker ClouD serviCes eu general Data proteCtion regulation Data minimization selF-Determination emergenCy plan DATA PrivAcy AnD DATA securiTy rePorT 2015 DATA PrivAcy AnD DATA securiTy rePorT 2015 14 The generAl Data ProTecTion regulation sTrengThens The sTrengThs of The euroPeAn iT inDusTry conTenTs 06 A key sTeP TowArDs fAir comPeTiTion Jan Philipp Albrecht, Member of the European The grounDbreAking ruling shAking 16 Parliament SecuriTy for The uP The DigiTAl economy 21 Dr. Thomas Kremer, fourTh inDusTriAl Member of the Board of Management for Data Privacy, revoluTion Legal Affairs and Compliance at Deutsche Telekom Reinhard Clemens, CEO of T-Systems and Member of Deutsche Telekom’s Board of Management and Director of its IT Division 08 Beginning The journey To moDern-day data Policies Dr. Thomas de Maizière, 10 Data securiTy AnD 22 Capturing The mArkeT…. Federal Minister of the Interior PrivAcy Are imPorTAnT eAsy, fAsT AnD secure issues for germAny’s Dr. Ferri Abolhassan, DomesTic inTelligence Member of the Management Board service of T-Systems International Dr. Heinz-Georg Maaßen, President of the BfV 52 Welcome To The zeTTAbyTe Age 27 creating TrusT Anette Bronder, Lothar Schröder, Member of T-Systems Inter- 12 A big sTeP forwArD inTo Deputy Chairman of the Supervisory national’s Board of Manage- The DigiTAl revoluTion Board at Deutsche Telekom and ment and Director of its Vĕra Jurová, Chairman of the Data Protection Digital Division European Commissioner for Justice, Advisory Board Consumers and Gender Equality 18 Europe and its privacy shield Wolfgang Kopf, LL.M. -

Number of Markets Cleared: 210 208 188 194 4 209 205 204 167 Percent of Households Cleared: 100.0% 99.3% 97.6% 97.9% 12.3% 99.7% 97.3% 97.6% 75.4%
NUMBER OF MARKETS CLEARED: 210 208 188 194 4 209 205 204 167 PERCENT OF HOUSEHOLDS CLEARED: 100.0% 99.3% 97.6% 97.9% 12.3% 99.7% 97.3% 97.6% 75.4% 175 198 194 195 203 170 197 128 201 DR. OZ 3RD QUEEN QUEEN MIND OF A SEINFELD 4TH SEINFELD 5TH DR. OZ CYCLE LATIFAH LATIFAH MAN CYCLE CYCLE KING 2nd Cycle KING 3rd Cycle RANK MARKET %US REP 2011-2014 2014-2015 2013-2014 2014-2015 2015-2016 4th Cycle 5th Cycle 2nd Cycle 3rd Cycle 1 NEW YORK NY 6.44% PM WNYW WNYW/WWOR WCBS/WLNY WCBS/WLNY WPIX WPIX WPIX WCBS/WLNY WCBS/WLNY 2 LOS ANGELES CA 4.89% ES KABC KCOP/KTTV KCAL/KCBS KCAL/KCBS KCOP/KDOC/KTTV KCOP/KDOC/KTTV KCOP/KTTV KCOP/KTTV 3 CHICAGO IL 3.05% ZH WFLD WFLD/WPWR WBBM/WCIU WBBM WCIU WCIU/WWME WCIU WCIU 4 PHILADELPHIA PA 2.56% PM WTXF WTXF KYW/WPSG KYW/WPSG KYW/WPSG KYW/WPSG KYW/WPSG KYW/WPSG 5 DALLAS-FT WORTH TX 2.29% JM KFWD/WFAA KDFI/KDFW KTVT/KTXA KTVT/KTXA KDAF KDAF KDAF KTVT/KTXA KTVT/KTXA 6 SAN FRANCISCO-OAKLAND-SAN JOSE CA 2.18% ES KICU/KTVU KICU/KTVU KBCW/KPIX KBCW/KPIX KICU/KTVU KICU/KTVU KBCW/KPIX KBCW/KPIX 7 BOSTON (MANCHESTER) MA 2.10% PM WFXT WFXT WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK 8 WASHINGTON (HAGERSTOWN) DC 2.08% PM WTTG WDCA/WTTG WJLA WJLA WDCW WDCW WJAL 9 ATLANTA GA 2.05% JM WAGA WSB WUPA WUPA WPCH WPCH WPCH WPCH 10 HOUSTON TX 1.98% JM KPRC KRIV/KTXH KPRC KPRC KIAH KIAH KUBE KRIV/KUBE KUBE 11 DETROIT MI 1.60% ZH WXYZ WXYZ WKBD/WWJ WKBD/WWJ WKBD/WWJ WMYD WADL WKBD/WWJ WKBD/WWJ 12 PHOENIX AZ 1.60% ES KTVK KSAZ/KUTP KASW/KTVK KASW/KTVK KAZT KAZT KASW/KTVK KASW/KTVK 13 SEATTLE-TACOMA WA 1.60% ES KOMO/KOMO-DT2 -

The Brussels Effect
Copyright 2012 by Northwestern University School of Law Printed in U.S.A. Northwestern University Law Review Vol. 107, No. 1 Articles THE BRUSSELS EFFECT Anu Bradford ABSTRACT—This Article examines the unprecedented and deeply underestimated global power that the European Union is exercising through its legal institutions and standards, and how it successfully exports that influence to the rest of the world. Without the need to use international institutions or seek other nations’ cooperation, the EU has a strong and growing ability to promulgate regulations that become entrenched in the legal frameworks of developed and developing markets alike, leading to a notable “Europeanization” of many important aspects of global commerce. The Article identifies the precise conditions for and the specific mechanism through which this externalization of EU’s standards unfolds. Enhanced understanding of these conditions and this mechanism helps explain why the EU is currently the only jurisdiction that can wield unilateral influence across a number of areas of law—ranging from antitrust and privacy to health and environmental regulation—and why the markets, other states, and international institutions can do little to constrain Europe’s global regulatory power. AUTHOR—Professor of Law, Columbia Law School. Helpful comments were provided by Lucas Bergkamp, George Bermann, Travis Bradford, Rachel Brewster, Tim Buthe, Grainne DeBurca, Lee Fennell, Jacob Gersen, Tom Ginsburg, Victor Goldberg, Michael Graetz, Todd Hendserson, Aziz Huq, Suzanne Kingston, Katerina Linos, Richard McAdams, Jay Modrall, Henry Monaghan, Jide Nzelibe, Nathaniel Persily, Katharina Pistor, Eric Posner, Tonya Putnam, Charles Sabel, Joanne Scott, Anne-Marie Slaughter, and David Vogel, as well as the participants of the workshops held at Columbia Law School, Duke Law School, University of Chicago Law School, and the University of Florence. -

Upholding Citizens' Privacy in the Use Of
Pace Law Review Volume 37 Issue 1 Fall 2016 Article 10 March 2017 Upholding Citizens’ Privacy in the Use of Stingray Technology: Is New York Behind? Samantha Hazen Elisabeth Haub School of Law at Pace University, [email protected] Follow this and additional works at: https://digitalcommons.pace.edu/plr Part of the Communications Law Commons, Criminal Law Commons, Fourth Amendment Commons, Science and Technology Law Commons, and the State and Local Government Law Commons Recommended Citation Samantha Hazen, Upholding Citizens’ Privacy in the Use of Stingray Technology: Is New York Behind?, 37 Pace L. Rev. 352 (2017) Available at: https://digitalcommons.pace.edu/plr/vol37/iss1/10 This Article is brought to you for free and open access by the School of Law at DigitalCommons@Pace. It has been accepted for inclusion in Pace Law Review by an authorized administrator of DigitalCommons@Pace. For more information, please contact [email protected]. Upholding Citizens’ Privacy in the Use of Stingray Technology: Is New York Behind? Samantha Hazen* I. Introduction The word “Stingray” likely does not resonate with citizens as something other than a marine animal. But in the realm of privacy, the word carries a much different (perhaps more dangerous) meaning. Stingray devices belong to a family of cell-site simulators that track a cell phone user’s location.1 Federal, state, and local agencies purchase these devices and use them during investigations to pinpoint a suspect’s location.2 The devices—which are the size of a briefcase—act as cell phone towers and gather enough identifying information to locate the suspect.3 Despite its obvious advantage of promoting security, the technology also plays a controversial role: detecting and tracking cell phones besides the suspect’s.4 The idea of tracking multiple cell phones in a given region raises privacy * J.D. -
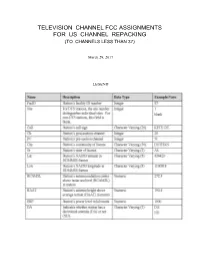
Television Channel Fcc Assignments for Us Channel Repacking (To Channels Less Than 37)
TELEVISION CHANNEL FCC ASSIGNMENTS FOR US CHANNEL REPACKING (TO CHANNELS LESS THAN 37) March 29, 2017 LEGEND FINAL TELEVISION CHANNEL ASSIGNMENT INFORMATION RELATED TO INCENTIVE AUCTION REPACKING Technical Parameters for Post‐Auction Table of Allotments NOTE: These results are based on the 20151020UCM Database, 2015Oct_132Settings.xml study template, and TVStudy version 1.3.2 (patched) FacID Site Call Ch PC City St Lat Lon RCAMSL HAAT ERP DA AntID Az 21488 KYES‐TV 5 5 ANCHORAGE AK 612009 1493055 614.5 277 15 DA 93311 0 804 KAKM 8 8 ANCHORAGE AK 612520 1495228 271.2 240 50 DA 67943 0 10173 KTUU‐TV 10 10 ANCHORAGE AK 612520 1495228 271.2 240 50 DA 89986 0 13815 KYUR 12 12 ANCHORAGE AK 612520 1495228 271.2 240 41 DA 68006 0 35655 KTBY 20 20 ANCHORAGE AK 611309 1495332 98 45 234 DA 90682 0 49632 KTVA 28 28 ANCHORAGE AK 611131 1495409 130.6 60.6 28.9 DA 73156 0 25221 KDMD 33 33 ANCHORAGE AK 612009 1493056 627.9 300.2 17.2 DA 102633 0 787 KCFT‐CD 35 35 ANCHORAGE AK 610400 1494444 539.7 0 15 DA 109112 315 64597 KFXF 7 7 FAIRBANKS AK 645518 1474304 512 268 6.1 DA 91018 0 69315 KUAC‐TV 9 9 FAIRBANKS AK 645440 1474647 432 168.9 30 ND 64596 K13XD‐D 13 13 FAIRBANKS AK 645518 1474304 521.6 0 3 DA 105830 170 13813 KATN 18 18 FAIRBANKS AK 645518 1474258 473 230 16 ND 49621 KTVF 26 26 FAIRBANKS AK 645243 1480323 736 471 27 DA 92468 110 8651 KTOO‐TV 10 10 JUNEAU AK 581755 1342413 37 ‐363 1 ND 13814 KJUD 11 11 JUNEAU AK 581804 1342632 82 ‐290 0.14 DA 78617 0 60520 KUBD 13 13 KETCHIKAN AK 552058 1314018 100 ‐71 0.413 DA 104820 0 20015 KJNP‐TV 20 20 NORTH