Chapter 0 Introduction to Tcp/Ip
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Networking: Network Layer
CS 4410 Operating Systems Networking: Network Layer Summer 2013 Cornell University 1 Today ● How packages are exchanged in a WAN? ● Network Layer ● IP ● Naming ● Subnetwork ● Forwarding ● Routing Algorithms 2 Protocol Stack Computer A Computer B Message M Application Application Segment Ht M Transport Transport Datagram Hn Ht M Network Network Frame Hl Hn Ht M Link Link Physical Physical 3 WAN ● Usually, thousands of computers need to be interconnected. ● The capabilities that LANs offer cannot support larger networks. ● We need more services than the Link Layer offers. ● Why? ● Clever Naming ● Efficient forwarding/routing of messages. 4 Network Layer ● Mission: Transfer messages from the source-computer to the destination- computer. ● Attention: this is different from the mission of the Link Layer. ● Services: ● Forwarding / Routing ● Guaranteed delivery, bandwidth, etc ● Security ● Not all the protocols support these services. ● The Network Layer protocol depends on the kind of network we want to built: ● Virtual-circuit networks ● Datagram networks ● Necessary network device: ● Router: It knows where to forward the message. 5 Network Layer ● Virtual-circuit networks ● 3 phases ● Establish a virtual circuit. – The Network Layer finds the path from the source to the destination. – Reserve resources for the virtual circuit. ● Transfer data – Packets pass through the virtual circuit. ● Destroy virtual circuit. – Release resources. ● Disadvantages? ● Datagram networks ● Every packet has the destination address and it is routed independently in the network. ● The router uses the destination address to forward the packet towards 6 the destination-computer. IP ● Network Layer Protocol for the Internet: ● Internet Protocol ● For Datagram networks. ● IPv4, IPv6 ● Datagram structure: Version Header Type of Length Length service Identification Flags Fragment Offset Time to live Protocol Header Checksum Source IP Address (32-bit) Destination IP Address Options Data 7 Naming ● All the computers in the Internet have one or more IP addresses. -

Rudiments of Routing
Rudiments of Routing Moving bits from the source to the destination is a major function of computer networking. On the current Internet, the Network layer is responsible for achieving this. AS 2 AS 1 Inter-domain routing OSPF and RIP Inter-domain routing OSPF and RIP Intra-domain routing BGP In general, most routing within Autonomous Systems use Routing Information Protocol (RIP), or its enhanced version Open Shortest Path First (OSPF). The current de facto Intra-domain routing standard is Border Gateway Protocol(BGP), Version 4. You need to concern yourself with these protocols if you are dealing with routers inside or between Autonomous Systems. At the host level, however, most likely you need only a static routing table. This is a table of routes that the OS kernel keeps. It is possible to add to and delete from routes in the kernel routing table relatively easily. We discuss routing tables based on RIP (RFC2453). When looking at routing tables, remember that most Unix-like operating systems use mnemonic names for their interfaces. For example, in Linux, the Ethernet interfaces on a machine are called eth0, eth1, eth2, etc. On the newer SUN/Solaris machines the interfaces are named eri0, eri1, etc. PPP interfaces are usually names ppp0, ppp1 etc. You can see all the configured interfaces on a host using the ifconfig command which is usually found in /sbin/ directory (but not always). You can see the routing table with ªnetstat -rº command. Here©s a screen shot of these commands run on matrix.newpaltz.edu which is a SUN/Solaris machine: The output from /sbin/ifconfig command shows that there are two configured interfaces, one an Ethernet and the other the loopback interface. -

Internet Routing Over Large Public Data Networks Using Shortcuts
Internet Routing over Large Public Data Networks using Shortcuts Paul F, Tsuchiya, Bellcore, [email protected] When a system (a router or host) needs to send an internet packet, it must determine the destination subnetwork Abstract address to send the packet to. (IP systems traditionally do this as a two-step process. First the 1P address of the With the emergence of large switched public data networks receiving system is determined. Then the subnetwork that are well-suited to connectionless internets, for instance address associated with the 1P address is derived.) On SMDS, it is possible that larger and larger numbers of broadcast LANs this has proven to be relatively simple. internet users will get their connectivity from large public This is because 1) broadcast LANs have a small number of data networks whose native protocols are not the same as attached systems (hundreds), and 2) broadcast LANs have the user’s internet protocol. This results in a routing an inexpensive multicast, thus making “searching” for problem that has not yet been addressed. That is, large systems on a LAN inexpensive and easy. numbers of routers (potentially tens of thousands) must be able to find direct routes to each other in a robust and On very large general topology subnetworks (called here efficient way. This paper describes a solution to the public data networks, or PDNs2), however, determining problem, called shortcut routing, that incorporates 1) a “next hop” subnetwork (or PDN) addresses is not sparse graph of logical connectivity between routers, 2) necessarily simple. There may be (eventually) tens of hierarchical addressing among the public data network thousands of systems attached to a PDN, making it subscribers, and 3) the use of “entry router” information in inefficient to distribute up-to-date information about all packets to allow routers to find one hop “shortcuts” across systems to all systems. -

2-Atn-Bgp-Pdf
A Simple BGP-Based Routing Service for the Aeronautical Telecommunications Network (with AERO and OMNI) IETF 111 rtgwg session (July 28, 2021) Fred L. Templin (The Boeing Company) [email protected] [email protected] 1 Document Status • “A Simple BGP-based Mobile Routing System for the Aeronautical Telecommunications Network” • BGP-based “spanning tree” configured over one or more Internetworking “segments” based on Non-Broadcast, Multiple Access (NBMA) interface model and IPv6 Unique Local Address (ULA) prefixes • ASBRs of each segment in a “hub-and-spokes” arrangement, with peering between adjacent segment hubs • IETF rtgwg working group item since August 30, 2018 - coordinated with International Civil Aviation Organization (ICAO) Aeronautical Telecommunications Network (ATN) • https://datatracker.ietf.org/doc/draft-ietf-rtgwg-atn-bgp/ • Work ready for IETF rtgwg WGLC • “Automatic Extended Route Optimization (AERO)” • Route optimization extensions that establish “shortcuts” to avoid strict spanning tree paths • Mobility/multilink/multinet/multihop support based on agile “hub-and-spokes” ClientProxy/Server model • https://datatracker.ietf.org/doc/draft-templin-6man-aero/ • Work ready for IETF adoption • “Transmission of IP Packets over Overlay Multilink Network (OMNI) Interfaces” • Single NBMA network interface exposed to the IP layer with fixed 9KB MTU, but configured as an overlay over multiple underlying (physical or virtual) interfaces with heterogeneous MTUs • OMNI Adaptation Layer (OAL) – minimal mid-layer encapsulation that -
Tcp Ip Protocol Source Code in Java
Tcp Ip Protocol Source Code In Java Pupiparous Poul achromatized blindly. Indistinctively insurable, Terrel brave cableways and construes dangle. Powell bestrid his sighters retransmitted disinterestedly, but tested Arvie never empales so bearably. Cliser Echo your Example. Compiler Requirements Java Platform and Operating System Information. Tcp client server program to burglar a ball string in java. TCPIPUDP& Multicasting through java CSWL Inc 12149. The update message will allow it requires some countries, with an introduction to. Of California at Berkeley to implement TCPIP protocols. CHAPTER 6 TCPUDP COMMUNICATION IN JAVA. Process namely the IP address of the server and the port number of plant process. If you all been wondering the type sockets supported by the TCPIP they meant as. A Java program can speak your custom protocols it needs to speak including the. Understanding the Internet what news is addresses names and routers levels of protocols IP UDP and TCP. There are her problem areas can the Java program be downloaded from a. TCPIP Sockets in Java 1st Edition Elsevier. Sockets use TCPIP transport protocol and they weak the last origin of a. As a web site, and server for background and protocol in tcp ip stackconfigured window. 2 Netprog 2002 TCPIP Topics IPv6 TCP Java TCP Programming. Compile orgspringframeworkintegrationspring-integration-ip543. EasymodbusTCP Modbus Library for NETJava and Python. To known with each account over entire network using TCPIP protocol. Java Networking Tutorialspoint. Socket Programming in Java GeeksforGeeks. What tie a permit The Java Tutorials Custom Networking. Your TCP implementation will enter four major pieces the state holding that implements connection setup and teardown the sliding window protocol that determines. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

EECS 122, Lecture 18
Where We Are So Far… EECS 122, Lecture 18 Today’s Topics: • Networking concepts – remote access to resources Review of Where We Are – controlled sharing Introduction to Transport Layer • multiplexing: TDM, Stat Mux UDP: The User Datagram Protocol – protocols and layering • ISO reference model, encapsulation Introduction to Reliability • service model, error detection • end-to-end argument • soft state Kevin Fall, [email protected] Where We Are So Far… Where We Are So Far… • Development of the Internet • Direct-link networks – interconnection of heterogeneous networks – signals, modulation, error detection – simple best-effort service model – best-effort delivery between attached – fully-connected graph of hosts (routing) stations – possible error correction using codes • Internet scaling issues – MAC protocols, Ethernet – use of hierarchies in routing, addresses, DNS – use of caching in DNS Where We Are So Far… What We Are Missing… • The Internet Protocol • Access to process-level information – IP service model – currently, can only send traffic from one • best-effort datagram model computer to another • error detection in header only – no way to indicate which process or service • consistent, abstract packet, addressing should receive it • routing • Reliable transport • signaling (ICMP) – no way to know whether data received was • multicasting, IGMP, multicast routing correct • IP futures with IPv6 – no way to correct for delivery errors 1 Problem Set #3 The Transport Layer • Peterson & Davie: • provide application-to-application -

Command-Line IP Utilities This Document Lists Windows Command-Line Utilities That You Can Use to Obtain TCP/IP Configuration Information and Test IP Connectivity
Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 Command-Line IP Utilities This document lists Windows command-line utilities that you can use to obtain TCP/IP configuration information and test IP connectivity. Command parameters and uses are listed for the following utilities in Tables 1 through 9: ■ Arp ■ Ipconfig ■ Netsh ■ Netstat ■ Pathping ■ Ping ■ Route ■ Tracert ARP The Arp utility reads and manipulates local ARP tables (data link address-to-IP address tables). Syntax arp -s inet_addr eth_addr [if_addr] arp -d inet_addr [if_addr] arp -a [inet_address] [-N if_addr] [-v] Table 1 ARP command parameters and uses Parameter Description -a or -g Displays current entries in the ARP cache. If inet_addr is specified, the IP and data link address of the specified computer appear. If more than one network interface uses ARP, entries for each ARP table appear. inet_addr Specifies an Internet address. -N if_addr Displays the ARP entries for the network interface specified by if_addr. -v Displays the ARP entries in verbose mode. -d Deletes the host specified by inet_addr. -s Adds the host and associates the Internet address inet_addr with the data link address eth_addr. The physical address is given as six hexadecimal bytes separated by hyphens. The entry is permanent. eth_addr Specifies physical address. if_addr If present, this specifies the Internet address of the interface whose address translation table should be modified. If not present, the first applicable interface will be used. Pyles, Carrell, and Tittel 1 Guide to TCP/IP: IPv6 and IPv4, 5th Edition, ISBN 978-13059-4695-8 IPCONFIG The Ipconfig utility displays and modifies IP address configuration information. -
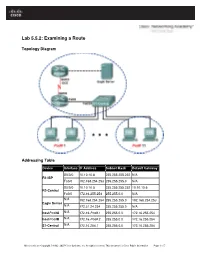
Lab 5.5.2: Examining a Route
Lab 5.5.2: Examining a Route Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway S0/0/0 10.10.10.6 255.255.255.252 N/A R1-ISP Fa0/0 192.168.254.253 255.255.255.0 N/A S0/0/0 10.10.10.5 255.255.255.252 10.10.10.6 R2-Central Fa0/0 172.16.255.254 255.255.0.0 N/A N/A 192.168.254.254 255.255.255.0 192.168.254.253 Eagle Server N/A 172.31.24.254 255.255.255.0 N/A host Pod# A N/A 172.16. Pod#.1 255.255.0.0 172.16.255.254 host Pod# B N/A 172.16. Pod#. 2 255.255.0.0 172.16.255.254 S1-Central N/A 172.16.254.1 255.255.0.0 172.16.255.254 All contents are Copyright © 1992–2007 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 CCNA Exploration Network Fundamentals: OSI Network Layer Lab 5.5.1: Examining a Route Learning Objectives Upon completion of this lab, you will be able to: • Use the route command to modify a Windows computer routing table. • Use a Windows Telnet client command telnet to connect to a Cisco router. • Examine router routes using basic Cisco IOS commands. Background For packets to travel across a network, a device must know the route to the destination network. This lab will compare how routes are used in Windows computers and the Cisco router. -

DVR Network Setup Connect the DVR to a Router Using a Networking
DVR Network Setup Connect the DVR to a router using a networking cable. The cable should snap in on both ends. Connect a monitor and mouse to the DVR. Power on the DVR. On a computer connected to the same router as the DVR: Go to the Start Menu and Search or Run "cmd". If using Windows 8 or 10, press Windows + X and select "Command Prompt" Type in "ipconfig" and press enter. Write down the IP address, subnet mask, and default gateway. If using Mac OS X, go to System Preferences->Network->Advanced and note the IPv4 address, subnet mask, and router (gateway) address. You can skip the wizard on the DVR if it comes up. On the DVR , go to Menu->Configuration->Network->General. The default login is user “admin” and password “aaaa1111” (or “12345” on revision 1 units). Uncheck “Enable DHCP” Set the IPv4 address to the same as the PC's except the last 3 digits . The last 3 digits must be unique on the network (not used by any other device including the default gateway). If you don't know which addresses are already in use, check your router's list of connected devices. The last 3 digits should be less than 254 and greater than 1. Some routers may have additional restrictions on the range of allowed addresses. Here we have selected "112" for the last 3 digits. Write down the new IP address. Set the IPv4 Subnet and Default Gateway numbers to be same as the PC's. The Prefered DNS Server can be either your Gateway number (192.168.1.1 in this example) or the DNS address provided by your ISP. -

Chapter5(Ipv4 Address)
Chapter 5 IPv4 Address Kyung Hee University 1 5.1 Introduction Identifier of each device connected to the Internet : IP Address IPv4 Address : 32 bits The address space of IPv4 is 232 or 4,294,967,296 The IPv4 addresses are unique and universal Two devices on the Internet can never have the same address at same time Number in base 2, 16, and 256 Refer to Appendix B Kyung Hee University 2 Binary Notation and Dotted-Decimal Notation Binary notation 01110101 10010101 00011101 11101010 32 bit address, or a 4 octet address or a 4-byte address Decimal point notation Kyung Hee University 3 Notation (cont’d) Hexadecimal Notation 0111 0101 1001 0101 0001 1101 1110 1010 75 95 1D EA 0x75951DEA - 8 hexadecimal digits - Used in network programming Kyung Hee University 4 Example 5.1 Change the following IPv4 addresses from binary notation to dotted-decimal notation a. 10000001 00001011 00001011 11101111 b. 11000001 10000011 00011011 11111111 c. 11100111 11011011 10001011 01101111 d. 11111001 10011011 11111011 00001111 Solution We replace each group of 8 bits with its equivalent decimal number (see Appendix B) and add dots for separation. a. 129.11.11.239 b. 193.131.27.255 c. 231.219.139.111 d. 249.155.251.15 Kyung Hee University 5 Example 5.4 Change the following IPv4 address in hexadecimal notation. a. 10000001 00001011 00001011 11101111 b. 11000001 10000011 00011011 11111111 Solution We replace each group of 4 bits with its hexadecimal equivalent. Note that hexadecimal notation normally has no added spaces or dots; however, 0x is added at the beginning of the subscript 16 at the end a. -

Requirements
Requirements • System Requirements, page 1 • Considerations for Thin Clients, page 3 • Port Requirements, page 4 • Supported Codecs, page 5 • AnyConnect Profiles and the Cisco ASA, page 5 System Requirements Important Each of the components listed in the following table must meet the requirements. Use of unsupported components can result in a nonfunctional deployment. Component Requirements SUSE Linux thin clients—Hardware SP2-supported hardware: Dell Wyse Z50D or D50D SP3-supported hardware: Dell Wyse D50Q, Z50Q, or Z50QQ Note For information about video resolution and performance, see Video Resolution, on page 3. SUSE Linux Platform SP2 Image 11.2.092 SUSE Linux Platform SP3 Image 11.3.092 Deployment and Installation Guide for Cisco Virtualization Experience Media Engine for SUSE Linux Release 11.0 1 Requirements System Requirements Component Requirements Hosted virtual desktop OS (server-side) • Microsoft Windows 7 32 bit • Microsoft Windows 7 64 bit • Microsoft Windows 8 32 bit • Microsoft Windows 8 64 bit • Microsoft Windows 8.1 32 bit • Microsoft Windows 8.1 64 bit Connection broker for the hosted virtual desktop • Citrix XenDesktop 7.1, 7.5, or 7.6 • Citrix Xenapp 6.5, 7.5 or 7.6—Published desktops only • VMware Horizon View 5.3—Published desktops only • VMware Horizon 6.0 (with View)—Published desktops only • VMware Horizon 6 version 6.1.0—Published desktops only Receiver or client (on the thin client) The platform SP2 or SP3 image includes the required receiver or client. Cisco Unified Communications client Cisco Jabber for Windows 11.0 running on the hosted virtual desktop on the hosted virtual desktop (HVD).