Products Claims Testing Claims Test ADPC0020 Piceasoft Limited
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
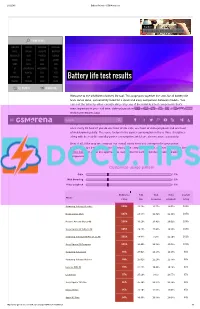
Battery Life Test Results HUAWEI TOSHIBA INTEX PLUM
2/12/2015 Battery life tests GSMArena.com Starborn SAMSUNG GALAXY S6 EDGE+ REVIEW PHONE FINDER SAMSUNG LENOVO VODAFONE VERYKOOL APPLE XIAOMI GIGABYTE MAXWEST MICROSOFT ACER PANTECH CELKON NOKIA ASUS XOLO GIONEE SONY OPPO LAVA VIVO LG BLACKBERRY MICROMAX NIU HTC ALCATEL BLU YEZZ MOTOROLA ZTE SPICE PARLA Battery life test results HUAWEI TOSHIBA INTEX PLUM ALL BRANDS RUMOR MILL Welcome to the GSMArena battery life tool. This page puts together the stats for all battery life tests we've done, conveniently listed for a quick and easy comparison between models. You can sort the table by either overall rating or by any of the individual test components that's most important to you call time, video playback or web browsing.TIP US 828K 100K You can find all about our84K 137K RSS LOG IN SIGN UP testing procedures here. SearchOur overall rating gives you an idea of how much battery backup you can get on a single charge. An overall rating of 40h means that you'll need to fully charge the device in question once every 40 hours if you do one hour of 3G calls, one hour of video playback and one hour of web browsing daily. The score factors in the power consumption in these three disciplines along with the reallife standby power consumption, which we also measure separately. Best of all, if the way we compute our overall rating does not correspond to your usage pattern, you are free to adjust the different usage components to get a closer match. Use the sliders below to adjust the approximate usage time for each of the three battery draining components. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

LG L Bello LG F60 LG G3 S Meizu MX3 Microsoft Lumia 532 Dual SIM
LG L Bello LG F60 LG G3 S Meizu MX3 Microsoft Lumia 532 Dual SIM procesor Mediatek MT6582, 4× 1,3 GHz Snapdragon 410, 4× 1,2 GHz Snapdragon 400, 4× 1,2 GHz Samsung Exynos 5 Octa, Qualcomm Snapdragon 200, 4× Cortex-A7 Cortex-A53 Cortex-A7 Cortex-A15 + Cortex-A7, 4 × 1,2 GHz Cortex-A7 1,6 GHz, 4 × 1,2 GHz pomnilnik (GB) 1 1 1 2 1 shramba (GB) 8 8 16 16 8 diagonala zaslona (palci) 5 4,5 5 5,1 4 ločljivost zaslona (pik) 480 × 854 480 × 800 720 × 1280 1800 × 1080 480 × 800 ločljivost fotoaparata (megapik) 8 5 8 5 reža za kartico microSD ✓ ✓ ✓ ✓ akumulator, mAh 2540 2100 2540 2400 1560 operacijski sistem Android 4.2.2 Android 4.2.2 Android 4.4 Android 4.2 Windows Phone 8.1 masa (g) 137 130 134 143 136 MERITVE geekbench eno jedro 351 475 338 743 geekbench več jeder 1171 1429 1131 1957 cena brez vezave 200 EUR 480 EUR 270 EUR 300 EUR 125 EUR prodaja ponudniki mobilne telefonije ponudniki mobilne telefonije ponudniki mobilne telefonije www.tusmobil.si ponudniki mobilne telefonije Microsoft Lumia 535 Nokia Lumia 735 OnePlus One Prestigio MultiPhone Samsung Galaxy Core Grace Prime procesor Qualcomm Snapdragon Snapdragon 400, 4× 1,2 GHz Snapdragon 801, MediaTek MT6592 1,6 GHz 8× Qualcomm Snapdragon 410 200, 4× 1,2 GHz Cortex-A7 Cortex-A7 4× 2,5 GHz Cortex A7 4× 1,2 GHz Cortex-A53 pomnilnik (GB) 1 1 3 2 1 shramba (GB) 8 8 16 16 8 diagonala zaslona (palci) 5 4,7 5,5 5 4,5 ločljivost zaslona (pik) 540 × 960 720 × 1280 1920 × 1080 1920 × 1080 480 × 800 ločljivost fotoaparata (megapik) 5 6,7 13 13 5 reža za kartico microSD ✓ ✓ ✗ ✗ ✓ akumulator, mAh 1905 -

Nokia Lumia 532 Manual Download Nokia Lumia 532 Manual
Nokia Lumia 532 Manual Download Nokia Lumia 532 Manual Free whatsapp download per nokia lumia 532 download software at UpdateStar - WhatsApp Messenger is a cross-platform mobile messaging app which allows you to exchange messages without having to pay for SMS. Microsoft Lumia 640 XL LTE Dual Sim - PDF manual · Microsoft Lumia 640. Microsoft Lumia 532 Dual - PDF manual · Microsoft Lumia 505. The Microsoft Lumia 532 currently has an Informr score of 6.4 out of 10. This score is based on. Where can I the Lumia 532 manual? We've got you. 24 Oct 2015. Microsoft Lumia 532 hard reset using Volume down, Volume up and Power button.We are glad to answer all your questions. Návod na Lumia 532 od výrobce Nokia. Část manuálu v češtině pro výrobek Nokia Lumia 532: Nebylo možné získat část návodu pro model Lumia 532. Currently the devices which are officially supported are, Alcatel OneTouch Fierce XL, BLU Win HD LTE x150e, BLU Win HD W510U, BLU Win HD LTE X150Q, BLU Win JR x130e, Lumia 430, Lumia 435, Lumia 532, Lumia 535, Lumia 540, Lumia 550, Lumia 635 (1GB), Lumia 636 (1GB), Lumia 638 (1GB), Lumia 640, Lumia 640 XL, Lumia 650, Lumia 730, Lumia 735, Lumia 830, Lumia 929 (ICON), Lumia 930, Lumia 950.Wallet Flip Leather Stand Case Cover for Microsoft Nokia Lumia 532 435 + SG. $4.83. Choose Any 1 Vinyl Decal-Skin for Nokia Lumia 521 Smartphone - Buy 1 Get 2.The debut of Cortana changed how Lumia users scan QR codes and text. Here’s a step-by-step guide on the new process. -

Lumia. Achieve More
Lumia. The tablet that can Achieve more. replace your laptop. Microsoft Lumia 640 Get things done anytime, anywhere and on any device. Microsoft Lumia 640 XL The power and performance R uns Windows, of a laptop with the convenience of a tablet and browsers Get unmatched versatility with the Use your favorite software and apps with 1TB of OneDrive thinnest and lightest in the Pro family. side by side for multitasking ease. online storage. Be more productive. Anytime. Anywhere. Coming soon! Free OneDrive Install Office applications on unlimited online storage. multiple devices and platforms Choose the color that clicks The ultra-thin backlit Surface Pro Type Cover comes in five vibrant colors and has the speed Access your files anytime, anywhere, and functionality of a classic laptop keyboard. with 1TB OneDrive online storage 1 million Best writing and Big-screen entertainment, Personalize your drawing experience anywhere Surface with apps Stay up to date with your favourite apps: From the Surface Pen to the kickstand Enjoy movies and games with the stunning Word, Excel, PowerPoint, Outlook and more to the screen size, every detail is designed 12" Full HD Plus display and Dolby® audio. for a natural feel. Make the most of your downtime with Surface’s amazing built-in apps. 10,000 70,000 You’ll find thousands more online in Songs Photos Everything’s connected the Windows Store — apps for With Windows 8.1, you can easily share the content between your Phone, laughing, dancing, traveling, playing, when you buy a PC, Mac, Windows tablet or iPad. Ask staff for details. -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -

Microsoft Seeks User Reviews for Windows Phone Devices
Microsoft Seeks User Reviews For Windows Phone Devices 1 / 4 Microsoft Seeks User Reviews For Windows Phone Devices 2 / 4 3 / 4 microsoft windows 10 mobile continuum apps support lumia 950 950xl front Microsoft ... According to the email, the company is seeking opinions about ... “which apps are more important” to Windows 10 Mobile device owners.. See screenshots, read the latest customer reviews, and compare ratings ... Lumia Models wants to be the best Lumia App from Windows Phone Store. ... for the following devices: - Nokia Lumia 530 DS - Microsoft Lumia 532 .... As of January 14, Windows 7 users will no longer receive updates or support. ... run the update, rather than forcing it, since Microsoft tries to validate updates for each ... Microsoft's goal with all this is to make your mobile devices smarter by .... This newsroom provides the latest product news, articles and reviews, event resources, and other press materials about Windows Phones. Press Contact. WE .... In any case, Microsoft needed a stake of the modern smartphone market and needed it fast. ... Windows Phone users who began using the platform with 8.1 may not be ... Now with a huge number of devices, a well-received OS and the ... back to an OS that wants to simply be an extension of your computer.. Windows 10 Mobile is a major step forward for Microsoft's usually ... Microsoft will keep the software updates coming to improve the user experience. ... and cohesive software experience across your devices – it wants you to .... Managed on the information platform Microsoft Windows Phone 8Microsoft Windows ... This page seeks to list and compare hardware devices that are shipped with Microsoft's .. -

Alcatel One Touch Go Play 7048 Alcatel One Touch
Acer Liquid Jade S Alcatel Idol 3 4,7" Alcatel Idol 3 5,5" Alcatel One Touch Go Play 7048 Alcatel One Touch Pop C3/C2 Alcatel One Touch POP C7 Alcatel Pixi 4 4” Alcatel Pixi 4 5” (5045x) Alcatel Pixi First Alcatel Pop 3 5” (5065x) Alcatel Pop 4 Lte Alcatel Pop 4 plus Alcatel Pop 4S Alcatel Pop C5 Alcatel Pop C9 Allview C6 Quad Apple Iphone 4 / 4s Apple Iphone 5 / 5s / SE Apple Iphone 5c Apple Iphone 6/6s 4,7" Apple Iphone 6 plus / 6s plus Apple Iphone 7 Apple Iphone 7 plus Apple Iphone 8 Apple Iphone 8 plus Apple Iphone X HTC 8S HTC Desire 320 HTC Desire 620 HTC Desire 626 HTC Desire 650 HTC Desire 820 HTC Desire 825 HTC 10 One M10 HTC One A9 HTC One M7 HTC One M8 HTC One M8s HTC One M9 HTC U11 Huawei Ascend G620s Huawei Ascend G730 Huawei Ascend Mate 7 Huawei Ascend P7 Huawei Ascend Y530 Huawei Ascend Y540 Huawei Ascend Y600 Huawei G8 Huawei Honor 5x Huawei Honor 7 Huawei Honor 8 Huawei Honor 9 Huawei Mate S Huawei Nexus 6p Huawei P10 Lite Huawei P8 Huawei P8 Lite Huawei P9 Huawei P9 Lite Huawei P9 Lite Mini Huawei ShotX Huawei Y3 / Y360 Huawei Y3 II Huawei Y5 / Y541 Huawei Y5 / Y560 Huawei Y5 2017 Huawei Y5 II Huawei Y550 Huawei Y6 Huawei Y6 2017 Huawei Y6 II / 5A Huawei Y6 II Compact Huawei Y6 pro Huawei Y635 Huawei Y7 2017 Lenovo Moto G4 Plus Lenovo Moto Z Lenovo Moto Z Play Lenovo Vibe C2 Lenovo Vibe K5 LG F70 LG G Pro Lite LG G2 LG G2 mini D620 LG G3 LG G3 s LG G4 LG G4c H525 / G4 mini LG G5 / H830 LG K10 / K10 Lte LG K10 2017 / K10 dual 2017 LG K3 LG K4 LG K4 2017 LG K7 LG K8 LG K8 2017 / K8 dual 2017 LG L Fino LG L5 II LG L7 LG -
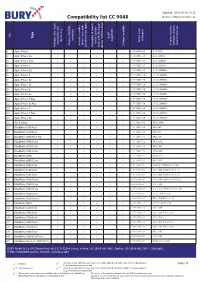
Compatibility List CC 9048 Device Software Version: 22
Updated: 2016-10-25 / V.22 Compatibility list CC 9048 Device software version: 22 No Type A2DP activation (Charger) supported device key Article code car kit / private connection with test/ Comments phone voice-dial software used to Phone‘s REDIAL Phone‘s REDIAL Version of phone Version Access to mobile Charger available Possibility to switch Activation Bluetooth function (voice tags) mode with Bluetooth device / phones keys 1 Apple iPhone 0-07-0258-0.07 3.0(7A341) 2 Apple iPhone 3G 0-07-0258-0.07 4.2.1 (8A306) 3 Apple iPhone 3GS 0-07-0258-0.07 6.1.2 (10B146) 4 Apple iPhone 4 0-07-0258-0.07 7.0.2 (11A501) 5 Apple iPhone 4S 0-07-0258-0.07 7.0.4 (11B554a) 6 Apple iPhone 5 0-07-0258-0.08 10.0.2 (14A456) 7 Apple iPhone 5c 0-07-0258-0.08 10.0.2 (14A456) 8 Apple iPhone 5s 0-07-0258-0.08 10.0.2 (14A456) 9 Apple iPhone 6 0-07-0258-0.08 10.0.2 (14A456) 10 Apple iPhone 6s 0-07-0258-0.08 10.0.2 (14A456) 11 Apple iPhone 6 Plus 0-07-0258-0.08 10.0.2 (14A456) 12 Apple iPhone 6s Plus 0-07-0258-0.08 10.0.2 (14A456) 13 Apple iPhone 7 0-07-0258-0.08 10.0.3 (14A551) 14 Apple iPhone 7 Plus 0-07-0258-0.08 10.0.3 (14A551) 15 Apple iPhone SE 0-07-0258-0.08 10.0.2 (14A456) 16 ASUS Solaris 0-07-0258-0.02 V4.2.2 WWE 17 BlackBerry 8100 Pearl 0-07-0258-0.02 V4.5.0.69 18 BlackBerry 8110 Pearl 0-07-0258-0.02 V4.5.0.55 19 BlackBerry 8220 Pearl Flip 0-07-0258-0.01 V4.6.0.94 20 BlackBerry 8300 Curve 0-07-0258-0.02 V4.5.0.182 21 BlackBerry 8310 Curve -

Arkusz1 Strona 1 MODEL TEL. ALCATEL 3040G
Arkusz1 QTY PRICE NET/ MODEL AVAILABLE UNIT TEL. ALCATEL 3040G- GRADE B (SL) 1 10 EUR TEL. ALCATEL ONE TOUCH 2007D - GRADE B 1 12 EUR TEL. ALCATEL ONE TOUCH 7041X - GRADE C 1 13 EUR TEL. ALCATEL ONETOUCH 2045X - GRADE B 1 10 EUR TEL. ALCATEL ONETOUCH 2045X - GRADE B* 1 8 EUR TEL. ALCATEL ONETOUCH 6030X-GRADE B 1 20 EUR TEL. ALCATEL OT-E221 - GRADE D (SL) 1 3 EUR TEL. ALCATEL PIXI 4 - GRADE D 1 10 EUR TEL. ALCATEL VLE5 - GRADE A (SL) 1 4 EUR TEL. ASUS_T00I ZENFONE 4 - GRADE C 1 40 EUR TEL. ASUS_T00J ZENFONE 5 - GRADE B* 1 55 EUR TEL. BLACKBERRY Classic Q20 - GRADE B*. 1 30 EUR TEL. BLACKBERRY Q10 - GRADE B 1 25 EUR TEL. BLACKBERRY Q5 - GRADE C 2 15 EUR TEL. BLACKBERRY Z10 STL100-1 - GRADE B 1 26 EUR TEL. CAT B25 - GRADE C 1 14 EUR TEL. CAT B25 - GRADE D 1 8 EUR TEL. CAT B30 - GRADE D 1 10 EUR TEL. DISCOVERY V8 - Grade B 1 30 EUR TEL. HTC DESIRE 310 (0PA2110) - GRADE B* 1 16 EUR TEL. HTC DESIRE 310 (0PA2110) - GRADE C 1 14 EUR TEL. HTC Desire 500 - GRADE B 1 16 EUR TEL. HTC G1 - GRADE A 1 20 EUR TEL. HTC HERM300 - GRADE A 1 45 EUR TEL. HTC WILDFIRE S (PG76100) - GRADE B* 1 12 EUR TEL. HTC WILDFIRE S (PG76100) - GRADE D 1 8 EUR TEL. HUAWEI ASCEND G 300 - GRADE C 1 25 EUR TEL. HUAWEI Ascend Y300 - GRADE C 1 16 EUR TEL. -

Offer Terms & Conditions • This Promotional Offer Is Only Available
Offer Terms & Conditions This promotional offer is only available to customers purchasing select models of smartphones (list available below) from Amazon.in between Aug 10th, 2015 and Aug 12th, 2015. In addition, this offer is only available to Amazon.in customers (i) located in India, (ii) that have set India as their country of record in their Amazon.in account settings, (iii) with a billing address in India and (iv) who have accepted the Amazon.in Kindle Store Terms of Use. Any customer attempting to redeem this promotion from outside of India (or from a device with a non-India IP address) are not eligible for this offer. By August 15, 2015 eligible participants will receive the promotion code to buy eBooks worth Rs.300 This is a limited time offer and the promotional credit will expire on September 9th, 2015 The promotional credit may only be applied to Kindle eBook titles sold and delivered by be Amazon Digital South Asia Inc. Offer limited to one promotional credit per qualifying device purchase. Promotional supplies are limited. Promotional credit will be allocated proportionally among all qualifying items in your order. If any of the products or content related to this offer are returned, your refund will equal the amount you paid for the product or content, subject to applicable refund policies. Standard terms and conditions, including the Amazon.in Conditions of Use and Sale and Privacy Notice, apply to this promotion, use of the Amazon.in website and the Kindle reading apps. The promotional credit is non-transferable, not exchangeable or redeemable for cash or other goods or services and may not be combined with other credits or special offers. -

Question Number: 76 Division/Agency: Information
Rural and Regional Affairs and Transport Legislation Committee ANSWERS TO QUESTIONS ON NOTICE Additional Estimates February 2017 Agriculture and Water Resources Question Number: 76 Division/Agency: Information Services Division Topic: Mobile devices Proof Hansard Page: Written Senator BILYK asked: 1. How many mobile telephones are currently on issue to departmental to staff? 2. Can an itemised list showing make and model please be provided? 3. How many new mobile phones were purchased by the Department in calendar year 2016? 4. What was the total cost (GST inclusive) of purchasing mobile telephones for departmental staff in calendar year 2016? 5. How many mobile telephones had to be replaced due to damage in calendar year 2016? What was the cost of replacement (GST inclusive)? 6. How many mobile telephones were reported lost or stolen in calendar year 2016? What was the cost of replacement (GST inclusive)? 7. How many ipads/tablets are currently on issue to departmental staff? 8. Can an itemised list showing make and model please be provided? 9. How many new ipads/tablets were purchased by the Department in calendar year 2016? 10. What was the total cost (GST inclusive) of purchasing ipads/tablets for departmental staff in calendar year 2016? 11. How many ipads/tablets had to be replaced due to damage in calendar year 2016? What was the cost of replacement (GST inclusive)? 12. How many ipads/tablets were reported lost or stolen in calendar year 2016? What was the cost of replacement (GST inclusive)? Question Number: 76 (continued) Answer: (Data current as at 31 Jan 2017) 1.