Zero-Day Vulnerability in Desktop Window Manager (CVE-2021-28310) Used in the Wild | Securelist
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Bitmap Graphics Model - Device Context • Windows Does Not Retain a Copy of What the Application Drew • Windows 3.0 (1990)
historie 08.11.2018 vjj 1 pravěk INPUT PROGRAM OUTPUT 08.11.2018 vjj 2 evoluce • dávkové zpracování • interaktivní práce • prompt • GUI 08.11.2018 vjj 3 evoluce INPUT PROGRAM OUTPUT 08.11.2018 vjj 4 evoluce Windows • bitmap graphics model - Device Context • Windows does not retain a copy of what the application drew • Windows 3.0 (1990) • bitmap graphics model - layered Device Context • Windows does retain a copy of the drawing as a bitmap • Windows 2000 (beta 1998) • .NET Framework (2001-2005) • vector graphics model – WPF (on DirectX) • tree of user-interface elements with objects representing graphical shapes • Windows Vista, .NET Framework 3.0 (2006) • Metro - deterioration • Windows 8, .NET Framework 4.5 (2012) 08.11.2018 vjj 5 1: Win32 API classique 08.11.2018 vjj 6 Uživatel Fronta zpráv GetMessage (mouse, keyboard) hardware interrupt DRIVER DispatchMessage System message queue WindowProc WindowProc RIT Raw Input Thread Fronta zpráv 8.11.18 vjj 7 WM_PAINT • každý ovládací prvek je samostatným oknem s vlastní procedurou na zpracovávání zpráv • celá stavba programu/algoritmu se točila kolem přípravy dat pro vykreslení obsahu okna vždy, když přišla zpráva WM_PAINT (a že chodila často) • během přímého kreslení se výstup do momentálně neviditelné části okna nikam nezapsal 08.11.2018 vjj 8 User Windows OS Invalidate... Program WM_PAINT GetDC Program Funkce GDI32 / GDI+ Graphics Card Frame Buffer for Screen Image data only retained as long as it remains visible on screen 08.11.2018 vjj 9 PROGRAM: direct Device Context OUTPUT PROGRAM PROGRAM PROGRAM PROGRAM PROGRAM WM_PAINT WM_PAINT WM_PAINT WM_PAINT WM_PAINT 08.11.2018 vjj 10 standardní funkce • TextOut • MoveToEx DrawText LineTo Rectangle Ellipse • DrawIcon Pie Arc Chord Polyline • BitBlt Polygon stretchBlt 08.11.2018 vjj 11 Device Context • standardní funkce pro kreslení do okna vyžadují hDC jako svůj první parametr • datová struktura popisující vlastnosti výstupu, např. -

Guidelines for Designing Embedded Systems with Windows 10 Iot Enterprise
Guidelines for Designing Embedded Systems with Windows 10 IoT Enterprise Version 2.0 Published July 15, 2016 Guidelines for designing embedded systems 1 CONFIDENTIAL Contents Overview .................................................................................................................................................................................................... 4 Building a task-specific experience ............................................................................................................................................ 4 General Group Policy settings ....................................................................................................................................................... 4 Application control ................................................................................................................................................................................ 5 Application boot options ................................................................................................................................................................. 5 Auto-boot Universal Windows apps ...................................................................................................................................... 5 Auto-boot Classic Windows apps ........................................................................................................................................... 5 Limit application access with AppLocker ............................................................................................................................... -

Mastering Powershellpowershell
CopyrightCopyright © 2009 BBS Technologies ALL RIGHTS RESERVED. No part of this work covered by the copyright herein may be reproduced, transmitted, stored, or used in any form or by any means graphic, electronic, or mechanical, including but not limited to photocopying, recording, scanning, digitizing, taping, Web distribution, information networks, or information storage and retrieval systems except as permitted under Section 107 or 108 of the 1976 United States Copyright Act without the prior written permission of the publisher. For permission to use material from the text please contact Idera at [email protected]. Microsoft® Windows PowerShell® and Microsoft® SQL Server® are registered trademarks of Microsoft Corporation in the United Stated and other countries. All other trademarks are the property of their respective owners. AboutAbout thethe AuthorAuthor Dr. Tobias Weltner is one of the most visible PowerShell MVPs in Europe. He has published more than 80 books on Windows and Scripting Techniques with Microsoft Press and other publishers, is a regular speaker at conferences and road shows and does high level PowerShell and Scripting trainings for companies throughout Europe. He created the powershell.com website and community in an effort to help people adopt and use PowerShell more efficiently. As software architect, he created a number of award-winning scripting tools such as SystemScripter (VBScript), the original PowerShell IDE and PowerShell Plus, a comprehensive integrated PowerShell development system. AcknowledgmentsAcknowledgments First and foremost, I’d like to thank my family who is always a source of inspiration and encouragement. A special thanks to Idera, Rick Pleczko, David Fargo, Richard Giles, Conley Smith and David Twamley for helping to bring this book to the English speaking world. -

Security Policy Page 1 of 20
Security Policy Page 1 of 20 Security Policy This security policy contains data to configure services and network security based on the server’s role, as well as data to configure registry and auditing settings. Server: VENGWIN207 Services Service Name Startup Mode Description Issues, manages, and removes X.509 certificates for such applications such as Active Directory Certificate S/MIME and SSL. If the service is stopped, Disabled Services certificates will not be issued. If this service is disabled, any services that explicitly depend on it will fail to start. AD DS Domain Controller service. If this service is stopped, users will be unable to log Active Directory Domain Services Disabled on to the network. If this service is disabled, any services that explicitly depend on it will fail to start. AD FS Web Agent Authentication The AD FS Web Agent Authentication Service Disabled Service validates incoming tokens and cookies. Adobe Acrobat Updater keeps your Adobe Adobe Acrobat Update Service Automatic software up to date. Sends logging messages to the logging database when logging is enabled for the Active Directory Rights Management Services role. If this service is disabled or stopped AdRmsLoggingService Disabled when logging is enabled, logging messages will be stored in local message queues and sent to the logging database when the service is started. Processes application compatibility cache Application Experience Disabled requests for applications as they are launched Provides administrative services for IIS, for example configuration history and Application Pool account mapping. If this Application Host Helper Service Disabled service is stopped, configuration history and locking down files or directories with Application Pool specific Access Control Entries will not work. -

Windows Tweaks Guide
Windows Tweaks Guide For By Windows Geeks Team Introduction .......................................................................................................................................... 5 Important Notes on This Guide........................................................................................................... 5 Usage Instruction.................................................................................................................................. 5 No Warranty .......................................................................................................................................... 5 Hosting, Distribution & Translation ................................................................................................... 6 Tweaks for Windows XP ...................................................................................................................... 6 Before You Begin Tweaking XP ................................................................................................. 6 Tweaks for Startup ..................................................................................................................... 8 Tweaks for Shutdown .............................................................................................................. 10 Tweaks for Mouse .................................................................................................................... 10 Tweaks for Start Menu ............................................................................................................ -

05 Vcloud Services Consultant
Optimizing Windows for VMware View 4.5 Optimizing Windows for VMware View™ 4.5 (Optimizing Windows 7, Windows Vista and XP) Version 2.0 For use only by VMware PSO and VMware Solution Providers Consulting Service Delivery Aid – Not a Customer Deliverable Optimizing Windows for VMware View 4.5 Version History Date Ver. Author Description Rev iewers February 2011 V2.0 Tim Federwitz Second Release (Added Dav id Richardson, John Windows XP and Vista) Dodge, Matt Coppinger, Matt Wood August 2010 V1.0 Tim Federwitz First Release (Windows 7 John Dodge, Matt only ) Coppinger, Matt Lesak, Ry an Miersma, Justin Venezia © 2011 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. This product is covered by one or more patents listed at http://www.vmware.com/download/patents.html . VMware is a registered trademark or trademark of VMware, Inc. in the United States and/or other jurisdictions. All other marks and names mentioned herein may be trademarks of their respective companies. VMware, Inc 3401 Hillview Ave Palo Alto, CA 94304 www.vmware.com © 2011 VMware, Inc. All rights reserved. Page 2 of 44 Optimizing Windows for VMware View 4.5 Contents 1. Introduction ......................................................................................... 4 1.1 Comparing Default and Optimized Windows 7 Installations ........................................ 4 1.2 How to use this Guide ............................................................................................... 4 2. -

Tweakhound, Windows 7 Beta Default Services
Sheet1 Name Startup Type Adaptive Brightness Manual AppID Service Manual Application Experience Manual Application Information Manual Application Layer Gateway Service Manual Application Management Manual Background Intelligent Transfer Service Automatic (Delayed Start) Base Filtering Engine Automatic BitLocker Drive Encryption Service Manual Block Level Backup Engine Service Manual Bluetooth Support Service Manual BranchCache Manual Certificate Propagation Manual CNG Key Isolation Manual COM+ Event System Automatic COM+ System Application Manual Computer Browser Automatic Credential Manager Service Manual Cryptographic Services Automatic DCOM Server Process Launcher Automatic Desktop Window Manager Session Manager Automatic DHCP Client Automatic Diagnostic Policy Service Automatic Diagnostic Service Host Manual Diagnostic System Host Manual Disk Defragmenter Manual Distributed Link Tracking Client Automatic Distributed Transaction Coordinator Manual DNS Client Automatic Encrypting File System (EFS) Manual Extensible Authentication Protocol Manual Fax Manual Function Discovery Provider Host Manual Function Discovery Resource Publication Automatic Group Policy Client Automatic Health Key and Certificate Management Manual HomeGroup Listener Manual HomeGroup Provider Manual Human Interface Device Access Manual IKE and AuthIP IPsec Keying Modules Automatic Interactive Services Detection Manual Internet Connection Sharing (ICS) Disabled IP Helper Automatic IPsec Policy Agent Manual KtmRm for Distributed Transaction Coordinator Manual Link-Layer -

3D Graphics for Virtual Desktops Smackdown
3D Graphics for Virtual Desktops Smackdown 3D Graphics for Virtual Desktops Smackdown Author(s): Shawn Bass, Benny Tritsch and Ruben Spruijt Version: 1.11 Date: May 2014 Page i CONTENTS 1. Introduction ........................................................................ 1 1.1 Objectives .......................................................................... 1 1.2 Intended Audience .............................................................. 1 1.3 Vendor Involvement ............................................................ 2 1.4 Feedback ............................................................................ 2 1.5 Contact .............................................................................. 2 2. About ................................................................................. 4 2.1 About PQR .......................................................................... 4 2.2 Acknowledgements ............................................................. 4 3. Team Remoting Graphics Experts - TeamRGE ....................... 6 4. Quotes ............................................................................... 7 5. Tomorrow’s Workspace ....................................................... 9 5.1 Vendor Matrix, who delivers what ...................................... 18 6. Desktop Virtualization 101 ................................................. 24 6.1 Server Hosted Desktop Virtualization directions ................... 24 6.2 VDcry?! ........................................................................... -

Release 343 Graphics Drivers for Windows, Version 344.48. RN
Release 343 Graphics Drivers for Windows - Version 344.48 RN-W34448-01v02 | September 22, 2014 Windows Vista / Windows 7 / Windows 8 / Windows 8.1 Release Notes TABLE OF CONTENTS 1 Introduction to Release Notes ................................................... 1 Structure of the Document ........................................................ 1 Changes in this Edition ............................................................. 1 2 Release 343 Driver Changes ..................................................... 2 Version 344.48 Highlights .......................................................... 2 What’s New in Version 344.48 ................................................. 3 What’s New in Release 343..................................................... 5 Limitations in This Release ..................................................... 8 Advanced Driver Information ................................................. 10 Changes and Fixed Issues in Version 344.48.................................... 14 Open Issues in Version 344.48.................................................... 15 Windows Vista/Windows 7 32-bit Issues..................................... 15 Windows Vista/Windows 7 64-bit Issues..................................... 15 Windows 8 32-bit Issues........................................................ 17 Windows 8 64-bit Issues........................................................ 17 Windows 8.1 Issues ............................................................. 18 Not NVIDIA Issues.................................................................. -
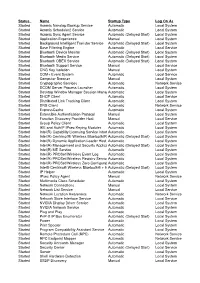
Status Name Startup Type Log on As Started Acronis Nonstop Backup Service Automatic Local System Started Acronis Scheduler2
Status Name Startup Type Log On As Started Acronis Nonstop Backup Service Automatic Local System Started Acronis Scheduler2 Service Automatic Local System Started Acronis Sync Agent Service Automatic (Delayed Start) Local System Started Application Experience Manual Local System Started Background Intelligent Transfer Service Automatic (Delayed Start) Local System Started Base Filtering Engine Automatic Local Service Started Bluetooth Device Monitor Automatic (Delayed Start) Local System Started Bluetooth Media Service Automatic (Delayed Start) Local System Started Bluetooth OBEX Service Automatic (Delayed Start) Local System Started Bluetooth Support Service Manual Local Service Started CNG Key Isolation Manual Local System Started COM+ Event System Automatic Local Service Started Computer Browser Manual Local System Started Cryptographic Services Automatic Network Service Started DCOM Server Process Launcher Automatic Local System Started Desktop Window Manager Session ManagerAutomatic Local System Started DHCP Client Automatic Local Service Started Distributed Link Tracking Client Automatic Local System Started DNS Client Automatic Network Service Started ExpressCache Automatic Local System Started Extensible Authentication Protocol Manual Local System Started Function Discovery Provider Host Manual Local Service Started Group Policy Client Automatic Local System Started IKE and AuthIP IPsec Keying Modules Automatic Local System Started Intel(R) Capability Licensing Service InterfaceAutomatic Local System Started Intel(R) Centrino(R) -

Matrox Imaging Library (MIL) 9.0 Mildisplay.Txt October 6, 2009 © Copyright Matrox Electronic Systems Ltd., 1992-2009
file:///C|/Work/mildisplay.txt -------------------------------------------------------------------------------- Matrox Imaging Library (MIL) 9.0 mildisplay.txt October 6, 2009 © Copyright Matrox Electronic Systems Ltd., 1992-2009. All rights reserved. -------------------------------------------------------------------------------- This document outlines what is new with MIL display module. It also presents last minute information that did not make it into the manual or on-line help. Note that this text file serves to complement your manual. The information found in this file overrides your formally documented material. -------------------------------------------------------------------------------- Main Table of Contents Section 1: What's new in MIL 9.0 Update 16 Section 2: What's new in MIL 9.0 -------------------------------------------------------------------------------- -------------------------------------------------------------------------------- Section 1: What's new in MIL 9.0 Update 16 Table of Contents for Section 1 1. Exclusive Displays 1.1 Overview 1.2 Allocation of an exclusive display 1.2.1 Requirements 1.2.2 InitFlag 1.2.3 DispNum 1.2.4 DispFormat 1.3 Available MdispControl types -------------------------------------------------------------------------------- 1. Exclusive Displays file:///C|/Work/mildisplay.txt (1 of 7)10/30/2009 1:06:36 PM file:///C|/Work/mildisplay.txt 1.1 Overview ------------ Exclusive display is a new full-screen display type, designed to replace legacy auxiliary displays. One of Windows® extended desktop monitors is exclusively dedicated to display and MIL restricts mouse-cursor outside of the display limits. 1.2 Allocation of an exclusive display -------------------------------------- MIL_ID MdispAlloc(MIL_ID SystemId, MIL_INT DispNum, MIL_CONST_TEXT_PTR DispFormat, MIL_INT InitFlag, MIL_ID *DisplayIdPtr) 1.2.1 Requirements ------------------ It works on any graphic adapter and is compatible with all Video Hardware Acceleration Modes. We suggest having two or more outputs currently used on the desktop. -
Display Driver Download for Windows 7 Microsoft Display Driver Download for Windows 7 Microsoft
display driver download for windows 7 microsoft Display driver download for windows 7 microsoft. Completing the CAPTCHA proves you are a human and gives you temporary access to the web property. What can I do to prevent this in the future? If you are on a personal connection, like at home, you can run an anti-virus scan on your device to make sure it is not infected with malware. If you are at an office or shared network, you can ask the network administrator to run a scan across the network looking for misconfigured or infected devices. Another way to prevent getting this page in the future is to use Privacy Pass. You may need to download version 2.0 now from the Chrome Web Store. Cloudflare Ray ID: 67e3e601dc388498 • Your IP : 188.246.226.140 • Performance & security by Cloudflare. DRIVER WDDM 1.0 GRAPHICS FOR WINDOWS 7 DOWNLOAD. How to graphics card drivers for the 4. This section provides details about new features and enhancements in Windows Display Driver Model WDDM version 1.2, which is available starting with Windows 8. You should be able to use the WDDM 1.0 Vista Driver with anything, does not have to be Dell. Follow this but that come with WDDM 1. Pre-Wddm 1.0 Intel driver 945 Express Driver thru Windows update Hi, I'm a little confused by one of my update options. Found for AMD APU Llano A6-3500 WDDM 1. Each grid square indicates the latest driver version for the corresponding Matrox product/operating system combination.