Deployment, Ddos Impact
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Munin Documentation Release 2.0.44
Munin Documentation Release 2.0.44 Stig Sandbeck Mathisen <[email protected]> Dec 20, 2018 Contents 1 Munin installation 3 1.1 Prerequisites.............................................3 1.2 Installing Munin...........................................4 1.3 Initial configuration.........................................7 1.4 Getting help.............................................8 1.5 Upgrading Munin from 1.x to 2.x..................................8 2 The Munin master 9 2.1 Role..................................................9 2.2 Components.............................................9 2.3 Configuration.............................................9 2.4 Other documentation.........................................9 3 The Munin node 13 3.1 Role.................................................. 13 3.2 Configuration............................................. 13 3.3 Other documentation......................................... 13 4 The Munin plugin 15 4.1 Role.................................................. 15 4.2 Other documentation......................................... 15 5 Documenting Munin 21 5.1 Nomenclature............................................ 21 6 Reference 25 6.1 Man pages.............................................. 25 6.2 Other reference material....................................... 40 7 Examples 43 7.1 Apache virtualhost configuration.................................. 43 7.2 lighttpd configuration........................................ 44 7.3 nginx configuration.......................................... 45 7.4 Graph aggregation -

Rrdtool – Perl Module • Net::Snmptrapd(Install It from CPAN by Root) • Netsnmp::Agent(Embedded on Net-Snmp) Requirement – SNMP Agent
Homework 5 DNS、HTTPD、SNMP Requirements One dedicated domain name for yourself Setup DNS server with following records SOA, NS, MX Make them reasonable NS Delegation (with team mates) Dedicate a sub domain to each of your team mates Building a slave server for your team mate And a stub server for another team mate Updates should be synchronized Reverse resolution for your NAT 192.168.x.0/24 for each of team mates Requirements (Cont.) slave a.nctucs.net 140.113.a.a stub 192.168.0.1/24 b.nctucs.net c.nctucs.net 140.113.b.b 140.113.c.c 192.168.0.2/24 192.168.0.3/24 Requirements (Cont.) View Create view.example.csie.net A record: Queries from 192.168.0.0/24: view.example.csie.net A 192.168.0.1 Otherwise, get your normal ip Logging Record all records to /var/log/named.log Do log rotate Note: you will be asked for explaining the what does the log entry means in named.log Requirements (Cont.) SPF/DomainKeys record for your server Add resonable SPF/DomainKeys records Configure your mail system to support these feature SSHFP record for your server Make a reasonable setting Requirements (Cont.) Dynamic DNS update Your DNS should accept the update requests from 140.113.17.225 and your team mates You should know how to update a dns record Management Your DNS server should support TSIG and allow the connection from 140.113.17.225 Your DNS server should only allow the AXFR request from 140.113.17.225 Only allow recursion query from your team mates and 140.113.17.225 Appendix Use ldap as backend database dns/bind9-sdb-ldap http://www.openldap.org/ http://bind9-ldap.bayour.com/ SPF setup wizard http://old.openspf.org/wizard.html DKIMproxy http://dkimproxy.sourceforge.net HTTPD Requirements HTTPD apache, lighttpd, nginx, etc. -

The Cacti Manual.Pdf
The Cacti Manual Ian Berry Tony Roman Larry Adams J.P. Pasnak Jimmy Conner Reinhard Scheck Andreas Braun The Cacti Manual by Ian Berry, Tony Roman, Larry Adams, J.P. Pasnak, Jimmy Conner, Reinhard Scheck, and Andreas Braun Published 2017 Copyright © 2017 The Cacti Group This project is licensed under the terms of the GPL. This program is free software; you can redistribute it and/or modify it under the terms of the GNU General Public License as published by the Free Software Foundation; either version 2 of the License, or (at your option) any later version. This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY; without even the implied warranty of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the GNU General Public License for more details. All product names are property of their respective owners. Such names are used for identification purposes only and are not indicative of endorsement by or of any company, organization, product, or platform. Table of Contents I. Installation...................................................................................................................................................................................1 1. Requirements.....................................................................................................................................................................1 2. Installing Under Unix.......................................................................................................................................................2 -

Storage of Network Monitoring and Measurement Data
Storage of Network Monitoring and Measurement Data A report submitted in partial fulfillment of the requirements for the degree of Bachelor of Computing and Mathematical Sciences at The University of Waikato by Nathan Overall c 2012 Nathan Overall Abstract Despite the limitations of current network monitoring tools, there has been little investigation into providing a viable alternative. Network operators need high resolution data over long time periods to make informed decisions about their networks. Current solutions discard data or do not provide the data in a practical format. This report addresses this problem and explores the development of a new solution to address these problems. Acknowledgements I would like to show my appreciation to the following persons who have made this project possible. Members of the WAND Network group for their continued support during the project, including my supervisor Richard Nelson. I would also like to give a special mention to Shane Alcock and Brendon Jones for their ongoing assistance to the project while they developed the WAND Network Event Monitor. DR. Scott Raynel for his support and advice throughout the project. The WAND network group and Lightwire LTD for providing the resources necessary to conduct the project. Contents List of Acronyms vi List of Figures vii 1 Introduction1 1.1 Network Operation.......................1 1.2 Overview of the Problem....................2 1.3 Goals...............................2 1.4 Plan of Action..........................3 2 Background4 2.1 Introduction...........................4 2.2 Round Robin Database.....................4 2.3 Tools using Round Robin Database (RRD)..........8 2.3.1 Smokeping...........................8 2.3.2 Cacti..............................9 2.4 The Active Measurement Project...............9 2.5 OpenTSDB.......................... -

Performance-Analyse in Großen Umgebungen Mit Collectd
Performance-Analyse in großen Umgebungen mit collectd Performance-Analyse in großen Umgebungen mit collectd Sebastian tokkee\ Harl " <[email protected]> FrOSCon 2009 2009-08-22 Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Gliederung Was ist collectd? Wichtige Eigenschaften Wichtige Plugins Eigene Erweiterungen Uber¨ den Tellerrand Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Was ist collectd? I collectd sammelt Leistungsdaten von Rechnern I Leistungsdaten sind zum Beispiel: I CPU-Auslastung I Speichernutzung I Netzwerkverkehr I Daten werden erhoben, verarbeitet und gespeichert I H¨aufig: Darstellung als Graphen I Nicht verwechseln mit Monitoring! Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Kontakt I Homepage: http://collectd.org/ I Mailinglist: [email protected] I IRC: #collectd auf irc.freenode.net Web 2.0\: http://identi.ca/collectd I " Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Wichtige Eigenschaften Wichtige Eigenschaften I Daemon I Freie Software (gr¨oßtenteils GPLv2) I Portierbar (Linux, *BSD, Solaris, . ) I Skalierbar (OpenWrt, . , Cluster / Cloud) I Effizient (Default-Aufl¨osung: 10 Sekunden) I Modular (Uber¨ 70 Plugins) Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Wichtige Eigenschaften Wichtige Eigenschaften I Daemon I Freie Software (gr¨oßtenteils GPLv2) I Portierbar (Linux, *BSD, Solaris, . ) I Skalierbar (OpenWrt, . , Cluster / Cloud) I Effizient (Default-Aufl¨osung: 10 Sekunden) I Modular (Uber¨ 70 Plugins) Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Wichtige Eigenschaften Wichtige Eigenschaften: 10-Sekunden-Aufl¨osung Performance-Analyse in großen Umgebungen mit collectd Was ist collectd? Wichtige Eigenschaften Wichtige Eigenschaften I Daemon I Freie Software (gr¨oßtenteils GPLv2) I Portierbar (Linux, *BSD, Solaris, . -

MRTG the Multi Router Traffic Grapher
The following paper was originally published in the Proceedings of the Twelfth Systems Administration Conference (LISA ’98) Boston, Massachusetts, December 6-11, 1998 MRTG The Multi Router Traffic Grapher Tobias Oetiker Swiss Federal Institute of Technology, Zurich For more information about USENIX Association contact: 1. Phone: 510 528-8649 2. FAX: 510 548-5738 3. Email: [email protected] 4. WWW URL: http://www.usenix.org MRTG – The Multi Router Traffic Grapher Tobias Oetiker – Swiss Federal Institute of Technology, Zurich ABSTRACT This paper describes the history and operation of the current version of MRTG as well as the Round Robin Database Tool. The Round Robin Database Tool is a program which logs and visualizes numerical data in a efficient manner. The RRD Tool is a key component of the next major release of the Multi Router Traffic Grapher (MRTG). It is already fully implemented and working. Because of the massive performance gain possible with RRD Tool some sites have already started to use RRD Tool in production. Motivation MRTG logged its data to an ASCII file, rewriting it every five minutes, constantly consolidating it, so In Summer 1994, the De Montfort University in that the logfile would not grow over time. The logfile Leicester, UK, had one 64 kBit Internet link for more did only store slightly more data than was needed to than 1000 networked computers. As it was not possi- draw the graphs on the web page. The graphs were ble to get a faster Internet link for another year, it was converted to GIF format by piping a graph in PNM desirable to at least provide the users on campus with format to the pnmtogif tool from the PBM pack- current and detailed information about the status of the age. -

RES Application Guide
ATTENTION This is NOT the application form to access RES resources. This document has been created only as a guide showing the information needed to fill the application form online. All the applications must be presented through the online form available at https://www.bsc.es/res-intranet/. 1. General Information a) Activity Title b) Area (select): Astronomy, Space and Earth Sciences Life and Health Sciences Physics Engineering and Mathematics Homogeneous Chemistry Heterogeneous Chemistry and Solids 2. Research Project Description a) Is this a Test Activity? Yes / No b) Is this a Long Term Activity that will extend over two application periods? Yes / No c) Brief description of the Project If this Activity takes place in the context of a Scientific Research Project, give a brief description of the Project, including the reference of National or International grants which support it. Summarize the research in the context of the current state-of-the-art, including references if appropriate. (Maximum 5000 characters). d) Grant References e) Brief description of the Project (If this Activity takes place in the context of a Technology or Industrial Project) If this Activity takes place in the context of a Technology or Industrial Project, give a brief description of the Project, including the potential impact resulting from this activity, in measurable terms (potential for patent applications, competitive advance, prototypes, new products, economic impact, etc.). (Maximum 5000 characters). f) Specific Activity proposed Describe the specific Activity proposed. Discuss the need for Supercomputing facilities. Describe in detail the specific calculations you plan to do, and their relevance to the Research Project. -

Ivoyeur Changing the Game, Part 2
iVoyeur Changing the Game, Part 2 DAVE JOSEPHSEN Dave Josephsen is the Near the end of his poem “The Talking Oak,” Tennyson alludes to the oldest of the author of Building a pagan oracles: Jupiter at Dodona . It was quite different from the oracles that fol- Monitoring Infrastructure lowed it in that no temple, altar, or human contrivance was ever constructed there . with Nagios (Prentice It was merely an oak grove on an island in the Aegean Sea . The Selli tribal priests Hall PTR, 2007) and is senior systems who lived there could decipher the word of Jupiter himself from the sound of the engineer at DBG, Inc., where he maintains wind rustling the leaves of those sacred oak trees (some stories say wind-chimes a gaggle of geographically dispersed server were also employed) . farms. He won LISA ’04’s Best Paper award for I’d read Tennyson’s poem in high school but, that being pre-Google, I never under- his co-authored work on spam mitigation, and stood his reference to “that Thessalian growth” until I recently happened to read he donates his spare time to the SourceMage about the oracle at Dodona . The resolution of that long-forgotten enigma must GNU Linux Project. have made an impression on my subconscious, because I subsequently dreamt that [email protected] I visited that ancient oracular forest and heard the whisper of its long-dead deity . His message to me? “Your Web server is down ”. I often tell people, when the subject of my occupation arises, that I’m a plumber . -

Monitoring Tools for Network Services and Systems Best Practice Document
Monitoring Tools for Network Services and Systems Best Practice Document Produced by CSC/Funet led working group on AccessFunet Author[s]: Kaisa Haapala, Janne Oksanen 13.05.2011 © TERENA 2010. All rights reserved. Document No: GN3-NA3-T4-Monitoring-Tools Version / date: 13.05.2011 Original language : Finnish Original title: “Verkon palvelujen ja järjestelmien valvontatyökaluja” Original version / date: 1.0 of 13.05.2011 Contact: kaisa.haapala (at) csc.fi CSC/Funet bears responsibility for the content of this document. The work has been carried out by a CSC/Funet led working group on AccessFunet as part of a joint-venture project within the HE sector in Finland. This translated version is based on the Finnish counterpart approved by the CSC/Funet annual general meeting on 13 May 2011 after an open consultation period of two weeks. Parts of the report may be freely copied, unaltered, provided that the original source is acknowledged and copyright preserved. The research leading to these results has received funding from the European Community's Seventh Framework Programme (FP7/2007-2013) under grant agreement n° 238875, relating to the project 'Multi-Gigabit European Research and Education Network and Associated Services (GN3)'. 2 Table of Contents 1. Introduction ......................................................................................................................... 4 2. Planning Monitoring ............................................................................................................ 4 3. Different Technical -
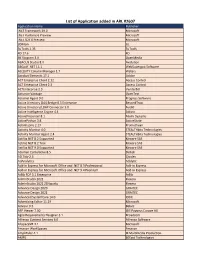
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Evaluating Web Development Frameworks: Django, Ruby on Rails and Cakephp
Evaluating web development frameworks: Django, Ruby on Rails and CakePHP Julia Plekhanova Temple University © September 2009 Institute for Business and Information Technology Fox School of Business Temple University The IBIT Report © 2009 Institute for Business and Information Technology, Bruce Fadem Fox School of Business, Temple University, Philadelphia, PA Editor-in-chief 19122, USA. All rights reserved. ISSN 1938-1271. Retired VP and CIO, Wyeth The IBIT Report is a publication for the members of the Fox Munir Mandviwalla School’s Institute for Business and Information Technology. IBIT reports are written for industry and based on rigorous Editor academic research and vendor neutral analysis. For additional Associate Professor and Executive Director reports, please visit our website at http://ibit.temple.edu. Fox School of Business, Temple University No part of this publication may be reproduced, stored in a Laurel Miller retrieval system or transmitted in any form or by any means, Managing Editor electronic, mechanical, photocopying, recording, scanning Director, Fox School of Business, Temple University or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher Board of editors for permission should be addressed to Institute for Business and Information Technology, Fox School of Business, Temple Andrea Anania University, 1810 N. 13th Street, Philadelphia, PA 19122, Retired VP and CIO, CIGNA USA, 215.204.5642, or [email protected]. Jonathan A. Brassington Disclaimer: The conclusions and statements of this report Founding Partner and CEO are solely the work of the authors. They do not represent LiquidHub Inc. -

Open Source Licenses
Threat Protection System v5.1.0 Open Source Licenses The TippingPoint Threat Protection System (TPS) devices use open source components. Many open source license agreements require user documentation to contain notification that the open source software is included in the product. For inquiries about acquiring license code, contact support. The following agreements are for software that this product includes or may include: • "BIND License Agreement" on page 9 • "boost License Agreement" on page 10 • "coreutils License Agreement regarding coreutils & libmspack" on page 11 • "corosync License Agreement" on page 20 • "cpputest License Agreement" on page 21 • "License Agreement regarding dbus; ecryptfs-utils; gdb; glibc; gptfdisk; ipset; keyutils; libcgi; libnih; libstatgrab; linux; lm-sensors; lttng; mxml; net-tools; open-vm-tools; pam-tacplus; rng-tools; RRDTool; syslog-ng; upstart & util-linux" on page 22 • "gSoap License Agreement" on page 26 • "host-sflow License Agreement" on page 33 • "ipmitool License Agreement" on page 38 • "jitterentropy-rngd License Agreement" on page 39 • "libpcap License Agreement" on page 40 • "libxml License Agreement" on page 41 • "NTP License Agreement" on page 42 • "OpenSSH License Agreement" on page 43 • "License Agreement regarding OpenSSL & openssl-fips" on page 49 • "qDecoder License Agreement" on page 52 • "shadow License Agreement" on page 53 • "tcpdump License Agreement" on page 55 TippingPoint acknowledges that the following open source components may be used in this product: • Adaptive Public License