Oracle® Secure Global Desktop Platform Support and Release Notes for Release 5.5
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Solaris: the Carrier-Grade Operating System Technical Brief
An Oracle White Paper February 2011 Oracle Solaris: The Carrier-Grade Operating System Oracle White Paper—Oracle Solaris: The Carrier-Grade OS Executive Summary.............................................................................1 ® Powering Communication—The Oracle Solaris Ecosystem..............3 Integrated and Optimized Stack ......................................................5 End-to-End Security ........................................................................5 Unparalleled Performance and Scalability.......................................6 Increased Reliability ........................................................................7 Unmatched Flexibility ......................................................................7 SCOPE Alliance ..............................................................................7 Security................................................................................................8 Security Hardening and Monitoring .................................................8 Process and User Rights Management...........................................9 Network Security and Encrypted Communications .......................10 Virtualization ......................................................................................13 Oracle VM Server for SPARC .......................................................13 Oracle Solaris Zones .....................................................................14 Virtualized Networking...................................................................15 -

Oracle Solaris 11 Overview and Design Guide
Oracle Solaris 11 Overview and Design Guide December 2016 (Edition 1.0) Fujitsu Limited Copyright 2012-2016 FUJITSU LIMITED Preface 1/2 Purpose - This document provides an overview of Oracle Solaris 11 and introduces the new functions. Audience - People who want to study Oracle Solaris 11 - People who already understand an overview of Oracle Solaris Notes - The contents of this document are based on Oracle Solaris 11.3. For the latest information on Oracle Solaris 11, see the manuals from Oracle. - Fujitsu M10 is sold as SPARC M10 Systems by Fujitsu in Japan. Fujitsu M10 and SPARC M10 Systems are identical products. Positioning of documents ⁃ Oracle Solaris 11 http://www.fujitsu.com/global/products/computing/servers/unix/sparc/downloads/documents/ Design Install Operate Oracle Solaris 11 Oracle Solaris 11 Implementation and Operations Guide Overview and Design Guide Oracle Solaris 11 Implementation and Operations Procedure Guide 1 Copyright 2012-2016 FUJITSU LIMITED Preface 2/2 Descriptions in this document - The section numbers of commands are omitted. Example: ⁃ ls(1) => ls command ⁃ shutdown(1M) => shutdown command - The following table lists terms that may be abbreviated. Abbreviation Formal Name Solaris Oracle Solaris Solaris zone Oracle Solaris zone Oracle VM Oracle VM Server for SPARC 2 Copyright 2012-2016 FUJITSU LIMITED Contents 1. Overview of Oracle Solaris 11 2. Installation of Oracle Solaris 11 3. Image Packaging System (IPS) - Oracle Solaris Package Management - 4. ZFS - Oracle Solaris File System - 5. Boot Environment (BE) - Oracle Solaris Boot Environment - 6. Virtualization of Oracle Solaris - Oracle Solaris Zones - 7. Security Appendix 3 Copyright 2012-2016 FUJITSU LIMITED 1. -

Oracle Berkeley DB Installation and Build Guide Release 18.1
Oracle Berkeley DB Installation and Build Guide Release 18.1 Library Version 18.1.32 Legal Notice Copyright © 2002 - 2019 Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. Berkeley DB, and Sleepycat are trademarks or registered trademarks of Oracle. All rights to these marks are reserved. No third- party use is permitted without the express prior written consent of Oracle. Other names may be trademarks of their respective owners. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

Adventures with Illumos
> Adventures with illumos Peter Tribble Theoretical Astrophysicist Sysadmin (DBA) Technology Tinkerer > Introduction ● Long-time systems administrator ● Many years pointing out bugs in Solaris ● Invited onto beta programs ● Then the OpenSolaris project ● Voted onto OpenSolaris Governing Board ● Along came Oracle... ● illumos emerged from the ashes > key strengths ● ZFS – reliable and easy to manage ● Dtrace – extreme observability ● Zones – lightweight virtualization ● Standards – pretty strict ● Compatibility – decades of heritage ● “Solarishness” > Distributions ● Solaris 11 (OpenSolaris based) ● OpenIndiana – OpenSolaris ● OmniOS – server focus ● SmartOS – Joyent's cloud ● Delphix/Nexenta/+ – storage focus ● Tribblix – one of the small fry ● Quite a few others > Solaris 11 ● IPS packaging ● SPARC and x86 – No 32-bit x86 – No older SPARC (eg Vxxx or SunBlades) ● Unique/key features – Kernel Zones – Encrypted ZFS – VM2 > OpenIndiana ● Direct continuation of OpenSolaris – Warts and all ● IPS packaging ● X86 only (32 and 64 bit) ● General purpose ● JDS desktop ● Generally rather stale > OmniOS ● X86 only ● IPS packaging ● Server focus ● Supported commercial offering ● Stable components can be out of date > XStreamOS ● Modern variant of OpenIndiana ● X86 only ● IPS packaging ● Modern lightweight desktop options ● Extra applications – LibreOffice > SmartOS ● Hypervisor, not general purpose ● 64-bit x86 only ● Basis of Joyent cloud ● No inbuilt packaging, pkgsrc for applications ● Added extra features – KVM guests – Lots of zone features – -

Oracle® Secure Global Desktop Platform Support and Release Notes for Release 5.2
Oracle® Secure Global Desktop Platform Support and Release Notes for Release 5.2 April 2015 E51729-03 Oracle Legal Notices Copyright © 2015, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -

Enterprise Computing with Oracle® Solaris for Dummies® Published by John Wiley & Sons, Inc
Enterprise Computing ® with Oracle Solaris by Lawrence C. Miller, CISSP These materials are the copyright of John Wiley & Sons, Inc. and any dissemination, distribution, or unauthorized use is strictly prohibited. Enterprise Computing with Oracle® Solaris For Dummies® Published by John Wiley & Sons, Inc. 111 River St. Hoboken, NJ 07030-5774 www.wiley.com Copyright © 2013 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without the prior written permission of the Publisher. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748-6008, or online at http://www.wiley.com/ go/permissions. Trademarks: Wiley, the Wiley logo, For Dummies, the Dummies Man logo, A Reference for the Rest of Us!, The Dummies Way, Dummies.com, Making Everything Easier, and related trade dress are trademarks or registered trademarks of John Wiley & Sons, Inc. and/or its affiliates in the United States and other countries, and may not be used without written permission. Oracle is a registered trademark of Oracle and/or its affiliates. All other trademarks are the property of their respec- tive owners. John Wiley & Sons, Inc., is not associated with any product or vendor mentioned in this book. LIMIT OF LIABILITY/DISCLAIMER OF WARRANTY: THE PUBLISHER AND THE AUTHOR MAKE NO REPRESENTATIONS OR WARRANTIES WITH RESPECT TO THE ACCURACY OR COMPLETE- NESS OF THE CONTENTS OF THIS WORK AND SPECIFICALLY DISCLAIM ALL WARRANTIES, INCLUDING WITHOUT LIMITATION WARRANTIES OF FITNESS FOR A PARTICULAR PURPOSE. -

Oracle Solaris and Oracle SPARC Systems—Integrated and Optimized for Mission Critical Computing
An Oracle White Paper September 2010 Oracle Solaris and Oracle SPARC Servers— Integrated and Optimized for Mission Critical Computing Oracle Solaris and Oracle SPARC Systems—Integrated and Optimized for Mission Critical Computing Executive Overview ............................................................................. 1 Introduction—Oracle Datacenter Integration ....................................... 1 Overview ............................................................................................. 3 The Oracle Solaris Ecosystem ........................................................ 3 SPARC Processors ......................................................................... 4 Architected for Reliability ..................................................................... 7 Oracle Solaris Predictive Self Healing ............................................ 7 Highly Reliable Memory Subsystems .............................................. 9 Oracle Solaris ZFS for Reliable Data ............................................ 10 Reliable Networking ...................................................................... 10 Oracle Solaris Cluster ................................................................... 11 Scalable Performance ....................................................................... 14 World Record Performance ........................................................... 16 Sun FlashFire Storage .................................................................. 19 Network Performance .................................................................. -

Oracle Solaris 11 Express What's
ORACLE SOLARIS 11 EXPRESS 2010.11 | WHAT’S NEW ORACLE SOLARIS 11 EXPRESS 2010.11 WHAT’S NEW Oracle Solaris is the industry leading operating system for the enterprise. Oracle Solaris 11 Express 2010.11 raises the bar on the innovation introduced in Oracle Solaris 10, with a unique feature set NEW FEATURE HIGHLIGHTS that few other operating systems can offer. Oracle Solaris 11 Express 2010.11 has been tested and • Oracle Solaris 10 Zones for business optimized for Oracle hardware and software, and is an integral part of Oracle's combined hardware investment protection and software portfolio. • Built-in network virtualization and resource Oracle Solaris 11 Express 2010.11 provides customers with the latest access to Oracle Solaris 11 management for enhanced server workload technology, allowing developers, architects and administrators to test and deploy within an consolidation enterprise environments and greatly simplify their day to day operations. Oracle Solaris 11 Express 2010.11 has the reliability, availability, and serviceability that you'd expect from a leading • Greatly reduced planned and unplanned downtime with new package management tools enterprise operating system. with safe system upgrade With new features such as network based package management tools to greatly decrease planned • New optimizations and features designed to system downtime and provide for a completely safe system upgrade, built-in network virtualization deliver proven scalability and reliability as an and resource control management for an unprecedented level of flexibility for application integrated component of Oracle's Exadata and consolidation, and on-disk ZFS encryption to provide the highest levels of security in your data Exalogic systems center, Oracle Solaris 11 Express 2010.11 is the most exciting release of the Oracle Solaris platform to date. -

Oracle Solaris 11.4 Data Sheet
Oracle Solaris is the trusted business platform that you depend on. Oracle Solaris 11 gives you consistent compatibility, is simple to use and is Key Features Consistent. Simple. Secure. designed to always be secure. • Strongest binary compatibility guarantee in INTRODUCTION the industry Oracle Solaris is designed to deliver a consistent platform to run your enterprise applications. It is the • Simple system and trusted solution for running both modern and legacy applications on the newest system hardware while application lifecycle providing the latest innovations. Our administrative interfaces are simple to use and protect your management business from error prone mistakes that could cost you critical downtime. All our technologies have been engineered for security and compliance from day one; allowing you to protect your business with • REST-based a comprehensive defense in depth strategy that’s easy to apply. administration and deployment CONSISTENT • Efficient enterprise virtualization We’ve been designing the OS for over two decades, always making sure we’ve engineered in features to meet the latest market trends while maintaining backward compatibility. Our Application Binary • Advanced data Guarantee gives you the ability to run your newest and legacy applications on modern infrastructure. management Binary Compatibility Guarantee • Simplified analysis with Observability Tools Oracle Solaris is designed and tested to protect your investment on-premises and in the cloud. The Oracle Solaris Binary Application Guarantee reflects Oracle’s confidence in the compatibility of • Remote administration applications from one release of Oracle Solaris to the next, so you can rest assured your applications will continue to run. The Oracle Solaris Source Code Guarantee assures developers that what they • Optimized for Oracle develop for Oracle SPARC will also compile and run on x86, and vice versa. -

Oracle® Solaris 11.3 Desktop User's Guide
® Oracle Solaris 11.3 Desktop User's Guide Part No: E54809 April 2020 Oracle Solaris 11.3 Desktop User's Guide Part No: E54809 Copyright © 2011, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. -
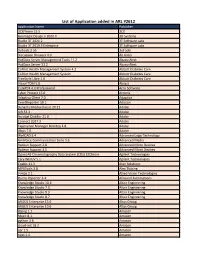
List of Application Added in ARL #2612
List of Application added in ARL #2612 Application Name Publisher 3CXPhone 15.5 3CX Geomagic Design X 2020.0 3D Systems Studio 3T 2021.2 3T Software Labs Studio 3T 2019.3 Enterprise 3T Software Labs 3uTools 2.55 3uTools Discussion Browser 4.0 Ab Initio HotDocs Server Management Tools 11.2 AbacusNext HotDocs Server 11.2 AbacusNext CoPilot Health Management System 4.2 Abbott Diabetes Care CoPilot Health Management System Abbott Diabetes Care FreeStyle Libre 1.0 Abbott Diabetes Care Visual TOM 5.8 Absyss CutePDF 4.0 Professional Acro Software Cyber Protect 15.0 Acronis Adaptiva Client 7.0 Adaptiva EventReporter 10.1 Adiscon Dynamic Media Classic 20.21 Adobe AIR 33.1 Adobe Acrobat Distiller 21.0 Adobe Connect 2021.3 Adobe Experience Manager Desktop 1.8 Adobe JBoss 7.0 Adobe WellCAD 5.4 Advanced Logic Technology AmiVoice Communication Suite 3.6 Advanced Media Radeon Support 2.8 Advanced Micro Devices Radeon Support 3.5 Advanced Micro Devices OpenLAB Chromatography Data System (CDS) EZChrom Agilent Technologies Cary WinUV 5.1 Agilent Technologies Coabis 11.3 Aker Solutions MP4Tools 3.8 Alex Thüring Vimba 2.1 Allied Vision Technologies Query Reporter 3.4 Allround Automations Knowledge Studio 10.4 Altair Engineering Knowledge Studio 7.0. Altair Engineering Knowledge Studio 9.3 Altair Engineering Knowledge Studio 8.7 Altair Engineering ARGUS Enterprise 13.0 Altus Group ARGUS Enterprise 10.6 Altus Group libpng 1.2 Amazon Music 8.1 Amazon python 3.6 Amazon cloud-init 18.2 Amazon apr 1.5 Amazon cups 1.4 Amazon java-1.7.0-openjdk 1.7 Amazon java-1.8.0-openjdk-devel -

The Rise & Development of Illumos
Fork Yeah! The Rise & Development of illumos Bryan Cantrill VP, Engineering [email protected] @bcantrill WTF is illumos? • An open source descendant of OpenSolaris • ...which itself was a branch of Solaris Nevada • ...which was the name of the release after Solaris 10 • ...and was open but is now closed • ...and is itself a descendant of Solaris 2.x • ...but it can all be called “SunOS 5.x” • ...but not “SunOS 4.x” — thatʼs different • Letʼs start at (or rather, near) the beginning... SunOS: A peopleʼs history • In the early 1990s, after a painful transition to Solaris, much of the SunOS 4.x engineering talent had left • Problems compounded by the adoption of an immature SCM, the Network Software Environment (NSE) • The engineers revolted: Larry McVoy developed a much simpler variant of NSE called NSElite (ancestor to git) • Using NSElite (and later, TeamWare), Roger Faulkner, Tim Marsland, Joe Kowalski and Jeff Bonwick led a sufficiently parallelized development effort to produce Solaris 2.3, “the first version that worked” • ...but with Solaris 2.4, management took over day-to- day operations of the release, and quality slipped again Solaris 2.5: Do or die • Solaris 2.5 absolutely had to get it right — Sun had new hardware, the UltraSPARC-I, that depended on it • To assure quality, the engineers “took over,” with Bonwick installed as the gatekeeper • Bonwick granted authority to “rip it out if itʼs broken" — an early BDFL model, and a template for later generations of engineering leadership • Solaris 2.5 shipped on schedule and at quality