Department of CSE / IT
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Deliverable No. 5.3 Techniques to Build the Cloud Infrastructure Available to the Community
Deliverable No. 5.3 Techniques to build the cloud infrastructure available to the community Grant Agreement No.: 600841 Deliverable No.: D5.3 Deliverable Name: Techniques to build the cloud infrastructure available to the community Contractual Submission Date: 31/03/2015 Actual Submission Date: 31/03/2015 Dissemination Level PU Public X PP Restricted to other programme participants (including the Commission Services) RE Restricted to a group specified by the consortium (including the Commission Services) CO Confidential, only for members of the consortium (including the Commission Services) Grant Agreement no. 600841 D5.3 – Techniques to build the cloud infrastructure available to the community COVER AND CONTROL PAGE OF DOCUMENT Project Acronym: CHIC Project Full Name: Computational Horizons In Cancer (CHIC): Developing Meta- and Hyper-Multiscale Models and Repositories for In Silico Oncology Deliverable No.: D5.3 Document name: Techniques to build the cloud infrastructure available to the community Nature (R, P, D, O)1 R Dissemination Level (PU, PP, PU RE, CO)2 Version: 1.0 Actual Submission Date: 31/03/2015 Editor: Manolis Tsiknakis Institution: FORTH E-Mail: [email protected] ABSTRACT: This deliverable reports on the technologies, techniques and configuration needed to install, configure, maintain and run a private cloud infrastructure for productive usage. KEYWORD LIST: Cloud infrastructure, OpenStack, Eucalyptus, CloudStack, VMware vSphere, virtualization, computation, storage, security, architecture. The research leading to these results has received funding from the European Community's Seventh Framework Programme (FP7/2007-2013) under grant agreement no 600841. The author is solely responsible for its content, it does not represent the opinion of the European Community and the Community is not responsible for any use that might be made of data appearing therein. -

Cloud Computing: a Taxonomy of Platform and Infrastructure-Level Offerings David Hilley College of Computing Georgia Institute of Technology
Cloud Computing: A Taxonomy of Platform and Infrastructure-level Offerings David Hilley College of Computing Georgia Institute of Technology April 2009 Cloud Computing: A Taxonomy of Platform and Infrastructure-level Offerings David Hilley 1 Introduction Cloud computing is a buzzword and umbrella term applied to several nascent trends in the turbulent landscape of information technology. Computing in the “cloud” alludes to ubiquitous and inexhaustible on-demand IT resources accessible through the Internet. Practically every new Internet-based service from Gmail [1] to Amazon Web Services [2] to Microsoft Online Services [3] to even Facebook [4] have been labeled “cloud” offerings, either officially or externally. Although cloud computing has garnered significant interest, factors such as unclear terminology, non-existent product “paper launches”, and opportunistic marketing have led to a significant lack of clarity surrounding discussions of cloud computing technology and products. The need for clarity is well-recognized within the industry [5] and by industry observers [6]. Perhaps more importantly, due to the relative infancy of the industry, currently-available product offerings are not standardized. Neither providers nor potential consumers really know what a “good” cloud computing product offering should look like and what classes of products are appropriate. Consequently, products are not easily comparable. The scope of various product offerings differ and overlap in complicated ways – for example, Ama- zon’s EC2 service [7] and Google’s App Engine [8] partially overlap in scope and applicability. EC2 is more flexible but also lower-level, while App Engine subsumes some functionality in Amazon Web Services suite of offerings [2] external to EC2. -
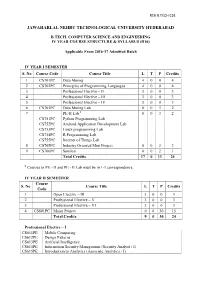
R16 B.TECH CSE IV Year Syllabus
R16 B.TECH CSE. JAWAHARLAL NEHRU TECHNOLOGICAL UNIVERSITY HYDERABAD B.TECH. COMPUTER SCIENCE AND ENGINEERING IV YEAR COURSE STRUCTURE & SYLLABUS (R16) Applicable From 2016-17 Admitted Batch IV YEAR I SEMESTER S. No Course Code Course Title L T P Credits 1 CS701PC Data Mining 4 0 0 4 2 CS702PC Principles of Programming Languages 4 0 0 4 3 Professional Elective – II 3 0 0 3 4 Professional Elective – III 3 0 0 3 5 Professional Elective – IV 3 0 0 3 6 CS703PC Data Mining Lab 0 0 3 2 7 PE-II Lab # 0 0 3 2 CS751PC Python Programming Lab CS752PC Android Application Development Lab CS753PC Linux programming Lab CS754PC R Programming Lab CS755PC Internet of Things Lab 8 CS705PC Industry Oriented Mini Project 0 0 3 2 9 CS706PC Seminar 0 0 2 1 Total Credits 17 0 11 24 # Courses in PE - II and PE - II Lab must be in 1-1 correspondence. IV YEAR II SEMESTER Course S. No Course Title L T P Credits Code 1 Open Elective – III 3 0 0 3 2 Professional Elective – V 3 0 0 3 3 Professional Elective – VI 3 0 0 3 4 CS801PC Major Project 0 0 30 15 Total Credits 9 0 30 24 Professional Elective – I CS611PE Mobile Computing CS612PE Design Patterns CS613PE Artificial Intelligence CS614PE Information Security Management (Security Analyst - I) CS615PE Introduction to Analytics (Associate Analytics - I) R16 B.TECH CSE. Professional Elective – II CS721PE Python Programming CS722PE Android Application Development CS723PE Linux Programming CS724PE R Programming CS725PE Internet of Things Professional Elective - III CS731PE Distributed Systems CS732PE Machine Learning CS733PE -

Design of a Platform of Virtual Service Containers for Service Oriented Cloud Computing
DESIGN OF A PLATFORM OF VIRTUAL SERVICE CONTAINERS FOR SERVICE ORIENTED CLOUD COMPUTING Carlos de Alfonso Andrés García Vicente Hernández INDEX • Introduction • Our approach • Platform design • Storage • Security • Management and QoS • Catalogue • User Interface • Virtual Container • User profiles • Working lines and open problems 2 INTRODUCTION • In the latter years there have been a growing interest in Cloud Computing technologies and its possible applications. • There have appeared many commercial products • Mainly storage and Infrastructure as a Service. • Storage examples: Amazon S3, Nirvanix, Savvis • IaaS examples: Amazon EC2, GoGrid, 3Tera • Other examples: Google App Engine, Salesforce, Engine Yard • Some small sets of open Cloud Computing tools have been also developed. • Eucalyptus, Nimbus, OpenNebula, Enomaly, Abicloud, etc. • Almost any of them are oriented to the IaaS level, since there is a lack of research projects towards other cloud approaches. 3 INTRODUCTION • Currently most of cloud computing solutions are focusing in the lowest levels of the infrastructure. • Virtual machine deployment and management infrastructure. • Storage management infrastructure. • The current approach of vendors, to deploy Services in the cloud, is based in those levels instead of Services virtualization. • Provider’s approach is to package a preconfigured service in a virtual machine image, and deploy a whole virtual appliance to run the service. • There are some drawbacks like the waste of resources, a less direct service management, the low abstraction level, etc. OUR APPROACH • To offer a platform which enable developers to deploy and to manage virtual services as IaaS platforms deploy and manage virtual machines. • That means to deploy only the service instance that is needed, instead of deploying the whole virtual appliance. -

Envisioning the Cloud: the Next Computing Paradigm
Marketspace® Point of View Envisioning the Cloud: The Next Computing Paradigm March 20, 2009 Jeffrey F. Rayport Andrew Heyward Research Associates Raj Beri Jake Samuelson Geordie McClelland Funding for this paper was provided by Google, Inc Table of Contents Executive Summary .................................................................................... i Introduction................................................................................................ 1 Understanding the cloud...................................................................... 3 The network is the (very big, very powerful) computer .................... 6 How the data center became possible ............................................. 8 The passengers are driving the bus ...................................................11 Where we go from here......................................................................12 Benefits and Opportunities in the Cloud ..............................................14 Anywhere/anytime access to software............................................14 Specialization and customization of applications...........................17 Collaboration .......................................................................................20 Processing power on demand...........................................................21 Storage as a universal service............................................................23 Cost savings in the cloud ....................................................................24 Enabling the Cloud -

DRE) for Software
Exceeding 99% in Defect Removal Efficiency (DRE) for Software Draft 11.0 September 6, 2016 Capers Jones, VP and CTO, Namcook Analytics LLC Abstract Software quality depends upon two important variables. The first variable is that of “defect potentials” or the sum total of bugs likely to occur in requirements, architecture, design, code, documents, and “bad fixes” or new bugs in bug repairs. Defect potentials are measured using function point metrics, since “lines of code” cannot deal with requirements and design defects. (This paper uses IFPUG function points version 4.3. The newer SNAP metrics are only shown experimentally due to insufficient empirical quality data with SNAP as of 2016. However an experimental tool is included for calculating SNAP defects.) The second important measure is “defect removal efficiency (DRE)” or the percentage of bugs found and eliminated before release of software to clients. The metrics of Defect Potentials and Defect Removal Efficiency (DRE) were developed by IBM circa 1973 and are widely used by technology companies and also by insurance companies, banks, and other companies with large software organizations. The author’s Software Risk Master (SRM) estimating tool predicts defect potentials and defect removal efficiency (DRE) as standard quality outputs for all software projects. Web: www.Namcook.com Email: [email protected] Copyright © 2016 by Capers Jones. All rights reserved. 1 Introduction Defect potentials and defect removal efficiency (DRE) are useful quality metrics developed by IBM circa 1973 and widely used by technology companies as well as by banks, insurance companies, and other organizations with large software staffs. This combination of defect potentials using function points and defect removal efficiency (DRE) are the only accurate and effective measures for software quality. -

ITSSD Assessment of the New ISO 26000 Social Responsibility Standard
ITSSD Assessment of the new ISO 26000 Social Responsibility Standard December 2005 Preliminary Conclusions: 1. It may be possible to procedurally shape and/or delay the development of the ISO SR guidance standard at the national mirror and international levels. 2. It may be impossible to prevent the actual adoption of an SR standard at the DIS and FDIS stages, unless the ISO voting rules are first modified to reflect only one vote for the European Community as a whole through its regional standards representative (e.g., CEN), as opposed to twenty-five separate votes representing the national standards bodies of each of the EU member states. 3. It is likely to be difficult to reverse the new stakeholder engagement process that has been introduced at the ISO incident to the commencement of this SR standard initiative, though it may arguably be shaped by filing procedural objections, and by strengthening traditional ISO benchmarks for consensus. 4. The real challenge is to prevent the new process from being expanded institutionally to all of ISO’s technical standards work, and thereby from being incorporated within business contracts that reference or directly incorporate such standards as conditions of manufacture, sale, service, etc. This is likely to be quite difficult given the current efforts of governments, NGOs and UN agencies to incorporate sustainable development dimensions into all ISO technical standards. 5. Further study and analysis of the evolving ISO SR operating procedures, the multi-stakeholder engagement process, and the ISO’s general consensus procedures is necessary to determine the proper course of action and the appropriate actors with which/whom to collaborate. -

Opinions of Small and Medium UK Construction Companies On
Opinions of small and medium UK construction companies on environmental management systems Bailey, M, Booth, CA, Horry, R, Vidalakis, C, Mahamadu, A-M and Gyau, KAB http://dx.doi.org/10.1680/jmapl.19.00033 Title Opinions of small and medium UK construction companies on environmental management systems Authors Bailey, M, Booth, CA, Horry, R, Vidalakis, C, Mahamadu, A-M and Gyau, KAB Type Article URL This version is available at: http://usir.salford.ac.uk/id/eprint/56909/ Published Date 2021 USIR is a digital collection of the research output of the University of Salford. Where copyright permits, full text material held in the repository is made freely available online and can be read, downloaded and copied for non-commercial private study or research purposes. Please check the manuscript for any further copyright restrictions. For more information, including our policy and submission procedure, please contact the Repository Team at: [email protected]. Accepted manuscript doi: 10.1680/jmapl.19.00033 Accepted manuscript As a service to our authors and readers, we are putting peer-reviewed accepted manuscripts (AM) online, in the Ahead of Print section of each journal web page, shortly after acceptance. Disclaimer The AM is yet to be copyedited and formatted in journal house style but can still be read and referenced by quoting its unique reference number, the digital object identifier (DOI). Once the AM has been typeset, an ‘uncorrected proof’ PDF will replace the ‘accepted manuscript’ PDF. These formatted articles may still be corrected by the authors. During the Production process, errors may be discovered which could affect the content, and all legal disclaimers that apply to the journal relate to these versions also. -

ISO 14000 Assessing Its Impact on Corporate Effectiveness and Efficiency
ISO 14000 Assessing Its Impact on Corporate Effectiveness and Efficiency Steven A. Melnyk Roger Calantone Rob Handfield R.L. (Lal) Tummala Gyula Vastag Timothy Hinds Robert Sroufe Frank Montabon Michigan State University Sime Curkovic Western Michigan University Contents Tables, Exhibits, Charts, and Appendices .................................................................... 4 Acknowledgments.......................................................................................................... 5 Executive Summary....................................................................................................... 6 Implications of the Study .............................................................................................. 7 Design of the Study........................................................................................................ 8 Overview .................................................................................................................... 8 The Large-Scale Survey.............................................................................................. 8 The Sample ............................................................................................................ 9 The Case Studies........................................................................................................ 9 The Sample for the Case Studies Phase ............................................................... 9 The Interview Protocol Described....................................................................... -

This Is Not a Complete Sample Paper
BCS Practitioner Certificate in Information Assurance Architecture Specimen Paper – This is not a complete sample paper. Attempt all 85 multiple-choice questions – 1 mark awarded to each question. Mark only one answer to each question. There are no trick questions. Section A – multiple-choice questions There are 60 questions for Section A, awarding 1 mark per question for a total of 60 points. Section B – Scenario based multi-choice questions There are 25 questions for Section B, over 5 scenarios, awarding 13 points per scenario, for a total of 65 points. Pass Mark: 81/125 65% This specimen paper has 30 questions in Section A with 30 points available for Section A and 3 scenarios with 15 questions in Section B with 39 points available. Therefore there are 69 points available for both sections. Specimen Paper Pass Mark: 45/69 65% Copying of this paper is expressly forbidden without the direct approval of BCS, The Chartered Institute for IT. Copyright © BCS 2014 Page 1 of 21 PCiAA Sample Paper A Version 1.0 August 2014 This page is intentionally blank. Section A Multiple-choice answers – 1 mark each NOTE: Choose only one answer per question 1 What is the correct ordering (Conceptual to Component) of the following artefacts for the SABSA Motivation (WHY) foci? a. Security Policies. b. Security Standards. c. Control Objectives. d. Security Rules, Practices and Procedures. A c, a, d and b. B a, c, b and d. C b, a, d and c. D c, b, a and d. 2 In the TOGAF Content MetaModel, under which viewpoint would you find the Business Principles, Objectives and Drivers? A Motivation. -

Multi-Tenant, Secure, Load Disseminated Saas Architecture
Multi-Tenant, Secure, Load Disseminated SaaS Architecture Zeeshan Pervez, Sungyoung Lee Department of Computer Engineering, Kyung Hee University, South Korea {zeeshan, sylee}@oslab.khu.ac.kr Abstract – The availability of high speed internet has diversified Leading companies in information technology industry are the way we used to intermingle with each other. The emergence gradually moving their applications and related data over the of social networks and interactive web applications has left a internet and delivering them through SaaS [2]. Google has dent in existing software and service delivery models. Software used SaaS platform to offer web applications for vendors now not only focus on functionality but also have to communication and collaboration [3], gradually replacing cater delivery model of their software. On-demand and ubiquitous accessibility has become an inimitable selling point recourse exhaustive desktop applications. Similarly Microsoft for software vendors. In the last few years we have witnessed a is offering their development and database services though term “Cloud computing” thronging blogs and search engines. SaaS platform codename Microsoft Azure [4]. SaaS is Cloud computing is on-demand service delivery; services preached by the companies like SalesForce.com, 3Tera, ranging from Infrastructure, Platform and Software. With the Microsoft, Zoho and Amazon, as a result of which business materialization of Amazon Cloud Computing Service we have specific services can be consumed in ubiquitous environment. seen exponential increase in interest of business as well as research community in Cloud computing Orchestra. Now 2. MULTI-TENANT ARCHITECTURE: technological oracles are offering their software in Cloud as Software as a Service (SaaS). Every service provider is laying on SaaS not only has altered the software delivery model, but line to gain competitive advantage over each other, there is need it also had amended the way in which software is developed. -

Parameterization, Analysis, and Risk Management in a Comprehensive Management System with Emphasis on Energy and Performance (ISO 50001: 2018)
energies Article Parameterization, Analysis, and Risk Management in a Comprehensive Management System with Emphasis on Energy and Performance (ISO 50001: 2018) P. Pablo Poveda-Orjuela 1,*, J. Carlos García-Díaz 2 , Alexander Pulido-Rojano 3 and Germán Cañón-Zabala 4 1 ASTEQ Technology, 53 Street No. 53-15, Barranquilla 080020, Colombia 2 Centre for Quality and Change Management, Universitat Politècnica de València, Camino de Vera, s/n. 46022 Valencia, Spain; [email protected] 3 Industrial Engineering Department, Universidad Simón Bolívar, Av. 59 No. 59-92, Barranquilla 080020, Colombia; [email protected] 4 QUARA Group, 157 Street No. 13 B-20, Bogotá 110121, Colombia; [email protected] * Correspondence: [email protected] or [email protected]; Tel.: +57-3008897111 Received: 7 September 2020; Accepted: 13 October 2020; Published: 26 October 2020 Abstract: The future of business development relies on the effective management of risks, opportunities, and energy and water resources. Here, we evaluate the application of best practices to identify, analyze, address, monitor, and control risks and opportunities (R/O) according to ISO 31000 and 50000. Furthermore, we shed light on tools, templates, ISO guides, and international documents that contribute to classifying, identifying, formulating control, and managing R/O parameterization in a comprehensive management system model, namely CMS QHSE3+, which consists of quality (Q), health and safety (HS), environmental management (E), energy efficiency (E2), and other risk components (+) that include comprehensive biosecurity and biosafety. By focusing on the deployment of R/O-based thinking (ROBT) at strategic and operational levels, we show vulnerability reduction in CMS QHSE3+ by managing energy, efficiency, and sustainability.