We4authors Factsheet
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Remember to Change Intro Slide Color As Needed
Simple AngularJS thanks to Best Practices Learn AngularJS the easy way Level 100-300 What’s this session about? 1. AngularJS can be easy when you understand basic concepts and best practices 2. But it can also be messy and difficult if you follow most online examples for just about anything I had to learn this the hard way I want to make it easier for you With know-how and sample code Quick Bad-Example Code Taken from AngularJS documentation. This example use the old $scope concept which you should avoid nowdays. Don’t worry if you don’t understand this – it’s meant to keep advanced developers in the room . 1. Demo 2. What is AngularJS 3. Deep Dive and Learn Goal: Get to know AngularJS based on a real App built with as many simple best practices as I could think of. Example AngularJS App Think of a DNN-Module, just simpler Live Demo Feedback given by anonymous users Feedback management for Admin users Download current edition http://2sxc.org/apps SoC Server and Client Server Concerns Client Concerns Storage of Data Form UI for new items Ability to deliver Data Instructs Server what to when needed do (Create, Read, …) Sorted Categories All/one Feedback Items List-UI for admin Ability to do other CRUD Change UIs when editing Create, Read, Update Delete Messages REST Dialogs Permissions on Content- refresh Types (allow create…) No code (zero c#) All code is on the client Look at the wire (live glimpse) Let’s watch these processes Recommended Tools Get Categories Chrome Debug Create Feedback-Item Firebug Get All Feedback -

Next Generation Web Scanning Presentation
Next generation web scanning New Zealand: A case study First presented at KIWICON III 2009 By Andrew Horton aka urbanadventurer NZ Web Recon Goal: To scan all of New Zealand's web-space to see what's there. Requirements: – Targets – Scanning – Analysis Sounds easy, right? urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com Targets What does 'NZ web-space' mean? It could mean: •Geographically within NZ regardless of the TLD •The .nz TLD hosted anywhere •All of the above For this scan it means, IPs geographically within NZ urbanadventurer (Andrew Horton) www.morningstarsecurity.com Finding Targets We need creative methods to find targets urbanadventurer (Andrew Horton) www.morningstarsecurity.com DNS Zone Transfer urbanadventurer (Andrew Horton) www.morningstarsecurity.com Find IP addresses on IRC and by resolving lots of NZ websites 58.*.*.* 60.*.*.* 65.*.*.* 91.*.*.* 110.*.*.* 111.*.*.* 113.*.*.* 114.*.*.* 115.*.*.* 116.*.*.* 117.*.*.* 118.*.*.* 119.*.*.* 120.*.*.* 121.*.*.* 122.*.*.* 123.*.*.* 124.*.*.* 125.*.*.* 130.*.*.* 131.*.*.* 132.*.*.* 138.*.*.* 139.*.*.* 143.*.*.* 144.*.*.* 146.*.*.* 150.*.*.* 153.*.*.* 156.*.*.* 161.*.*.* 162.*.*.* 163.*.*.* 165.*.*.* 166.*.*.* 167.*.*.* 192.*.*.* 198.*.*.* 202.*.*.* 203.*.*.* 210.*.*.* 218.*.*.* 219.*.*.* 222.*.*.* 729,580,500 IPs. More than we want to try. urbanadventurer (Andrew Horton) www.morningstarsecurity.com IP address blocks in the IANA IPv4 Address Space Registry Prefix Designation Date Whois Status [1] ----- -

The Zope Developer's Guide (2.4 Edition)
The Zope Developer's Guide (2.4 Edition) Chris McDonough, Michel Pelletier, Shane Hathaway Zope Developer's Guide (2.4 edition) Introduction 7 Chapter 1: Components and Interfaces 8 Zope Components 8 Python Interfaces 10 Why Use Interfaces? 10 Creating Interfaces 10 The Interface Model 12 Querying an Interface 12 Checking Implementation 13 Conclusion 14 Chapter 2: Object Publishing 15 Introduction 15 HTTP Publishing 15 15 URL Traversal 16 Traversal Interfaces 17 Publishable Object Requirements 17 Traversal Methods 17 Publishing Methods 18 HTTP Responses 19 Controlling Base HREF 19 Response Headers 20 Pre-Traversal Hook 20 Traversal and Acquisition 20 Traversal and Security 22 Basic Publisher Security 22 Zope Security 22 Environment Variables 23 Testing 23 Publishable Module 23 Calling the Published Object 24 Marshalling Arguments from the Request 24 Argument Conversion 24 Method Arguments 25 Record Arguments 26 Exceptions 27 2 Zope Developer's Guide (2.4 edition) Exceptions and Transactions 27 Manual Access to Request and Response 28 Other Network Protocols 29 FTP 29 WebDAV 30 Supporting Write Locking 30 XML-RPC 31 Summary 32 Chapter 3: Zope Products 33 Introduction 33 Development Process 33 Consider Alternatives 33 Starting with Interfaces 33 Implementing Interfaces 34 Building Product Classes 35 Base Classes 35 Acquisition.Implicit 35 Globals.Persistent 36 OFS.SimpleItem.Item 36 AccessControl.Role.RoleManager 37 OFS.ObjectManager 37 OFS.PropertyManager 37 Security Declarations 38 Summary 39 Registering Products 40 Product Initialization -
![Environmental Protection Commission[567]](https://docslib.b-cdn.net/cover/3404/environmental-protection-commission-567-533404.webp)
Environmental Protection Commission[567]
IAC 5/19/21 Environmental Protection[567] Analysis, p.1 ENVIRONMENTAL PROTECTION COMMISSION[567] Former Water, Air and Waste Management[900], renamed by 1986 Iowa Acts, chapter 1245, Environmental Protection Commission under the “umbrella” of the Department of Natural Resources. TITLE I GENERAL CHAPTER 1 OPERATION OF ENVIRONMENTAL PROTECTION COMMISSION 1.1(17A,455A) Scope 1.2(17A,455A) Time of meetings 1.3(17A,455A) Place of meetings 1.4(17A,455A) Notification of meetings 1.5(17A,455A) Attendance and participation by the public 1.6(17A,455A) Quorum and voting requirements 1.7(17A,455A) Conduct of meeting 1.8(17A,455A) Minutes, transcripts, and recordings of meetings 1.9(17A,455A) Officers and duties 1.10(17A,455A) Election and succession of officers 1.11(68B) Sales of goods and services CHAPTER 2 PUBLIC RECORDS AND FAIR INFORMATION PRACTICES (Uniform Rules) 2.1(17A,22) Adoption by reference CHAPTER 3 SUBMISSION OF INFORMATION AND COMPLAINTS—INVESTIGATIONS 3.1(17A,455B) Adoption by reference CHAPTER 4 AGENCY PROCEDURE FOR RULE MAKING 4.1(17A) Adoption by reference CHAPTER 5 PETITIONS FOR RULE MAKING 5.1(17A) Adoption by reference CHAPTER 6 DECLARATORY ORDERS 6.1(17A) Adoption by reference CHAPTER 7 RULES OF PRACTICE IN CONTESTED CASES 7.1(17A) Adoption by reference CHAPTER 8 CONTRACTS FOR PUBLIC IMPROVEMENTS AND PROFESSIONAL SERVICES 8.1(17A) Adoption by reference CHAPTER 9 DELEGATION OF CONSTRUCTION PERMITTING AUTHORITY 9.1(455B) Scope 9.2(455B,17A) Forms 9.3(455B) Procedures 9.4(455B) Criteria for permitting authority at local public -

Let's Encrypt: 30,229 Jan, 2018 | Let's Encrypt: 18,326 Jan, 2016 | Let's Encrypt: 330 Feb, 2017 | Let's Encrypt: 8,199
Let’s Encrypt: An Automated Certificate Authority to Encrypt the Entire Web Josh Aas∗ Richard Barnes∗ Benton Case Let’s Encrypt Cisco Stanford University Zakir Durumeric Peter Eckersley∗ Alan Flores-López Stanford University Electronic Frontier Foundation Stanford University J. Alex Halderman∗† Jacob Hoffman-Andrews∗ James Kasten∗ University of Michigan Electronic Frontier Foundation University of Michigan Eric Rescorla∗ Seth Schoen∗ Brad Warren∗ Mozilla Electronic Frontier Foundation Electronic Frontier Foundation ABSTRACT 1 INTRODUCTION Let’s Encrypt is a free, open, and automated HTTPS certificate au- HTTPS [78] is the cryptographic foundation of the Web, providing thority (CA) created to advance HTTPS adoption to the entire Web. an encrypted and authenticated form of HTTP over the TLS trans- Since its launch in late 2015, Let’s Encrypt has grown to become the port [79]. When HTTPS was introduced by Netscape twenty-five world’s largest HTTPS CA, accounting for more currently valid cer- years ago [51], the primary use cases were protecting financial tificates than all other browser-trusted CAs combined. By January transactions and login credentials, but users today face a growing 2019, it had issued over 538 million certificates for 223 million do- range of threats from hostile networks—including mass surveil- main names. We describe how we built Let’s Encrypt, including the lance and censorship by governments [99, 106], consumer profiling architecture of the CA software system (Boulder) and the structure and ad injection by ISPs [30, 95], and insertion of malicious code of the organization that operates it (ISRG), and we discuss lessons by network devices [68]—which make HTTPS important for prac- learned from the experience. -

Dual-Arm Peg-In-Hole Assembly Using DNN with Double Force/Torque Sensor
applied sciences Article Dual-Arm Peg-in-Hole Assembly Using DNN with Double Force/Torque Sensor David Ortega-Aranda 1,* , Julio Fernando Jimenez-Vielma 1 , Baidya Nath Saha 2 and Ismael Lopez-Juarez 3 1 Centro de Ingenieria y Desarrollo Industrial (CIDESI), Apodaca 66628, Mexico; [email protected] 2 Faculty of Science, Concordia University of Edmonton, Information Technology, Edmonton, AB T5B 4E4, Canada; [email protected] 3 Centre for Research and Advanced Studies (CINVESTAV), Ramos Arizpe 25900, Mexico; [email protected] * Correspondence: [email protected] Abstract: Assembly tasks executed by a robot have been studied broadly. Robot assembly applica- tions in industry are achievable by a well-structured environment, where the parts to be assembled are located in the working space by fixtures. Recent changes in manufacturing requirements, due to unpredictable demanded products, push the factories to seek new smart solutions that can au- tonomously recover from failure conditions. In this way, new dual arm robot systems have been studied to design and explore applications based on its dexterity. It promises the possibility to get rid of fixtures in assembly tasks, but using less fixtures increases the uncertainty on the location of the components in the working space. It also increases the possibility of collisions during the assembly sequence. Under these considerations, adding perception such as force/torque sensors have been done to produce useful data to perform control actions. Unfortunately, the interaction forces between mating parts produced non-linear behavior. Consequently, machine learning algorithms have been Citation: Ortega-Aranda, D.; Jimenez-Vielma, J.F.; Saha, B.N.; considered an alternative tool to avoid the non-linearity. -

Colorado College Is Hiring!
Colorado College is hiring! Early Childhood Teacher (multiple positions available) - Children’s Center Under minimal supervision while in the classroom provide nurturing early care and educational experience to benefit the children and families of the CC Community. Design and implement age-appropriate individualized curriculum to foster growth and development socially, emotionally, physically and cognitively for each child. Be flexible, adaptive, reliable, and a confidential resource for families in an assigned classroom (infant, toddler or pre-school). Full position description: https://employment.coloradocollege.edu/postings/4697 OC (on call) Educational Assistant- Children’s Center Hours may vary Monday through Friday between 7:30 and 5:30 up to 1000 hours per fiscal year. Under general supervision, assists with providing on-site early childhood education and supervision for infants, toddlers and preschool children when teachers are sick and/or on vacation, teacher daily breaks, teacher daily planning times, daily kitchen duties, and working in the afterschool care program. Full position description: https://employment.coloradocollege.edu/postings/4607 Counselor (Occasional) Provide professional mental health services to the students of Colorado College. Positions Type: On Call Full position description: https://employment.coloradocollege.edu/postings/4746 Driver/Automotive Technician Performs maintenance and repair of college vehicles and maintenance equipment; drives fleet vehicles, including highway buses. Position Type: Full-time -

Dotnetnuke Remote Code Execution Vulnerability Cve®1-2017-9822
DOTNETNUKE REMOTE CODE EXECUTION VULNERABILITY CVE®1-2017-9822 DISCUSSION DotNetNuke®2 (DNN), also known as DNN Evoq and DNN Evoq Engage, is a web-based Content Management System (CMS) developed on the Microsoft®3 .NET framework. DNN is a web application commonly deployed on local or cloud Microsoft Internet Information Service (IIS) servers. On July 7, 2017, security researchers revealed a vulnerability within DNN versions 5.2.0 through 9.1.0 that allows an attacker to forge valid DNN credentials and execute arbitrary commands on DNN web servers. Web-based applications, such as DNN, can be overlooked in routine patching since vulnerability scans may be unaware of their presence. Furthermore, administrators often postpone major version updates to web applications due to the frequent user impact and incompatibility with customized features. Web applications are a frequent target for attackers and vulnerabilities can be exploited days or even hours after their release. For this reason, configuring web applications to update automatically is imperative to secure web application servers. There are many web-based CMSs similar to DNN. Other common CMS’s are WordPress®4, Drupal®5 and Joomla®6. Organizations should be aware of CMS instances within their purview (i.e., blog, wiki, etc.) and ensure adequate processes are in place for timely updates. MITIGATION ACTIONS The most effective mitigation action is to update to the latest version of DNN, version 9.1.1, which is not vulnerable. A hotfix is available at dnnsoftware.com for older versions of DNN, but NSA recommends to only use the hotfix as a temporary measure while migrating to the latest version. -

The Drupal Decision
The Drupal Decision Stephen Sanzo | Director of Marketing and Business Development | Isovera [email protected] www.isovera.com Agenda 6 Open Source 6 The Big Three 6 Why Drupal? 6 Overview 6 Features 6 Examples 6 Under the Hood 6 Questions (non-technical, please) Open Source Software “Let the code be available to all!” 6 Software that is available in source code form for which the source code and certain other rights normally reserved for copyright holders are provided under a software license that permits users to study, change, and improve the software. 6 Adoption of open-source software models has resulted in savings of about $60 billion per year to consumers. http://en.wikipedia.org/wiki/Open-source_software www.isovera.com Open Source Software However… Open source doesn't just mean access to the source code. The distribution terms of open-source software must comply criteria established by the Open Source Initiative. http://www.opensource.org/docs/osd www.isovera.com Open Source Software Free as in… Not this… www.isovera.com Open Source CMS Advantages for Open Source CMS 6 No licensing fees - allows you to obtain enterprise quality software at little to no cost 6 Vendor flexibility - you can choose whether or not you want to hire a vendor to help you customize, implement, and support it, or do this internally. If at any point along the way you decide you don’t like your vendor, you are free to find another. 6 Software flexibility – in many cases, proprietary software is slow to react to the markets needs. -
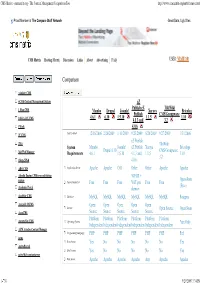
CMS Matrix - Cmsmatrix.Org - the Content Management Comparison Tool
CMS Matrix - cmsmatrix.org - The Content Management Comparison Tool http://www.cmsmatrix.org/matrix/cms-matrix Proud Member of The Compare Stuff Network Great Data, Ugly Sites CMS Matrix Hosting Matrix Discussion Links About Advertising FAQ USER: VISITOR Compare Search Return to Matrix Comparison <sitekit> CMS +CMS Content Management System eZ Publish eZ TikiWiki 1 Man CMS Mambo Drupal Joomla! Xaraya Bricolage Publish CMS/Groupware 4.6.1 6.10 1.5.10 1.1.5 1.10 1024 AJAX CMS 4.1.3 and 3.2 1Work 4.0.6 2F CMS Last Updated 12/16/2006 2/26/2009 1/11/2009 9/23/2009 8/20/2009 9/27/2009 1/31/2006 eZ Publish 2flex TikiWiki System Mambo Joomla! eZ Publish Xaraya Bricolage Drupal 6.10 CMS/Groupware 360 Web Manager Requirements 4.6.1 1.5.10 4.1.3 and 1.1.5 1.10 3.2 4Steps2Web 4.0.6 ABO.CMS Application Server Apache Apache CGI Other Other Apache Apache Absolut Engine CMS/news publishing 30EUR + system Open-Source Approximate Cost Free Free Free VAT per Free Free (Free) Academic Portal domain AccelSite CMS Database MySQL MySQL MySQL MySQL MySQL MySQL Postgres Accessify WCMS Open Open Open Open Open License Open Source Open Source AccuCMS Source Source Source Source Source Platform Platform Platform Platform Platform Platform Accura Site CMS Operating System *nix Only Independent Independent Independent Independent Independent Independent ACM Ariadne Content Manager Programming Language PHP PHP PHP PHP PHP PHP Perl acms Root Access Yes No No No No No Yes ActivePortail Shell Access Yes No No No No No Yes activeWeb contentserver Web Server Apache Apache -

Kosten Senken Dank Open Source?
View metadata, citation and similar papers at core.ac.uk brought to you by CORE Kosten senken dank Open Source? provided by Bern Open Repository andStrategien Information System (BORIS) | downloaded: 13.3.2017 https://doi.org/10.7892/boris.47380 source: 36 Nr. 01/02 | Februar 2014 Swiss IT Magazine Strategien Kosten senken dank Open Source? Mehr Geld im Portemonnaie und weniger Sorgen im Gepäck Der Einsatz von Open Source Software kann das IT-Budget schonen, wenn man richtig vorgeht. Viel wichtiger sind aber strategische Vorteile wie die digitale Nachhaltigkeit oder die Unabhängigkeit von Herstellern, die sich durch den konsequenten Einsatz von Open Source ergeben. V ON D R . M ATTHIAS S TÜR M ER ines vorweg: Open Source ist nicht gra- tis. Oder korrekt ausgedrückt: Der Download von Open Source Software (OSS) von den vielen Internet-Portalen wieE Github, Google Code, Sourceforge oder Freecode ist selbstverständlich kostenlos. Aber wenn Open-Source-Lösungen professionell eingeführt und betrieben werden, verursacht dies interne und/oder externe Kosten. Geschäftskritische Lösungen benötigen stets zuverlässige Wartung und Support, ansonsten steigt das Risiko erheblich, dass zentrale Infor- matiksysteme ausfallen oder wichtige Daten verloren gehen oder gestohlen werden. Für den sicheren Einsatz von Open Source Soft- ware braucht es deshalb entweder interne INHALT Ressourcen und Know-how, wie die entspre- chenden Systeme betrieben werden. Oder es MEHR GELD im PORTemoNNaie UND weNIGER SorgeN im GEPÄck 36 wird ein Service Level Agreement (SLA) bei- MarkTÜbersicHT: 152 SCHweiZer OPEN-SOUrce-SPEZialisTEN 40 spielsweise in Form einer Subscription mit einem kommerziellen Anbieter von Open- SpareN ODER NICHT spareN 48 Source-Lösungen abgeschlossen. -

Andrew Keats
Andrew Keats Genera Experienc Nationality British Aug 2019 - May 2020 Front-end Team Lead Date of Birth 12 November 1983 Toggle, Led delivery of a greenfield 187 Wardour Street, React-TypeScript SPA trading insight Soho app; complex data-driven UI using D3. Contac London Front-end Architect. In charge of a Telephone 07931998868 W1F 8ZB team of front-end developers; defined Email a [email protected] requirements, managed workloads. Defined best practices and set-up automated linting, unit tests and code Skill & Technologie quality processes. Responsible for CI Client & Front-end Development pipeline in GitLab, using Docker, Web Browser: TypeScript/JavaScript (ES5-2017, OO & NodeJS, and Kubernetes. Functional); Svelte, React, Aurelia, Backbone (SPA frameworks); Ramda, Lo-Dash, jQuery, (utility libraries); CSS, Oct 2018 – Aug 2019 Lead Front-end Developer SASS, PostCSS; HTML5 & Markdown; XML & XSLT. Equal Experts, Delivering a greenfield front-end service Desktop and Mobile: C#; .Net WinForms; Unity. 30 Brock St, for John Lewis, using GCP, Docker, Build tools: Parcel; Rollup; Webpack; Gulp; Grunt; Browserify. Kings Cross, NodeJS, isomorphic React with ES6 Test tools: RTL, Enzyme; Jest, Mocha, Karma, Jasmine; Cypress, London and modular SCSS. YAML driven CI. Selenium, ScalaTest.. NW1 3FG TDD using Jest; ATs using Kotlin and ChromeDriver. Back-end Development Server-side UIs: NodeJS with Polka/Express on GCP/Heroku, Apr 2017 – Sep 2017 Senior Front-end Developer SSR Svelte/React; Use of Scala with the Play framework & Clarksons Platou, Helping to deliver the front-end of a some Java; Experience with MS .Net (2-4), C#, use of DNN Commodity Quay, real-time, global shipping brokerage CMS and Episerver CMS; Experience with the Django St Katharine's & platform using TypeScript, Aurelia, AG framework; Some PHP (Wordpress & Laravel).