Bash/Unix Command Cheat Sheet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
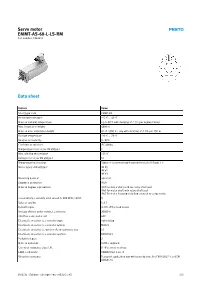
Servo Motor EMMT-AS-60-L-LS-RM Part Number: 5242213
Servo motor EMMT-AS-60-L-LS-RM Part number: 5242213 Data sheet Feature Value Short type code EMMT-AS Ambient temperature -15 °C ... 40 °C Note on ambient temperature Up to 80°C with derating of -1.5% per degree Celsius Max. installation height 4000 m Note on max. installation height As of 1,000 m: only with derating of -1.0% per 100 m Storage temperature -20 °C ... 70 °C Relative air humidity 0 - 90% Conforms to standard IEC 60034 Temperature class as per EN 60034-1 F Max. winding temperature 155 °C Rating class as per EN 60034-1 S1 Temperature monitoring Digital motor temperature transmission via EnDat® 2.2 Motor type to EN 60034-7 IM B5 IM V1 IM V3 Mounting position optional Degree of protection IP40 Note on degree of protection IP40 for motor shaft without rotary shaft seal IP65 for motor shaft with rotary shaft seal IP67 for motor housing including connection components Concentricity, coaxiality, axial runout to DIN SPEC 42955 N Balance quality G 2.5 Detent torque <1.0% of the peak torque Storage lifetime under nominal conditions 20000 h Interface code, motor out 60P Electrical connection 1, connection type Hybrid plug Electrical connection 1, connector system M23x1 Electrical connection 1, number of connections/cores 15 Electrical connection 1, connection pattern 00995913 Pollution degree 2 Note on materials RoHS-compliant Corrosion resistance class CRC 0 - No corrosion stress LABS-Conformity VDMA24364 zone III Vibration resistance Transport application test with severity level 2 to FN 942017-4 and EN 60068-2-6 10/2/21 - Subject to change - Festo AG & Co. -

MASTERCLASS GNUPG MASTERCLASS You Wouldn’T Want Other People Opening Your Letters and BEN EVERARD Your Data Is No Different
MASTERCLASS GNUPG MASTERCLASS You wouldn’t want other people opening your letters and BEN EVERARD your data is no different. Encrypt it today! SECURE EMAIL WITH GNUPG AND ENIGMAIL Send encrypted emails from your favourite email client. our typical email is about as secure as a The first thing that you need to do is create a key to JOHN LANE postcard, which is good news if you’re a represent your identity in the OpenPGP world. You’d Ygovernment agency. But you wouldn’t use a typically create one key per identity that you have. postcard for most things sent in the post; you’d use a Most people would have one identity, being sealed envelope. Email is no different; you just need themselves as a person. However, some may find an envelope – and it’s called “Encryption”. having separate personal and professional identities Since the early 1990s, the main way to encrypt useful. It’s a personal choice, but starting with a single email has been PGP, which stands for “Pretty Good key will help while you’re learning. Privacy”. It’s a protocol for the secure encryption of Launch Seahorse and click on the large plus-sign email that has since evolved into an open standard icon that’s just below the menu. Select ‘PGP Key’ and called OpenPGP. work your way through the screens that follow to supply your name and email address and then My lovely horse generate the key. The GNU Privacy Guard (GnuPG), is a free, GPL-licensed You can, optionally, use the Advanced Key Options implementation of the OpenPGP standard (there are to add a comment that can help others identify your other implementations, both free and commercial – key and to select the cipher, its strength and set when the PGP name now refers to a commercial product the key should expire. -

DC Console Using DC Console Application Design Software
DC Console Using DC Console Application Design Software DC Console is easy-to-use, application design software developed specifically to work in conjunction with AML’s DC Suite. Create. Distribute. Collect. Every LDX10 handheld computer comes with DC Suite, which includes seven (7) pre-developed applications for common data collection tasks. Now LDX10 users can use DC Console to modify these applications, or create their own from scratch. AML 800.648.4452 Made in USA www.amltd.com Introduction This document briefly covers how to use DC Console and the features and settings. Be sure to read this document in its entirety before attempting to use AML’s DC Console with a DC Suite compatible device. What is the difference between an “App” and a “Suite”? “Apps” are single applications running on the device used to collect and store data. In most cases, multiple apps would be utilized to handle various operations. For example, the ‘Item_Quantity’ app is one of the most widely used apps and the most direct means to take a basic inventory count, it produces a data file showing what items are in stock, the relative quantities, and requires minimal input from the mobile worker(s). Other operations will require additional input, for example, if you also need to know the specific location for each item in inventory, the ‘Item_Lot_Quantity’ app would be a better fit. Apps can be used in a variety of ways and provide the LDX10 the flexibility to handle virtually any data collection operation. “Suite” files are simply collections of individual apps. Suite files allow you to easily manage and edit multiple apps from within a single ‘store-house’ file and provide an effortless means for device deployment. -

FAKULT¨AT F¨UR INFORMATIK Cryogenic Enabling Power-Aware
FAKULTAT¨ FUR¨ INFORMATIK DER TECHNISCHEN UNIVERSITAT¨ MUNCHEN¨ Masterarbeit in Informatik Cryogenic Enabling Power-Aware Applications on Linux Alejandra Morales Ruiz FAKULTAT¨ FUR¨ INFORMATIK DER TECHNISCHEN UNIVERSITAT¨ MUNCHEN¨ Masterarbeit in Informatik Cryogenic Enabling Power-Aware Applications on Linux Cryogenic Ein Linux Kernel-Modul fur¨ Kooperatives Energiesparen Author: Alejandra Morales Ruiz Supervisor: Dr. Christian Grothoff Date: February 17, 2014 Ich versichere, dass ich dieses Master-Thesis selbstandig¨ verfasst und nur die angegebe- nen Quellen und Hilfsmittel verwendet habe. I assure the single handed composition of this master’s thesis only supported by declared resources. Munich, February 17, 2014 Alejandra Morales Ruiz Acknowledgments I want to thank Christian Grothoff for giving me the opportunity to write this thesis as well as for the support and advice given throughout its completion. I also thank the people at the Chair for Robotics and Embedded Systems, especially Reinhard Lafrenz and Steffen Wittmeier, who allowed me to access their laboratory and provided me with the necessary equipment to perform the energy measurements. Thanks to Danny Hughes and Wilfried Daniels, from the Katholieke Universiteit Leuven, for their advice and contributions to the experimentation and the subsequent results of this work. I would also like to express my gratitude to the whole community of Linux developers for sharing their knowledge and experience on the Internet, which has helped me not only during this thesis, but during all my studies. Finally, I would like to thank my parents and brothers, who always supported and en- couraged me to finish my studies abroad, and my partner, Angel,´ because this thesis would have never been possible without him. -
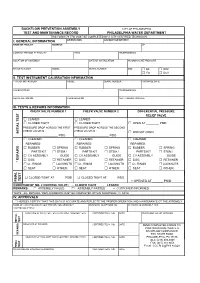
BFP Test Form
BACKFLOW PREVENTION ASSEMBLY CITY OF PHILADELPHIA TEST AND MAINTENANCE RECORD PHILADELPHIA WATER DEPARTMENT THIS FORM (79-770) MUST BE COMPLETED BY A CITY CERTIFIED TECHNICIAN I. GENERAL INFORMATION ORIENTATION ACCOUNT OR METER # NAME OF FACILITY ADDRESS ZIP CONTACT PERSON AT FACILITY TITLE TELEPHONE NO. LOCATION OF ASSEMBLY DATE OF INSTALLATION INCOMING LINE PRESSURE MANUFACTURER MODEL SERIAL NUMBER SIZE □ DS □ RPZ □ FS □ DCV II. TEST INSTRUMENT CALIBRATION INFORMATION TYPE OF INSTRUMENT MODEL SERIAL NUMBER PURCHASE DATE CALIBRATED BY TELEPHONE NO. REGISTRATION NO. CALIBRATED ON NEXT CALIBRATION DUE III. TESTS & REPAIRS INFORMATION CHECK VALVE NUMBER 1 CHECK VALVE NUMBER 2 DIFFERENTIAL PRESSURE RELIEF VALVE □ LEAKED □ LEAKED □ CLOSED TIGHT □ CLOSED TIGHT □ OPEN AT ________ PSID PRESSURE DROP ACROSS THE FIRST PRESSURE DROP ACROSS THE SECOND CHECK VALVE IS : CHECK VALVE IS : INITIAL TEST INITIAL □ DID NOT OPEN ______________________ PSID ______________________ PSID □ CLEANED □ CLEANED □ CLEANED REPAIRED: REPAIRED: REPAIRED: □ RUBBER □ SPRING □ RUBBER □ SPRING □ RUBBER □ SPRING PARTS KIT □ STEM / PARTS KIT □ STEM / PARTS KIT □ STEM / □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ DISC □ RETAINER □ DISC □ RETAINER □ DISC □ RETAINER * REPAIRS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ SEAT □ OTHER: □ SEAT □ OTHER: □ SEAT □ OTHER: □ CLOSED TIGHT AT ______ PSID □ CLOSED TIGHT AT ______ PSID TEST FINAL FINAL □ OPENED AT ______ PSID CONDITION OF NO. 2 CONTROL VALVE : □ CLOSED TIGHT □ LEAKED REMARKS : □ ASSEMBLY FAILED □ ASSEMBLY PASSED □ CUSTOMER INFORMED *NOTE : ALL REPAIRS / REPLACEMENTS MUST BE COMPLETED WITHIN FOURTEEN (14) DAYS IV. APPROVALS * I HEREBY CERTIFY THAT THIS DATA IS ACCURATE AND REFLECTS THE PROPER OPERATION AND MAINTENANCE OT THE ASSEMBLY NAME OF CERTIFIED BACKFLOW PREVENTION ASSEMBLY BUSINESS TELEPHONE NO. -

BIMM 143 Introduction to UNIX
BIMM 143 Introduction to UNIX Barry Grant http://thegrantlab.org/bimm143 Do it Yourself! Lets get started… Mac Terminal PC Git Bash SideNote: Terminal vs Shell • Shell: A command-line interface that allows a user to Setting Upinteract with the operating system by typing commands. • Terminal [emulator]: A graphical interface to the shell (i.e. • Mac users: openthe a window Terminal you get when you launch Git Bash/iTerm/etc.). • Windows users: install MobaXterm and then open a terminal Shell prompt Introduction To Barry Grant Introduction To Shell Barry Grant Do it Yourself! Print Working Directory: a.k.a. where the hell am I? This is a comment line pwd This is our first UNIX command :-) Don’t type the “>” bit it is the “shell prompt”! List out the files and directories where you are ls Q. What do you see after each command? Q. Does it make sense if you compare to your Mac: Finder or Windows: File Explorer? On Mac only :( open . Note the [SPACE] is important Download any file to your current directory/folder curl -O https://bioboot.github.io/bggn213_S18/class-material/bggn213_01_unix.zip curl -O https://bioboot.github.io/bggn213_S18/class-material/bggn213_01_unix.zip ls unzip bggn213_01_unix.zip Q. Does what you see at each step make sense if you compare to your Mac: Finder or Windows: File Explorer? Download any file to your current directory/folder curl -O https://bioboot.github.io/bggn213_S18/class-material/bggn213_01_unix.zip List out the files and directories where you are (NB: Use TAB for auto-complete) ls bggn213_01_unix.zip Un-zip your downloaded file unzip bggn213_01_unix.zip curlChange -O https://bioboot.github.io/bggn213_S18/class-material/bggn213_01_unix.zip directory (i.e. -

Cluster Generate — Generate Grouping Variables from a Cluster Analysis
Title stata.com cluster generate — Generate grouping variables from a cluster analysis Description Quick start Menu Syntax Options Remarks and examples Also see Description cluster generate creates summary or grouping variables from a hierarchical cluster analysis; the result depends on the function. A single variable may be created containing a group number based on the requested number of groups or cutting the dendrogram at a specified (dis)similarity value. A set of new variables may be created if a range of group sizes is specified. Users can add more cluster generate functions; see[ MV] cluster programming subroutines. Quick start Generate grouping variable g5 with 5 groups from the most recent cluster analysis cluster generate g5 = groups(5) As above, 4 grouping variables (g4, g5, g6, and g7) with 4, 5, 6, and 7 groups cluster generate g = groups(4/7) As above, but use the cluster analysis named myclus cluster generate g = groups(4/7), name(myclus) Generate grouping variable mygroups from the most recent cluster analysis by cutting the dendrogram at dissimilarity value 38 cluster generate mygroups = cut(38) Menu Statistics > Multivariate analysis > Cluster analysis > Postclustering > Summary variables from cluster analysis 1 2 cluster generate — Generate grouping variables from a cluster analysis Syntax Generate grouping variables for specified numbers of clusters cluster generate newvar j stub = groups(numlist) , options Generate grouping variable by cutting the dendrogram cluster generate newvar = cut(#) , name(clname) option Description name(clname) name of cluster analysis to use in producing new variables ties(error) produce error message for ties; default ties(skip) ignore requests that result in ties ties(fewer) produce results for largest number of groups smaller than your request ties(more) produce results for smallest number of groups larger than your request Options name(clname) specifies the name of the cluster analysis to use in producing the new variables. -

Installing Freepbx 13 on Centos 7
Installing FreePBX 13 on CentOS 7 READ FIRST Manual installations of FreePBX is considered an EXPERTS ONLY exercise. This method of installation is enough to get CORE functionality of FreePBX. Non-commercial modules may not function as expected or detailed in the Wiki's. Certain modules and features may require additional software to be installed and configured on the server. **** COMMERCIAL MODULES CANNOT BE INSTALLED ON THIS OS **** Install Centos 7 **** COMMERCIAL MODULES CANNOT BE INSTALLED ON THIS OS **** Install Centos 7 Initial System Setup Disable selinux Update Your System Install Additional Required Dependencies Install Legacy Pear requirements Firewalld Basic Configuration Enable and Start MariaDB Enable and Start Apache Install Dependencies for Google Voice (if required) Install iksemel Add the Asterisk User Install and Configure Asterisk Download Asterisk source files. Compile and install DAHDI Compile and install pjproject Compile and Install jansson Compile and install Asterisk Install Asterisk Soundfiles. Set Asterisk ownership permissions. Install and Configure FreePBX A few small modifications to Apache. Download and install FreePBX. That's it! Automatic Startup Initial System Setup You MUST run all of these commands as the root user! You MUST disable selinux. selinux can cause strange behavior during the install Disable selinux In /etc/sysconfig/selinux , change the following lines: sed -i 's/\(^SELINUX=\).*/\SELINUX=disabled/' /etc/sysconfig/selinux sed -i 's/\(^SELINUX=\).*/\SELINUX=disabled/' /etc/selinux/config reboot, -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Student Number: Surname: Given Name
Computer Science 2211a Midterm Examination Sample Solutions 9 November 20XX 1 hour 40 minutes Student Number: Surname: Given name: Instructions/Notes: The examination has 35 questions on 9 pages, and a total of 110 marks. Put all answers on the question paper. This is a closed book exam. NO ELECTRONIC DEVICES OF ANY KIND ARE ALLOWED. 1. [4 marks] Which of the following Unix commands/utilities are filters? Correct answers are in blue. mkdir cd nl passwd grep cat chmod scriptfix mv 2. [1 mark] The Unix command echo HOME will print the contents of the environment variable whose name is HOME. True False 3. [1 mark] In C, the null character is another name for the null pointer. True False 4. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod a=x abc.dat is equivalent to the command: a. chmod 755 abc.dat b. chmod 711 abc.dat c. chmod 155 abc.dat d. chmod 111 abc.dat e. none of the above 5. [3 marks] The protection code for the file abc.dat is currently –rwxr--r-- . The command chmod ug+w abc.dat is equivalent to the command: a. chmod 766 abc.dat b. chmod 764 abc.dat c. chmod 754 abc.dat d. chmod 222 abc.dat e. none of the above 2 6. [3 marks] The protection code for def.dat is currently dr-xr--r-- , and the protection code for def.dat/ghi.dat is currently -r-xr--r-- . Give one or more chmod commands that will set the protections properly so that the owner of the two files will be able to delete ghi.dat using the command rm def.dat/ghi.dat chmod u+w def.dat or chmod –r u+w def.dat 7. -

Emacspeak User's Guide
Emacspeak User's Guide Jennifer Jobst Revision History Revision 1.3 July 24,2002 Revised by: SDS Updated the maintainer of this document to Sharon Snider, corrected links, and converted to HTML Revision 1.2 December 3, 2001 Revised by: JEJ Changed license to GFDL Revision 1.1 November 12, 2001 Revised by: JEJ Revision 1.0 DRAFT October 19, 2001 Revised by: JEJ This document helps Emacspeak users become familiar with Emacs as an audio desktop and provides tutorials on many common tasks and the Emacs applications available to perform those tasks. Emacspeak User's Guide Table of Contents 1. Legal Notice.....................................................................................................................................................1 2. Introduction.....................................................................................................................................................2 2.1. What is Emacspeak?.........................................................................................................................2 2.2. About this tutorial.............................................................................................................................2 3. Before you begin..............................................................................................................................................3 3.1. Getting started with Emacs and Emacspeak.....................................................................................3 3.2. Emacs Command Conventions.........................................................................................................3 -

GNU Wget 1.10 the Non-Interactive Download Utility Updated for Wget 1.10, Apr 2005
GNU Wget 1.10 The non-interactive download utility Updated for Wget 1.10, Apr 2005 by Hrvoje Nikˇsi´cand the developers Copyright c 1996–2005, Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with the Invariant Sections being “GNU General Public License” and “GNU Free Documentation License”, with no Front-Cover Texts, and with no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”. Chapter 1: Overview 1 1 Overview GNU Wget is a free utility for non-interactive download of files from the Web. It supports http, https, and ftp protocols, as well as retrieval through http proxies. This chapter is a partial overview of Wget’s features. • Wget is non-interactive, meaning that it can work in the background, while the user is not logged on. This allows you to start a retrieval and disconnect from the system, letting Wget finish the work. By contrast, most of the Web browsers require constant user’s presence, which can be a great hindrance when transferring a lot of data. • Wget can follow links in html and xhtml pages and create local versions of remote web sites, fully recreating the directory structure of the original site. This is sometimes referred to as “recursive downloading.” While doing that, Wget respects the Robot Exclusion Standard (‘/robots.txt’). Wget can be instructed to convert the links in downloaded html files to the local files for offline viewing.