Extending Bitcoin's Proof of Work Via Proof of Stake
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Money Laundering Using Cryptocurrency: the Case of Bitcoin!
Athens Journal of Law - Volume 7, Issue 2, April 2021 – Pages 253-264 Money Laundering using Cryptocurrency: The Case of Bitcoin! By Gaspare Jucan Sicignano* The bitcoin, one of the most discussed topics in recent years, is a virtual currency with enormous potential and can be used almost immediately with no intervention from financial institutions. It has spread rapidly over the last few years, and all financial and governmental institutions have warned of the risk of its use for money laundering. The paper focuses on this aspect in order to understand if any purchases of bitcoins, using illicit money, can come under the anti-money laundering criminal law. Keywords: Bitcoin; Money laundering; Italian law; Cryptocurrency. Introduction The bitcoin1 is a virtual, decentralised and partially anonymous currency based on cryptography and peer-to-peer technology2. With bitcoins it is possible to buy any type of good or service securely and rapidly. Transactions need not be authorised by a central entity; rather, they are validated by all users of the platform. The system is totally secure, since it is practically impossible to hack the protocol3. Bitcoin has been much criticised over the last few years; it has quickly become public enemy number one for everything from financing terrorism to drug dealing to money laundering. It has also recently been said that bitcoin would pollute the planet due to the resources required for mining4. This paper will attempt to analyse in depth the relationship between the bitcoin and money laundering in Italian law. It will analyse the warnings issued by authorities in various sectors, as well as the opinions expressed in Italian legal literature regarding the possibility of committing money laundering and self- laundering crimes in various operations carried out using virtual currency. -

Bitcoin Tumbles As Miners Face Crackdown - the Buttonwood Tree Bitcoin Tumbles As Miners Face Crackdown
6/8/2021 Bitcoin Tumbles as Miners Face Crackdown - The Buttonwood Tree Bitcoin Tumbles as Miners Face Crackdown By Haley Cafarella - June 1, 2021 Bitcoin tumbles as Crypto miners face crackdown from China. Cryptocurrency miners, including HashCow and BTC.TOP, have halted all or part of their China operations. This comes after Beijing intensified a crackdown on bitcoin mining and trading. Beijing intends to hammer digital currencies amid heightened global regulatory scrutiny. This marks the first time China’s cabinet has targeted virtual currency mining, which is a sizable business in the world’s second-biggest economy. Some estimates say China accounts for as much as 70 percent of the world’s crypto supply. Cryptocurrency exchange Huobi suspended both crypto-mining and some trading services to new clients from China. The plan is that China will instead focus on overseas businesses. BTC.TOP, a crypto mining pool, also announced the suspension of its China business citing regulatory risks. On top of that, crypto miner HashCow said it would halt buying new bitcoin mining rigs. Crypto miners use specially-designed computer equipment, or rigs, to verify virtual coin transactions. READ MORE: Sustainable Mineral Exploration Powers Electric Vehicle Revolution This process produces newly minted crypto currencies like bitcoin. “Crypto mining consumes a lot of energy, which runs counter to China’s carbon neutrality goals,” said Chen Jiahe, chief investment officer of Beijing-based family office Novem Arcae Technologies. Additionally, he said this is part of China’s goal of curbing speculative crypto trading. As result, bitcoin has taken a beating in the stock market. -

Initial Coin Offerings: Financing Growth with Cryptocurrency Token
Initial Coin Offerings: Financing Growth with Cryptocurrency Token Sales Sabrina T. Howell, Marina Niessner, and David Yermack⇤ June 21, 2018 Abstract Initial coin offerings (ICOs) are sales of blockchain-based digital tokens associated with specific platforms or assets. Since 2014 ICOs have emerged as a new financing instrument, with some parallels to IPOs, venture capital, and pre-sale crowdfunding. We examine the relationship between issuer characteristics and measures of success, with a focus on liquidity, using 453 ICOs that collectively raise $5.7 billion. We also employ propriety transaction data in a case study of Filecoin, one of the most successful ICOs. We find that liquidity and trading volume are higher when issuers offer voluntary disclosure, credibly commit to the project, and signal quality. s s ss s ss ss ss s ⇤NYU Stern and NBER; Yale SOM; NYU Stern, ECGI and NBER. Email: [email protected]. For helpful comments, we are grateful to Bruno Biais, Darrell Duffie, seminar participants at the OECD Paris Workshop on Digital Financial Assets, Erasmus University, and the Swedish House of Finance. We thank Protocol Labs and particularly Evan Miyazono and Juan Benet for providing data. Sabrina Howell thanks the Kauffman Foundation for financial support. We are also grateful to all of our research assistants, especially Jae Hyung (Fred) Kim. Part of this paper was written while David Yermack was a visiting professor at Erasmus University Rotterdam. 1Introduction Initial coin offerings (ICOs) may be a significant innovation in entrepreneurial finance. In an ICO, a blockchain-based venture raises capital by selling cryptographically secured digital assets, usually called “tokens.” These ventures often resemble the startups that conventionally finance themselves with angel or venture capital (VC) investment, though there are many scams, jokes, and tokens that have nothing to do with a new product or business. -

Bitcoin Making Gold Redundant?
March 2021 Edition BloombergMarch 2021 GalaxyEdition Crypto Index (BGCI) Bloomberg Crypto Outlook 2021 Bloomberg Crypto Outlook Bitcoin Making Gold Redundant? `There's No Alternative' Tilting Toward Bitcoin vs. Gold, Stocks Bitcoin $40,000-$60,000 Consolidation and 60/40 Mix Migration Grayscale Bitcoin Trust Discount May Signal March to $100,000 Bitcoin Replacing Gold Is Happening -- A Question of Endurance Death, Taxes and Bitcoin Volatility Dropping Toward Gold, Amazon Worried About Bitcoin Sellers? They Appear Similar to 2017 Start 1 March 2021 Edition Bloomberg Crypto Outlook 2021 CONTENTS 3 Overview 3 60/40 Mix Migration 5 Rising Bitcoin Wave and GBTC 5 Bitcoin Is Replacing Gold 6 Bitcoin Volatity In Decline 7 Diminishing Bitcon Supply, Reluctant Sellers 2 March 2021 Edition Bloomberg Crypto Outlook 2021 Learn more about Bloomberg Indices Most data and outlook as of March 2, 2021 Mike McGlone – BI Senior Commodity Strategist BI COMD (the commodity dashboard) Note ‐ Click on graphics to get to the Bloomberg terminal `There's No Alternative' Tilting Toward Bitcoin vs. Gold, Stocks $100,000 May Be Bitcoin's Next Threshold. Maturation makes sense in the Bitcoin price-discovery process, but we see the upward trajectory more likely to simply stay the Performance: Bloomberg Galaxy Cypto Index (BGCI) course on rising demand vs. declining supply and an February +24%, 2021 to March 2: +77% increasingly favorable macroeconomic environment. Having February +40%, 2021 +64% Bitcoin met the initial 2021 threshold just above $50,000 and a $1 trillion market cap, the benchmark crypto asset is ripe to (Bloomberg Intelligence) -- Bitcoin in 2021 is transitioning stabilize for awhile, with $40,000 marking initial retracement from a speculative risk asset to a global digital store-of-value, support. -
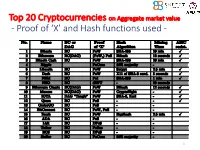
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Consent Order: HDR Global Trading Limited, Et Al
Case 1:20-cv-08132-MKV Document 62 Filed 08/10/21 Page 1 of 22 UNITED STATES DISTRICT COURT SOUTHERN DISTRICT OF NEW YORK USDC SDNY DOCUMENT ELECTRONICALLY FILED COMMODITY FUTURES TRADING DOC #: COMMISSION, DATE FILED: 8/10/2021 Plaintiff v. Case No. 1:20-cv-08132 HDR GLOBAL TRADING LIMITED, 100x Hon. Mary Kay Vyskocil HOLDINGS LIMITED, ABS GLOBAL TRADING LIMITED, SHINE EFFORT INC LIMITED, HDR GLOBAL SERVICES (BERMUDA) LIMITED, ARTHUR HAYES, BENJAMIN DELO, and SAMUEL REED, Defendants CONSENT ORDER FOR PERMANENT INJUNCTION, CIVIL MONETARY PENALTY, AND OTHER EQUITABLE RELIEF AGAINST DEFENDANTS HDR GLOBAL TRADING LIMITED, 100x HOLDINGS LIMITED, SHINE EFFORT INC LIMITED, and HDR GLOBAL SERVICES (BERMUDA) LIMITED I. INTRODUCTION On October 1, 2020, Plaintiff Commodity Futures Trading Commission (“Commission” or “CFTC”) filed a Complaint against Defendants HDR Global Trading Limited (“HDR”), 100x Holdings Limited (100x”), ABS Global Trading Limited (“ABS”), Shine Effort Inc Limited (“Shine”), and HDR Global Services (Bermuda) Limited (“HDR Services”), all doing business as “BitMEX” (collectively “BitMEX”) as well as BitMEX’s co-founders Arthur Hayes (“Hayes”), Benjamin Delo (“Delo”), and Samuel Reed (“Reed”), (collectively “Defendants”), seeking injunctive and other equitable relief, as well as the imposition of civil penalties, for violations of the Commodity Exchange Act (“Act”), 7 U.S.C. §§ 1–26 (2018), and the Case 1:20-cv-08132-MKV Document 62 Filed 08/10/21 Page 2 of 22 Commission’s Regulations (“Regulations”) promulgated thereunder, 17 C.F.R. pts. 1–190 (2020). (“Complaint,” ECF No. 1.)1 II. CONSENTS AND AGREEMENTS To effect settlement of all charges alleged in the Complaint against Defendants HDR, 100x, ABS, Shine, and HDR Services (“Settling Defendants”) without a trial on the merits or any further judicial proceedings, Settling Defendants: 1. -

Cryptocurrency: the Economics of Money and Selected Policy Issues
Cryptocurrency: The Economics of Money and Selected Policy Issues Updated April 9, 2020 Congressional Research Service https://crsreports.congress.gov R45427 SUMMARY R45427 Cryptocurrency: The Economics of Money and April 9, 2020 Selected Policy Issues David W. Perkins Cryptocurrencies are digital money in electronic payment systems that generally do not require Specialist in government backing or the involvement of an intermediary, such as a bank. Instead, users of the Macroeconomic Policy system validate payments using certain protocols. Since the 2008 invention of the first cryptocurrency, Bitcoin, cryptocurrencies have proliferated. In recent years, they experienced a rapid increase and subsequent decrease in value. One estimate found that, as of March 2020, there were more than 5,100 different cryptocurrencies worth about $231 billion. Given this rapid growth and volatility, cryptocurrencies have drawn the attention of the public and policymakers. A particularly notable feature of cryptocurrencies is their potential to act as an alternative form of money. Historically, money has either had intrinsic value or derived value from government decree. Using money electronically generally has involved using the private ledgers and systems of at least one trusted intermediary. Cryptocurrencies, by contrast, generally employ user agreement, a network of users, and cryptographic protocols to achieve valid transfers of value. Cryptocurrency users typically use a pseudonymous address to identify each other and a passcode or private key to make changes to a public ledger in order to transfer value between accounts. Other computers in the network validate these transfers. Through this use of blockchain technology, cryptocurrency systems protect their public ledgers of accounts against manipulation, so that users can only send cryptocurrency to which they have access, thus allowing users to make valid transfers without a centralized, trusted intermediary. -

Blockchain & Cryptocurrency Regulation
Blockchain & Cryptocurrency Regulation Third Edition Contributing Editor: Josias N. Dewey Global Legal Insights Blockchain & Cryptocurrency Regulation 2021, Third Edition Contributing Editor: Josias N. Dewey Published by Global Legal Group GLOBAL LEGAL INSIGHTS – BLOCKCHAIN & CRYPTOCURRENCY REGULATION 2021, THIRD EDITION Contributing Editor Josias N. Dewey, Holland & Knight LLP Head of Production Suzie Levy Senior Editor Sam Friend Sub Editor Megan Hylton Consulting Group Publisher Rory Smith Chief Media Officer Fraser Allan We are extremely grateful for all contributions to this edition. Special thanks are reserved for Josias N. Dewey of Holland & Knight LLP for all of his assistance. Published by Global Legal Group Ltd. 59 Tanner Street, London SE1 3PL, United Kingdom Tel: +44 207 367 0720 / URL: www.glgroup.co.uk Copyright © 2020 Global Legal Group Ltd. All rights reserved No photocopying ISBN 978-1-83918-077-4 ISSN 2631-2999 This publication is for general information purposes only. It does not purport to provide comprehensive full legal or other advice. Global Legal Group Ltd. and the contributors accept no responsibility for losses that may arise from reliance upon information contained in this publication. This publication is intended to give an indication of legal issues upon which you may need advice. Full legal advice should be taken from a qualified professional when dealing with specific situations. The information contained herein is accurate as of the date of publication. Printed and bound by TJ International, Trecerus Industrial Estate, Padstow, Cornwall, PL28 8RW October 2020 PREFACE nother year has passed and virtual currency and other blockchain-based digital assets continue to attract the attention of policymakers across the globe. -

Does the Hashrate Affect the Bitcoin Price?
Journal of Risk and Financial Management Article Does the Hashrate Affect the Bitcoin Price? Dean Fantazzini 1,* and Nikita Kolodin 2 1 Moscow School of Economics, Moscow State University, Leninskie Gory, 1, Building 61, Moscow 119992, Russia 2 Higher School of Economics, Moscow 109028, Russia; [email protected] * Correspondence: [email protected]; Tel.: +7-4955105267; Fax: +7-4955105256 Received: 30 September 2020; Accepted: 27 October 2020; Published: 30 October 2020 Abstract: This paper investigates the relationship between the bitcoin price and the hashrate by disentangling the effects of the energy efficiency of the bitcoin mining equipment, bitcoin halving, and of structural breaks on the price dynamics. For this purpose, we propose a methodology based on exponential smoothing to model the dynamics of the Bitcoin network energy efficiency. We consider either directly the hashrate or the bitcoin cost-of-production model (CPM) as a proxy for the hashrate, to take any nonlinearity into account. In the first examined subsample (01/08/2016–04/12/2017), the hashrate and the CPMs were never significant, while a significant cointegration relationship was found in the second subsample (11/12/2017–24/02/2020). The empirical evidence shows that it is better to consider the hashrate directly rather than its proxy represented by the CPM when modeling its relationship with the bitcoin price. Moreover, the causality is always unidirectional going from the bitcoin price to the hashrate (or its proxies), with lags ranging from one week up to six weeks later. These findings are consistent with a large literature in energy economics, which showed that oil and gas returns affect the purchase of the drilling rigs with a delay of up to three months, whereas the impact of changes in the rig count on oil and gas returns is limited or not significant. -

A Probe Survey of Bitcoin Transactions Through Analysis of Advertising in an On-Line Discussion Forum
Acta Informatica Pragensia, 2019, 8(2), 112–131 DOI: 10.18267/j.aip.127 Original Article A Probe Survey of Bitcoin Transactions Through Analysis of Advertising in an On-Line Discussion Forum Zoltan Ban 1, Jan Lansky 1, Stanislava Mildeova 1, Petr Tesar 1 Abstract Cryptocurrencies have become a major phenomenon in recent years. For IT, a breakthrough is both the cryptocurrency itself as a commodity and the technology that cryptocurrency development has brought. The article focuses on the bitcoin cryptocurrency as the most important cryptocurrency. A relatively unexplored topic is what goods or services are purchased for bitcoins. To track what bitcoins are spent on, it is necessary to look for places that are dedicated to trading cryptocurrencies. The bitcointalk.org forum was chosen as a source for our data mining. The aim of the article is to find an answer to the research question: What are bitcoins on the discussion forum bitcointalk.org planned to be spent on? As part of the research, an application was developed using a PHP script to gather information from the discussion forum (bitcointalk.org). There is some evidence which suggests what types of products or services people spend cryptocurrencies on. This research has proven that cryptocurrencies are used to buy and sell goods or services in the electronics and computer world segments. Today, these segments are widespread, which may speed up the integration of cryptocurrencies into everyday life. This applies, of course, only if the risks associated with cryptocurrencies do not increase. Keywords: Cryptocurrency, Bitcoin, On-Line Advertisement, Text Mining, Cybersecurity, Discussion Forum. -

Download Criminal Complaint Filed in the Eastern District of California
AO 91 (Rev. 11/11) Criminal Complaint UNITED STATES DISTRICT COURT for the Eastern District of California United States of America ) V. ) MARCOS PAULO DE OLIVEIRA ) Case No. ANNIBALE, ) aka "Med3lin," ) aka "Med3lln," ) aka "Med3lln WSM" ) Defendant(s) CRIMINAL COMPLAINT I, the complainant in this case, state that the following is true to the best of my knowledge and belief. On or about the date( s) of October 2017 through April 2019__ in the county of Sacramento in the Eastern District of California , and elsewhere, the defendant(s) violated: Code Section Offense Description 21 U.S.C. §§ 841 and 846 Distribution and Conspiracy to Distribute Controlled Substances 18 U.S.C. §§ 1956 and 1957 Money Laundering This criminal complaint is based on these facts: (see attachment) IX! Continued on the attached sheet. -j- ;1 ·) / , / l 1 - • / L ',;;;_ . _/__I-- / Complainant's signature JAY D. DIAL, Jr., Special Agent Dl'llg Enforcem~_11t Ad111inistration Printed name and title Sworn to before me and signed in my presence. ;]t "-" ' Date: l.2 _/,_ I ---=- (.___ ,,--- "'-~ Judge 's signature City and state: Sacramento, CA Allls__on Claire, U_.§~ Magi~trate__.J__udge Printed name and title AO 91 (Rev. 11/11) Criminal Complaint UNITED STATES DISTRICT COURT for the Eastern District of California United States of America ) V. ) MARCOS PAULO DE OLIVEIRA ) Case No. ANNIBALE, ) aka "Med3lin," ) aka "Med3l1n," ) aka "Med3lln_WSM" ) Defendant(s) CRIMINAL COMPLAINT I, the complainant in this case, state that the following is true to the best of my knowledge and belief. On or about the date(s) of ~tober 20 I 7 through April 2019_ in the county of . -

Bitcoin and Cryptocurrencies Law Enforcement Investigative Guide
2018-46528652 Regional Organized Crime Information Center Special Research Report Bitcoin and Cryptocurrencies Law Enforcement Investigative Guide Ref # 8091-4ee9-ae43-3d3759fc46fb 2018-46528652 Regional Organized Crime Information Center Special Research Report Bitcoin and Cryptocurrencies Law Enforcement Investigative Guide verybody’s heard about Bitcoin by now. How the value of this new virtual currency wildly swings with the latest industry news or even rumors. Criminals use Bitcoin for money laundering and other Enefarious activities because they think it can’t be traced and can be used with anonymity. How speculators are making millions dealing in this trend or fad that seems more like fanciful digital technology than real paper money or currency. Some critics call Bitcoin a scam in and of itself, a new high-tech vehicle for bilking the masses. But what are the facts? What exactly is Bitcoin and how is it regulated? How can criminal investigators track its usage and use transactions as evidence of money laundering or other financial crimes? Is Bitcoin itself fraudulent? Ref # 8091-4ee9-ae43-3d3759fc46fb 2018-46528652 Bitcoin Basics Law Enforcement Needs to Know About Cryptocurrencies aw enforcement will need to gain at least a basic Bitcoins was determined by its creator (a person Lunderstanding of cyptocurrencies because or entity known only as Satoshi Nakamoto) and criminals are using cryptocurrencies to launder money is controlled by its inherent formula or algorithm. and make transactions contrary to law, many of them The total possible number of Bitcoins is 21 million, believing that cryptocurrencies cannot be tracked or estimated to be reached in the year 2140.