How Tracking Companies Circumvent Ad Blockers Using Websockets
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Demystifying Content-Blockers: a Large-Scale Study of Actual Performance Gains
Demystifying Content-blockers: A Large-scale Study of Actual Performance Gains Ismael Castell-Uroz Josep Sole-Pareta´ Pere Barlet-Ros Universitat Politecnica` de Catalunya Universitat Politecnica` de Catalunya Universitat Politecnica` de Catalunya Barcelona, Spain Barcelona, Spain Barcelona, Spain [email protected] [email protected] [email protected] Abstract—With the evolution of the online advertisement and highly parallel network measurement system [10] that loads tracking ecosystem, content-filtering has become the reference every website using one of the most relevant content-blockers tool for improving the security, privacy and browsing experience of each category and compares their performance. when surfing the Internet. It is also commonly believed that using content-blockers to stop unsolicited content decreases the time We found that, although we can observe some improvements needed for loading websites. In this work, we perform a large- in terms of effective page size, the results do not directly scale study with the 100K most popular websites on the actual translate to gains in loading time. In some cases, there could performance improvements of using content-blockers. We focus even be an overhead to be paid. This is the case for two of the our study on two relevant metrics for measuring the browsing studied plugins, especially in small and fast loading websites. performance; page size and loading time. Our results show that using such tools results in small improvements in terms of page The measurement system and methodology proposed in this size but, contrary to popular belief, it has a negligible impact in paper can also be useful for network and service administrators terms of loading time. -

E Cost of Ad Blocking Pagefair and Adobe 2015 Ad Blocking Report
!e cost of ad blocking PageFair and Adobe 2015 Ad Blocking Report Introduction In the third annual ad blocking report, PageFair, with the help of Adobe, provides updated data on the scale and growth of ad blocking so"ware usage and highlights the global and regional economic impact associated with it. Additionally, this report explores the early indications surrounding the impact of ad blocking within the mobile advertising space and how mobile will change the ad blocking landscape. Table of Contents 3. Key insights 8. Effect of ad blocking by industry 13. A"erword 4. Global ad blocking growth 9. Google Chrome still the main driver of ad 14. Background 5. Usage of ad blocking so"ware in the United block growth 15. Methodology States 10. Mobile is yet to be a factor in ad blocking 16. Tables 6. Usage of ad blocking so"ware in Europe growth 17. Tables 7. !e cost of blocking ads 11. Mobile will facilitate future ad blocking growth 12. Reasons to start using an ad blocker PAGEFAIR AND ADOBE | 2015 Ad Blocking Report 2 Key Insights More consumers block ads, continuing the strong growth rates seen during 2013 and 2014. 41% YoY global growth Q2 2014 - Q2 2015 !e "ndings • Globally, the number of people using ad blocking so"ware grew by 41% year over year. • 16% of the US online population blocked ads during Q2 2015. • Ad block usage in the United States grew 48% during the past year, increasing to 45 million monthly active 45 million users (MAUs) during Q2 2015. Average MAUs in the United • Ad block usage in Europe grew by 35% during the past year, increasing to 77 million monthly active users States Q2 2015 during Q2 2015. -

The Impact of Ad-Blockers on Online Consumer Behavior
Marketing Science Institute Working Paper Series 2021 Report No. 21-119 The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri “The Impact of Ad-blockers on Online Consumer Behavior” © 2021 Vilma Todri MSI Working Papers are Distributed for the benefit of MSI corporate and academic members and the general public. Reports are not to be reproduced or published in any form or by any means, electronic or mechanical, without written permission. Marketing Science Institute Working Paper Series The Impact of Ad-blockers on Online Consumer Behavior Vilma Todri Goizueta Business School, Emory University, Atlanta, GA 30322 [email protected] Digital advertising is on track to become the dominant form of advertising but ad-blocking technologies have recently emerged posing a potential threat to the online advertising ecosystem. A significant and increasing fraction of Internet users has indeed already started employing ad-blockers. However, surprisingly little is known yet about the effects of ad-blockers on consumers. This paper investigates the impact of ad- blockers on online search and purchasing behaviors by empirically analyzing a consumer-level panel dataset. Interestingly, the analyses reveal that ad-blockers have a significant effect on online purchasing behavior: online consumer spending decreases due to ad-blockers by approximately $14:2 billion a year in total. In examining the underlying mechanism of the ad-blocker effects, I find that ad-blockers significantly decrease spending for brands consumers have not experienced before, partially shifting spending towards brands they have experienced in the past. I also find that ad-blockers spur additional unintended consequences as they reduce consumers' search activities across information channels. -

HTML5 Websocket Protocol and Its Application to Distributed Computing
CRANFIELD UNIVERSITY Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc arXiv:1409.3367v1 [cs.DC] 11 Sep 2014 Academic Year: 2013 - 2014 Supervisor: Mark Stillwell September 2014 CRANFIELD UNIVERSITY SCHOOL OF ENGINEERING Computational Software Techniques in Engineering MSc Academic Year: 2013 - 2014 Gabriel L. Muller HTML5 WebSocket protocol and its application to distributed computing Supervisor: Mark Stillwell September 2014 This thesis is submitted in partial fulfilment of the requirements for the degree of Master of Science © Cranfield University, 2014. All rights reserved. No part of this publication may be reproduced without the written permission of the copyright owner. Declaration of Authorship I, Gabriel L. Muller, declare that this thesis titled, HTML5 WebSocket protocol and its application to distributed computing and the work presented in it are my own. I confirm that: This work was done wholly or mainly while in candidature for a research degree at this University. Where any part of this thesis has previously been submitted for a degree or any other qualification at this University or any other institution, this has been clearly stated. Where I have consulted the published work of others, this is always clearly attributed. Where I have quoted from the work of others, the source is always given. With the exception of such quotations, this thesis is entirely my own work. I have acknowledged all main sources of help. Where the thesis is based on work done by myself jointly with others, I have made clear exactly what was done by others and what I have contributed myself. -

Will Ad Blocking Break the Internet?
NBER WORKING PAPER SERIES WILL AD BLOCKING BREAK THE INTERNET? Ben Shiller Joel Waldfogel Johnny Ryan Working Paper 23058 http://www.nber.org/papers/w23058 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 January 2017 Johnny Ryan is an employee of PageFair, a firm that measures the extent of ad blocking and offers ad-recovery technologies that enable publishers to display ads in a manner that adblockers cannot block. Neither Shiller nor Waldfogel has received any compensation for the research in the paper. PageFair was allowed to review the paper for accuracy but did not have control over the paper's findings nor conclusions. The views expressed herein are those of the authors and do not necessarily reflect the views of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer-reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2017 by Ben Shiller, Joel Waldfogel, and Johnny Ryan. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Will Ad Blocking Break the Internet? Ben Shiller, Joel Waldfogel, and Johnny Ryan NBER Working Paper No. 23058 January 2017 JEL No. L81,L82 ABSTRACT Ad blockers allow Internet users to obtain information without generating ad revenue for site owners; and by 2016 they were used by roughly a quarter of site visitors. Given the ad-supported nature of much of the web, ad blocking poses a threat to site revenue and, if revenue losses undermine investment, a possible threat to consumers' access to appealing content. -
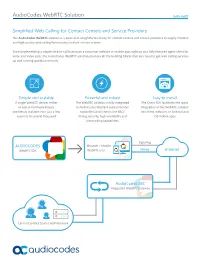
Audiocodes Webrtc Solution DATA SHEET
AudioCodes WebRTC Solution DATA SHEET Simplified Web Calling for Contact Centers and Service Providers The AudioCodes WebRTC solution is a quick and straightforward way for contact centers and service providers to supply intuitive and high-quality web calling functionality to their service centers. From implementing a simple click-to-call button on a consumer website or mobile app, right up to a fully featured agent client for voice and video calls, the AudioCodes WebRTC solution provides all the building blocks that you need to get web calling services up and running quickly and easily. Simple and scalable Powerful and robust Easy to install A single WebRTC device, either The WebRTC solution is fully integrated The Client SDK facilitates the quick virtual or hardware-based, in AudioCodes Mediant session border integration of the WebRTC solution seamlessly scalable from just a few controllers and inherits the SBCs’ into client websites or Android and sessions to several thousand strong security, high availability and iOS mobile apps transcoding capabilities Signaling AUDIOCODES Browser / Mobile WebRTC SDK WebRTC user Media Internet AudioCodes SBC Integrated WebRTC Gateway Carrier/Contact Center VoIP Network AudioCodes WebRTC Solution DATA SHEET Specifications WebRTC Gateway About AudioCodes AudioCodes Ltd. (NasdaqGS: AUDC) is a Deployment leading vendor of advanced voice networking VMWare KVM AWS Mediant 9000 Mediant 4000 method and media processing solutions for the digital workplace. With a commitment to the human 3,000 voice deeply embedded in its DNA, AudioCodes 5,000 WebRTC sessions 2,700 3,500 (20,000 on 1,000 enables enterprises and service providers (20K on roadmap) roadmap) to build and operate all-IP voice networks for unified communications, contact centers 3,000 1,050 integrated and hosted business services. -

A Websocket-Based Approach to Transporting Web Application Data
A WebSocket-based Approach to Transporting Web Application Data March 26, 2015 A thesis submitted to the Division of Graduate Studies and Research of the University of Cincinnati in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in the Department of Computer Science of the College of Engineering and Applied Science by Ross Andrew Hadden B.S., University of Cincinnati, Cincinnati, Ohio (2014) Thesis Adviser and Committee Chair: Dr. Paul Talaga Committee members: Dr. Fred Annexstein, Professor, and Dr. John Franco, Professor Abstract Most web applications serve dynamic data by either deferring an initial page response until the data has been retrieved, or by returning the initial response immediately and loading additional content through AJAX. We investigate another option, which is to return the initial response immediately and send additional content through a WebSocket connection as the data becomes available. We intend to illustrate the performance of this proposition, as compared to popular conventions of both a server- only and an AJAX approach for achieving the same outcome. This dissertation both explains and demonstrates the implementation of the proposed model, and discusses an analysis of the findings. We use a Node.js web application built with the Cornerstone web framework to serve both the content being tested and the endpoints used for data requests. An analysis of the results shows that in situations when minimal data is retrieved after a timeout, the WebSocket method is marginally faster than the server and AJAX methods, and when retrieving populated files or database records it is marginally slower. The WebSocket method considerably outperforms the AJAX method when making multiple requests in series, and when making requests in parallel the WebSocket and server approaches both outperform AJAX by a tremendous amount. -

Digital Privacy
DIGITAL PRIVACY Web-Tracking stoppen Sie haben Interesse an den Kompaktseminaren Digital Privacy? E-Mail: [email protected] Die Inhalte dieses Dokuments wurden sehr sorgfältig recherchiert und verfasst. Die dargestellten Tipps&Tricks, Apps, Links und Programme wurden bereits tausendfach erfolgreich zur Anwendung gebracht. Bitte haben Sie Verständnis, dass eine Garantie, Gewährleistung oder Haftung dennoch ausgeschlossen ist. Sollten sich trotz aller Sorgfalt Fehler eingeschlichen haben, freue ich mich auf Ihre E-Mail [email protected] QUICK-GUIDE – TRACKING KONTROLLIEREN Auf den folgenden Seiten findet sich Hintergründiges zum Thema „Tracking kontrollieren“. Abgewo- gen werden verschiedene Wege zum Ziel, die Vor- und Nachteile von Erweiterungen (sogenannter Add-ons) für den Firefox-Browser unter Windows/Android, Installationshinweise sowie einige Tra- cking-Stopp-Tipps für das iPhone. Für alle, die sich direkt an die Umsetzung machen wollen, hier vorab ein kleiner Quick-Guide für Windows und Android. Unabdingbar: Der Mozilla Firefox-Browser (… vgl. jedoch auch „Tipp! Brave-Browser“) Mozilla Firefox (Windows) - https://www.mozilla.org/de/firefox/new/ Mozilla Firefox (Android) - https://www.mozilla.org/de/firefox/android/ oder Google Play Store Ab Version 70 kommt der Firefox-Browser mit einem sehr gut funktionierendem integrierten Tracker- und Fingerprintblocker daher. Das war auch schon in früheren Versionen der Fall, jedoch nur an- wählbar für den 'Privatmodus' bzw. nicht ganz so leistungsstark. Der Firefox-Browser -

Who Filters the Filters: Understanding the Growth, Usefulness and EIciency of Crowdsourced Ad Blocking
Who Filters the Filters: Understanding the Growth, Usefulness and Eiciency of Crowdsourced Ad Blocking Peter Snyder Antoine Vastel Benjamin Livshits Brave Soware University of Lille / INRIA Brave Soware / Imperial College USA France London [email protected] [email protected] United Kingdom [email protected] ABSTRACT 1 INTRODUCTION Ad and tracking blocking extensions are popular tools for improv- As the web has become more popular as a platform for information ing web performance, privacy and aesthetics. Content blocking and application delivery, users have looked for ways to improve the extensions generally rely on lter lists to decide whether a web privacy and performance of their browsing. Such eorts include request is associated with tracking or advertising, and so should popup blockers, hosts.txt les that blackhole suspect domains, be blocked. Millions of web users rely on lter lists to protect their and privacy-preserving proxies (like Privoxy 1) that lter unwanted privacy and improve their browsing experience. content. Currently, the most popular ltering tools are ad-blocking Despite their importance, the growth and health of lter lists are browser extensions, which determine whether to fetch a web re- poorly understood. Filter lists are maintained by a small number of source based on its URL. e most popular ad-blocking extensions contributors who use undocumented heuristics and intuitions to are Adblock Plus 2, uBlock Origin 3 and Ghostery 4, all of which determine what rules should be included. Lists quickly accumulate use lter lists to block unwanted web resources. rules, and rules are rarely removed. As a result, users’ browsing Filter lists play a large and growing role in making the web pleas- experiences are degraded as the number of stale, dead or otherwise ant and useful. -

Be Library Smart: Protecting Your Privacy
BE LIBRARY SMART: PROTECTING YOUR PRIVACY Browsers and Search Engines duckduckgo.com This search engine doesn’t track your activity, and their mobile app that assigns grades based on sites’ privacy offers more secure mobile browsing. startpage.com This search engine uses Google’s results but does not track your IP address or use cookies. brave.com Brave is a browser that blocks trackers and ads and automatically upgrades to https when available. Their mobile app features the same protections. torproject.org The Tor browser routes users’ activity through proxies all over the world to help provide anonymity. Add-ons/extensions disconnect.me This browser extension blocks third-party trackers. Available for Chrome, Firefox, and Opera, with laptop/desktop and mobile versions. noscript.net This browser extension disables JavaScript, Flash, and other elements of websites that can be used to track or infect a computer. Available for Firefox and Chrome. HTTPS Everywhere If a secure version of a website exists, this extension will automatically connect to it over the insecure default version. Available for Firefox, Chrome, and Opera. eff.org/https-everywhere Privacy Badger This add-on prevents websites from using invisible trackers. It learns from trackers’ behavior to block tracking across multiple sites. Available for Firefox, Chrome, and Opera. eff.org/privacybadger uBlock Origin This add-on blocks ads, trackers, and malware. Available for Firefox, Chrome, Microsoft Edge, and Safari. github.com/gorhill/uBlock Brought to you by the Maryland Library Association's Intellectual Freedom Panel and the Ruth Enlow Library. BE LIBRARY SMART: PROTECTING YOUR PRIVACY Apps and Services VPN Short for Virtual Private Network, this will route your internet connection through different IP addresses to better protect your privacy. -

Personal Data Processing Policy
PERSONAL DATA PROCESSING POLICY (website, customers and prospects) Cisbio Bioassays is a business-to-business (B2B) company and in most cases, the information we process concerns legal entities and not individuals. Nevertheless, behind the companies, there are men and women. Respect for your privacy and the protection of your personal data is a priority and constant concern for Cisbio Bioassays, who have adopted a "privacy by design" approach. This notably implies that your personal data is protected by default both in terms of the system design and Cisbio Bioassays internal practices. Everyone in our company that is required to view or use personal data has been trained to respect the applicable law and the issues of confidentiality. Data processing is performed transparently within the rights granted to you by the laws and regulations, but also by this personal data processing policy. The protection of your privacy is ensured from end to end, from the design of the application to the erasure of your data. Cisbio Bioassays ensures a high level of protection in accordance with the European standards for the protection of personal data to all its customers and users, whatever their country of origin and, subject to legal and regulatory obligations, regardless of where they access the services. OUR PRINCIPLES, OUR ETHICS Our ethics on privacy protection and personal data is based on the following principles: • Transparency and loyalty: you know what information is collected, by whom, by what means and for which use. At any moment you can also request details on the processing implemented by contacting our services. -

The Websockets Package
The websockets Package Bryan W. Lewis [email protected] December 18, 2012 1 Introduction HTML 5 websockets define an efficient socket-like communication protocol for the web. The websockets package is a native websocket implementation for R that supports most of the draft IETF protocols in use today by web browsers. The websockets package is especially well-suited to interaction between R and web scripting languages like Javascript. Multiple simultaneous web- socket server and client connections are supported. The package has few dependencies and is written mostly in R. Packages are available for all major R platforms including GNU/Linux, OS X, and Windows. Websockets are a particularly simple way to expose R to the Web as a service–they let Javascript and other scripts embedded in web pages directly interact with R, bypassing traditional middleware layers like .NET, Java, and web servers normally used for such interaction. In some cases, websockets can be much more efficient than traditional Ajax schemes for interacting with clients over web protocols. Websockets also simplify service scalability in many cases. The websockets package provides three main capabilities: 1. An websocket service. 2. An websocket client. 3. A basic HTTP service. This guide illustrates each capability with simple examples. The websockets Package 2 Running an R websockets server, step by step The websockets package includes a server function that can initiate and respond to websocket and HTTP events over a network connection (websockets are an extension of standard HTTP). All R/Websocket server applications share the following basic recipe: 1. Load the library. 2. Initialize a websocket server with create_server.