Desktop Computer Terminal Meaning
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
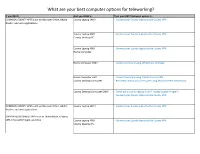
What Are Your Best Computer Options for Teleworking?
What are your best computer options for teleworking? If you NEED… And you HAVE a… Then your BEST telework option is… COMMON COUNTY APPS such as Microsoft Office, Adobe County Laptop ONLY - Connect your County laptop to the County VPN Reader, and web applications County Laptop AND - Connect your County laptop to the County VPN County Desktop PC County Laptop AND - Connect your County laptop to the County VPN Home Computer Home Computer ONLY - Connect remotely using VDI (Virtual Desktop) Home Computer AND - Connect remotely using Dakota County VPN County Desktop Computer - Remotely control your computer using Windows Remote Desktop County Desktop Computer ONLY - Check out a County laptop from IT Laptop Loaner Program - Connect your County laptop to the County VPN COMMON COUNTY APPS such as Microsoft Office, Adobe County Laptop ONLY - Connect your County laptop to the County VPN Reader, and web applications SUPPORTED BUSINESS APPS such as OneSolution, OnBase, SIRE, Microsoft Project, and Visio County Laptop AND - Connect your County laptop to the County VPN County Desktop PC If you NEED… And you HAVE a… Then your BEST telework option is… County Laptop AND - Connect your County laptop to the County VPN Home Computer Home Computer ONLY - Contact the County IT Help Desk at 651/438-4346 Home Computer AND - Connect remotely using Dakota County VPN County Desktop Computer - Remotely control your computer using Windows Remote Desktop County Desktop Computer ONLY - Check out a County laptop from IT Laptop Loaner Program - Connect your County laptop -

A Secure Peer-To-Peer Web Framework
A Secure Peer-to-Peer Web Framework Joakim Koskela Andrei Gurtov Helsinki Institute for Information Technology Helsinki Institute for Information Technology PO Box 19800, 00076 Aalto PO Box 19800, 00076 Aalto Email: joakim.koskela@hiit.fi Email: andrei.gurtov@hiit.fi Abstract—We present the design and evaluation of a se- application, that can be deployed without investing in dedi- cure peer-to-peer HTTP middleware framework that enables cated infrastructure while addressing issues such as middlebox a multitude of web applications without relying on service traversal, mobility, security and identity management. providers. The framework is designed to be deployed in existing network environments, allowing ordinary users to create private II. PEER-TO-PEER HTTP services without investing in network infrastructure. Compared to previous work, scalability, NAT/firewall traversal and peer From its launch in the early 1990s, the HyperText Transfer mobility is achieved without the need for maintaining dedicated Protocol (HTTP) had grown to be one of the most popular servers by utilizing new network protocols and re-using existing protocols on the Internet today. It is used daily for everything network resources. from past-time activities, such as recreational browsing, gam- I. INTRODUCTION ing and media downloads, to business- and security-critical Peer-to-peer (P2P) systems have been popular within net- applications such as payment systems and on-line banking. work research during the past years as they have the potential The success of HTTP has clearly grown beyond its original to offer more reliable, fault-tolerant and cost-efficient network- design as a simple, easy to manage protocol for exchanging ing. -

I.L. 40-614A 1 1. INTRODUCTION the Basic Interface to Remote Terminal, Or BIRT, Is an INCOM Network Master. BIRT Gives Users An
I.L. 40-614A 1. INTRODUCTION 3. DESCRIPTION The Basic Interface to Remote Terminal, or BIRT, is 3.1. Power Requirements an INCOM Network Master. BIRT gives users an economical way of getting information from their Range: 48 Vdc to 250 Vdc and 120 Vac INCOM-compatible devices since it connects directly between a user’s external MODEM or personal com- Burden: 3.5 W @ 48 Vdc puter and the INCOM network. 9 W @ 250 Vdc 5 W @ 120 Vac BIRT can directly replace Westinghouse MINTs, talk- ing to all INCOM-based communication devices. 3.2. Temperature Range BIRTs also include a special high-speed mode for communicating with SADIs – allowing users to collect For Operation: 0˚ to +55˚ C data from other manufacturer’s relays more rapidly For Storage: -20˚ to +80˚ C than ever before. 3.3. Physical Dimensions BIRTs are built to handle the abuse of substation environment; their “hardened” RS-232 serial port can The BIRT enclosure dimensions are identical to the handle surges and sustained high voltages that ERNI and SADI, as shown in figure 1. would destroy ordinary serial ports, and BIRTs can run on a wide range of voltages, from 48 to 250 Vdc Dimensions and weight of chassis or even 120 Vac, with no jumpers or adjustments needed. Height: 5.26” (133.6) mm) Width: 3.32” (84.3) mm) Depth: 5.92” (150.4) mm) 2. FEATURES Weight: 2.0 lbs (0.9 kg) BIRT is designed to be very flexible in its RS-232 External Wiring: See figures 2 and 3. -

Introduction to Peer-To-Peer Networks
Introduction to Peer-to-Peer Networks The Story of Peer-to-Peer The Nature of Peer-to-Peer: Generals & Paradigms Unstructured Peer-to-Peer Systems Sample Applications 1 Prof. Dr. Thomas Schmidt http:/www.informatik.haw-hamburg.de/~schmidt A Peer-to-Peer system is a self-organizing system of equal, autonomous entities (peers) which aims for the shared usage of distributed resources in a networked environment avoiding central services. Andy Oram 2 Prof. Dr. Thomas Schmidt http:/www.informatik.haw-hamburg.de/~schmidt The Old Days NetNews (nntp) Usenet since 1979, initially based on UUCP Exchange (replication) of news articles by subscription Group creation/deletion decentralised DNS Distributed delegation of name authorities: file sharing of host tables Name “Servers” act as peers Hierarchical information space permits exponential growth Systems are manually configured distributed peers 3 Prof. Dr. Thomas Schmidt http:/www.informatik.haw-hamburg.de/~schmidt SETI@home: Distributed Computing Search for Extraterrestrial Intelligence (SETI) Analyse radio sig- nals from space Globally shared computing res. Idea 1995 First version 1998 2002 ≈ 4 Mio clnt E.g. Screensaver From Anderson et. al.: SETI@home, Comm. ACM, 45 (11), Nov. 2002 http://setiathome.berkeley.edu/ - ongoing 4 Prof. Dr. Thomas Schmidt http:/www.informatik.haw-hamburg.de/~schmidt SETI@home (2) http-based client-server model No client-client communication Data chunks: load & return N-redundancy for fault detection Attacks: bogus code From Anderson -

Peer-To-Peer Networks
Peer-to-Peer Networks 14-740: Fundamentals of Computer Networks Credit to Bill Nace, 14-740, Fall 2017 Material from Computer Networking: A Top Down Approach, 6th edition. J.F. Kurose and K.W. Ross traceroute • P2P Overview • Architecture components • Napster (Centralized) • Gnutella (Distributed) • Skype and KaZaA (Hybrid, Hierarchical) • KaZaA Reverse Engineering Study 14-740: Spring 2018 2 What is P2P? • Client / Server interaction • Client: any end-host • Server: specific end-host • P2P: Peer-to-peer • Any end-host • Aim to leverage resources available on “clients” (peers) • Hard drive space • Bandwidth (especially upload) • Computational power • Anonymity (i.e. Zombie botnets) • “Edge-ness” (i.e. being distributed at network edges) • Clients are particularly fickle • Users have not agreed to provide any particular level of service • Users are not altruistic -- algorithm must force participation without allowing cheating • Clients are not trusted • Client code may be modified • And yet, availability of resources must be assured P2P History • Proto-P2P systems exist • DNS, Netnews/Usenet • Xerox Grapevine (~1982): name, mail delivery service • Kicked into high gear in 1999 • Many users had “always-on” broadband net connections • 1st Generation: Napster (music exchange) • 2nd Generation: Freenet, Gnutella, Kazaa, BitTorrent • More scalable, designed for anonymity, fault-tolerant • 3rd Generation: Middleware -- Pastry, Chord • Provide for overlay routing to place/find resources 14-740: Spring 2018 6 P2P Architecture • Content Directory -

Resource Guide: Workstation Productivity
Resource Guide: Workstation Productivity Contents Beyond the Desktop: Workstation Productivity ……………………………………………………2 Find out how to get the highest productivity possible from high performance applications that require more power than traditional desktop computers Top IT Considerations for Mobile Workstations …………………...............................................4 Discover the top IT considerations for organization that require mobile workstations designed to provide a balance of performance and portability Maximum Management and Control with Virtualized Workstations ....…………………...…….6 Explore the benefits of virtualization to ensure the greatest possible management and control of high performance workstations for the most demanding workloads and applications Sponsored by: Page 1 of 6 Copyright © MMIX, CBS Broadcasting Inc. All Rights Reserved. For more downloads and a free TechRepublic membership, please visit http://techrepublic.com.com/2001-6240-0.html TechRepublic Resource Guide: Workstations Productivity Beyond the Desktop: Workstation Productivity Find out how to get the highest productivity possible from high performance applications that require more power than traditional desktop computers Desktop computers have come a long way in terms of value and performance for the average user but more advanced applications now require even more in terms of processing, graphics, memory and storage. The following is a brief overview of the differences between standard desktops and workstations as well as the implications for overall performance and productivity as compiled from the editorial resources of CNET, TechRepublic and ZDNet.com. Think Inside the Box A lot of people tend to think of desktop computers and computer workstation as one and the same but that isn’t always the case in terms of power and performance. In fact, many of today’s most demanding workloads and applications for industries such as engineering, entertainment, finance, manufacturing, and science actually require much higher functionality than what traditional desktops have to offer. -

Good Reasons to Use a Desktop Computer
Good reasons to use a desktop computer Why would anyone possibly need a desktop? For most, it goes against all common sense to use a desktop because they're not as convenient and portable as a lap- top, and a laptop does what you need it to do just fine. At the same time, the good ol' bulky, stationary desktop still has a place for many people. Here are good reasons why you might want to use desktop computer. You can upgrade the parts, which is cheaper than buying a new laptop. When a laptop starts to slow down, your only option is to buy a whole new one. Depending on what you need a com- puter for, a new laptop could cost thousands of dollars. That's because you have to buy every single part inside the laptop brand new — the processor, motherboard, RAM, hard drive, and everything else. But most of the parts in your old laptop are probably still fine, and it's usually only the processor (and the motherboard it sits on) that needs upgrading. With a desktop you can easily replace an aging processor (and motherboard) for around $300. That said, all-in-one desktops like the iMac can be a little difficult to upgrade. You get more bang for your buck. Depending on the brand, desktops and laptops with similar specs can often cost the same. Yet, the main differences between the two are the processor and the graphics processor. Most Laptops use the smaller mobile version of a processor model, which often aren't quite as powerful as the full-size desktop versions. -

Secure Shell- Its Significance in Networking (Ssh)
International Journal of Application or Innovation in Engineering & Management (IJAIEM) Web Site: www.ijaiem.org Email: [email protected] Volume 4, Issue 3, March 2015 ISSN 2319 - 4847 SECURE SHELL- ITS SIGNIFICANCE IN NETWORKING (SSH) ANOOSHA GARIMELLA , D.RAKESH KUMAR 1. B. TECH, COMPUTER SCIENCE AND ENGINEERING Student, 3rd year-2nd Semester GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India 2.Assistant Professor Computer Science and Engineering GITAM UNIVERSITY Visakhapatnam, Andhra Pradesh India ABSTRACT This paper is focused on the evolution of SSH, the need for SSH, working of SSH, its major components and features of SSH. As the number of users over the Internet is increasing, there is a greater threat of your data being vulnerable. Secure Shell (SSH) Protocol provides a secure method for remote login and other secure network services over an insecure network. The SSH protocol has been designed to support many features along with proper security. This architecture with the help of its inbuilt layers which are independent of each other provides user authentication, integrity, and confidentiality, connection- oriented end to end delivery, multiplexes encrypted tunnel into several logical channels, provides datagram delivery across multiple networks and may optionally provide compression. Here, we have also described in detail what every layer of the architecture does along with the connection establishment. Some of the threats which Ssh can encounter, applications, advantages and disadvantages have also been mentioned in this document. Keywords: SSH, Cryptography, Port Forwarding, Secure SSH Tunnel, Key Exchange, IP spoofing, Connection- Hijacking. 1. INTRODUCTION SSH Secure Shell was first created in 1995 by Tatu Ylonen with the release of version 1.0 of SSH Secure Shell and the Internet Draft “The SSH Secure Shell Remote Login Protocol”. -

Terminal Services Manager Getting Started
Terminal Services Manager Getting Started LizardSystems Table of Contents Introduction 3 Installing Terminal Services Manager 3 Before starting the application 4 Starting the application 5 Connect to a Remote Desktop Services Servers 6 User Interface 10 Main Window 10 Main menu 11 Administrative tools 16 Network tools 16 Toolbar 17 Computer list 18 Servers tab 19 Users tab 20 Sessions tab 22 Processes tab 23 Dialog boxes 25 Add Computer 25 Create New Group 26 Add Computers Wizard 26 Import computers from network 27 Import computers from Active Directory 28 Import computers from IP Range 28 Import computers from file 30 Search for computers 30 Select grouping type for computers 31 Add computers to list 32 Preferences 33 General 33 Computer list 34 Terminal services 35 2 Terminal Services Manager - Getting Started Introduction Using Terminal Services Manager, you can see the details of users connected to a remote host, their sessions, and their active processes. For several hosts simultaneously, you can monitor each user, session, and process's usage of remote host resources (CPU, memory, etc.) in real-time. Using Terminal Services Manager, you can easily perform various administrative tasks to manage resources and users on a remote host, for example, disconnecting all inactive users, closing inactive users' sessions, or terminating a remote host process. You may use Terminal Services Manager to view information and monitor servers, users, sessions, and processes on servers running Windows Server. You can also perform certain administrative tasks; for example, you can disconnect or log off users from their Remote Desktop Services sessions. Installing Terminal Services Manager • You can install Terminal Services Manager after downloading it from the Download page. -

VMS CRA Y Station Now Available It Is Now Possible to Submit Jobs Functions Closely
VMS CRA Y Station Now Available It is now possible to submit jobs Functions closely. It is implemented as a to the CRAY-1 from UCC's VAX/VMS The VMS station provides these series of commands entered in system. functions: response to the system's $ A CRAY-1 running the cos oper prompt. The commands look like ating system requires another -It submits jobs to the CRAY-1, VMS commands: they have pa computer to act as a "front-end" and returns output as a file un rameters and /qualifiers; they fol system. You prepare jobs and der the user's VMS directory. low much the same syntax and data on the front-end system, us -It transfers files between the interpretation rules (for example, ing whatever tools that system machines using the cos AC wild cards are handled correctly); provides, then submit the files as QUIRE and DISPOSE commands. and they prompt for required a batch job to the CRAY for proc The source of an ACQUIREd file parameters not present on the essing. Output is returned to the can be disk or tape; the desti command line. You can always front-end system for viewing. nation of a DISPOSEd file can recognize a station command, The software that runs on the be disk, tape, printer, or the though, because it always begins front-end machine to provide this VMS batch input queue. with the letter C. For example, communication is called a -At your option, it sends bulle the station command to submit a "station." tins to the terminal chronicling job to the CRAY is CSUBMIT. -

Today Computers Are All Around Us. from Desktop Computers To
Today computers are all around us. From desktop computers to smartphones, they're changing the way that we live our lives. But have you ever asked yourself what exactly is a computer? A computer is an electronic device that manipulates information or data. The computer sees data as ones and zeros but it knows how to combine them into more complex things such as a photograph, a movie, a website, a game and much more... Computers use a combination of hardware and software. Hardware is any physical part of the computer which includes all of the internal components and also the external parts like the monitor and keyboard. Software is any set of instructions that tells the hardware what to do such as a web browser, media player or word processor. Now when most people say computer, they're talking about a personal computer. This can be a desktop computer or a laptop computer which has basically the same capabilities but in a more portable package. Personal computers come in two main styles, PC and Mac. PCs are the most common types, there are many different companies that make them and they usually come with the Microsoft Windows operating system. Macs or Macintosh computers are all made by one company, Apple, and they come with the Mac OS 10 operating system. Computers come in many other shapes and sizes, mobile phones, tablets, game consoles and even TVs have built-in computers, although they may not do everything a desktop or laptop can. There is another type of computer that plays an important role in our lives, servers. -

Desktop Computer Replacement Program Date: May 22, 2019 From: Information Technology Department Presentation Steve Ely, I.T
CITY COUNCIL AGENDA REPORT MEETING DATE: JUNE 4, 2019 ITEM NUMBER: CC-7 SUBJECT: DESKTOP COMPUTER REPLACEMENT PROGRAM DATE: MAY 22, 2019 FROM: INFORMATION TECHNOLOGY DEPARTMENT PRESENTATION STEVE ELY, I.T. DIRECTOR BY: FOR FURTHER INFORMATION STEVE ELY, I.T. DIRECTOR, 714-754-4891 CONTACT: RECOMMENDATION: Staff recommends that the City Council: 1 . Approve the Desktop Computer Replacement Program for the purchase of 435 desktop computers in three phases to replace the computers that have already reached their end-of-life stage. 2. Approve and authorize the Acting City Manager to execute a purchase order with Dell Marketing, LP. (Dell) in the amount of $166,266.27 for completion of the first phase of the Desktop Computer Replacement Program, which includes the purchase of 140 desktop computers. BACKGROUND: The City purchased 435 desktop computers in 2013. These computers have long passed their life expectancy. Their warranty expired in 2016, which makes them prone to issues and causes staff to have to troubleshoot or make repairs as much as they can. In addition to dedicating time for repairs, parts may become obsolete or costly to obtain, resulting in the necessity to purchase new equipment. Desktop computers are the most heavily used pieces of equipment and upgrading them will allow employees to be more efficient in their daily duties and provide the assurance that data and information will not be lost due to aging equipment. ANALYSIS: Many department computers have exceeded their useful life and become inefficient in performing normal functions. Over time, these resources wear, age, 1 and/or become obsolete, causing performance degradation, excessive support and repair activity, and loss of reliability.