National Strategy for Countering Domestic Terrorism
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Combating Islamic Extremist Terrorism 1
CGT 1/22/07 11:30 AM Page 1 Combating Islamic Extremist Terrorism 1 OVERALL GRADE D+ Al-Qaeda headquarters C+ Al-Qaeda affiliated groups C– Al-Qaeda seeded groups D+ Al-Qaeda inspired groups D Sympathizers D– 1 CGT 1/22/07 11:30 AM Page 2 2 COMBATING ISLAMIC EXTREMIST TERRORISM ive years after the September 11 attacks, is the United States win- ning or losing the global “war on terror”? Depending on the prism through which one views the conflict or the metrics used Fto gauge success, the answers to the question are starkly different. The fact that the American homeland has not suffered another attack since 9/11 certainly amounts to a major achievement. U.S. military and security forces have dealt al-Qaeda a severe blow, cap- turing or killing roughly three-quarters of its pre-9/11 leadership and denying the terrorist group uncontested sanctuary in Afghanistan. The United States and its allies have also thwarted numerous terror- ist plots around the world—most recently a plan by British Muslims to simultaneously blow up as many as ten jetliners bound for major American cities. Now adjust the prism. To date, al-Qaeda’s top leaders have sur- vived the superpower’s most punishing blows, adding to the near- mythical status they enjoy among Islamic extremists. The terrorism they inspire has continued apace in a deadly cadence of attacks, from Bali and Istanbul to Madrid, London, and Mumbai. Even discount- ing the violence in Iraq and Afghanistan, the tempo of terrorist attacks—the coin of the realm in the jihadi enterprise—is actually greater today than before 9/11. -
During Track Work And/Or Rail Shutdown Events, This Bus Stop Will Also Be Served by Metro Shuttle Buses. NOTE
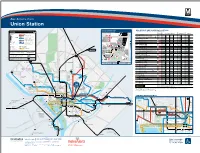
– Bus Service from Union Station Silver Spring Eastern Ave BUS BOARDING MAP BUS SERVICE AND BOARDING LOCATIONS schematic map The table shows approximate minutes between buses; check schedules for full details LEGEND not to scale 16th St BOARD AT MONDAY TO FRIDAY SATURDAY SUNDAY Rail Lines Metrobus Routes t t S ROUTE DESTINATION BUS STOP AM RUSH MIDDAY PM RUSH EVENING DAY EVENING DAY EVENING t S L G d t S n s l Metrobus Major Route 2 80 1 o ARLINGTON-UNION STATION LINE t Frequent, seven-day service on the core i Metrorail H St p H St route. On branches, service levels vary. a 13Y Ronald Reagan Washington Nat’l Airport m -- -- -- -- 30* -- 30* -- Station and Line C B h D6 Metrobus Local Route Alaska Ave t M r F Less frequent service, with some evening o NORTH CAPITOL ST LINE and weekend service available. N G Pl Union Station 80 Fort Totten m 8-15 15 10 30 30 30 30 30 X1 Metrobus Commuter Route Takoma Government EF Printing Office H Parking Peak-hour service linking residential areas Garage 80 Kennedy Center 14-20 30 20-30 30 30 30 30 30 Commuter to rail stations and employment centers. Georgia Ave GN G St G St Railroad Western Ave Bethesda X9 MetroExtra Route 80 McPherson Sq m 14-20 30 20-30 -- -- -- -- -- Transfer National Bureau of GN Limited stops for a faster ride. Days, times Guard Labor Statistics t Q Points S and service levels vary by route. EAST CAPITOL ST LINE Memorial t N s M 1 as E sa 96 Tenleytown-AU m 20 24 21 33 25-30 30-35 30-35 30-35 Map Symbols Routes Operated by ch J us National ett City/County Systems s A Postal 96 -

Attribution and Response to Cybercrime/Terrorism/Warfare Susan W
Journal of Criminal Law and Criminology Volume 97 Article 2 Issue 2 Winter Winter 2007 At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare Susan W. Brenner Follow this and additional works at: https://scholarlycommons.law.northwestern.edu/jclc Part of the Criminal Law Commons, Criminology Commons, and the Criminology and Criminal Justice Commons Recommended Citation Susan W. Brenner, At Light Speed: Attribution and Response to Cybercrime/Terrorism/Warfare, 97 J. Crim. L. & Criminology 379 (2006-2007) This Symposium is brought to you for free and open access by Northwestern University School of Law Scholarly Commons. It has been accepted for inclusion in Journal of Criminal Law and Criminology by an authorized editor of Northwestern University School of Law Scholarly Commons. 0091-4169/07/9702-0379 THE JOURNALOF CRIMINAL LAW & CRIMINOLOGY Vol. 97. No. 2 Copyright 0 2007 by NorthwesternUniversity. Schoolof Low Printedin U.S.A. "AT LIGHT SPEED": ATTRIBUTION AND RESPONSE TO CYBERCRIME/TERRORISM/WARFARE SUSAN W. BRENNER* This Article explains why and how computer technology complicates the related processes of identifying internal (crime and terrorism) and external (war) threats to social order of respondingto those threats. First, it divides the process-attribution-intotwo categories: what-attribution (what kind of attack is this?) and who-attribution (who is responsiblefor this attack?). Then, it analyzes, in detail, how and why our adversaries' use of computer technology blurs the distinctions between what is now cybercrime, cyberterrorism, and cyberwarfare. The Article goes on to analyze how and why computer technology and the blurring of these distinctions erode our ability to mount an effective response to threats of either type. -

Ford's Theatre National Historic Site Scope of Collection Statement
DEPARTMENT OFTHE INTERIOR NATIONAL PARK SERVICE FORD'S THEATRE NATIONAL HISTORIC SITE Scope of Collection Statement Recommended by: _________________________________________________________________________ Bob Sonderman, Regional Curator, National Capital Region Catherine Dewey, Chief of Resource Management, National Mall and Memorial Parks Prepared by:_______________________________________________________________________________ Mark Nelson, CESU Project Staff, Museum Resource Center Elena Popchock, CESU Project Staff, Museum Resource Center Reviewed by:______________________________________________________________________________ Laura Anderson, Museum Curator, National Mall and Memorial Parks Renny Bergeron, Supervisory Museum Curator, National Capital Region Approved by:______________________________________________________________________________ Gay Vietzke, Superintendent, National Mall and Memorial Parks TABLE OF CONTENTS I. INTRODUCTION ................................................................................................................................ 1 A. Executive Summary .....................................................................................................................1 B. Purpose of the Scope of Collection Statement ............................................................................2 C. Legislation Related to the National Park Service Museum Collections .....................................2 D. Site History, Significance, Purpose, Themes and Goals .......................................................... -

The Security Lexicon from Westphalia to the Present a Cautionary Tale
THE SECURITY LEXICON FROM WESTPHALIA TO THE PRESENT A CAUTIONARY TALE MAX G. MANWARING, PH.D. A new and dangerous dynamic is at work around the world today. That new dynamic involves the migration of some of the monopoly of political power (i.e., the authoritative allocation of values in a society) from the traditional nation-state to unconventional actors such as the Islamic State (ISIS), transnational criminal organizations, Leninist-Maoist insurgents, tribal militias, pri- vate armies, enforcer gangs and other modern mercenaries. These actors conduct their own political-psychological type of war against various state and other non-state adversaries. These violent politicized non-state actors are being ignored; or, alternatively, are being considered too hard to deal with. That misunderstanding must inevitably result in an epochal transition from traditional Western nation-state systems and their liberal democratic values to something else dependent on the values—good, bad, or non-existent—of the winner.1 To help civilian and military leaders, policy-makers, opinion-makers, and anyone else who might have the responsibility for dealing with modern conflict come to grips analytically with the security dilemma and other realities of the 21st century political-psychological environment, this paper seeks to do three things. In Part One, we outline a bit of essential history that takes us from the Westphalian Peace Treaty of 1648 to the present. In that context, we briefly consider a con- temporary example of the traditional military-centric approach to national and international security that is still alive and well. That is, Chinese military activity in the South China Sea. -

Extremists on the Left and Right Use Angry, Negative Language
PSPXXX10.1177/0146167218809705Personality and Social Psychology BulletinFrimer et al. 809705research-article2018 Empirical Research Paper Personality and Social Psychology Bulletin Extremists on the Left and Right 1 –16 © 2018 by the Society for Personality and Social Psychology, Inc Use Angry, Negative Language Article reuse guidelines: sagepub.com/journals-permissions DOI:https://doi.org/10.1177/0146167218809705 10.1177/0146167218809705 journals.sagepub.com/home/pspb Jeremy A. Frimer1 , Mark J. Brandt2 , Zachary Melton3, and Matt Motyl3 Abstract We propose that political extremists use more negative language than moderates. Previous research found that conservatives report feeling happier than liberals and yet liberals “display greater happiness” in their language than do conservatives. However, some of the previous studies relied on questionable measures of political orientation and affective language, and no studies have examined whether political orientation and affective language are nonlinearly related. Revisiting the same contexts (Twitter, U.S. Congress), and adding three new ones (political organizations, news media, crowdsourced Americans), we found that the language of liberal and conservative extremists was more negative and angry in its emotional tone than that of moderates. Contrary to previous research, we found that liberal extremists’ language was more negative than that of conservative extremists. Additional analyses supported the explanation that extremists feel threatened by the activities of political rivals, and their angry, negative language represents efforts to communicate as much to others. Keywords language, anger, extremism, liberals and conservatives, threat, happiness Received February 27, 2018; revision accepted October 1, 2018 For too many of our citizens, a different reality exists: extremists—on both the political left and right—use more Mothers and children trapped in poverty in our inner cities; negative language than moderates. -

Jefferson Memorial Accessibility Ramps
THOMAS JEFFERSON MEMORIAL Submission to the National Capital Planning Commission for March 29, 2019 Project Overview Description of Project Area The Thomas Jefferson Memorial is located at 701 E NCPC Plans and Policies Basin Drive SW. The site of the Memorial is located in Comprehensive Plan for the National Capital West Potomac Park on the shore of the Potomac River Tidal Basin. This project is in line with the Comprehensive Plan for the National Capital (2016), specifically the Parks & Based on the McMillan Plan, the famous architect Open Space Element. The project complies with the John Russell Pope designed a monolithic pantheon, following policies: which faces towards the White House. The site for the Memorial was low, swampy land created from fill from • Preserve and maintain cultural landscapes, river dredging. including their natural and constructed elements. The Tidal Basin flanks the north and the west side • Protect or restore viewsheds that contribute to of the Memorial. To the south of the Memorial is the cultural landscapes and the aesthetic quality, busy, heavily traveled East Basin Drive SW. This road is historic significance and visitor experience of the traveled by pedestrians, buses, bicyclists, tour groups, parks and open space system. etc. The main point of access to the Memorial for most • Protect the image of Washington, along with visitors traveling via vehicle is from the south of the the lighting hierarchy established by iconic civil Memorial. The east of the Memorial is a wooded area landmarks including the U.S. Capital, White House, that is filled with paths to the Memorial. -

National Security and Constitutional Rights in Korea
National Security and Constitutional Rights in Korea - National Security Law, Past and Present Park Won Soon, Human Rights Lawyer Chair, Executive Committee, PSPD Director, Beautiful Foundation As of 25 August, of the 99 political prisoners in detention, 54 were detained on charges under the National Security Law. Of these, the majority were arrested under Article 7, which punishes membership of organizations deemed to "benefit the enemy", improving relations with North Korea prompted debate on reform of the National Security Law. President Kim Dae-Jung apparently encouraged by his award of the Nobel Peace Prize, announced his support for revisions to the National Security Law, but opposition to reform in the National Assembly from both the GNP and the ULD prevented significant revisions. (Amnesty International Report 2001) 1. Introduction De Facto Constitution - The National Security Law The National Security Law (NSL) in Korea has been called as a de facto constitution. It meas the NSL was under no other laws including the Constitution. Even though it is inferior to the Constitution namely, no legal enforcement agencies and the court could not challenge unconstitutionality of the law in reality. Korean peninsula has been one of the powder magazine where small incident could lead to big armed conflict. As a matter of fact, in 1950, there broke out Korean war in which over 3 million people were killed. Since then, national security has been regarded as the most important and senstive agenda among Korean people. Basic freedom and human rights enshrined in the Constitution has been sacrificed in the name of national security. -

The Leadership Issue
SUMMER 2017 NON PROFIT ORG. U.S. POSTAGE PAID ROLAND PARK COUNTRY SCHOOL connections BALTIMORE, MD 5204 Roland Avenue THE MAGAZINE OF ROLAND PARK COUNTRY SCHOOL Baltimore, MD 21210 PERMIT NO. 3621 connections THE ROLAND PARK COUNTRY SCHOOL COUNTRY PARK ROLAND SUMMER 2017 LEADERSHIP ISSUE connections ROLAND AVE. TO WALL ST. PAGE 6 INNOVATION MASTER PAGE 12 WE ARE THE ROSES PAGE 16 ADENA TESTA FRIEDMAN, 1987 FROM THE HEAD OF SCHOOL Dear Roland Park Country School Community, Leadership. A cornerstone of our programming here at Roland Park Country School. Since we feel so passionately about this topic we thought it was fitting to commence our first themed issue of Connections around this important facet of our connections teaching and learning environment. In all divisions and across all ages here at Roland Park Country School — and life beyond From Roland Avenue to Wall Street graduation — leadership is one of the connecting, lasting 06 President and CEO of Nasdaq, Adena Testa Friedman, 1987 themes that spans the past, present, and future lives of our (cover) reflects on her time at RPCS community members. Joe LePain, Innovation Master The range of leadership experiences reflected in this issue of Get to know our new Director of Information and Innovation Connections indicates a key understanding we have about the 12 education we provide at RPCS: we are intentional about how we create leadership opportunities for our students of today — and We Are The Roses for the ever-changing world of tomorrow. We want our students 16 20 years. 163 Roses. One Dance. to have the skills they need to be successful in the future. -

Colombian Nationalism: Four Musical Perspectives for Violin and Piano
COLOMBIAN NATIONALISM: FOUR MUSICAL PERSPECTIVES FOR VIOLIN AND PIANO by Ana Maria Trujillo A Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Musical Arts Major: Music The University of Memphis December 2011 ABSTRACT Trujillo, Ana Maria. DMA. The University of Memphis. December/2011. Colombian Nationalism: Four Musical Perspectives for Violin and Piano. Dr. Kenneth Kreitner, Ph.D. This paper explores the Colombian nationalistic musical movement, which was born as a search for identity that various composers undertook in order to discover the roots of Colombian musical folklore. These roots, while distinct, have all played a significant part in the formation of the culture that gave birth to a unified national identity. It is this identity that acts as a recurring motif throughout the works of the four composers mentioned in this study, each representing a different stage of the nationalistic movement according to their respective generations, backgrounds, and ideological postures. The idea of universalism and the integration of a national identity into the sphere of the Western musical tradition is a dilemma that has caused internal struggle and strife among generations of musicians and artists in general. This paper strives to open a new path in the research of nationalistic music for violin and piano through the analyses of four works written for this type of chamber ensemble: the third movement of the Sonata Op. 7 No.1 for Violin and Piano by Guillermo Uribe Holguín; Lopeziana, piece for Violin and Piano by Adolfo Mejía; Sonata for Violin and Piano No.3 by Luís Antonio Escobar; and Dúo rapsódico con aires de currulao for Violin and Piano by Andrés Posada. -

Father Heinrich As Kindred Spirit
father heinrich as kindred spirit or, how the log-house composer of kentucky became the beethoven of america betty e. chmaj Thine eyes shall see the light of distant skies: Yet, COLE! thy heart shall bear to Europe's strand A living image of their own bright land Such as on thy glorious canvas lies. Lone lakes—savannahs where the bison roves— Rocks rich with summer garlands—solemn streams— Skies where the desert eagle wheels and screams— Spring bloom and autumn blaze of boundless groves. Fair scenes shall greet thee where thou goest—fair But different—everywhere the trace of men. Paths, homes, graves, ruins, from the lowest glen To where life shrinks from the fierce Alpine air, Gaze on them, till the tears shall dim thy sight, But keep that earlier, wilder image bright. —William Cullen Bryant, "To Cole, the Painter, Departing for Europe" (1829) More than any other single painting, Asher B. Durand's Kindred Spirits of 1849 has come to speak for mid-nineteenth-century America (Figure 1). FIGURE ONE (above): Asher B. Durand, Kindred Spirits (1849). The painter Thomas Cole and the poet William Cullen Bryant are shown worshipping wild American Nature together from a precipice high in the CatskiJI Mountains. Reprinted by permission of the New York Public Library. 0026-3079/83/2402-0035$0l .50/0 35 The work portrays three kinds of kinship: the American's kinship with Nature, the kinship of painting and poetry, and the kinship of both with "the wilder images" of specifically American landscapes. Commissioned by a patron at the time of Thomas Cole's death as a token of gratitude to William Cullen Bryant for his eulogy at Cole's funeral, the work shows Cole and Bryant admiring together the kind of images both had commem orated in their art. -

Facebook and Violent Extremism Awareness Brief
Facebook and Violent Extremism Understanding Facebook legitimate reasons, violent extremists, gangs, and terrorist groups also have a significant With more than 1 billion users, Facebook is presence and following on Facebook.1 The one of the most popular social networking following identifies the ways domestic and sites. After users create a personal profile or international extremists of all persuasions use organization page and add photos, contact Facebook to promote violence: information, and additional information, they can search for people with similar interests, Recruitment create networks of “friends,” communicate by sending private messages or posting Facebook provides violent extremists with a comments on another user’s wall, “like” pages vast recruiting ground. In the United States of organizations and join “groups” with other alone, 67 percent of all Internet users have a users who share similar interests, and post and Facebook profile, and the percentages are even share content created on Facebook or linked to higher for youth and young adults. Moreover, another website. Facebook is one of the top three websites visited by people under the age of 18.2 How Extremists Use Facebook Extremists take advantage of the fact that parents and law enforcement often are not Although individuals and organizations aware of the dangers that could be present worldwide use Facebook for a variety of when a young person spends large amounts AWARENESS BRIEF 2 AWARENESS BRIEF of time on Facebook. Extremist individuals bring propaganda to a wider audience and and organizations use this viewing potential to serve as a gateway to other extremist websites create lines of communication, enabling them where more radical content is available.