ATN Presentationpresentation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Networking: Network Layer
CS 4410 Operating Systems Networking: Network Layer Summer 2013 Cornell University 1 Today ● How packages are exchanged in a WAN? ● Network Layer ● IP ● Naming ● Subnetwork ● Forwarding ● Routing Algorithms 2 Protocol Stack Computer A Computer B Message M Application Application Segment Ht M Transport Transport Datagram Hn Ht M Network Network Frame Hl Hn Ht M Link Link Physical Physical 3 WAN ● Usually, thousands of computers need to be interconnected. ● The capabilities that LANs offer cannot support larger networks. ● We need more services than the Link Layer offers. ● Why? ● Clever Naming ● Efficient forwarding/routing of messages. 4 Network Layer ● Mission: Transfer messages from the source-computer to the destination- computer. ● Attention: this is different from the mission of the Link Layer. ● Services: ● Forwarding / Routing ● Guaranteed delivery, bandwidth, etc ● Security ● Not all the protocols support these services. ● The Network Layer protocol depends on the kind of network we want to built: ● Virtual-circuit networks ● Datagram networks ● Necessary network device: ● Router: It knows where to forward the message. 5 Network Layer ● Virtual-circuit networks ● 3 phases ● Establish a virtual circuit. – The Network Layer finds the path from the source to the destination. – Reserve resources for the virtual circuit. ● Transfer data – Packets pass through the virtual circuit. ● Destroy virtual circuit. – Release resources. ● Disadvantages? ● Datagram networks ● Every packet has the destination address and it is routed independently in the network. ● The router uses the destination address to forward the packet towards 6 the destination-computer. IP ● Network Layer Protocol for the Internet: ● Internet Protocol ● For Datagram networks. ● IPv4, IPv6 ● Datagram structure: Version Header Type of Length Length service Identification Flags Fragment Offset Time to live Protocol Header Checksum Source IP Address (32-bit) Destination IP Address Options Data 7 Naming ● All the computers in the Internet have one or more IP addresses. -

Internet Routing Over Large Public Data Networks Using Shortcuts
Internet Routing over Large Public Data Networks using Shortcuts Paul F, Tsuchiya, Bellcore, [email protected] When a system (a router or host) needs to send an internet packet, it must determine the destination subnetwork Abstract address to send the packet to. (IP systems traditionally do this as a two-step process. First the 1P address of the With the emergence of large switched public data networks receiving system is determined. Then the subnetwork that are well-suited to connectionless internets, for instance address associated with the 1P address is derived.) On SMDS, it is possible that larger and larger numbers of broadcast LANs this has proven to be relatively simple. internet users will get their connectivity from large public This is because 1) broadcast LANs have a small number of data networks whose native protocols are not the same as attached systems (hundreds), and 2) broadcast LANs have the user’s internet protocol. This results in a routing an inexpensive multicast, thus making “searching” for problem that has not yet been addressed. That is, large systems on a LAN inexpensive and easy. numbers of routers (potentially tens of thousands) must be able to find direct routes to each other in a robust and On very large general topology subnetworks (called here efficient way. This paper describes a solution to the public data networks, or PDNs2), however, determining problem, called shortcut routing, that incorporates 1) a “next hop” subnetwork (or PDN) addresses is not sparse graph of logical connectivity between routers, 2) necessarily simple. There may be (eventually) tens of hierarchical addressing among the public data network thousands of systems attached to a PDN, making it subscribers, and 3) the use of “entry router” information in inefficient to distribute up-to-date information about all packets to allow routers to find one hop “shortcuts” across systems to all systems. -

2-Atn-Bgp-Pdf
A Simple BGP-Based Routing Service for the Aeronautical Telecommunications Network (with AERO and OMNI) IETF 111 rtgwg session (July 28, 2021) Fred L. Templin (The Boeing Company) [email protected] [email protected] 1 Document Status • “A Simple BGP-based Mobile Routing System for the Aeronautical Telecommunications Network” • BGP-based “spanning tree” configured over one or more Internetworking “segments” based on Non-Broadcast, Multiple Access (NBMA) interface model and IPv6 Unique Local Address (ULA) prefixes • ASBRs of each segment in a “hub-and-spokes” arrangement, with peering between adjacent segment hubs • IETF rtgwg working group item since August 30, 2018 - coordinated with International Civil Aviation Organization (ICAO) Aeronautical Telecommunications Network (ATN) • https://datatracker.ietf.org/doc/draft-ietf-rtgwg-atn-bgp/ • Work ready for IETF rtgwg WGLC • “Automatic Extended Route Optimization (AERO)” • Route optimization extensions that establish “shortcuts” to avoid strict spanning tree paths • Mobility/multilink/multinet/multihop support based on agile “hub-and-spokes” ClientProxy/Server model • https://datatracker.ietf.org/doc/draft-templin-6man-aero/ • Work ready for IETF adoption • “Transmission of IP Packets over Overlay Multilink Network (OMNI) Interfaces” • Single NBMA network interface exposed to the IP layer with fixed 9KB MTU, but configured as an overlay over multiple underlying (physical or virtual) interfaces with heterogeneous MTUs • OMNI Adaptation Layer (OAL) – minimal mid-layer encapsulation that -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Chapter5(Ipv4 Address)
Chapter 5 IPv4 Address Kyung Hee University 1 5.1 Introduction Identifier of each device connected to the Internet : IP Address IPv4 Address : 32 bits The address space of IPv4 is 232 or 4,294,967,296 The IPv4 addresses are unique and universal Two devices on the Internet can never have the same address at same time Number in base 2, 16, and 256 Refer to Appendix B Kyung Hee University 2 Binary Notation and Dotted-Decimal Notation Binary notation 01110101 10010101 00011101 11101010 32 bit address, or a 4 octet address or a 4-byte address Decimal point notation Kyung Hee University 3 Notation (cont’d) Hexadecimal Notation 0111 0101 1001 0101 0001 1101 1110 1010 75 95 1D EA 0x75951DEA - 8 hexadecimal digits - Used in network programming Kyung Hee University 4 Example 5.1 Change the following IPv4 addresses from binary notation to dotted-decimal notation a. 10000001 00001011 00001011 11101111 b. 11000001 10000011 00011011 11111111 c. 11100111 11011011 10001011 01101111 d. 11111001 10011011 11111011 00001111 Solution We replace each group of 8 bits with its equivalent decimal number (see Appendix B) and add dots for separation. a. 129.11.11.239 b. 193.131.27.255 c. 231.219.139.111 d. 249.155.251.15 Kyung Hee University 5 Example 5.4 Change the following IPv4 address in hexadecimal notation. a. 10000001 00001011 00001011 11101111 b. 11000001 10000011 00011011 11111111 Solution We replace each group of 4 bits with its hexadecimal equivalent. Note that hexadecimal notation normally has no added spaces or dots; however, 0x is added at the beginning of the subscript 16 at the end a. -

Introduction to IP Multicast Routing
Introduction to IP Multicast Routing by Chuck Semeria and Tom Maufer Abstract The first part of this paper describes the benefits of multicasting, the Multicast Backbone (MBONE), Class D addressing, and the operation of the Internet Group Management Protocol (IGMP). The second section explores a number of different algorithms that may potentially be employed by multicast routing protocols: - Flooding - Spanning Trees - Reverse Path Broadcasting (RPB) - Truncated Reverse Path Broadcasting (TRPB) - Reverse Path Multicasting (RPM) - Core-Based Trees The third part contains the main body of the paper. It describes how the previous algorithms are implemented in multicast routing protocols available today. - Distance Vector Multicast Routing Protocol (DVMRP) - Multicast OSPF (MOSPF) - Protocol-Independent Multicast (PIM) Introduction There are three fundamental types of IPv4 addresses: unicast, broadcast, and multicast. A unicast address is designed to transmit a packet to a single destination. A broadcast address is used to send a datagram to an entire subnetwork. A multicast address is designed to enable the delivery of datagrams to a set of hosts that have been configured as members of a multicast group in various scattered subnetworks. Multicasting is not connection oriented. A multicast datagram is delivered to destination group members with the same “best-effort” reliability as a standard unicast IP datagram. This means that a multicast datagram is not guaranteed to reach all members of the group, or arrive in the same order relative to the transmission of other packets. The only difference between a multicast IP packet and a unicast IP packet is the presence of a “group address” in the Destination Address field of the IP header. -

Networking Basics
Networking Basics Pre-class work…read/watch all the material at least once before class…I will clarify in class. Binary Training(Google search for “binary tutorial”): http://www.math.grin.edu/~rebelsky/Courses/152/97F/Readings/student-binary http://www.codeconquest.com/tutorials/binary/ https://www.youtube.com/watch?v=0qjEkh3P9RE https://www.youtube.com/watch?v=VBDoT8o4q00 Subnet Addressing and Masks(Google search for “subnet mask tutorial”: http://www.techopedia.com/6/28587/internet/8-steps-to-understanding-ip-subnetting http://www.subnetting.net/Tutorial.aspx https://www.youtube.com/watch?v=aA-8owNNy_c 2/10/2017 1 Table of Contents (3)What is the OSI Model? (6)What is a Hub, Switch, & Router/Access Server? (10)Mac Addresses and IP Addresses (15)The “3 GOLDEN PARAMETERS” (16)Day in the Life of a Packet (17)Duplex Issues (18)PC Configuration Guidance (21)Basic Discovery & Connectivity Tools (23)IPv4 Layers and Port Numbers 2/10/2017 2 What is the OSI Model? OSI – open systems interconnection Main functions Network dependent functions Application-oriented functions Seven layer model Each layer performs a well- defined set of functions 2/10/2017 3 Data Encapsulation Application User data Presentation converted for Data (PDU) transmission Session Add transport Segments Transport type header Add network Packets Network header (datagram) Add datalink Frames Datalink header Convert 11001010…100 Bits Physical to bits 2/10/2017 4 ISO’s OSI Reference Model Application Application Presentation Presentation Session Session Transport Transport -

Ipv6 Addressing and Basic Connectivity Configuration Guide Cisco IOS Release 15.1SG
IPv6 Addressing and Basic Connectivity Configuration Guide Cisco IOS Release 15.1SG Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -
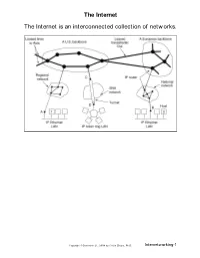
The Internet the Internet Is an Interconnected Collection of Networks
The Internet The Internet is an interconnected collection of netw orks. Copyright © December 21, 2004 by Chaim Ziegler, Ph.D. Internetw orking-1 Internetworking ! Communications Network: A facility that provides a data transfer service among stations attached to the network. ! Internet: A collection of interconnected communications netw orks. ! Subnetwork: A constituent network of an internet. ! Intermediate System (IS) or Interw orking Unit (IWU): A device used to interconnect two subnetworks and permit communications between end systems attached to different subnetworks. ! Bridge: An IWU used to interconnect tw o or more LANs. A bridge operates at layer 2 of the OSI model. ! Router: A device used to interconnect two or more networks at layer 3 of the OSI model. Copyright © December 21, 2004 by Chaim Ziegler, Ph.D. Internetw orking-2 Requirements for Internetworking ! Provide a link betw een netw orks. ! Provide for routing and delivery of data between processes on different netw orks. ! Provide an accounting service that keeps track of the use and status of the various netw orks and IWUs. ! Accommodate differences among netw orks: - network service - addressing - routing - quality of service - maximum packet size - flow and congestion control - error reporting Copyright © December 21, 2004 by Chaim Ziegler, Ph.D. Internetw orking-3 Addressing ! Network Service Access Point (NSAP): - Uniquely identifies a DTE w ithin the internet (global internet address). - A DTE may have more than one NSAP. - Usually has the form (netw ork, host). ! Subnetwork Attachment Point Address (Network Point of Attachment): - Each subnetw ork must maintain a unique address for each DTE attached to that subnetwork. -

Advice for Internet Subnetwork Designers
Horst D. Clausen, NMT Multimedia Communications-SS2002 Internet Engineering Task Force Phil Karn, editor INTERNET DRAFT Qualcomm Advice for Internet Subnetwork Designers File: draft-ietf-pilc-link-design-09.txt February, 2002 Expires: August, 2002 Performance Implications of Link Characteristics Working Group Abstract This document provides advice to the designers of digital communication equipment, link-layer protocols and packet-switched subnetworks (collectively referred to as subnetworks) who wish to support the Inter- net protocols but who may be unfamiliar with Internet architecture and the implications of their design choices on the performance and efficiency of the Internet. This document represents a consensus of the members of the IETF Performance Implications of Link Characteristics (PILC) working group. 1. Introduction and Overview IP, the Internet Protocol [RFC791] is the core protocol of the Internet. IP defines a simple “connectionless” packet-switched network. The success of the Internet is largely attributed to IP’s simplicity, the “end-to-end principle” [SRC81] on which the Internet is based, and the resulting ease of carrying IP on a wide variety of subnetworks not necessarily designed with IP in mind. But while many subnetworks carry IP, they do not necessarily do so with maximum efficiency, minimum complexity or minimum cost. Nor do they implement certain features to efficiently support newer Internet features of increasing importance, such as multicasting and quality of service. With the explosive growth of the Internet, IP is an increasingly large fraction of the traffic carried by the world’s telecommunications networks. It therefore makes sense to optimize both existing and new subnet- work technologies for IP as much as possible. -

IP Addressing and Subnetting Workbook Version 1.5
10011000 1010100 10001111100 1011100101011100 101100011101001 1011110100011010 00001010010110010 1001010101100111 1111010101000101 1101001101010011 001010010101010 1010101000110010 010101001011000 110101100011010 11010100001011 001010100110 1001010010 001IP Addressing and Subnetting Workbook Version 1.5 Instructor’s Edition 11111110 10010101 00011011 10000110 11010011 0101 IP Address Classes Class A 1 – 127 (Network 127 is reserved for loopback and internal testing) Leading bit pattern 0 00000000.00000000.00000000.00000000 Network . Host . Host . Host Class B 128 – 191 Leading bit pattern 10 10000000.00000000.00000000.00000000 Network . Network . Host . Host Class C 192 – 223 Leading bit pattern 110 11000000.00000000.00000000.00000000 Network . Network . Network . Host Class D 224 – 239 (Reserved for multicast) Class E 240 – 255 (Reserved for experimental, used for research) Private Address Space Class A 10.0.0.0 to 10.255.255.255 Class B 172.16.0.0 to 172.31.255.255 Class C 192.168.0.0 to 192.168.255.255 Default Subnet Masks Class A 255.0.0.0 Class B 255.255.0.0 Class C 255.255.255.0 Produced by: Robb Jones [email protected] Frederick County Career & Technology Center Cisco Networking Academy Frederick County Public Schools Frederick, Maryland, USA Special Thanks to Melvin Baker and Jim Dorsch for taking the time to check this workbook for errors, and to everyone who has sent in suggestions to improve the series. Workbooks included in the series: IP Addressing and Subnetting Workbooks ACLs - Access Lists Workbooks VLSM Variable-Length Subnet Mask IWorkbooks Instructors (and anyone else for that matter) please do not post the Instructors version on public websites. When you do this you are giving everyone else worldwide the answers. -

Packetradio©
ALL cables and interfaces shown in this book are available at: www.HamRadioExpress.com PacketRadio© This Handbook is dedicated to the PacketRadio System Node Operator (SNO) by Buck Rogers, K4ABT A Guide to PacketRadio operating and X-1J4 TheNET Node implementation. This manual will serve as a multi-function handbook that supports digital networking and communications. As a PacketRadio handbook, this manual can provide a “heads-up” for the new PacketRadio user with a wealth of information that applies directly to the interfacing, installation, and operation of a PacketRadio station, and the implementation of the X-1J4 TheNET node. This handbook will become a ready-reference in your day-to-day, PacketRadio operations. It is my intent to provide the this manual as a final gesture of friendship to my many friends of the SEDAN. I hope these documents and tools serve you well, and may God smile on you as you continue to experience the fun within this wonderful, fun-filled facet of Amateur Radio. Buck Rogers K4ABT E-Mail [email protected] PacketRadio Editor, CQ Magazine Copyrights 1999-2007 BUX CommCo; 115 Luenburg Drive; Evington, Virginia 24550-1702 - 800 726 2919 This Digital Radio Handbook is FREE and is to be freely distributed without any commercial association. A PacketRadio Primer ! By Buck Rogers K4ABT Digital Editor; CQ Magazine When you first turn on the TNC you may see garbled text on the screen. This is usually because the terminal to TNC baudrate is not set to the same parameters. Some TNCs will do a "search" mode to find the setting that you have your terminal program set to/for.