Microsoft Windows Server 2012 R2 Benchmark
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Bitmap Graphics Model - Device Context • Windows Does Not Retain a Copy of What the Application Drew • Windows 3.0 (1990)
historie 08.11.2018 vjj 1 pravěk INPUT PROGRAM OUTPUT 08.11.2018 vjj 2 evoluce • dávkové zpracování • interaktivní práce • prompt • GUI 08.11.2018 vjj 3 evoluce INPUT PROGRAM OUTPUT 08.11.2018 vjj 4 evoluce Windows • bitmap graphics model - Device Context • Windows does not retain a copy of what the application drew • Windows 3.0 (1990) • bitmap graphics model - layered Device Context • Windows does retain a copy of the drawing as a bitmap • Windows 2000 (beta 1998) • .NET Framework (2001-2005) • vector graphics model – WPF (on DirectX) • tree of user-interface elements with objects representing graphical shapes • Windows Vista, .NET Framework 3.0 (2006) • Metro - deterioration • Windows 8, .NET Framework 4.5 (2012) 08.11.2018 vjj 5 1: Win32 API classique 08.11.2018 vjj 6 Uživatel Fronta zpráv GetMessage (mouse, keyboard) hardware interrupt DRIVER DispatchMessage System message queue WindowProc WindowProc RIT Raw Input Thread Fronta zpráv 8.11.18 vjj 7 WM_PAINT • každý ovládací prvek je samostatným oknem s vlastní procedurou na zpracovávání zpráv • celá stavba programu/algoritmu se točila kolem přípravy dat pro vykreslení obsahu okna vždy, když přišla zpráva WM_PAINT (a že chodila často) • během přímého kreslení se výstup do momentálně neviditelné části okna nikam nezapsal 08.11.2018 vjj 8 User Windows OS Invalidate... Program WM_PAINT GetDC Program Funkce GDI32 / GDI+ Graphics Card Frame Buffer for Screen Image data only retained as long as it remains visible on screen 08.11.2018 vjj 9 PROGRAM: direct Device Context OUTPUT PROGRAM PROGRAM PROGRAM PROGRAM PROGRAM WM_PAINT WM_PAINT WM_PAINT WM_PAINT WM_PAINT 08.11.2018 vjj 10 standardní funkce • TextOut • MoveToEx DrawText LineTo Rectangle Ellipse • DrawIcon Pie Arc Chord Polyline • BitBlt Polygon stretchBlt 08.11.2018 vjj 11 Device Context • standardní funkce pro kreslení do okna vyžadují hDC jako svůj první parametr • datová struktura popisující vlastnosti výstupu, např. -

Using Remote Desktop Services with Ifix 1
Proficy iFIX 6.5 Using Remote Desktop Services GE Digital Proficy Historian and Operations Hub: Data Analysis in Context 1 Proprietary Notice The information contained in this publication is believed to be accurate and reliable. However, General Electric Company assumes no responsibilities for any errors, omissions or inaccuracies. Information contained in the publication is subject to change without notice. No part of this publication may be reproduced in any form, or stored in a database or retrieval system, or transmitted or distributed in any form by any means, electronic, mechanical photocopying, recording or otherwise, without the prior written permission of General Electric Company. Information contained herein is subject to change without notice. © 2021, General Electric Company. All rights reserved. Trademark Notices GE, the GE Monogram, and Predix are either registered trademarks or trademarks of General Electric Company. Microsoft® is a registered trademark of Microsoft Corporation, in the United States and/or other countries. All other trademarks are the property of their respective owners. We want to hear from you. If you have any comments, questions, or suggestions about our documentation, send them to the following email address: [email protected] Table of Contents Using Remote Desktop Services with iFIX 1 Reference Documents 1 Introduction to Remote Desktop Services 2 Using iClientTS 2 Understanding the iFIX and Remote Desktop Services 3 File System Support 5 Where to Find More Information on Remote Desktop Services 5 Getting -

Word Processing Tool
WORD PROCESSING 3 TOOL Objectives I like the computer because it keeps giving you After completing this Chapter, the options. What if I do this? You try it, and if you student will be able to: don't like it you undo it. The original can always be resurrected. It raises the idea of working on • work with any word processing program, one painting your whole life, saving it and working on it again and again. • create, save and open a Elliott Green document using a word Research Associate and Tutorial Fellow, Oxford University processor, • format a document inserting bullets/numbering, tables, pictures, etc., Introduction • set custom tabs and apply styles, We have to submit a project as part of our course • prepare a document for printing, evaluation. We will perhaps take a chart paper • enhance the features of the and design the project, write a report and submit document inserting graphics, it to our teacher. That’s the way we have done it tables, pictures, charts, etc., and all along? Have we ever thought of typing the entire using different formatting styles, project report using a computer and submitting it • modify document using various in a nicely designed printed form? Ever reflected editing and formatting features on getting information from the Internet and within or across documents, presenting it neatly for the project? Now that’s • produce documents for various the way things are being done! And if we are already purposes and thinking of it, it’s time to discover some document creation software, i.e., word processing tool to get • apply mail merge facility to send a document to different the job done. -

Adobe Introduction to Scripting
ADOBE® INTRODUCTION TO SCRIPTING © Copyright 2007 Adobe Systems Incorporated. All rights reserved. Adobe® Introduction to Scripting NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. The software described in this document is furnished under license and may only be used or copied in accordance with the terms of such license. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and non-infringement of third-party rights. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe®, the Adobe logo, Illustrator®, InDesign®, and Photoshop® are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple®, Mac OS®, and Macintosh® are trademarks of Apple Computer, Inc., registered in the United States and other countries. Microsoft®, and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. JavaScriptTM and all Java-related marks are trademarks or registered trademarks of Sun Microsystems, Inc. -

Scala Infochannel Player Setup Guide
SETUP GUIDE P/N: D40E04-01 Copyright © 1993-2002 Scala, Inc. All rights reserved. No part of this publication, nor any parts of this package, may be copied or distributed, transmitted, transcribed, recorded, photocopied, stored in a retrieval system, or translated into any human or computer language, in any form or by any means, electronic, mechanical, magnetic, manual, or otherwise, or disclosed to third parties without the prior written permission of Scala Incorporated. TRADEMARKS Scala, the exclamation point logo, and InfoChannel are registered trademarks of Scala, Inc. All other trademarks or registered trademarks are the sole property of their respective companies. The following are trademarks or registered trademarks of the companies listed, in the United States and other countries: Microsoft, MS-DOS, Windows, Windows 95, Windows 98, Windows NT, Windows 2000, Windows XP, DirectX, DirectDraw, DirectSound, ActiveX, ActiveMovie, Internet Explorer, Outlook Express: Microsoft Corporation IBM, IBM-PC: International Business Machines Corporation Intel, Pentium, Indeo: Intel Corporation Adobe, the Adobe logo, Adobe Type Manager, Acrobat, ATM, PostScript: Adobe Systems Incorporated TrueType, QuickTime, Macintosh: Apple Computer, Incorporated Agfa: Agfa-Gevaert AG, Agfa Division, Bayer Corporation “Segoe” is a trademark of Agfa Monotype Corporation. “Flash” and “Folio” are trademarks of Bauer Types S.A. Some parts are derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm. JPEG file handling is based in part on the work of the Independent JPEG Group. Lexsaurus Speller Technology Copyright © 1992, 1997 by Lexsaurus Software Inc. All rights reserved. TIFF-LZW and/or GIF-LZW: Licensed under Unisys Corporation US Patent No. 4,558,302; End-User use restricted to use on only a single personal computer or workstation which is not used as a server. -

Login with Amazon Developer Guide for Websites
Login with Amazon Developer Guide for Websites Login with Amazon: Developer Guide for Websites Copyright © 2017 Amazon Services, LLC or its affiliates. All rights reserved. Amazon and the Amazon logo are trademarks of Amazon.com, Inc. or its affiliates. All other trademarks not owned by Amazon are the property of their respective owners Contents Welcome .................................................................................................................................................. 2 How Do I...? .............................................................................................................................................. 2 Understanding Login with Amazon ........................................................................................................... 3 Login with Amazon Conceptual Overview ................................................................................................. 4 Single Sign-On (SSO) for Web ................................................................................................................. 6 Single Sign-On (SSO) for Mobile ............................................................................................................. 7 Access Token ............................................................................................................................................ 7 Authorization Code ................................................................................................................................... 7 Refresh Token .......................................................................................................................................... -
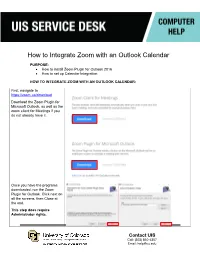
How to Integrate Zoom with an Outlook Calendar
How to Integrate Zoom with an Outlook Calendar PURPOSE: • How to install Zoom Plugin for Outlook 2016 • How to set up Calendar Integration HOW TO INTEGRATE ZOOM WITH AN OUTLOOK CALENDAR: First, navigate to https://zoom.us/download Download the Zoom Plugin for Microsoft Outlook, as well as the zoom client for Meetings if you do not already have it. Once you have the programs downloaded, run the Zoom Plugin for Outlook. Click next on all the screens, then Close at the end. This step does require Administrator rights. Contact UIS Call: (303) 860-4357 Email: [email protected] Restart Outlook, then you will see it in the top menu. Next, navigate to https://cusystem.zoom.us, choose SSO and login with your CU credentials Contact UIS Call: (303) 860-4357 Email: [email protected] On the left side, choose My Meeting Settings Under My Meeting Settings, scroll down until you find Calendar Integration. Click the toggle on the right side. Under Calendar Integration, for the Exchange login username or UPN enter your CU username followed by @ad.cu.edu. Under password, enter your CU password. For Exchange version, select Exchange 2013. In the EWS URL, enter https://exchange.cu.edu/ EWS/Exchange.asmx After that, click Authorize and you should be set! Keep in mind this isn’t a perfect integration, it will only create new meetings for meetings created after this has been done, and changing or deleting meetings will not necessarily reflect in Outlook. The Zoom desktop client will be the best place to check for updated meetings. -

Deploying Microsoft Windows Server Update Services
Deploying Microsoft Windows Server Update Services Microsoft Corporation Published: June 3, 2005 Author: Tim Elhajj Editor: Sean Bentley Abstract This paper describes how to deploy Microsoft® Windows Server™ Update Services (WSUS). You will find a comprehensive description of how WSUS functions, as well as descriptions of WSUS scalability and bandwidth management features. This paper also offers step-by-step procedures for installation and configuration of the WSUS server. You will read how to update and configure Automatic Updates on client workstations and servers that will be updated by WSUS. Also included are steps for migrating from Microsoft Software Update Services (SUS) to WSUS, as well as steps for setting up a WSUS server on an isolated segment of your network and manually importing updates. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This White Paper is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. -

Microsoft DNS
1 a. Domain Name Service (DNS) encompassing Microsoft DNS From Wikipedia, the free encyclopedia Jump to: navigation, search Microsoft DNS is the name given to the implementation of domain name system services provided in Microsoft Windows operating systems. Contents [hide] 1 Overview 2 DNS lookup client o 2.1 The effects of running the DNS Client service o 2.2 Differences from other systems 3 Dynamic DNS Update client 4 DNS server o 4.1 Common issues 5 See also 6 References 7 External links [edit] Overview The Domain Name System support in Microsoft Windows NT, and thus its derivatives Windows 2000, Windows XP, and Windows Server 2003, comprises two clients and a server. Every Microsoft Windows machine has a DNS lookup client, to perform ordinary DNS lookups. Some machines have a Dynamic DNS client, to perform Dynamic DNS Update transactions, registering the machines' names and IP addresses. Some machines run a DNS server, to publish DNS data, to service DNS lookup requests from DNS lookup clients, and to service DNS update requests from DNS update clients. The server software is only supplied with the server versions of Windows. [edit] DNS lookup client Applications perform DNS lookups with the aid of a DLL. They call library functions in the DLL, which in turn handle all communications with DNS servers (over UDP or TCP) and return the final results of the lookup back to the applications. 2 Microsoft's DNS client also has optional support for local caching, in the form of a DNS Client service (also known as DNSCACHE). Before they attempt to directly communicate with DNS servers, the library routines first attempt to make a local IPC connection to the DNS Client service on the machine. -

Open Search Environments: the Free Alternative to Commercial Search Services
Open Search Environments: The Free Alternative to Commercial Search Services. Adrian O’Riordan ABSTRACT Open search systems present a free and less restricted alternative to commercial search services. This paper explores the space of open search technology, looking in particular at lightweight search protocols and the issue of interoperability. A description of current protocols and formats for engineering open search applications is presented. The suitability of these technologies and issues around their adoption and operation are discussed. This open search approach is especially useful in applications involving the harvesting of resources and information integration. Principal among the technological solutions are OpenSearch, SRU, and OAI-PMH. OpenSearch and SRU realize a federated model to enable content providers and search clients communicate. Applications that use OpenSearch and SRU are presented. Connections are made with other pertinent technologies such as open-source search software and linking and syndication protocols. The deployment of these freely licensed open standards in web and digital library applications is now a genuine alternative to commercial and proprietary systems. INTRODUCTION Web search has become a prominent part of the Internet experience for millions of users. Companies such as Google and Microsoft offer comprehensive search services to users free with advertisements and sponsored links, the only reminder that these are commercial enterprises. Businesses and developers on the other hand are restricted in how they can use these search services to add search capabilities to their own websites or for developing applications with a search feature. The closed nature of the leading web search technology places barriers in the way of developers who want to incorporate search functionality into applications. -

Guidelines for Designing Embedded Systems with Windows 10 Iot Enterprise
Guidelines for Designing Embedded Systems with Windows 10 IoT Enterprise Version 2.0 Published July 15, 2016 Guidelines for designing embedded systems 1 CONFIDENTIAL Contents Overview .................................................................................................................................................................................................... 4 Building a task-specific experience ............................................................................................................................................ 4 General Group Policy settings ....................................................................................................................................................... 4 Application control ................................................................................................................................................................................ 5 Application boot options ................................................................................................................................................................. 5 Auto-boot Universal Windows apps ...................................................................................................................................... 5 Auto-boot Classic Windows apps ........................................................................................................................................... 5 Limit application access with AppLocker ............................................................................................................................... -
Using a Remote Desktop Connection with Filemaker Pro 12 © 2007–2012 Filemaker, Inc
FileMaker® Pro 12 Using a Remote Desktop Connection with FileMaker Pro 12 © 2007–2012 FileMaker, Inc. All Rights Reserved. FileMaker, Inc. 5201 Patrick Henry Drive Santa Clara, California 95054 FileMaker and Bento are trademarks of FileMaker, Inc. registered in the U.S. and other countries. The file folder logo and the Bento logo are trademarks of FileMaker, Inc. All other trademarks are the property of their respective owners. FileMaker documentation is copyrighted. You are not authorized to make additional copies or distribute this documentation without written permission from FileMaker. You may use this documentation solely with a valid licensed copy of FileMaker software. All persons, companies, email addresses, and URLs listed in the examples are purely fictitious and any resemblance to existing persons, companies, email addresses, or URLs is purely coincidental. Credits are listed in the Acknowledgements documents provided with this software. Mention of third-party products and URLs is for informational purposes only and constitutes neither an endorsement nor a recommendation. FileMaker, Inc. assumes no responsibility with regard to the performance of these products. For more information, visit our website at http://www.filemaker.com. Edition: 01 Contents Chapter 1 Introduction to Remote Desktop Services and Citrix XenApp 4 About Remote Desktop Services 4 Remote Desktop Services server 4 Remote Desktop Services client (Remote Desktop Connection) 4 Remote Desktop Protocol (RDP) 4 Benefits of using Remote Desktop Services 4 System