Drawing Graphs with Dot
Total Page:16
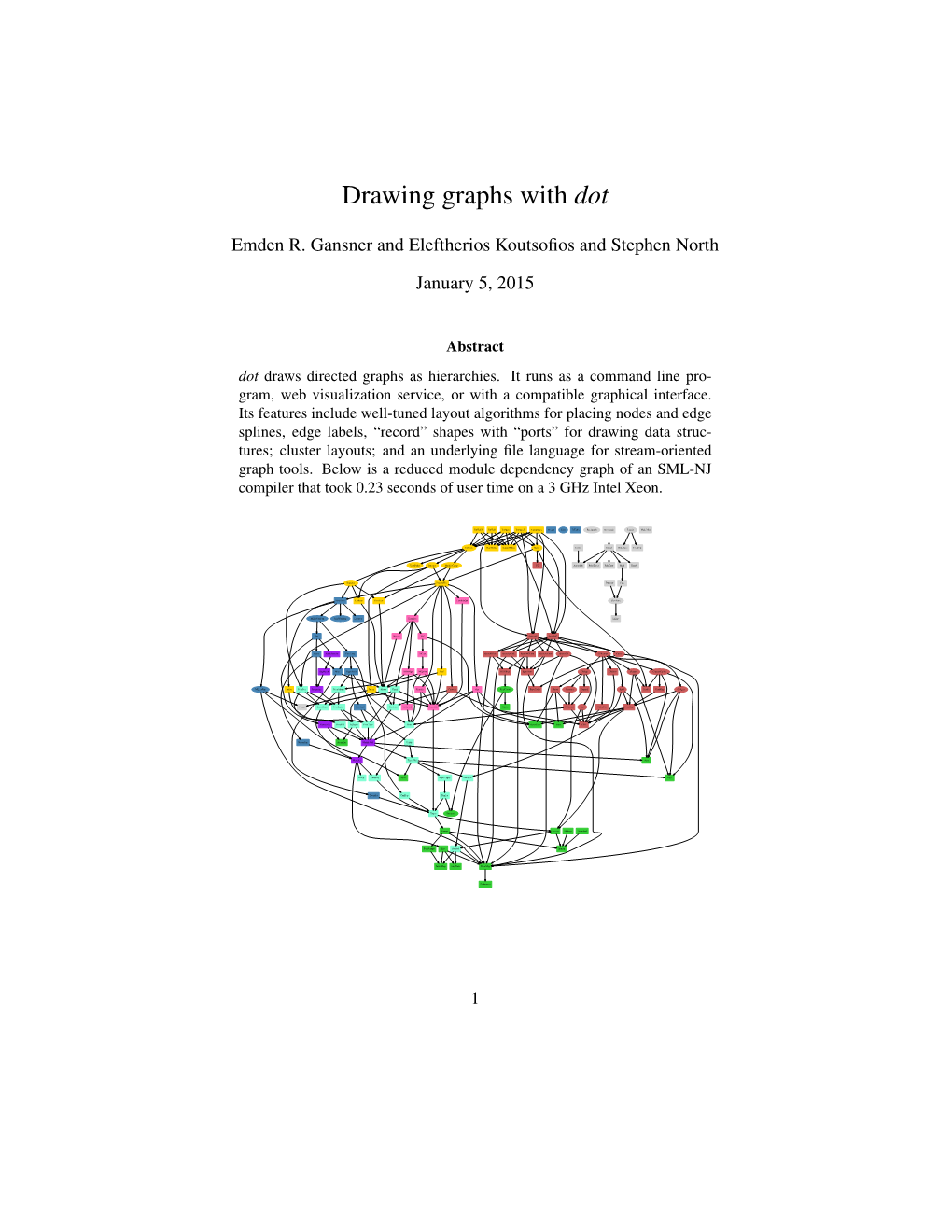
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Networkx Tutorial
5.03.2020 tutorial NetworkX tutorial Source: https://github.com/networkx/notebooks (https://github.com/networkx/notebooks) Minor corrections: JS, 27.02.2019 Creating a graph Create an empty graph with no nodes and no edges. In [1]: import networkx as nx In [2]: G = nx.Graph() By definition, a Graph is a collection of nodes (vertices) along with identified pairs of nodes (called edges, links, etc). In NetworkX, nodes can be any hashable object e.g. a text string, an image, an XML object, another Graph, a customized node object, etc. (Note: Python's None object should not be used as a node as it determines whether optional function arguments have been assigned in many functions.) Nodes The graph G can be grown in several ways. NetworkX includes many graph generator functions and facilities to read and write graphs in many formats. To get started though we'll look at simple manipulations. You can add one node at a time, In [3]: G.add_node(1) add a list of nodes, In [4]: G.add_nodes_from([2, 3]) or add any nbunch of nodes. An nbunch is any iterable container of nodes that is not itself a node in the graph. (e.g. a list, set, graph, file, etc..) In [5]: H = nx.path_graph(10) file:///home/szwabin/Dropbox/Praca/Zajecia/Diffusion/Lectures/1_intro/networkx_tutorial/tutorial.html 1/18 5.03.2020 tutorial In [6]: G.add_nodes_from(H) Note that G now contains the nodes of H as nodes of G. In contrast, you could use the graph H as a node in G. -

PHP Game Programming
PHP Game Programming Matt Rutledge © 2004 by Premier Press, a division of Course Technology. All rights SVP, Course Professional, Trade, reserved. No part of this book may be reproduced or transmitted in any Reference Group: form or by any means, electronic or mechanical, including photocopy- Andy Shafran ing, recording, or by any information storage or retrieval system with- Publisher: out written permission from Course PTR, except for the inclusion of Stacy L. Hiquet brief quotations in a review. Senior Marketing Manager: The Premier Press logo and related trade dress are trademarks of Premier Sarah O’Donnell Press and may not be used without written permission. Marketing Manager: Paint Shop Pro 8 is a registered trademark of Jasc Software. Heather Hurley PHP Coder is a trademark of phpIDE. Series Editor: All other trademarks are the property of their respective owners. André LaMothe Important: Course PTR cannot provide software support. Please contact Manager of Editorial Services: the appropriate software manufacturer’s technical support line or Web Heather Talbot site for assistance. Senior Acquisitions Editor: Course PTR and the author have attempted throughout this book to Emi Smith distinguish proprietary trademarks from descriptive terms by following Associate Marketing Manager: the capitalization style used by the manufacturer. Kristin Eisenzopf Information contained in this book has been obtained by Course PTR Project Editor and Copy Editor: from sources believed to be reliable. However, because of the possibility Dan Foster, Scribe Tribe of human or mechanical error by our sources, Course PTR, or others, the Publisher does not guarantee the accuracy, adequacy, or complete- Technical Reviewer: ness of any information and is not responsible for any errors or omis- John Freitas sions or the results obtained from use of such information. -

Networkx: Network Analysis with Python
NetworkX: Network Analysis with Python Salvatore Scellato Full tutorial presented at the XXX SunBelt Conference “NetworkX introduction: Hacking social networks using the Python programming language” by Aric Hagberg & Drew Conway Outline 1. Introduction to NetworkX 2. Getting started with Python and NetworkX 3. Basic network analysis 4. Writing your own code 5. You are ready for your project! 1. Introduction to NetworkX. Introduction to NetworkX - network analysis Vast amounts of network data are being generated and collected • Sociology: web pages, mobile phones, social networks • Technology: Internet routers, vehicular flows, power grids How can we analyze this networks? Introduction to NetworkX - Python awesomeness Introduction to NetworkX “Python package for the creation, manipulation and study of the structure, dynamics and functions of complex networks.” • Data structures for representing many types of networks, or graphs • Nodes can be any (hashable) Python object, edges can contain arbitrary data • Flexibility ideal for representing networks found in many different fields • Easy to install on multiple platforms • Online up-to-date documentation • First public release in April 2005 Introduction to NetworkX - design requirements • Tool to study the structure and dynamics of social, biological, and infrastructure networks • Ease-of-use and rapid development in a collaborative, multidisciplinary environment • Easy to learn, easy to teach • Open-source tool base that can easily grow in a multidisciplinary environment with non-expert users -

Network Monitoring & Management Using Cacti
Network Monitoring & Management Using Cacti Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Introduction Network Monitoring Tools Availability Reliability Performance Cact monitors the performance and usage of devices. Introduction Cacti: Uses RRDtool, PHP and stores data in MySQL. It supports the use of SNMP and graphics with RRDtool. “Cacti is a complete frontend to RRDTool, it stores all of the necessary information to create graphs and populate them with data in a MySQL database. The frontend is completely PHP driven. Along with being able to maintain Graphs, Data Sources, and Round Robin Archives in a database, cacti handles the data gathering. There is also SNMP support for those used to creating traffic graphs with MRTG.” Introduction • A tool to monitor, store and present network and system/server statistics • Designed around RRDTool with a special emphasis on the graphical interface • Almost all of Cacti's functionality can be configured via the Web. • You can find Cacti here: http://www.cacti.net/ Getting RRDtool • Round Robin Database for time series data storage • Command line based • From the author of MRTG • Made to be faster and more flexible • Includes CGI and Graphing tools, plus APIs • Solves the Historical Trends and Simple Interface problems as well as storage issues Find RRDtool here:http://oss.oetiker.ch/rrdtool/ RRDtool Database Format General Description 1. Cacti is written as a group of PHP scripts. 2. The key script is “poller.php”, which runs every 5 minutes (by default). -

Munin Documentation Release 2.0.44
Munin Documentation Release 2.0.44 Stig Sandbeck Mathisen <[email protected]> Dec 20, 2018 Contents 1 Munin installation 3 1.1 Prerequisites.............................................3 1.2 Installing Munin...........................................4 1.3 Initial configuration.........................................7 1.4 Getting help.............................................8 1.5 Upgrading Munin from 1.x to 2.x..................................8 2 The Munin master 9 2.1 Role..................................................9 2.2 Components.............................................9 2.3 Configuration.............................................9 2.4 Other documentation.........................................9 3 The Munin node 13 3.1 Role.................................................. 13 3.2 Configuration............................................. 13 3.3 Other documentation......................................... 13 4 The Munin plugin 15 4.1 Role.................................................. 15 4.2 Other documentation......................................... 15 5 Documenting Munin 21 5.1 Nomenclature............................................ 21 6 Reference 25 6.1 Man pages.............................................. 25 6.2 Other reference material....................................... 40 7 Examples 43 7.1 Apache virtualhost configuration.................................. 43 7.2 lighttpd configuration........................................ 44 7.3 nginx configuration.......................................... 45 7.4 Graph aggregation -

Automatic Placement of Authorization Hooks in the Linux Security Modules Framework
Automatic Placement of Authorization Hooks in the Linux Security Modules Framework Vinod Ganapathy [email protected] University of Wisconsin, Madison Joint work with Trent Jaeger Somesh Jha [email protected] [email protected] Pennsylvania State University University of Wisconsin, Madison Context of this talk Authorization policies and their enforcement Three concepts: Subjects (e.g., users, processes) Objects (e.g., system resources) Security-sensitive operations on objects. Authorization policy: A set of triples: (Subject, Object, Operation) Key question: How to ensure that the authorization policy is enforced? CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 2 Enforcing authorization policies Reference monitor consults the policy. Application queries monitor at appropriate locations. Can I perform operation OP? Reference Monitor Application to Policy be secured Yes/No (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 3 Linux security modules framework Framework for authorization policy enforcement. Uses a reference monitor-based architecture. Integrated into Linux-2.6 Linux Kernel Reference Monitor Policy (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 4 Linux security modules framework Reference monitor calls (hooks) placed appropriately in the Linux kernel. Each hook is an authorization query. Linux Kernel Reference Monitor Policy (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) Hooks CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 5 Linux security modules framework Authorization query of the form: (subj., obj., oper.)? Kernel performs operation only if query succeeds. -

Graph Database Fundamental Services
Bachelor Project Czech Technical University in Prague Faculty of Electrical Engineering F3 Department of Cybernetics Graph Database Fundamental Services Tomáš Roun Supervisor: RNDr. Marko Genyk-Berezovskyj Field of study: Open Informatics Subfield: Computer and Informatic Science May 2018 ii Acknowledgements Declaration I would like to thank my advisor RNDr. I declare that the presented work was de- Marko Genyk-Berezovskyj for his guid- veloped independently and that I have ance and advice. I would also like to thank listed all sources of information used Sergej Kurbanov and Herbert Ullrich for within it in accordance with the methodi- their help and contributions to the project. cal instructions for observing the ethical Special thanks go to my family for their principles in the preparation of university never-ending support. theses. Prague, date ............................ ........................................... signature iii Abstract Abstrakt The goal of this thesis is to provide an Cílem této práce je vyvinout webovou easy-to-use web service offering a database službu nabízející databázi neorientova- of undirected graphs that can be searched ných grafů, kterou bude možno efektivně based on the graph properties. In addi- prohledávat na základě vlastností grafů. tion, it should also allow to compute prop- Tato služba zároveň umožní vypočítávat erties of user-supplied graphs with the grafové vlastnosti pro grafy zadané uži- help graph libraries and generate graph vatelem s pomocí grafových knihoven a images. Last but not least, we implement zobrazovat obrázky grafů. V neposlední a system that allows bulk adding of new řadě je také cílem navrhnout systém na graphs to the database and computing hromadné přidávání grafů do databáze a their properties. -

Ffontiau Cymraeg
This publication is available in other languages and formats on request. Mae'r cyhoeddiad hwn ar gael mewn ieithoedd a fformatau eraill ar gais. [email protected] www.caerphilly.gov.uk/equalities How to type Accented Characters This guidance document has been produced to provide practical help when typing letters or circulars, or when designing posters or flyers so that getting accents on various letters when typing is made easier. The guide should be used alongside the Council’s Guidance on Equalities in Designing and Printing. Please note this is for PCs only and will not work on Macs. Firstly, on your keyboard make sure the Num Lock is switched on, or the codes shown in this document won’t work (this button is found above the numeric keypad on the right of your keyboard). By pressing the ALT key (to the left of the space bar), holding it down and then entering a certain sequence of numbers on the numeric keypad, it's very easy to get almost any accented character you want. For example, to get the letter “ô”, press and hold the ALT key, type in the code 0 2 4 4, then release the ALT key. The number sequences shown from page 3 onwards work in most fonts in order to get an accent over “a, e, i, o, u”, the vowels in the English alphabet. In other languages, for example in French, the letter "c" can be accented and in Spanish, "n" can be accented too. Many other languages have accents on consonants as well as vowels. -

Dot at Command Firmware Release 4.0.0 Release 3.3.5
Product Change Notification Software Release Notes Dot AT Command Firmware Release 4.0.0 Release 3.3.5 MultiTech xDot® MultiTech mDot™ Date: March 30, 2021 Contents Product Change Notification (PCN) Number PCN 03302021-001 (Dot) I. Overview II. Suggested Action Plan I. Overview MultiTech announces the availability of new AT Command III. Release 4.0.0 Overview Firmware for use on MultiTech® Long Range LoRa® Modules: MultiTech xDot® (MTXDOT Series) IV. Release 3.3.5 Overview MultiTech mDot™ (MTDOT Series) V. Schedule New versions are currently available for download and VI. Flashing mDot Firmware evaluation: VII. Part Numbers Impacted Release 4.0.0 (shipping in June 2021) Release 3.3.5 VIII. Mbed OS Overview IX. xDot Overview Release 4.0.0 will released into standard MultiTech product starting in June 2021. Currently, product ships with X. mDot Overview Release 3.2.1 XI. xDot Micro Developer Kit II. Suggested Action Plan XII. Additional Information Customers Review the information in this PCN and forward to Attachments others within your organization who are actively Identifying Firmware Version involved with the development of IoT applications using the MultiTech xDot and MultiTech mDot. Identifying Date of Manufacture Consider downloading the firmware available on MultiTech or Mbed websites to check compatibility mPower & mLinux Software with existing deployments. PCN 03302021-001 (Dot) Page 1 of 12 https://support.multitech.com Review the release schedule for the upcoming firmware release and understand the effect on your manufacturing and deployment schedules. Distributors Forward this announcement to others within your organization who are actively involved in the sale or support of LoRa-enabled sensors. -

Dell EMC Powerstore CLI Guide
Dell EMC PowerStore CLI Guide May 2020 Rev. A01 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2020 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Contents Additional Resources.......................................................................................................................4 Chapter 1: Introduction................................................................................................................... 5 Overview.................................................................................................................................................................................5 Use PowerStore CLI in scripts.......................................................................................................................................5 Set up the PowerStore CLI client........................................................................................................................................5 Install the PowerStore CLI client.................................................................................................................................. -

Shell Variables
Shell Using the command line Orna Agmon ladypine at vipe.technion.ac.il Haifux Shell – p. 1/55 TOC Various shells Customizing the shell getting help and information Combining simple and useful commands output redirection lists of commands job control environment variables Remote shell textual editors textual clients references Shell – p. 2/55 What is the shell? The shell is the wrapper around the system: a communication means between the user and the system The shell is the manner in which the user can interact with the system through the terminal. The shell is also a script interpreter. The simplest script is a bunch of shell commands. Shell scripts are used in order to boot the system. The user can also write and execute shell scripts. Shell – p. 3/55 Shell - which shell? There are several kinds of shells. For example, bash (Bourne Again Shell), csh, tcsh, zsh, ksh (Korn Shell). The most important shell is bash, since it is available on almost every free Unix system. The Linux system scripts use bash. The default shell for the user is set in the /etc/passwd file. Here is a line out of this file for example: dana:x:500:500:Dana,,,:/home/dana:/bin/bash This line means that user dana uses bash (located on the system at /bin/bash) as her default shell. Shell – p. 4/55 Starting to work in another shell If Dana wishes to temporarily use another shell, she can simply call this shell from the command line: [dana@granada ˜]$ bash dana@granada:˜$ #In bash now dana@granada:˜$ exit [dana@granada ˜]$ bash dana@granada:˜$ #In bash now, going to hit ctrl D dana@granada:˜$ exit [dana@granada ˜]$ #In original shell now Shell – p. -

Application for New Or Duplicate License Plates
APPLICATION FOR NEW OR DUPLICATE LICENSE PLATES APPLICANT AND VEHICLE INFORMATION Owner(s) Name Daytime Phone Number ( ) - Mailing Address City State ZIP Vehicle Make Model Year VIN Body Style Original License Plate Number Expiration Date Number of Plate(s) lost, stolen, destroyed Plate(s) Surrendered STEP STEP #1 If license plate(s) cannot be surrendered because they are lost or stolen, duplicate license plates (plates that are reproduced with the same plate number) cannot be displayed on the vehicle until the validation stickers on the original plates have expired. This form cannot be used to replace lost, damaged, or mutilated embossed plates. You must reapply for embossed plates using the form MV-145. In case of lost, damaged or mutilated plates, a new or duplicate license plate and registration certificate will be issued by the County Treasurer. Damaged or mutilated license plates must be surrendered to the County Treasurer when you receive your new license plates. The fee to obtain a replacement license plate is eight dollars ($8.00), made payable to the County Treasurer. A replacement plate is the next available consecutive plate. The fee to obtain a duplicate license plate is thirty dollars ($30.00), made payable to the County Treasurer. A duplicate plate is the plate with the same number or combination that you currently have; WYDOT will reproduce your plate. Please note the following plates are the ONLY license plates that can be remade: Prestige, all types of Specialty Plates and preferred number series plates. Preferred number series in each county are determined by the County Treasurer, but will not exceed 9,999.