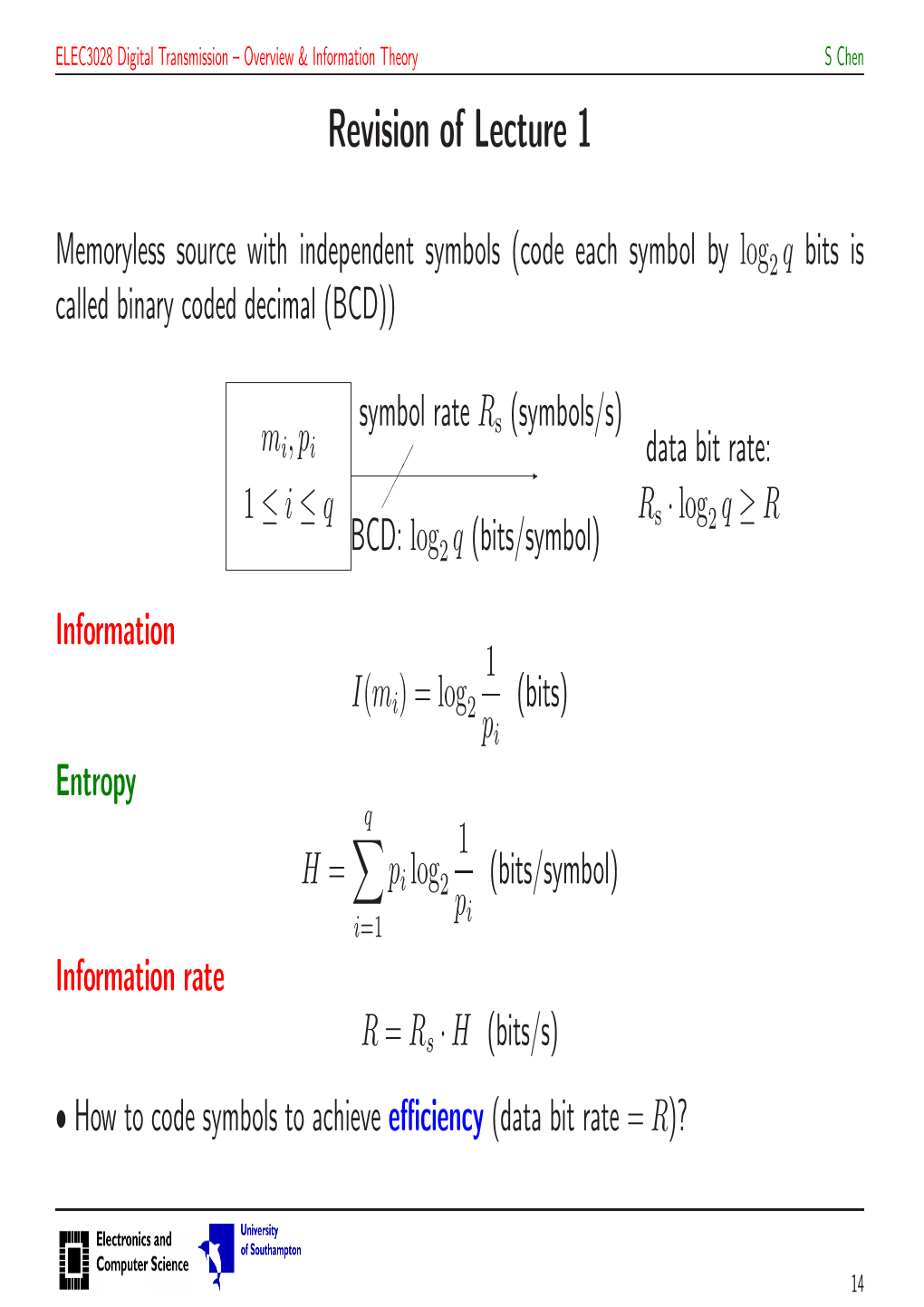
Revision of Lecture 1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

XAPP616 "Huffman Coding" V1.0
Product Obsolete/Under Obsolescence Application Note: Virtex Series R Huffman Coding Author: Latha Pillai XAPP616 (v1.0) April 22, 2003 Summary Huffman coding is used to code values statistically according to their probability of occurence. Short code words are assigned to highly probable values and long code words to less probable values. Huffman coding is used in MPEG-2 to further compress the bitstream. This application note describes how Huffman coding is done in MPEG-2 and its implementation. Introduction The output symbols from RLE are assigned binary code words depending on the statistics of the symbol. Frequently occurring symbols are assigned short code words whereas rarely occurring symbols are assigned long code words. The resulting code string can be uniquely decoded to get the original output of the run length encoder. The code assignment procedure developed by Huffman is used to get the optimum code word assignment for a set of input symbols. The procedure for Huffman coding involves the pairing of symbols. The input symbols are written out in the order of decreasing probability. The symbol with the highest probability is written at the top, the least probability is written down last. The least two probabilities are then paired and added. A new probability list is then formed with one entry as the previously added pair. The least symbols in the new list are then paired. This process is continued till the list consists of only one probability value. The values "0" and "1" are arbitrarily assigned to each element in each of the lists. Figure 1 shows the following symbols listed with a probability of occurrence where: A is 30%, B is 25%, C is 20%, D is 15%, and E = 10%. -

Image Compression Through DCT and Huffman Coding Technique
International Journal of Current Engineering and Technology E-ISSN 2277 – 4106, P-ISSN 2347 – 5161 ©2015 INPRESSCO®, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Image Compression through DCT and Huffman Coding Technique Rahul Shukla†* and Narender Kumar Gupta† †Department of Computer Science and Engineering, SHIATS, Allahabad, India Accepted 31 May 2015, Available online 06 June 2015, Vol.5, No.3 (June 2015) Abstract Image compression is an art used to reduce the size of a particular image. The goal of image compression is to eliminate the redundancy in a file’s code in order to reduce its size. It is useful in reducing the image storage space and in reducing the time needed to transmit the image. Image compression is more significant for reducing data redundancy for save more memory and transmission bandwidth. An efficient compression technique has been proposed which combines DCT and Huffman coding technique. This technique proposed due to its Lossless property, means using this the probability of loss the information is lowest. Result shows that high compression rates are achieved and visually negligible difference between compressed images and original images. Keywords: Huffman coding, Huffman decoding, JPEG, TIFF, DCT, PSNR, MSE 1. Introduction that can compress almost any kind of data. These are the lossless methods they retain all the information of 1 Image compression is a technique in which large the compressed data. amount of disk space is required for the raw images However, they do not take advantage of the 2- which seems to be a very big disadvantage during dimensional nature of the image data. -

The Strengths and Weaknesses of Different Image Compression Methods Samuel Teare and Brady Jacobson Lossy Vs Lossless
The Strengths and Weaknesses of Different Image Compression Methods Samuel Teare and Brady Jacobson Lossy vs Lossless Lossy compression reduces a file size by permanently removing parts of the data that may be redundant or not as noticeable. Lossless compression guarantees the original data can be recovered or decompressed from the compressed file. PNG Compression PNG Compression consists of three parts: 1. Filtering 2. LZ77 Compression Deflate Compression 3. Huffman Coding Filtering Five types of Filters: 1. None - No filter 2. Sub - difference between this byte and the byte to its left a. Sub(x) = Original(x) - Original(x - bpp) 3. Up - difference between this byte and the byte above it a. Up(x) = Original(x) - Above(x) 4. Average - difference between this byte and the average of the byte to the left and the byte above. a. Avg(x) = Original(x) − (Original(x-bpp) + Above(x))/2 5. Paeth - Uses the byte to the left, above, and above left. a. The nearest of the left, above, or above left to the estimate is the Paeth Predictor b. Paeth(x) = Original(x) - Paeth Predictor(x) Paeth Algorithm Estimate = left + above - above left Distance to left = Absolute(estimate - left) Distance to above = Absolute(estimate - above) Distance to above left = Absolute(estimate - above left) The byte with the smallest distance is the Paeth Predictor LZ77 Compression LZ77 Compression looks for sequences in the data that are repeated. LZ77 uses a sliding window to keep track of previous bytes. This is then used to compress a group of bytes that exhibit the same sequence as previous bytes. -

An Optimized Huffman's Coding by the Method of Grouping
An Optimized Huffman’s Coding by the method of Grouping Gautam.R Dr. S Murali Department of Electronics and Communication Engineering, Professor, Department of Computer Science Engineering Maharaja Institute of Technology, Mysore Maharaja Institute of Technology, Mysore [email protected] [email protected] Abstract— Data compression has become a necessity not only the 3 depending on the size of the data. Huffman's coding basically in the field of communication but also in various scientific works on the principle of frequency of occurrence for each experiments. The data that is being received is more and the symbol or character in the input. For example we can know processing time required has also become more. A significant the number of times a letter has appeared in a text document by change in the algorithms will help to optimize the processing processing that particular document. After which we will speed. With the invention of Technologies like IoT and in assign a variable string to the letter that will represent the technologies like Machine Learning there is a need to compress character. Here the encoding take place in the form of tree data. For example training an Artificial Neural Network requires structure which will be explained in detail in the following a lot of data that should be processed and trained in small paragraph where encoding takes place in the form of binary interval of time for which compression will be very helpful. There tree. is a need to process the data faster and quicker. In this paper we present a method that reduces the data size. -

Arithmetic Coding
Arithmetic Coding Arithmetic coding is the most efficient method to code symbols according to the probability of their occurrence. The average code length corresponds exactly to the possible minimum given by information theory. Deviations which are caused by the bit-resolution of binary code trees do not exist. In contrast to a binary Huffman code tree the arithmetic coding offers a clearly better compression rate. Its implementation is more complex on the other hand. In arithmetic coding, a message is encoded as a real number in an interval from one to zero. Arithmetic coding typically has a better compression ratio than Huffman coding, as it produces a single symbol rather than several separate codewords. Arithmetic coding differs from other forms of entropy encoding such as Huffman coding in that rather than separating the input into component symbols and replacing each with a code, arithmetic coding encodes the entire message into a single number, a fraction n where (0.0 ≤ n < 1.0) Arithmetic coding is a lossless coding technique. There are a few disadvantages of arithmetic coding. One is that the whole codeword must be received to start decoding the symbols, and if there is a corrupt bit in the codeword, the entire message could become corrupt. Another is that there is a limit to the precision of the number which can be encoded, thus limiting the number of symbols to encode within a codeword. There also exist many patents upon arithmetic coding, so the use of some of the algorithms also call upon royalty fees. Arithmetic coding is part of the JPEG data format. -

Image Compression Using Discrete Cosine Transform Method
Qusay Kanaan Kadhim, International Journal of Computer Science and Mobile Computing, Vol.5 Issue.9, September- 2016, pg. 186-192 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320–088X IMPACT FACTOR: 5.258 IJCSMC, Vol. 5, Issue. 9, September 2016, pg.186 – 192 Image Compression Using Discrete Cosine Transform Method Qusay Kanaan Kadhim Al-Yarmook University College / Computer Science Department, Iraq [email protected] ABSTRACT: The processing of digital images took a wide importance in the knowledge field in the last decades ago due to the rapid development in the communication techniques and the need to find and develop methods assist in enhancing and exploiting the image information. The field of digital images compression becomes an important field of digital images processing fields due to the need to exploit the available storage space as much as possible and reduce the time required to transmit the image. Baseline JPEG Standard technique is used in compression of images with 8-bit color depth. Basically, this scheme consists of seven operations which are the sampling, the partitioning, the transform, the quantization, the entropy coding and Huffman coding. First, the sampling process is used to reduce the size of the image and the number bits required to represent it. Next, the partitioning process is applied to the image to get (8×8) image block. Then, the discrete cosine transform is used to transform the image block data from spatial domain to frequency domain to make the data easy to process. -

Hybrid Compression Using DWT-DCT and Huffman Encoding Techniques for Biomedical Image and Video Applications
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology ISSN 2320–088X IJCSMC, Vol. 2, Issue. 5, May 2013, pg.255 – 261 RESEARCH ARTICLE Hybrid Compression Using DWT-DCT and Huffman Encoding Techniques for Biomedical Image and Video Applications K.N. Bharath 1, G. Padmajadevi 2, Kiran 3 1Department of E&C Engg, Malnad College of Engineering, VTU, India 2Associate Professor, Department of E&C Engg, Malnad College of Engineering, VTU, India 3Department of E&C Engg, Malnad College of Engineering, VTU, India 1 [email protected]; 2 [email protected]; 3 [email protected] Abstract— Digital image and video in their raw form require an enormous amount of storage capacity. Considering the important role played by digital imaging and video, it is necessary to develop a system that produces high degree of compression while preserving critical image/video information. There is various transformation techniques used for data compression. Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) are the most commonly used transformation. DCT has high energy compaction property and requires less computational resources. On the other hand, DWT is multi resolution transformation. In this work, we propose a hybrid DWT-DCT, Huffman algorithm for image and video compression and reconstruction taking benefit from the advantages of both algorithms. The algorithm performs the Discrete Cosine Transform (DCT) on the Discrete Wavelet Transform (DWT) coefficients. Simulations have been conducted on several natural, benchmarks, medical and endoscopic images. Several high definition and endoscopic videos have also been used to demonstrate the advantage of the proposed scheme. -

Implementation of a Fast Mpeg-2 Compliant Huffman Decoder
IMPLEMENTATION OF A FAST MPEG-2 COMPLIANT HUFFMAN DECODER Mikael Karlsson Rudberg ([email protected]) and Lars Wanhammar ([email protected]) Department of Electrical Engineering, Linköping University, S-581 83 Linköping, Sweden Tel: +46 13 284059; fax: +46 13 139282 ABSTRACT 2. HUFFMAN DECODER In this paper a 100 Mbit/s Huffman decoder Huffman decoding can be performed in a numerous implementation is presented. A novel approach ways. One common principle is to decode the where a parallel decoding of data mixed with a incoming bit stream in parallel [3, 4]. The serial input has been used. The critical path has simplified decoding process is described below: been reduced and a significant increase in throughput is achieved. The decoder is aimed at 1. Feed a symbol decoder and a length the MPEG-2 Video decoding standard and has decoder with M bits, where M is the length therefore been designed to meet the required of the longest code word. performance. 2. The symbol decoder maps the input vector to the corresponding symbol. A length 1. INTRODUCTION decoder will at the same time find the length of the input vector. Huffman coding is a lossless compression 3. The information from the length decoder is technique often used in combination with other used in the input buffer to fill up the buffer lossy compression methods, in for instance digital again (with between one and M bits, figure video and audio applications. The Huffman coding 1). method uses codes with different lengths, where symbols with high probability are assigned shorter The problem with this solution is the long critical codes than symbols with lower probability. -
Chapter 4 Information Theory
Chapter Information Theory Intro duction This lecture covers entropy joint entropy mutual information and minimum descrip tion length See the texts by Cover and Mackay for a more comprehensive treatment Measures of Information Information on a computer is represented by binary bit strings Decimal numb ers can b e represented using the following enco ding The p osition of the binary digit 3 2 1 0 Bit Bit Bit Bit Decimal Table Binary encoding indicates its decimal equivalent such that if there are N bits the ith bit represents N i the decimal numb er Bit is referred to as the most signicant bit and bit N as the least signicant bit To enco de M dierent messages requires log M bits 2 Signal Pro cessing Course WD Penny April Entropy The table b elow shows the probability of o ccurrence px to two decimal places of i selected letters x in the English alphab et These statistics were taken from Mackays i b o ok on Information Theory The table also shows the information content of a x px hx i i i a e j q t z Table Probability and Information content of letters letter hx log i px i which is a measure of surprise if we had to guess what a randomly chosen letter of the English alphab et was going to b e wed say it was an A E T or other frequently o ccuring letter If it turned out to b e a Z wed b e surprised The letter E is so common that it is unusual to nd a sentence without one An exception is the page novel Gadsby by Ernest Vincent Wright in which -

Guide for the Use of the International System of Units (SI)
Guide for the Use of the International System of Units (SI) m kg s cd SI mol K A NIST Special Publication 811 2008 Edition Ambler Thompson and Barry N. Taylor NIST Special Publication 811 2008 Edition Guide for the Use of the International System of Units (SI) Ambler Thompson Technology Services and Barry N. Taylor Physics Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 (Supersedes NIST Special Publication 811, 1995 Edition, April 1995) March 2008 U.S. Department of Commerce Carlos M. Gutierrez, Secretary National Institute of Standards and Technology James M. Turner, Acting Director National Institute of Standards and Technology Special Publication 811, 2008 Edition (Supersedes NIST Special Publication 811, April 1995 Edition) Natl. Inst. Stand. Technol. Spec. Publ. 811, 2008 Ed., 85 pages (March 2008; 2nd printing November 2008) CODEN: NSPUE3 Note on 2nd printing: This 2nd printing dated November 2008 of NIST SP811 corrects a number of minor typographical errors present in the 1st printing dated March 2008. Guide for the Use of the International System of Units (SI) Preface The International System of Units, universally abbreviated SI (from the French Le Système International d’Unités), is the modern metric system of measurement. Long the dominant measurement system used in science, the SI is becoming the dominant measurement system used in international commerce. The Omnibus Trade and Competitiveness Act of August 1988 [Public Law (PL) 100-418] changed the name of the National Bureau of Standards (NBS) to the National Institute of Standards and Technology (NIST) and gave to NIST the added task of helping U.S. -

Understanding Shannon's Entropy Metric for Information
Understanding Shannon's Entropy metric for Information Sriram Vajapeyam [email protected] 24 March 2014 1. Overview Shannon's metric of "Entropy" of information is a foundational concept of information theory [1, 2]. Here is an intuitive way of understanding, remembering, and/or reconstructing Shannon's Entropy metric for information. Conceptually, information can be thought of as being stored in or transmitted as variables that can take on different values. A variable can be thought of as a unit of storage that can take on, at different times, one of several different specified values, following some process for taking on those values. Informally, we get information from a variable by looking at its value, just as we get information from an email by reading its contents. In the case of the variable, the information is about the process behind the variable. The entropy of a variable is the "amount of information" contained in the variable. This amount is determined not just by the number of different values the variable can take on, just as the information in an email is quantified not just by the number of words in the email or the different possible words in the language of the email. Informally, the amount of information in an email is proportional to the amount of “surprise” its reading causes. For example, if an email is simply a repeat of an earlier email, then it is not informative at all. On the other hand, if say the email reveals the outcome of a cliff-hanger election, then it is highly informative. -

Huffman Based LZW Lossless Image Compression Using Retinex Algorithm
ISSN (Print) : 2319-5940 ISSN (Online) : 2278-1021 International Journal of Advanced Research in Computer and Communication Engineering Vol. 2, Issue 8, August 2013 Huffman Based LZW Lossless Image Compression Using Retinex Algorithm Dalvir Kaur1, Kamaljit Kaur 2 Master of Technology in Computer Science & Engineering, Sri Guru Granth Sahib World University, Fatehgarh Sahib, Punjab, India1 Assistant Professor, Department Of Computer Science & Engineering, Sri Guru Granth Sahib World University, Fatehgarh Sahib, Punjab, India2 Abstract-Image compression is an application of data compression that encodes the original image with few bits. The objective of image compression is to reduce irrelevance and redundancy of the image data in order to be able to store or transmit data in an efficient form. So image compression can reduce the transmit time over the network and increase the speed of transmission. In Lossless image compression no data loss when the compression Technique is done. In this research, a new lossless compression scheme is presented and named as Huffman Based LZW Lossless Image Compression using Retinex Algorithm which consists of three stages: In the first stage, a Huffman coding is used to compress the image. In the second stage all Huffman code words are concatenated together and then compressed with LZW coding and decoding. In the third stage the Retinex algorithm are used on compressed image for enhance the contrast of image and improve the quality of image. This Proposed Technique is used to increase the compression ratio (CR), Peak signal of Noise Ratio (PSNR), and Mean Square Error (MSE) in the MATLAB Software. Keywords-Compression, Encode, Decode, Huffman, LZW.