A Criminological Analysis of Copper Cable Theft in Gauteng
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

All Animals Are Equal but Some Are More Equal Than Others
ALL ANIMALS ARE EQUAL BUT SOME ARE MORE EQUAL THAN OTHERS George Orwell’s novel “Animal Farm” gave birth to the oft-repeated affirmation that equality is an admirable aspiration but that it is virtually unattainable. Some are more equal than others, it was implied. Equality before the law as enshrined in the South African constitution is rarely achieved when a political or racial component is involved. Under the ANC these aspects take on a trajectory of their own and justice is often the victim of the political clash of civilizations that is acted out every day in post-apartheid South Africa. For the past 27 years of ANC rule, hundreds of thousands of criminals have systematically plundered South Africa’s infrastructure with malice and purpose. No definitive action to curb this anarchy has emanated from government. We have been occasionally told that “several arrests have been made” and then we hear nothing more. Thousands if not millions of miscreants never reached the courts, let alone became the subject of a police docket. If a suspect actually did appear in court, there was little if any media flurry surrounding the person’s appearance. Many of these cases simply died on the altar of the government’s justice system’s bias, ineptitude and/or negligence. Compare this scenario to the recent rumpus at a Senekal, Free State court where a group of farmers gathered to express their rage and frustration at yet another gruesome farm murder. A young farm manager Brendin Horner (22) was attacked by a group of cattle thieves, beaten to a pulp, stabbed repeatedly and his body was tied to a fence pole. -

EASTERN CAPE NARL 2014 (Approved by the Federal Executive)
EASTERN CAPE NARL 2014 (Approved by the Federal Executive) Rank Name 1 Andrew (Andrew Whitfield) 2 Nosimo (Nosimo Balindlela) 3 Kevin (Kevin Mileham) 4 Terri Stander 5 Annette Steyn 6 Annette (Annette Lovemore) 7 Confidential Candidate 8 Yusuf (Yusuf Cassim) 9 Malcolm (Malcolm Figg) 10 Elza (Elizabeth van Lingen) 11 Gustav (Gustav Rautenbach) 12 Ntombenhle (Rulumeni Ntombenhle) 13 Petrus (Petrus Johannes de WET) 14 Bobby Cekisani 15 Advocate Tlali ( Phoka Tlali) EASTERN CAPE PLEG 2014 (Approved by the Federal Executive) Rank Name 1 Athol (Roland Trollip) 2 Vesh (Veliswa Mvenya) 3 Bobby (Robert Stevenson) 4 Edmund (Peter Edmund Van Vuuren) 5 Vicky (Vicky Knoetze) 6 Ross (Ross Purdon) 7 Lionel (Lionel Lindoor) 8 Kobus (Jacobus Petrus Johhanes Botha) 9 Celeste (Celeste Barker) 10 Dorah (Dorah Nokonwaba Matikinca) 11 Karen (Karen Smith) 12 Dacre (Dacre Haddon) 13 John (John Cupido) 14 Goniwe (Thabisa Goniwe Mafanya) 15 Rene (Rene Oosthuizen) 16 Marshall (Marshall Von Buchenroder) 17 Renaldo (Renaldo Gouws) 18 Bev (Beverley-Anne Wood) 19 Danny (Daniel Benson) 20 Zuko (Prince-Phillip Zuko Mandile) 21 Penny (Penelope Phillipa Naidoo) FREE STATE NARL 2014 (as approved by the Federal Executive) Rank Name 1 Patricia (Semakaleng Patricia Kopane) 2 Annelie Lotriet 3 Werner (Werner Horn) 4 David (David Christie Ross) 5 Nomsa (Nomsa Innocencia Tarabella Marchesi) 6 George (George Michalakis) 7 Thobeka (Veronica Ndlebe-September) 8 Darryl (Darryl Worth) 9 Hardie (Benhardus Jacobus Viviers) 10 Sandra (Sandra Botha) 11 CJ (Christian Steyl) 12 Johan (Johannes -

African National Congress NATIONAL to NATIONAL LIST 1. ZUMA Jacob
African National Congress NATIONAL TO NATIONAL LIST 1. ZUMA Jacob Gedleyihlekisa 2. MOTLANTHE Kgalema Petrus 3. MBETE Baleka 4. MANUEL Trevor Andrew 5. MANDELA Nomzamo Winfred 6. DLAMINI-ZUMA Nkosazana 7. RADEBE Jeffery Thamsanqa 8. SISULU Lindiwe Noceba 9. NZIMANDE Bonginkosi Emmanuel 10. PANDOR Grace Naledi Mandisa 11. MBALULA Fikile April 12. NQAKULA Nosiviwe Noluthando 13. SKWEYIYA Zola Sidney Themba 14. ROUTLEDGE Nozizwe Charlotte 15. MTHETHWA Nkosinathi 16. DLAMINI Bathabile Olive 17. JORDAN Zweledinga Pallo 18. MOTSHEKGA Matsie Angelina 19. GIGABA Knowledge Malusi Nkanyezi 20. HOGAN Barbara Anne 21. SHICEKA Sicelo 22. MFEKETO Nomaindiya Cathleen 23. MAKHENKESI Makhenkesi Arnold 24. TSHABALALA- MSIMANG Mantombazana Edmie 25. RAMATHLODI Ngoako Abel 26. MABUDAFHASI Thizwilondi Rejoyce 27. GODOGWANA Enoch 28. HENDRICKS Lindiwe 29. CHARLES Nqakula 30. SHABANGU Susan 31. SEXWALE Tokyo Mosima Gabriel 32. XINGWANA Lulama Marytheresa 33. NYANDA Siphiwe 34. SONJICA Buyelwa Patience 35. NDEBELE Joel Sibusiso 36. YENGENI Lumka Elizabeth 37. CRONIN Jeremy Patrick 38. NKOANA- MASHABANE Maite Emily 39. SISULU Max Vuyisile 40. VAN DER MERWE Susan Comber 41. HOLOMISA Sango Patekile 42. PETERS Elizabeth Dipuo 43. MOTSHEKGA Mathole Serofo 44. ZULU Lindiwe Daphne 45. CHABANE Ohm Collins 46. SIBIYA Noluthando Agatha 47. HANEKOM Derek Andre` 48. BOGOPANE-ZULU Hendrietta Ipeleng 49. MPAHLWA Mandisi Bongani Mabuto 50. TOBIAS Thandi Vivian 51. MOTSOALEDI Pakishe Aaron 52. MOLEWA Bomo Edana Edith 53. PHAAHLA Matume Joseph 54. PULE Dina Deliwe 55. MDLADLANA Membathisi Mphumzi Shepherd 56. DLULANE Beauty Nomvuzo 57. MANAMELA Kgwaridi Buti 58. MOLOI-MOROPA Joyce Clementine 59. EBRAHIM Ebrahim Ismail 60. MAHLANGU-NKABINDE Gwendoline Lindiwe 61. NJIKELANA Sisa James 62. HAJAIJ Fatima 63. -
5 Framework 5 Framework
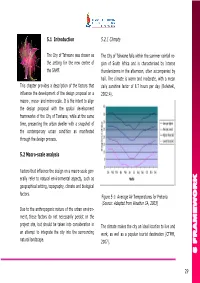
5.1 Introduction 5.2.1 Climate The City of Tshwane was chosen as The City of Tshwane falls within the summer rainfall re- the setting for the new centre of gion of South Africa and is characterised by intense the SAMF. thunderstorms in the afternoon, often accompanied by hail. The climate is warm and moderate, with a mean This chapter provides a description of the factors that daily sunshine factor of 8.7 hours per day (Bolwheki, influence the development of the design proposal on a 2002:4). macro-, meso- and micro-scale. It is the intent to align the design proposal with the spatial development frameworks of the City of Tswhane, while at the same time, presenting the urban dweller with a snapshot of the contemporary urban condition as manifested through the design process. 5.2 Macro-scale analysis Factors that influence the design on a macro-scale gen- erally refer to natural environmental aspects, such as geographical setting, topography, climate and biological factors. Figure 5-1: Average Air Temperatures for Pretoria (Source: Adapted from Weather SA, 2003) Due to the anthropogenic nature of the urban environ- ment, these factors do not necessarily persist on the project site, but should be taken into consideration in The climate makes the city an ideal location to live and an attempt to integrate the city into the surrounding work, as well as a popular tourist destination (CTMM, natural landscape. 2007). 5 FRAMEWORK 5 FRAMEWORK 29 Table 5-1: Climate of City of Tswhane, 1961 – 1990 (Source: Weather SA, 2003) Temperature (° C) Precipitation -

Annual Report 2015/2016
SOUTH AFRICAN POLICE SERVICE: VOTE 23 ANNUAL REPORT 2015/2016 ANNUAL REPORT 2015/16 SOUTH AFRICAN POLICE SERVICE VOTE 23 2015/16 ANNUAL REPORT REPORT ANNUAL www.saps.gov.za BACK TO BASICS TOWARDS A SAFER TOMORROW #CrimeMustFall A SOUTH AFRICAN POLICE SERVICE: VOTE 23 ANNUAL REPORT 2015/2016 B SOUTH AFRICAN POLICE SERVICE: VOTE 23 ANNUAL REPORT 2015/2016 Compiled by: SAPS Strategic Management Layout and Design: SAPS Corporate Communication Corporate Identity and Design Photographs: SAPS Corporate Communication Language Editing: SAPS Corporate Communication Further information on the Annual Report for the South African Police Service for 2015/2016 may be obtained from: SAPS Strategic Management (Head Office) Telephone: 012 393 3082 RP Number: RP188/2016 ISBN Number: 978-0-621-44668-5 i SOUTH AFRICAN POLICE SERVICE: VOTE 23 ANNUAL REPORT 2015/2016 SUBMISSION OF THE ANNUAL REPORT TO THE MINISTER OF POLICE Mr NPT Nhleko MINISTER OF POLICE I have the honour of submitting the Annual Report of the Department of Police for the period 1 April 2015 to 31 March 2016. LIEUTENANT GENERAL JK PHAHLANE Date: 31 August 2016 ii SOUTH AFRICAN POLICE SERVICE: VOTE 23 ANNUAL REPORT 2015/2016 CONTENTS PART A: GENERAL INFORMATION 1. GENERAL INFORMATION OF THE DEPARTMENT 1 2. LIST OF ABBREVIATIONS/ACRONYMS 2 3. FOREWORD BY THE MINISTER 7 4. DEPUTY MINISTER’S STATEMENT 10 5. REPORT OF THE ACCOUNTING OFFICER 13 6. STATEMENT OF RESPONSIBILITY AND CONFIRMATION OF ACCURACY FOR THE ANNUAL REPORT 24 7. STRATEGIC OVERVIEW 25 7.1 VISION 25 7.2 MISSION 25 7.3 VALUES 25 7.4 CODE OF CONDUCT 25 8. -

TSH City of Tshwane Draft BEPP 2015-16
BUILT ENVIRONMENT PERFORMANCE PLAN (BEPP) 2015/16 First Draft November 2014 City Planning and Development Department 0 TABLE OF CONTENTS A INTRODUCTION AND BACKGROUND 2 LIST OF REFERENCE DOCUMENTS 3 B STRATEGIC REVIEW OF THE BUILT ENVIRONMENT 4 B1 CURRENT PERFORMANCE OF THE BUILT ENVIRONMENT 4 B2 ECONOMIC INFRASTRUCTURE 21 B3 BASIC INFRASTRUCTURE REVIEW 39 B4 RESIDENTIAL INFRASTRUCTURE REVIEW 73 B5 COMMUNITY INFRASTRUCTURE REVIEW 154 B6 TRANSPORTATION REVIEW 161 B7 SUSTAINABLE DEVELOPMENT REVIEW 176 B8 IMPACT OF SECTOR REVIEWS ON SPATIAL FORM 181 C STRATEGIES AND PROGRAMMES 181 C1 LONG TERM VISION 181 C2 THE SPATIAL DEVELOPMENT STRATEGY OF THE MUNICIPALITY 186 C3 OVERVIEW OF AREA-BASED INITIATIVES INCLUDING CATALYTIC PROJECTS 193 C4 IDENTIFICATION OF URBAN NETWORK, INTEGRATION ZONES AND HUBS 225 D OUTCOMES AND OUTPUTS 229 E INSTITUTIONAL AND FINANCIAL ARRANGMENTS 229 1 INTRODUCTION The City of Tshwane Draft BEPP 2015/2016 dated 03 November 2014 is submitted in line with the BEPP Guidance Note 2015/16-2017/18. It is hereby submitted that in terms of the Council Approved IDP Process Plan 2015/2016, a comprehensive BEPP 2015/2016 will be submitted once the draft Capital Budget has been finalised in January 2015. The Final Draft will be submitted together with the Draft IDP and Capex 15_16 to the Mayoral Committee during the period March-May 2015. This submission provides the city’s in context approach towards spatial targeting with primary focus on the movement system as the key spatial restructuring element of the built environment. Other built environment restructuring components will be incorporated in the next submission. -

Window to the Soul of Africa… Journey of a Lifetime
Window to the Soul of Africa… Journey of a lifetime Pretoria to Cape Town Route Description The Blue Train’s most popular route is between Pretoria and Cape Town (in either direction) – a 1,600 kilometres (994 miles) journey through some of South Africa’s most diverse and spectacular scenery – a “window to the soul of Africa”. If heading southbound, the adventure starts in Pretoria which is a 30-mile drive away from Johannesburg’s O.R. Tambo International Airport. Pretoria is one of South Africa’s three capital cities (legislative capital) and is affectionately known as the “Jacaranda city” thanks to the beautiful streets lined with purple flowers between September and November. This is usually when local university students write exams and it’s a local belief that if a flower falls on your head it’s good luck. The union buildings, built in 1913, are South Africa’s official seat of power and it’s where all new presidents, including Nelson Mandela in 1994, are sworn into office. The 9m high bronze statue of Madiba in the gardens is the tallest statue of Mandela in the world and a very popular “selfie” spot. The statue of him opening his arms to embrace the Rainbow Nation was unveiled on the Day of Reconciliation (16 December), bringing the official 10-day mourning period of Mandela’s death to a close in 2013. Other tourist spots include the National Zoological Gardens, Church Square, Freedom Park Heritage Site and Museum, the Botanical gardens and many historical sites and museums. Blue Train guests tend to spend the night before travel in either Pretoria or Johannesburg but thanks to the new 2019 late afternoon departure time, a night is Gauteng is not essential, unless you wish to explore this buzzing city. -

I I I I I I I I I I I I I I I
I I SUPPLEMENTARY VOLUME 2 OF THE ADDENDUM TO THE DRAFT I ENVIRONMENTAL IMPACT ASSESSMENT REPORT FOR THE PROPOSED GAUTRAIN RAPID RAIL LINK BETWEEN JOHANNESBURG, PRETORIA AND JOHANNESBURG I INTERNATIONAL AIRPORT I I HERITAGE IMPACT ASSESSMENT I OF THE I RECOMMENDED ROUTE ALIGNMENT I FOR THE PROPOSED I GAUTRAIN RAPID RAIL LINK PROJECT I I Final Report Dr Johann Bruwer I William Martinson Mauritz Naude Henry Paine I Hannes Raath I April 2003 I on behalf of Bohlweki Environmental (Pty) Ltd PO Box 11784 I Vorna Valley 1686 Telephone : (011) 805-0250 I Fax (011) 805-0226 Email: [email protected] I Web Site: www.bohlweki.co.za 1- I I I I I I I I I I I I I I I ~. ~ I / 1 rary. I Acccsrion No. ~O..a.~ ....0. .!e.~ ....... ,1 7 I :' _·: ,.. ,~ ?.:?.}:.7.2 .. $.:€:.':::' ......... ._j ~ ---· . --- - .. --- --- I I r I 1111,111111111111111111111,1111111111111111111 2006 0620 I SA Heritage Resources Agency library CONTENTS I PAGE 1. INTRODUCTION AND TERMS OF REFERENCE 1 2. I AIM OF THE STUDY 2 3. I STUDY AREA 2 4. I ZONING OF THE STUDY AREA 3 5. ASSUMPTIONS, CONDITIONS AND METHODOLOGY 3 I 5.1 Terminology and relevant provisions of the NHRA 3 5.2 I Assessment of culturally significant places 4 5.3 Evaluation of the impact of the proposed route alignment on 5 I heritage resources 5.4 Application of the Burra Charter 7 I 5.5 Categories of investigation and sources of information 8 5.6 Limiting factors I 9 5.7 I Structure of the report 10 6. -

Faheema Bava
DEMOCRATIC ALLIANCE SHADOW CABINET – OCTOBER 2015 Portfolio Shadow Minister Shadow Deputy Minister Additional Member Agriculture, Forestry & ANETTE STEYN ZELDA JONGBLOED Fisheries 082 323 0027 081 532 5979 Arts & Culture WINSTON RABOTAPI ALLEN GROOTBOOM DR 082 464 2651 076 886 8262 Basic Education GAVIN DAVIS DESIREE VAN DER WALT SONJA BOSHOFF 082 528 7903 082 452 0444 082 429 0280 Communications PHUMZILE VAN DAMME VERONICA VAN DYK 074 462 1279 083 236 2152 Co-operative Governance & KEVIN MILEHAM NQABA BHANGA DAVID MATSEPE Traditional Affairs 083 463 8858 071 410 0902 071 330 2955 Defence & Military Veterans KOBUS MARAIS SHAHID ESAU 084 448 3838 082 704 5378 Economic Development MICHAEL CARDO DR PATRICK ATKINSON 082 323 9296 083 445 2059 Energy GORDON MACKAY PIETER VAN DALEN 060 507 2009 083 655 2203 Environmental Affairs THOMAS HADEBE JóHNI EDWARDS 081 357 7153 082 568 3044 Finance DAVID MAYNIER ALF LEES MALCOLM FIGG DR 071 534 6398 082 806 4340 084 581 5584 Appropriations MALCOLM FIGG DR ALAN MCLOUGHLIN ‘084 581 5584 ‘060 525 8977 Health WILMOT JAMES DR HEINRICH VOLMINK DR LUNGISWA JAMES 082 824 8879 082 458 6867 083 398 5371 Higher Education & Training BELINDA BOZZOLI PROF YUSUF CASSIM 082 802 5110 083 788 5088/ 073 422 5662 Home Affairs HANIFF HOOSEN ARCHIBOLD FIGLAN 072 206 5273 071 678 9675 Human Settlements MAKASHULE GANA TANDEKA GQADA TARNIA BAKER 082 773 4755 083 349 9184 076 521 2711 International Relations & Co- STEVENS MOKGALAPA SANDY KALYAN operations 083 275 1779 082 578 5207 Justice & Correctional Services GLYNNIS BREYTENBAC -

Democratic Alliance Candidates' Lists 2009
DEMOCRATIC ALLIANCE CANDIDATES’ LISTS 2009 ELECTION EASTERN CAPE NATIONAL ASSEMBLY LIST 1. Athol Trollip 2. Annette Lovemore 3. Donald Lee 4. Stuart Farrow 5. Donald Smiles 6. Annette Steyn 7. Elza van Lingen 8. Peter van Vuuren 9. Gustav Rautenbach 10. Kevin Mileham PROVINCIAL LEGISLATURE LIST 1. Athol Trollip 2. Bobby Stevenson 3. Veliswa Mvenya 4. John Cupido 5. Pine Pienaar 6. Dacre Haddon 7. Peter Van Vuuren 8. Kevin Mileham 9. Isaac Adams 10. Mzimkhulu Xesha FREE STATE NATIONAL ASSEMBLY LIST 1. Cobus Schmidt 2. Semakaleng Patricia Kopane 3. Theo Coetzee 4. Annelie Lotriet 5. Darryl Worth 6. David Ross 7. Ruloph Van der Merwe 8. Helena Hageman 9. Kingsley Ditabe PROVINCIAL LEGISLATURE LIST 1. Roy Jankielsohn 2. Peter Frewen 3. Basil Alexander 4. David Janse van Vuuren 5. Henk van der Walt 6. David Ross 7. Nicolene du Toit 8. Tseko Mpakate GAUTENG NATIONAL ASSEMBLY LIST 1. Ian Davidson 2. Sej Motau 3. Butch Steyn 4. Natasha Michael 5. Niekie Van der Berg 6. Anthea Jeffrey 7. Kenneth Mubu 8. Manny de Freitas 9. Mike Waters 10. Stevens Mokgalapa 11. James Lorimer 12. Ian Ollis 13. Marti Wenger 14. Juanita Kloppers-Lourens 15. Anchen Dreyer 16. Dion George 17. Manie van Dyk 18. Hendrik Schmidt 19. Emmah More 20. George Boinamo 21. Justus de Goede 22. Rika Kruger 23. Sherry Chen 24. Anthony Still 25. Shelley Loe 26. Kevin Wax 27. James Swart 28. Bev Abrahams 29. Don Forbes 30. Jan Boshoff 31. Wildri Peach 32. Danie Erasmus 33. Frank Van der Tas 34. Johan Jordaan 35. Cilicia Augustine 36. -

PROVINCIAL LIST Eastern Cape 1. Roland Athol Price Trollip 2
PROVINCIAL LIST Eastern Cape 1. Roland Athol Price Trollip 2. Veliswa Mvenya 3. Robert Sykes Stevenson 4. Peter Edmund Van Vuuren 5. Vicky Knoetze 6. Ross Kriel Purdon 7. Marshall Roberto Von Buchenroder Jacobus Petrus 8. Botha Johannes 9. Celeste Heloise Barker 10. Dorah Nokonwaba Matikinca 11. Karen Smith 12. Dacre Berrange Haddon 13. John Cristiano Cupido 14. Thabisa Goniwe Mafanya 15. Renaldo Gouws 16. Beverley-Anne Frieda Wood 17. Danny Benson 18. Penelope Phillipa Naidoo 19. Chris Tembalihle Xangayi Mbongeni Praisehim 20. Kotana Jackson Derrick Velile 21. Madini Livingstone 22. Gideon Daniel Wagenaar 23. Nico du Plessis 24. Jonathan Lawack 25. Andy George Jordan 26. Cecilia Reeders 27. Mandisa Lydia Tyholo 28. Kenneth Charles Biggs 29. Cecilia Anne Auld 30. Brenton John Williams 31. Eugene Andre Goliath 32. Hendrik Booysen 33. Marelese Van Rensburg 34. Werner Senekal 35. Sharne Muriel Jacobs 36. Elia Robin Jantjies 37. Christina Magdalena Botha 38. Lulamo Pili 39. Sandra Fillis 40. Brian Desmond Kivedo 41. Carike Wiese 42. Thobani Sebastian Noqoli 43. Vianca Swart 44. Masizakhe Fullman 45. Lucilla Loletta Mazwati 46. Brian William Fargher 47. Priscilla Ntombekhaya Mahlathi 48. Leslie Michael Reynolds 49. Sydney Peter Smith 50. Andrew Grant Whitfield 51. Chris Hattingh Bornman 52. Morne Steyn 53. David Alan Hayselden 54. Nicola Cathleen Montgomery 55. Louisa Stella Cilliers 56. Ingrid Leslie Van Wyk 57. Rene Meyer 58. Nomonde Veronica Mazantsi 59. Cathrine Willemse 60. Bianca Jeni Steyn 61. Franz Alexander Du Plessis 62. Taswell Theo Solomons 63. Hazel Nasiphi Moyo Free State 1. Semakaleng Patricia Kopane 2. Roy Jankielsohn 3. David Edward Janse Van Vuuren 4. -

Ÿþm Icrosoft W
inSA9 inSA9 ov 0 1% V oAce 7 Nv Datp3 Arow'. break, lip 0-so, GOVERNMENT CREATED POLITICAL BODIES Bantustans THE BANTUSTAN POLICY, perhaps sooner than has always been anticipated by its black opponents in South Africa and abroad, began to crystallise in 1974. In 1974 and 1975 certain developments can be singled out which had the profound effect of making the Bantustan policy sound more accomplished:there was more definite planning with the Transkei for the "independence" of that territory; there were new developments regarding South Africa at the United Nations. the South African Foreign Affairs Department developed a much more outgoing diplomatic African policy. By and large these events have given rise to intense debate and speculation in South Africa about the course of events over the next few years. On the one hand protagonists of the Bantustan policy are capitalising on the "gains" and claim that with more time their policy will be seen to be working. On the other hand those who are opposed to the Bantustan policy argue that the so-called gains are gimmicks calculated to buy more time for the South African Government which is being overtaken by events in nearby countries. The Transkei Independence Question The announcement of independence plans for 1976 by the Transkei's Chief Matanzima had three immediate results. The first was the disturbance of the fraternity of Bantustan leaders whose agreed strategy had been to reject independence until the Government was prepared to grant more land to the homelands and that no individual Bantustan leader would bargain alone with Pretoria without consulting the others.