Clang Tooling
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KDE 2.0 Development, Which Is Directly Supported
23 8911 CH18 10/16/00 1:44 PM Page 401 The KDevelop IDE: The CHAPTER Integrated Development Environment for KDE by Ralf Nolden 18 IN THIS CHAPTER • General Issues 402 • Creating KDE 2.0 Applications 409 • Getting Started with the KDE 2.0 API 413 • The Classbrowser and Your Project 416 • The File Viewers—The Windows to Your Project Files 419 • The KDevelop Debugger 421 • KDevelop 2.0—A Preview 425 23 8911 CH18 10/16/00 1:44 PM Page 402 Developer Tools and Support 402 PART IV Although developing applications under UNIX systems can be a lot of fun, until now the pro- grammer was lacking a comfortable environment that takes away the usual standard activities that have to be done over and over in the process of programming. The KDevelop IDE closes this gap and makes it a joy to work within a complete, integrated development environment, combining the use of the GNU standard development tools such as the g++ compiler and the gdb debugger with the advantages of a GUI-based environment that automates all standard actions and allows the developer to concentrate on the work of writing software instead of managing command-line tools. It also offers direct and quick access to source files and docu- mentation. KDevelop primarily aims to provide the best means to rapidly set up and write KDE software; it also supports extended features such as GUI designing and translation in con- junction with other tools available especially for KDE development. The KDevelop IDE itself is published under the GNU Public License (GPL), like KDE, and is therefore publicly avail- able at no cost—including its source code—and it may be used both for free and for commer- cial development. -

What Is LLVM? and a Status Update
What is LLVM? And a Status Update. Approved for public release Hal Finkel Leadership Computing Facility Argonne National Laboratory Clang, LLVM, etc. ✔ LLVM is a liberally-licensed(*) infrastructure for creating compilers, other toolchain components, and JIT compilation engines. ✔ Clang is a modern C++ frontend for LLVM ✔ LLVM and Clang will play significant roles in exascale computing systems! (*) Now under the Apache 2 license with the LLVM Exception LLVM/Clang is both a research platform and a production-quality compiler. 2 A role in exascale? Current/Future HPC vendors are already involved (plus many others)... Apple + Google Intel (Many millions invested annually) + many others (Qualcomm, Sony, Microsoft, Facebook, Ericcson, etc.) ARM LLVM IBM Cray NVIDIA (and PGI) Academia, Labs, etc. AMD 3 What is LLVM: LLVM is a multi-architecture infrastructure for constructing compilers and other toolchain components. LLVM is not a “low-level virtual machine”! LLVM IR Architecture-independent simplification Architecture-aware optimization (e.g. vectorization) Assembly printing, binary generation, or JIT execution Backends (Type legalization, instruction selection, register allocation, etc.) 4 What is Clang: LLVM IR Clang is a C++ frontend for LLVM... Code generation Parsing and C++ Source semantic analysis (C++14, C11, etc.) Static analysis ● For basic compilation, Clang works just like gcc – using clang instead of gcc, or clang++ instead of g++, in your makefile will likely “just work.” ● Clang has a scalable LTO, check out: https://clang.llvm.org/docs/ThinLTO.html 5 The core LLVM compiler-infrastructure components are one of the subprojects in the LLVM project. These components are also referred to as “LLVM.” 6 What About Flang? ● Started as a collaboration between DOE and NVIDIA/PGI. -

Avatud Lähtekoodiga Vahendite Kohandamine Microsoft Visual C++ Tarkvaralahenduste Kvaliteedi Analüüsiks Sonarqube Serveris
TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Tarkvarateaduse instituut Anton Ašot Roolaid 980774IAPB AVATUD LÄHTEKOODIGA VAHENDITE KOHANDAMINE MICROSOFT VISUAL C++ TARKVARALAHENDUSTE KVALITEEDI ANALÜÜSIKS SONARQUBE SERVERIS Bakalaureusetöö Juhendaja: Juhan-Peep Ernits PhD Tallinn 2019 Autorideklaratsioon Kinnitan, et olen koostanud antud lõputöö iseseisvalt ning seda ei ole kellegi teise poolt varem kaitsmisele esitatud. Kõik töö koostamisel kasutatud teiste autorite tööd, olulised seisukohad, kirjandusallikatest ja mujalt pärinevad andmed on töös viidatud. Autor: Anton Ašot Roolaid 21.05.2019 2 Annotatsioon Käesolevas bakalaureusetöös uuritakse, kuidas on võimalik saavutada suure hulga C++ lähtekoodi kvaliteedi paranemist, kui ettevõttes kasutatakse arenduseks Microsoft Visual Studiot ning koodikaetuse ja staatilise analüüsi ülevaate saamiseks SonarQube serverit (Community Edition). Seejuures SonarSource'i poolt pakutava tasulise SonarCFamily for C/C++ analüsaatori (mille eelduseks on SonarQube serveri Developer Edition) asemel kasutatakse tasuta ja vaba alternatiivi: SonarQube C++ Community pluginat. Analüüsivahenditena eelistatakse avatud lähtekoodiga vabu tarkvaravahendeid. Valituks osutuvad koodi kaetuse analüüsi utiliit OpenCppCoverage ja staatilise analüüsi utiliit Cppcheck. Siiski selgub, et nende utiliitide töö korraldamiseks ja väljundi sobitamiseks SonarQube Scanneri vajadustega tuleb kirjutada paar skripti: üks PowerShellis ja teine Windowsi pakkfailina. Regulaarselt ajastatud analüüside käivitamist tagab QuickBuild, -

A DSL for Resource Checking Using Finite State Automaton-Driven Symbolic Execution Code
Open Comput. Sci. 2021; 11:107–115 Research Article Endre Fülöp and Norbert Pataki* A DSL for Resource Checking Using Finite State Automaton-Driven Symbolic Execution https://doi.org/10.1515/comp-2020-0120 code. Compilers validate the syntactic elements, referred Received Mar 31, 2020; accepted May 28, 2020 variables, called functions to name a few. However, many problems may remain undiscovered. Abstract: Static analysis is an essential way to find code Static analysis is a widely-used method which is by smells and bugs. It checks the source code without exe- definition the act of uncovering properties and reasoning cution and no test cases are required, therefore its cost is about software without observing its runtime behaviour, lower than testing. Moreover, static analysis can help in restricting the scope of tools to those which operate on the software engineering comprehensively, since static anal- source representation, the code written in a single or mul- ysis can be used for the validation of code conventions, tiple programming languages. While most static analysis for measuring software complexity and for executing code methods are designed to detect anomalies (called bugs) in refactorings as well. Symbolic execution is a static analy- software code, the methods they employ are varied [1]. One sis method where the variables (e.g. input data) are inter- major difference is the level of abstraction at which the preted with symbolic values. code is represented [2]. Because static analysis is closely Clang Static Analyzer is a powerful symbolic execution related to the compilation of the code, the formats used engine based on the Clang compiler infrastructure that to represent the different abstractions are not unique to can be used with C, C++ and Objective-C. -

SMT-Based Refutation of Spurious Bug Reports in the Clang Static Analyzer
SMT-Based Refutation of Spurious Bug Reports in the Clang Static Analyzer Mikhail R. Gadelha∗, Enrico Steffinlongo∗, Lucas C. Cordeiroy, Bernd Fischerz, and Denis A. Nicole∗ ∗University of Southampton, UK. yUniversity of Manchester, UK. zStellenbosch University, South Africa. Abstract—We describe and evaluate a bug refutation extension bit in a is one, and (a & 1) ˆ 1 inverts the last bit in a. for the Clang Static Analyzer (CSA) that addresses the limi- The analyzer, however, produces the following (spurious) bug tations of the existing built-in constraint solver. In particular, report when analyzing the program: we complement CSA’s existing heuristics that remove spurious bug reports. We encode the path constraints produced by CSA as Satisfiability Modulo Theories (SMT) problems, use SMT main.c:4:12: warning: Dereference of null solvers to precisely check them for satisfiability, and remove pointer (loaded from variable ’z’) bug reports whose associated path constraints are unsatisfi- return *z; able. Our refutation extension refutes spurious bug reports in ˆ˜ 8 out of 12 widely used open-source applications; on aver- age, it refutes ca. 7% of all bug reports, and never refutes 1 warning generated. any true bug report. It incurs only negligible performance overheads, and on average adds 1.2% to the runtime of the The null pointer dereference reported here means that CSA full Clang/LLVM toolchain. A demonstration is available at claims to nevertheless have found a path where the dereference https://www.youtube.com/watch?v=ylW5iRYNsGA. of z is reachable. Such spurious bug reports are in practice common; in our I. -

The Kate Handbook
The Kate Handbook Anders Lund Seth Rothberg Dominik Haumann T.C. Hollingsworth The Kate Handbook 2 Contents 1 Introduction 10 2 The Fundamentals 11 2.1 Starting Kate . 11 2.1.1 From the Menu . 11 2.1.2 From the Command Line . 11 2.1.2.1 Command Line Options . 12 2.1.3 Drag and Drop . 13 2.2 Working with Kate . 13 2.2.1 Quick Start . 13 2.2.2 Shortcuts . 13 2.3 Working With the KateMDI . 14 2.3.1 Overview . 14 2.3.1.1 The Main Window . 14 2.3.2 The Editor area . 14 2.4 Using Sessions . 15 2.5 Getting Help . 15 2.5.1 With Kate . 15 2.5.2 With Your Text Files . 16 2.5.3 Articles on Kate . 16 3 Working with the Kate Editor 17 4 Working with Plugins 18 4.1 Kate Application Plugins . 18 4.2 External Tools . 19 4.2.1 Configuring External Tools . 19 4.2.2 Variable Expansion . 20 4.2.3 List of Default Tools . 22 4.3 Backtrace Browser Plugin . 25 4.3.1 Using the Backtrace Browser Plugin . 25 4.3.2 Configuration . 26 4.4 Build Plugin . 26 The Kate Handbook 4.4.1 Introduction . 26 4.4.2 Using the Build Plugin . 26 4.4.2.1 Target Settings tab . 27 4.4.2.2 Output tab . 28 4.4.3 Menu Structure . 28 4.4.4 Thanks and Acknowledgments . 28 4.5 Close Except/Like Plugin . 28 4.5.1 Introduction . 28 4.5.2 Using the Close Except/Like Plugin . -

Compiling and Makefiles
Compiling C Programs Makefiles Compiling and Makefiles 2501ICT/7421ICTNathan René Hexel School of Information and Communication Technology Griffith University Semester 1, 2012 René Hexel Compiling and Makefiles Compiling C Programs Makefiles Outline 1 Compiling C Programs 2 Makefiles Using the make Utility Makefiles for Objective-C Code Makefiles for C++ Code René Hexel Compiling and Makefiles Compiling C Programs Makefiles Compiling C Programs Integrated Development Environment (IDE) Eclipse, XCode, Visual C++, Project Center, . Compiles programs at the press of a button (like BlueJ) Often difficult to customise Very rarely support multiple platforms and languages Command Line Requires manual invocation Requires knowledge of command line parameters Can be tedious for large projects Cross-platform and -language compilers (e.g. clang) Makefiles Combine the best of both worlds Recompile a complex project with a simple make command René Hexel Compiling and Makefiles Compiling C Programs Makefiles Getting a Command Line Interface Via Dwarf ssh dwarf.ict.griffith.edu.au using putty (Windows) Via a local Terminal Mac OS X: e.g. Applications / Utilities / Terminal.app Linux: e.g. through the Gnome program menu Windows: e.g. Start / Programs / Programming Tools / GNUstep / Shell ) Enter commands to compile your program Hit Return (or Enter) after every command! René Hexel Compiling and Makefiles Compiling C Programs Makefiles Compiling a C program using clang or gcc Once on the command line change to the directory (folder) your program is in cd /my/example/directory -

ENCM 335 Fall 2018: Command-Line C Programming on Macos
page 1 of 4 ENCM 335 Fall 2018: Command-line C programming on macOS Steve Norman Department of Electrical & Computer Engineering University of Calgary September 2018 Introduction This document is intended to help students who would like to do ENCM 335 C pro- gramming on an Apple Mac laptop or desktop computer. A note about software versions The information in this document was prepared using the latest versions of macOS Sierra version 10.12.6 and Xcode 9.2, the latest version of Xcode available for that version of macOS. Things should work for you if you have other but fairly recent versions of macOS and Xcode. If you have versions that are several years old, though you may experience difficulties that I'm not able to help with. Essential Software There are several key applications needed to do command-line C programming on a Mac. Web browser I assume you all know how to use a web browser to find course documents, so I won't say anything more about web browsers here. Finder Finder is the tool built in to macOS for browsing folders and files. It really helps if you're fluent with its features. Terminal You'll need Terminal to enter commands and look at output of commands. To start it up, look in Utilities, which is a folder within the Applications folder. It probably makes sense to drag the icon for Terminal to the macOS Dock, so that you can launch it quickly. macOS Terminal runs the same bash shell that runs in Cygwin Terminal, so commands like cd, ls, mkdir, and so on, are all available on your Mac. -
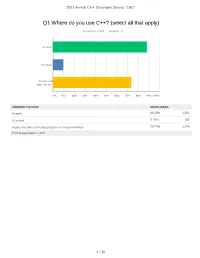
Q1 Where Do You Use C++? (Select All That Apply)
2021 Annual C++ Developer Survey "Lite" Q1 Where do you use C++? (select all that apply) Answered: 1,870 Skipped: 3 At work At school In personal time, for ho... 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES At work 88.29% 1,651 At school 9.79% 183 In personal time, for hobby projects or to try new things 73.74% 1,379 Total Respondents: 1,870 1 / 35 2021 Annual C++ Developer Survey "Lite" Q2 How many years of programming experience do you have in C++ specifically? Answered: 1,869 Skipped: 4 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 7.60% 142 3-5 years 20.60% 385 6-10 years 20.71% 387 10-20 years 30.02% 561 >20 years 21.08% 394 TOTAL 1,869 2 / 35 2021 Annual C++ Developer Survey "Lite" Q3 How many years of programming experience do you have overall (all languages)? Answered: 1,865 Skipped: 8 1-2 years 3-5 years 6-10 years 10-20 years >20 years 0% 10% 20% 30% 40% 50% 60% 70% 80% 90% 100% ANSWER CHOICES RESPONSES 1-2 years 1.02% 19 3-5 years 12.17% 227 6-10 years 22.68% 423 10-20 years 29.71% 554 >20 years 34.42% 642 TOTAL 1,865 3 / 35 2021 Annual C++ Developer Survey "Lite" Q4 What types of projects do you work on? (select all that apply) Answered: 1,861 Skipped: 12 Gaming (e.g., console and.. -

Compiling Linux with LLVM
Open Source Open Possibilities Compiling Linux with LLVM Presented by: Mark Charlebois Presentation Date: 06/07/2012 PAGE 1 Open Source Open Possibilities Agenda Why would I want to use Clang to compile Linux? Status updates: cross compiling for ARM with Clang building Linux kernel with Clang running Linux compiled with Clang To do list PAGE 2 Open Source Open Possibilities Open Source Open Possibilities Why Would I Want to Use Clang to Compile Linux? PAGE 3 Open Source Open Possibilities Better Diagnostics $ gcc-4.2 -fsyntax-only t.c t.c:7: error: invalid operands to binary + (have 'int' and 'struct A') $ clang -fsyntax-only t.c t.c:7:39: error: invalid operands to binary expression ('int' and 'struct A') return y + func(y ? ((SomeA.X + 40) + SomeA) / 42 + SomeA.X : SomeA.X); ~~~~~~~~~~~~~~ ^ ~~~~~ See http://clang.llvm.org/diagnostics.html for more examples GCC extensions: all extensions are explicitly recognized as such and marked with extension diagnostics, which can be mapped to warnings, errors, or just ignored. Google builds their products also with Clang just for the better debug output Rich diagnostic output enables auto-generation of patches PAGE 4 Open Source Open Possibilities Fix-it Hints "Fix-it" hints provide advice for fixing small, localized problems in source code. $ clang t.c t.c:5:28: warning: use of GNU old-style field designator extension struct point origin = { x: 0.0, y: 0.0 }; ~~ ^ .x = t.c:5:36: warning: use of GNU old-style field designator extension struct point origin = { x: 0.0, y: 0.0 }; ~~ ^ .y = PAGE 5 -

The Breadth and Depth of Early Learning Standards
March 2005 INSIDE THE CONTENT: THE BREADTH AND DEPTH OF EARLY LEARNING STANDARDS By Catherine Scott-Little Sharon Lynn Kagan Victoria Stebbins Frelow Inside the Content: The Breadth and Depth of Early Learning Standards By Catherine Scott-Little, Ph.D. Human Development and Family Studies SERVE University of North Carolina at Greensboro Sharon Lynn Kagan, Ed.D. Victoria Stebbins Frelow Teachers College Columbia University In Association with the School of Education University of North Carolina at Greensboro 2005 Edited by Donna Nalley, Ph.D., SERVE Publications Director Karen DeMeester, Ph.D., SERVE Publications Cover Design by Shelley Call, SERVE Graphic Designer Research and production of this document were supported by the Institute of Education Sciences, U.S. Department of Education, through the Regional Educational Laboratory at SERVE (under contract no. ED-01-CO-0015). The findings and opinions expressed do not necessarily reflect the position or policies of IES or the U.S. Department of Education. Acknowledgments We would like to thank a number of persons who were instrumental to our efforts to bring this work to fruition. Rosemarie Andrews, Sarah Boeving, Amanda Weisner, and Jennifer Kunzman’s assistance in development of the document was invaluable. We would also like to thank Victoria Seitz for her insightful assistance with data analysis for the report. We especially would like to thank the early childhood specialists in state departments of education who participated in the interviews for Phase 1 of this study and have continued to provide us with updated standards documents and insights on early learning standards. We are grateful to each of the informants for their interest in this study and their tireless dedication to their work on behalf of families and children. -

Kdevelop Handbook
KDevelop Handbook This documentation was converted from the KDE UserBase KDevelop4/Manual page. KDevelop Handbook 2 Contents 1 What is KDevelop?6 2 Sessions and projects: The basics of KDevelop8 2.1 Terminology . .8 2.2 Setting up a session and importing an existing project . .9 2.2.1 Option 1: Importing a project from a version control system server . .9 2.2.2 Option 2: Importing a project that is already on your hard drive . 10 2.3 Setting up an application as a second project . 10 2.4 Creating projects from scratch . 10 3 Working with source code 12 3.1 Tools and views . 12 3.2 Exploring source code . 14 3.2.1 Local information . 14 3.2.2 File scope information . 16 3.2.3 Project and session scope information . 17 3.2.4 Rainbow color highlighting explained . 19 3.3 Navigating in source code . 19 3.3.1 Local navigation . 19 3.3.2 File scope navigation and outline mode . 20 3.3.3 Project and session scope navigation: Semantic navigation . 21 3.4 Writing source code . 25 3.4.1 Auto-completion . 25 3.4.2 Adding new classes and implementing member functions . 27 3.4.3 Documenting declarations . 31 3.4.4 Renaming variables, functions and classes . 34 3.4.5 Code snippets . 35 3.5 Modes and working sets . 37 3.6 Some useful keyboard shortcuts . 39 KDevelop Handbook 4 Code generation with templates 41 4.1 Creating a new class . 41 4.2 Creating a new unit test . 43 4.3 Other files .