Zack's Kernel News
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MLNX OFED Documentation Rev 5.0-2.1.8.0
MLNX_OFED Documentation Rev 5.0-2.1.8.0 Exported on May/21/2020 06:13 AM https://docs.mellanox.com/x/JLV-AQ Notice This document is provided for information purposes only and shall not be regarded as a warranty of a certain functionality, condition, or quality of a product. NVIDIA Corporation (“NVIDIA”) makes no representations or warranties, expressed or implied, as to the accuracy or completeness of the information contained in this document and assumes no responsibility for any errors contained herein. NVIDIA shall have no liability for the consequences or use of such information or for any infringement of patents or other rights of third parties that may result from its use. This document is not a commitment to develop, release, or deliver any Material (defined below), code, or functionality. NVIDIA reserves the right to make corrections, modifications, enhancements, improvements, and any other changes to this document, at any time without notice. Customer should obtain the latest relevant information before placing orders and should verify that such information is current and complete. NVIDIA products are sold subject to the NVIDIA standard terms and conditions of sale supplied at the time of order acknowledgement, unless otherwise agreed in an individual sales agreement signed by authorized representatives of NVIDIA and customer (“Terms of Sale”). NVIDIA hereby expressly objects to applying any customer general terms and conditions with regards to the purchase of the NVIDIA product referenced in this document. No contractual obligations are formed either directly or indirectly by this document. NVIDIA products are not designed, authorized, or warranted to be suitable for use in medical, military, aircraft, space, or life support equipment, nor in applications where failure or malfunction of the NVIDIA product can reasonably be expected to result in personal injury, death, or property or environmental damage. -

ECE 598 – Advanced Operating Systems Lecture 19
ECE 598 { Advanced Operating Systems Lecture 19 Vince Weaver http://web.eece.maine.edu/~vweaver [email protected] 7 April 2016 Announcements • Homework #7 was due • Homework #8 will be posted 1 Why use FAT over ext2? • FAT simpler, easy to code • FAT supported on all major OSes • ext2 faster, more robust filename and permissions 2 btrfs • B-tree fs (similar to a binary tree, but with pages full of leaves) • overwrite filesystem (overwite on modify) vs CoW • Copy on write. When write to a file, old data not overwritten. Since old data not over-written, crash recovery better Eventually old data garbage collected • Data in extents 3 • Copy-on-write • Forest of trees: { sub-volumes { extent-allocation { checksum tree { chunk device { reloc • On-line defragmentation • On-line volume growth 4 • Built-in RAID • Transparent compression • Snapshots • Checksums on data and meta-data • De-duplication • Cloning { can make an exact snapshot of file, copy-on- write different than link, different inodles but same blocks 5 Embedded • Designed to be small, simple, read-only? • romfs { 32 byte header (magic, size, checksum,name) { Repeating files (pointer to next [0 if none]), info, size, checksum, file name, file data • cramfs 6 ZFS Advanced OS from Sun/Oracle. Similar in idea to btrfs indirect still, not extent based? 7 ReFS Resilient FS, Microsoft's answer to brtfs and zfs 8 Networked File Systems • Allow a centralized file server to export a filesystem to multiple clients. • Provide file level access, not just raw blocks (NBD) • Clustered filesystems also exist, where multiple servers work in conjunction. -

Chapter 19 RECOVERING DIGITAL EVIDENCE from LINUX SYSTEMS
Chapter 19 RECOVERING DIGITAL EVIDENCE FROM LINUX SYSTEMS Philip Craiger Abstract As Linux-kernel-based operating systems proliferate there will be an in evitable increase in Linux systems that law enforcement agents must process in criminal investigations. The skills and expertise required to recover evidence from Microsoft-Windows-based systems do not neces sarily translate to Linux systems. This paper discusses digital forensic procedures for recovering evidence from Linux systems. In particular, it presents methods for identifying and recovering deleted files from disk and volatile memory, identifying notable and Trojan files, finding hidden files, and finding files with renamed extensions. All the procedures are accomplished using Linux command line utilities and require no special or commercial tools. Keywords: Digital evidence, Linux system forensics !• Introduction Linux systems will be increasingly encountered at crime scenes as Linux increases in popularity, particularly as the OS of choice for servers. The skills and expertise required to recover evidence from a Microsoft- Windows-based system, however, do not necessarily translate to the same tasks on a Linux system. For instance, the Microsoft NTFS, FAT, and Linux EXT2/3 file systems work differently enough that under standing one tells httle about how the other functions. In this paper we demonstrate digital forensics procedures for Linux systems using Linux command line utilities. The ability to gather evidence from a running system is particularly important as evidence in RAM may be lost if a forensics first responder does not prioritize the collection of live evidence. The forensic procedures discussed include methods for identifying and recovering deleted files from RAM and magnetic media, identifying no- 234 ADVANCES IN DIGITAL FORENSICS tables files and Trojans, and finding hidden files and renamed files (files with renamed extensions. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

Important Notice Regarding Software
Important Notice Regarding Software The software package installed in this product includes software licensed to Onkyo & Pioneer Corporation (hereinafter, called “O&P Corporation”) directly or indirectly by third party developers. Please be sure to read this notice regarding such software. Notice Regarding GNU GPL/LGPL-applicable Software This product includes the following software that is covered by GNU General Public License (hereinafter, called "GPL") or by GNU Lesser General Public License (hereinafter, called "LGPL"). O&P Corporation notifies you that, according to the attached GPL/LGPL, you have right to obtain, modify, and redistribute software source code for the listed software. ソフトウェアに関する重要なお知らせ 本製品に搭載されるソフトウェアには、オンキヨー & パイオニア株式会社(以下「弊社」とします)が 第三者より直接的に又は間接的に使用の許諾を受けたソフトウェアが含まれております。これらのソフト ウェアに関する本お知らせを必ずご一読くださいますようお願い申し上げます。 GNU GPL / LGPL 適用ソフトウェアに関するお知らせ 本製品には、以下の GNU General Public License(以下「GPL」とします)または GNU Lesser General Public License(以下「LGPL」とします)の適用を受けるソフトウェアが含まれております。 お客様は添付の GPL/LGPL に従いこれらのソフトウェアソースコードの入手、改変、再配布の権利があ ることをお知らせいたします。 Package List パッケージリスト alsa-conf-base glibc-gconv alsa-conf glibc-gconv-utf-16 alsa-lib glib-networking alsa-utils-alsactl gstreamer1.0-libav alsa-utils-alsamixer gstreamer1.0-plugins-bad-aiff alsa-utils-amixer gstreamer1.0-plugins-bad-bluez alsa-utils-aplay gstreamer1.0-plugins-bad-faac avahi-autoipd gstreamer1.0-plugins-bad-mms base-files gstreamer1.0-plugins-bad-mpegtsdemux base-passwd gstreamer1.0-plugins-bad-mpg123 bluez5 gstreamer1.0-plugins-bad-opus busybox gstreamer1.0-plugins-bad-rawparse -

MC-1200 Series Linux Software User's Manual
MC-1200 Series Linux Software User’s Manual Version 1.0, November 2020 www.moxa.com/product © 2020 Moxa Inc. All rights reserved. MC-1200 Series Linux Software User’s Manual The software described in this manual is furnished under a license agreement and may be used only in accordance with the terms of that agreement. Copyright Notice © 2020 Moxa Inc. All rights reserved. Trademarks The MOXA logo is a registered trademark of Moxa Inc. All other trademarks or registered marks in this manual belong to their respective manufacturers. Disclaimer Information in this document is subject to change without notice and does not represent a commitment on the part of Moxa. Moxa provides this document as is, without warranty of any kind, either expressed or implied, including, but not limited to, its particular purpose. Moxa reserves the right to make improvements and/or changes to this manual, or to the products and/or the programs described in this manual, at any time. Information provided in this manual is intended to be accurate and reliable. However, Moxa assumes no responsibility for its use, or for any infringements on the rights of third parties that may result from its use. This product might include unintentional technical or typographical errors. Changes are periodically made to the information herein to correct such errors, and these changes are incorporated into new editions of the publication. Technical Support Contact Information www.moxa.com/support Moxa Americas Moxa China (Shanghai office) Toll-free: 1-888-669-2872 Toll-free: 800-820-5036 Tel: +1-714-528-6777 Tel: +86-21-5258-9955 Fax: +1-714-528-6778 Fax: +86-21-5258-5505 Moxa Europe Moxa Asia-Pacific Tel: +49-89-3 70 03 99-0 Tel: +886-2-8919-1230 Fax: +49-89-3 70 03 99-99 Fax: +886-2-8919-1231 Moxa India Tel: +91-80-4172-9088 Fax: +91-80-4132-1045 Table of Contents 1. -

Developer Conference 2012 Schedule
Developer Conference 2012 Schedule Friday D1 D2 D3 Vlastimil Eliáš Jakub Hrozek, Jan Zeleny František Řezníček Centralized Identity Management 9:00 - 9:45 FreeIPA/SSSD + Intro to MIT Kerberos [Security] Towards Unified Messaging [CoreOS] And SSO for jboss.org Community Systems [JBoss] Alexander Bokovoy, Andreas Schneider Kamil Dudka, Ondřej Vašík Christian Sadilek 9:50 - 10:35 Cross-realm Trusts in FreeIPA v3.0 [Security] Common C/C++ Error Patterns & Static Analysis [CoreOS] JBoss Errai Framework [JBoss] Eduard Beneš, Miroslav Grepl Adam Tkáč Martin Kouba 10:40 - 11:25 SELinux News in Fedora 16 [Security] DNSSEC in Fedora 17 [CoreOS] CDI for Seam2 [JBoss] Dmitri Pal Marcela Maslanova, Jindrich Novy Peter Skopek 11:30 - 12:15 Identity Management Roadmap + MIT and Kerberos [Security] Dynamic Software Collections [CoreOS] PicketBox in AS7 [JBoss] Quick break Peter Vrabec Bryn Reeves Karel Piwko 12:30 - 13:15 Security Compliance Check in Fedora [Security] Supporting the Open Source Enterprise [Misc] Arquillian Drone Helping Ike Get Rid of the Bugs [JBoss] Jan Hutar Miloslav Trmac Software Robot Competition Around the World and Our Way Pavol Pitoňák 13:20 - 14:05 Concise Overview of Security [Security] [Misc, CZ] RichFaces: Testing on Mobile Devices [JBoss] Steve Grubb Stanislav Kozina Geoffrey De Smet 14:10 - 14:55 Government Security [Security] What Can Linux Learn from the Others [Misc] What Are Drools, Guvnor and Planner? [JBoss] Lennart Poettering, Kay Sievers Phil Knirsch Pavel Tisnovsky 15:00 - 15:45 Do's and Don'ts when Writing System -

Oracle® Linux 7 Managing File Systems
Oracle® Linux 7 Managing File Systems F32760-07 August 2021 Oracle Legal Notices Copyright © 2020, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Filesystem Considerations for Embedded Devices ELC2015 03/25/15
Filesystem considerations for embedded devices ELC2015 03/25/15 Tristan Lelong Senior embedded software engineer Filesystem considerations ABSTRACT The goal of this presentation is to answer a question asked by several customers: which filesystem should you use within your embedded design’s eMMC/SDCard? These storage devices use a standard block interface, compatible with traditional filesystems, but constraints are not those of desktop PC environments. EXT2/3/4, BTRFS, F2FS are the first of many solutions which come to mind, but how do they all compare? Typical queries include performance, longevity, tools availability, support, and power loss robustness. This presentation will not dive into implementation details but will instead summarize provided answers with the help of various figures and meaningful test results. 2 TABLE OF CONTENTS 1. Introduction 2. Block devices 3. Available filesystems 4. Performances 5. Tools 6. Reliability 7. Conclusion Filesystem considerations ABOUT THE AUTHOR • Tristan Lelong • Embedded software engineer @ Adeneo Embedded • French, living in the Pacific northwest • Embedded software, free software, and Linux kernel enthusiast. 4 Introduction Filesystem considerations Introduction INTRODUCTION More and more embedded designs rely on smart memory chips rather than bare NAND or NOR. This presentation will start by describing: • Some context to help understand the differences between NAND and MMC • Some typical requirements found in embedded devices designs • Potential filesystems to use on MMC devices 6 Filesystem considerations Introduction INTRODUCTION Focus will then move to block filesystems. How they are supported, what feature do they advertise. To help understand how they compare, we will present some benchmarks and comparisons regarding: • Tools • Reliability • Performances 7 Block devices Filesystem considerations Block devices MMC, EMMC, SD CARD Vocabulary: • MMC: MultiMediaCard is a memory card unveiled in 1997 by SanDisk and Siemens based on NAND flash memory. -

The Linux Kernel Past, Present and Future - the Linux Way
The Linux kernel Past, Present and Future - the Linux way Muli Ben-Yehuda [email protected] IBM Haifa Research Labs The Linux Kernel - HRL 2003 – p.1/21 The Linux Kernel linux is a free (speech and beer) UNIX like operating system, developed by thousands of volunteers around the world - including yours truly started as a hobby, grew and matured with the years countless man years went into it, some paid, some for fun one of the leading server operating systems today . and one of the leading embedded operating systems poised to take over the desktop? Hebrew support? The Linux Kernel - HRL 2003 – p.2/21 The beginning From: [email protected] (Linus Benedict Torvalds) Date: 25 Aug 91 20:57:08 GMT Hello everybody out there using minix - I'm doing a (free) operating system (just a hobby, won't be big and professional like gnu) for 386(486) AT clones. This has been brewing since april, and is starting to get ready. I'd like any feedback on things people like/dislike in minix, as my OS resembles it somewhat (same physical layout of the file-system (due to practical reasons) among other things). I've currently ported bash(1.08) and gcc(1.40), and things seem to work.This implies that I'll get something practical within a few months, andI'd like to know what features most people would want. Any suggestions are welcome, but I won't promise I'll implement them :-) Linus ([email protected]) PS. Yes - it's free of any minix code, and it has a multi-threaded fs. -

Beyond Init: Systemd Linux Plumbers Conference 2010
Beyond Init: systemd Linux Plumbers Conference 2010 Kay Sievers Lennart Poettering November 2010 Kay Sievers, Lennart Poettering Beyond Init: systemd Triggers: Boot, Socket, Bus, Device, Path, Timers, More Kay Sievers, Lennart Poettering Beyond Init: systemd Kay Sievers, Lennart Poettering Beyond Init: systemd Substantial coverage of basic OS boot-up tasks, including fsck, mount, quota, hwclock, readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. Status: almost made Fedora 14. Kay Sievers, Lennart Poettering Beyond Init: systemd including fsck, mount, quota, hwclock, readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. Status: almost made Fedora 14. Substantial coverage of basic OS boot-up tasks, Kay Sievers, Lennart Poettering Beyond Init: systemd mount, quota, hwclock, readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. Status: almost made Fedora 14. Substantial coverage of basic OS boot-up tasks, including fsck, Kay Sievers, Lennart Poettering Beyond Init: systemd quota, hwclock, readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. Status: almost made Fedora 14. Substantial coverage of basic OS boot-up tasks, including fsck, mount, Kay Sievers, Lennart Poettering Beyond Init: systemd hwclock, readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. Status: almost made Fedora 14. Substantial coverage of basic OS boot-up tasks, including fsck, mount, quota, Kay Sievers, Lennart Poettering Beyond Init: systemd readahead, tmpfiles, random-seed, console, static module loading, early syslog, plymouth, shutdown, kexec, SELinux, initrd+initrd-less boots. -
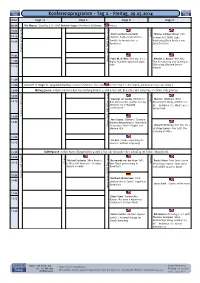
Konferenzprogramm - Tag 2 - Freitag, 09.05.2014 Time Stage 12 Stage C Stage D Stage E 09:30 Nils Magnus (Linuxtag E
Konferenzprogramm - Tag 2 - Freitag, 09.05.2014 Time Stage 12 Stage C Stage D Stage E 09:30 Nils Magnus (LinuxTag e. V.) und Heinrich Seeger (droidcon): Eröffnung Freitag l 4 n e i 10:00 1 g n 0 r g 2 e Martin Gerhard Loschwitz Thomas Schöbel-Theuer (1&1 o K L y 10:15 a (hastexo Professional Services Internet AG): MARS Light: d D n GmbH): An Introduction to Replicating Block Devices over a 10:30 H C g OpenStack Long Distances A n i D c a k r c T a t S 10:45 n e p Fabio M. Di Nitto (Red Hat, Inc.): Alasdair G. Kergon (Red Hat): 11:00 O Highly Available OpenStack done Thin Provisioning and Caching on 11:15 right SSDs using LVM and Device- mapper 11:30 12:00 Keynote in Stage 11: Greg Kroah-Hartman (Linux Foundation): The Linux kernel, how it is developed, and how we stay sane doing it 13:00 Mittagspause in Buffetform in den Ausstellungshallen 4 und 6 (für alle Besucher des LinuxTag im Ticket inbegriffen). l 4 n e i 14:00 1 g n 0 r g 2 e Giuseppe de Candia (Midokura) Thorsten Leemhuis (Heise : o K L y 14:15 a How Linux kernel enables overlay Zeitschriften Verlag GmbH & Co. d D n networks for virtualized KG -- Redaktion c't): What's up in a H C environments g Kernel land A n i D c a k r c T 14:30 a t S Yves Fauser (VMware): Software- 14:45 n e Defined Networking for OpenStack p Lennart Poettering (Red Hat, Inc.) O using Open Source Plugins and VMware NSX und Kay Sievers (Red Hat): The anatomy of kdbus 15:00 Tim Bell (CERN): Expanding the 15:15 universe without a Big Bang 15:30 Kaffeepause in den Ausstellungshallen 4 und 6 (für alle Besucher des LinuxTag im Ticket inbegriffen).