Oracle® Secure Global Desktop Platform Support and Release Notes for Release 5.4
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Trabajo De Diploma
Universidad Central “Marta Abreu” de Las Villas Facultad de Ingeniería Eléctrica Departamento de Automática y Sistemas Computacionales TRABAJO DE DIPLOMA Virtualización de la Red UCLV Autor: Okier Arzola Rodríguez Tutor: M.Sc: Miriel Martín Mesa M.Sc: Manuel Oliver Domínguez Santa Clara 2011 "Año 53 de la Revolución" Universidad Central “Marta Abreu” de Las Villas Facultad de Ingeniería Eléctrica Departamento de Automática y Sistemas Computacionales TRABAJO DE DIPLOMA Virtualización de la Red UCLV Autor: Okier Arzola Rodríguez [email protected] Tutor: M.Sc: Miriel Martín Mesa CEETA, Facultad de Ing. Mecánica, UCLV Email: [email protected] M.Sc: Manuel Oliver Domínguez Dpto. de Automática, Facultad de Ing. Eléctrica, UCLV Email: [email protected] Santa Clara 2011 "Año 53 de la Revolución" Hago constar que el presente trabajo de diploma fue realizado en la Universidad Central “Marta Abreu” de Las Villas como parte de la culminación de estudios de la especialidad de Ingeniería en Automática, autorizando a que el mismo sea utilizado por la Institución, para los fines que estime conveniente, tanto de forma parcial como total y que además no podrá ser presentado en eventos, ni publicados sin autorización de la Universidad. Firma del Autor Los abajo firmantes certificamos que el presente trabajo ha sido realizado según acuerdo de la dirección de nuestro centro y el mismo cumple con los requisitos que debe tener un trabajo de esta envergadura referido a la temática señalada. Firma del Autor Firma del Jefe de Departamento donde se defiende el trabajo Firma del Responsable de Información Científico-Técnica i PENSAMIENTO El futuro tiene muchos nombres. -

Oracle® Secure Global Desktop Platform Support and Release Notes for Release 4.7
Oracle® Secure Global Desktop Platform Support and Release Notes for Release 4.7 E26357-02 November 2012 Oracle® Secure Global Desktop: Platform Support and Release Notes for Release 4.7 Copyright © 2012, Oracle and/or its affiliates. All rights reserved. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open Group. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. -

Oracle 1Z0-559 Exam
Oracle 1Z0-559 Exam Volume: 76 Questions Question No : 1 Which three platforms are supported for the Oracle Virtual Desktop client? A. Windows 7 B. Wyse OS C. iPad iOS D. Solaris 10 E. Apple Mac OS X Answer: A,C,E Question No : 2 Identify the Desktop state where the desktop isassigned,butisnot currently in use or the userhaslogged off. A. Available B. Used C. Idle D. Reserved E. Unresponsive Answer: C Question No : 3 Which two hypervisor options do notsupport template revision management from theOracleVDIadmin GUI? A. OracleVirtualBox B. Microsoft Windows2008 Hyper-V Leading the way in IT testing and certification tools, www.examkiller.net Oracle 1Z0-559 Exam C. VMware vSphere D. Citrix XenDesktop Answer: B,C Question No : 4 Users cannot login to their desktops and after investigation it seems to have started right after the primary LDAP server went offline. What settings need to be the same on the primary LDAP server and backup LDAP server so that VDI will continue to operate? A. The same security level, TCP port, base dim, and credentials B. The same hostname,LDAP server, MAC address, and baseDN C. The same DNSname, baseDN, SSLcertificates,andversion ofLDAP D. The same toot password, base DN, SSI certificates, and forest configuration Answer: D Question No : 5 Which two guest operating systemsare supported when deploying a VMware vSphere Desktop Provider within OracleVDI? A. Oracle Linux 5.6 B. Windows 2000 SP4 C. Windows 7 D. Oracle Solaris 10 E. Windows XP Answer: B,E Question No : 6 A customer has an IT group that needs to be able to plug in USB 2.0 devices. -

Oracle Solaris 11 Express What's
ORACLE SOLARIS 11 EXPRESS 2010.11 | WHAT’S NEW ORACLE SOLARIS 11 EXPRESS 2010.11 WHAT’S NEW Oracle Solaris is the industry leading operating system for the enterprise. Oracle Solaris 11 Express 2010.11 raises the bar on the innovation introduced in Oracle Solaris 10, with a unique feature set NEW FEATURE HIGHLIGHTS that few other operating systems can offer. Oracle Solaris 11 Express 2010.11 has been tested and • Oracle Solaris 10 Zones for business optimized for Oracle hardware and software, and is an integral part of Oracle's combined hardware investment protection and software portfolio. • Built-in network virtualization and resource Oracle Solaris 11 Express 2010.11 provides customers with the latest access to Oracle Solaris 11 management for enhanced server workload technology, allowing developers, architects and administrators to test and deploy within an consolidation enterprise environments and greatly simplify their day to day operations. Oracle Solaris 11 Express 2010.11 has the reliability, availability, and serviceability that you'd expect from a leading • Greatly reduced planned and unplanned downtime with new package management tools enterprise operating system. with safe system upgrade With new features such as network based package management tools to greatly decrease planned • New optimizations and features designed to system downtime and provide for a completely safe system upgrade, built-in network virtualization deliver proven scalability and reliability as an and resource control management for an unprecedented level of flexibility for application integrated component of Oracle's Exadata and consolidation, and on-disk ZFS encryption to provide the highest levels of security in your data Exalogic systems center, Oracle Solaris 11 Express 2010.11 is the most exciting release of the Oracle Solaris platform to date. -

Oracle VDI Collected Informations ======Stand 10/2011
Oracle VDI collected informations ============================ Stand 10/2011 Oracle Virtualization Blog http://blogs.oracle.com/virtualization/ Oracle Think Thin Blog http://blogs.oracle.com/ThinkThin/ Oracle Wim Coekaerts Blog Our Senior Vice President, Linux and Virtualization http://blogs.oracle.com/wim/ New Desktop Virtualization White Paper http://www.oracle.com/us/technologies/virtualization/client-access-for-oracle-apps-428850.pdf This paper describes the difficulties customers often have deploying Oracle Apps and how the desktop virtualization products can make this process significantly more streamlined and easier to manage. New VDI TCO Tool available A new desktop virtualization TCO calculator is now available on oracle.com. You can access it directly here http://www.oracle.com/us/media/calculator/vdi/index.html The calculator operates in two modes, simple and detailed. The above link takes you to the simple calculator. From there, you can choose to register with us and will be given access to the detailed calculator. Desktop Templates (ready for testing) ------------------------------------------------- Oracle VM Sun Ray 5 Template http://www.oracle.com/technetwork/server-storage/vm/sunray-171445.html Oracle VM Secure Global Desktop Template http://www.oracle.com/technetwork/server-storage/vm/sgd-171455.html Oracle VDI Software 3.3 available since July 6, 2011 -------------------------------------------------------------------- What's new in VDI 3.3 VDI is now supported for Solaris x86 and Oracle Linux (Red Hat) Role based administration -

Oracle® Virtual Desktop Infrastructure Update Guide for Version 3.2.2
Oracle® Virtual Desktop Infrastructure Update Guide for Version 3.2.2 April 2011 Copyright © 2011, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this software or related documentation is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle USA, Inc., 500 Oracle Parkway, Redwood City, CA 94065. -

Oracle® Virtual Desktop Client Release Notes for Release 3.2
Oracle® Virtual Desktop Client Release Notes for Release 3.2 E36350-03 January 2013 Oracle® Virtual Desktop Client: Release Notes for Release 3.2 Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open Group. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. -

Oracle® Solaris 11.3 Desktop User's Guide
® Oracle Solaris 11.3 Desktop User's Guide Part No: E54809 April 2020 Oracle Solaris 11.3 Desktop User's Guide Part No: E54809 Copyright © 2011, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -

Enterprise Manager for Oracle VDI Plug-In User's Guide for Release 3.5
Enterprise Manager for Oracle VDI Plug-in User's Guide for Release 3.5 E38982-02 March 2013 Enterprise Manager for Oracle VDI: Plug-in User's Guide for Release 3.5 Copyright © 2013, Oracle and/or its affiliates. All rights reserved. Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners. Intel and Intel Xeon are trademarks or registered trademarks of Intel Corporation. All SPARC trademarks are used under license and are trademarks or registered trademarks of SPARC International, Inc. AMD, Opteron, the AMD logo, and the AMD Opteron logo are trademarks or registered trademarks of Advanced Micro Devices. UNIX is a registered trademark of The Open Group. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. -
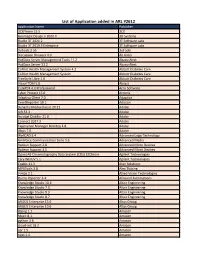
List of Application Added in ARL #2612
List of Application added in ARL #2612 Application Name Publisher 3CXPhone 15.5 3CX Geomagic Design X 2020.0 3D Systems Studio 3T 2021.2 3T Software Labs Studio 3T 2019.3 Enterprise 3T Software Labs 3uTools 2.55 3uTools Discussion Browser 4.0 Ab Initio HotDocs Server Management Tools 11.2 AbacusNext HotDocs Server 11.2 AbacusNext CoPilot Health Management System 4.2 Abbott Diabetes Care CoPilot Health Management System Abbott Diabetes Care FreeStyle Libre 1.0 Abbott Diabetes Care Visual TOM 5.8 Absyss CutePDF 4.0 Professional Acro Software Cyber Protect 15.0 Acronis Adaptiva Client 7.0 Adaptiva EventReporter 10.1 Adiscon Dynamic Media Classic 20.21 Adobe AIR 33.1 Adobe Acrobat Distiller 21.0 Adobe Connect 2021.3 Adobe Experience Manager Desktop 1.8 Adobe JBoss 7.0 Adobe WellCAD 5.4 Advanced Logic Technology AmiVoice Communication Suite 3.6 Advanced Media Radeon Support 2.8 Advanced Micro Devices Radeon Support 3.5 Advanced Micro Devices OpenLAB Chromatography Data System (CDS) EZChrom Agilent Technologies Cary WinUV 5.1 Agilent Technologies Coabis 11.3 Aker Solutions MP4Tools 3.8 Alex Thüring Vimba 2.1 Allied Vision Technologies Query Reporter 3.4 Allround Automations Knowledge Studio 10.4 Altair Engineering Knowledge Studio 7.0. Altair Engineering Knowledge Studio 9.3 Altair Engineering Knowledge Studio 8.7 Altair Engineering ARGUS Enterprise 13.0 Altus Group ARGUS Enterprise 10.6 Altus Group libpng 1.2 Amazon Music 8.1 Amazon python 3.6 Amazon cloud-init 18.2 Amazon apr 1.5 Amazon cups 1.4 Amazon java-1.7.0-openjdk 1.7 Amazon java-1.8.0-openjdk-devel -

Fedora I18n Flock 2017
Fedora i18n Flock 2017 Jens Petersen, Parag Nemade, Pravin Satpute Red Hat i18n/l10n/g11n Track ● Fedora i18n (this session) ● Transtats (3:30pm) ● Fedora G11N (4pm) About us ● Jens Petersen ○ i18n Software Engineering Manager, Red Hat ○ Fedora i18n, Haskell, Packager Sponsor, Fedora Workstation WG ● Parag Nemade ○ Senior Software Engineer, i18n Software Engineering, RH ● Pravin Satpute ○ G11n Quality Engineering Manager, Red Hat I18n Agenda ● F24-F27 Review ● Langpacks auto-installation ● Input methods ● Fonts ● Transtats ● Modularity ● Fedora Editions ● QA and test automation ● Community involvement/events ● Brand Internationalization: ● helps to make your software work uniformly across multiple regions. ● includes adding i18n support in your code which allows UI strings to be translated (l10n). ● helps to set user locale settings such as date, number, currency, sorting, paper size. ● allows users to display and input text in their own preferred language. Globalization, Internationalization, and Localization G11N I18N L10N I18N is a part of G11N Recent Fedora i18n Changes F24 i18n Changes ● Langpacks Installation With RPM Weak Dependencies ● Glibc locale subpackaging F25 i18n Changes ● IBus Emoji Typing ● Unicode 9.0 ● ibus-typing-booster multilingual support ibus Typing Booster Suggestive text input https://mike-fabian.github.io/ibus-typing-booster/ F26 i18n Changes ● libpinyin 2.0 ● Fontconfig cache directory change libpinyin-1.3 libpinyin-2 F27 i18n Changes ● Chinese Serif Fonts ● libpinyin 2.1 ● Flatpak ibus support and fontconfig caches ● Emoji color rendering Chinese Serif font Future features and discussion How to install Langpacks for users? After installing Workstation Live users want to have langpacks for Libreoffice etc automatically installed. Where is do this: A. Initial-setup B. -

Support for Sun Ray Kiosk Session Development Kit (All Topics)
Support for Sun Ray Kiosk Session Development Kit (All Topics) Contents Purpose Support Statement for 3rd Party Provided Kiosk Session Types Support for Examples provided in this Guide Support for information related to System Internals Support for Sun Ray Kiosk Session Development Kit (All Topics) Purpose This guide is intended to enhance the understanding, use of, and development for the Kiosk Mode feature of Sun Ray Server Software (SRSS). This guide contains a more in-depth look at the the Kiosk Mode feature than is found in the official SRSS Documentation. It should be viewed as both a companion and supplemental guide to the official documentation, but it should be viewed as not a replacement. This guide assumes the reader has a basic understanding of the operation of SRSS and does not cover items such as installation and configuration of SRSS, with the exception of where those items may have implications on Kiosk Mode. Support Statement for 3rd Party Provided Kiosk Session Types Oracle fully supports the creation of Kiosk Session Types by 3rd parties for use with Sun Ray Server Software. Any documented interfaces, unless specifically noted otherwise, used by the 3rd Party Provided Kiosk Session Type are supported. For Customers with support contracts, this means service calls can be logged if a reproducible issue occurs with any supported interfaces do not perform as documented. Oracle does not provide support for the actual application used in the custom Kiosk Session Type. The definition of an "application" as it pertains to support of the Kiosk Session Type is the specified script or binary that is referenced by the 'KIOSK_SESSION_EXEC' variable in the custom Kiosk Session Type Descriptor.