Easter Eggs: Hidden Tracks and Messages in Musical Mediums
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

PERFORMED IDENTITIES: HEAVY METAL MUSICIANS BETWEEN 1984 and 1991 Bradley C. Klypchak a Dissertation Submitted to the Graduate
PERFORMED IDENTITIES: HEAVY METAL MUSICIANS BETWEEN 1984 AND 1991 Bradley C. Klypchak A Dissertation Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY May 2007 Committee: Dr. Jeffrey A. Brown, Advisor Dr. John Makay Graduate Faculty Representative Dr. Ron E. Shields Dr. Don McQuarie © 2007 Bradley C. Klypchak All Rights Reserved iii ABSTRACT Dr. Jeffrey A. Brown, Advisor Between 1984 and 1991, heavy metal became one of the most publicly popular and commercially successful rock music subgenres. The focus of this dissertation is to explore the following research questions: How did the subculture of heavy metal music between 1984 and 1991 evolve and what meanings can be derived from this ongoing process? How did the contextual circumstances surrounding heavy metal music during this period impact the performative choices exhibited by artists, and from a position of retrospection, what lasting significance does this particular era of heavy metal merit today? A textual analysis of metal- related materials fostered the development of themes relating to the selective choices made and performances enacted by metal artists. These themes were then considered in terms of gender, sexuality, race, and age constructions as well as the ongoing negotiations of the metal artist within multiple performative realms. Occurring at the juncture of art and commerce, heavy metal music is a purposeful construction. Metal musicians made performative choices for serving particular aims, be it fame, wealth, or art. These same individuals worked within a greater system of influence. Metal bands were the contracted employees of record labels whose own corporate aims needed to be recognized. -

Physicality of the Analogue by Duncan Robinson BFA(Hons)
Physicality of the Analogue by Duncan Robinson BFA(Hons) Submitted in the fulfilment of the requirements for the degree of Master of Fine Arts. 2 Signed statement of originality This Thesis contains no material which has been accepted for a degree or diploma by the University or any other institution. To the best of my knowledge and belief, it incorporates no material previously published or written by another person except where due acknowledgment is made in the text. Duncan Robinson 3 Signed statement of authority of access to copying This Thesis may be made available for loan and limited copying in accordance with the Copyright Act 1968. Duncan Robinson 4 Abstract: Inside the video player, spools spin, sensors read and heads rotate, generating an analogue signal from the videotape running through the system to the monitor. Within this electro mechanical space there is opportunity for intervention. Its accessibility allows direct manipulation to take place, creating imagery on the tape as pre-recorded signal of black burst1 without sound rolls through its mechanisms. The actual physical contact, manipulation of the tape, the moving mechanisms and the resulting images are the essence of the variable electrical space within which the analogue video signal is generated. In a way similar to the methods of the Musique Concrete pioneers, or EISENSTEIN's refinement of montage, I have explored the physical possibilities of machine intervention. I am working with what could be considered the last traces of analogue - audiotape was superseded by the compact disc and the videotape shall eventually be replaced by 2 digital video • For me, analogue is the space inside the video player. -

Apocrypha Discordiadiscordia Ðe Seconde Edityon
ApocryphaApocrypha DiscordiaDiscordia Ðe Seconde Edityon Compy’eled fromme Dyverƒ Sorƒeƒ by Hiƒ Wholineß ðe Rev DrJon Swabey Wið ILLUMINATIONS by Pope Phil Wlodarczyk III To the Prettiest One and to Blade, without whom. and in honour: Mal2 and Omar; Greg and Kerry; A couple of guys, A couple of saints. Dance with the Goddess (Jiggy-Jiggy) ILLUMINATIONS BY POPE PHIL WLODARCZYK III Content and Layout The Rev DrJon Swabey & a whole bunch of other Erisians, Discordians and Weirdos far too many to list here on this tiny page (sorry). Where identified, they’re all credited in the text. All effort has been made to verify the (K) status of individual items, however in the event of non - (K) items being accidentally included, please notify, and said items will be removed in subsequent editions. ( K ) 2001 ALL RITES REVERSED REPRINT WHAT YOU LIKE Second Edition 2002 3 5 7 9 8 6 4 2 Apocrypha Discordia with ILLUMINATIONS by Pope Phil Wlodarczyk III Assembled by His Wholiness the Rev DrJon on behalf of The Committee for Public Safety Approved for abuse in schools Give me your tired, your poor, Your huddled masses yearning to be free The wretched refuse of your teeming shore This country always needs more Soylent Green HAIL ERIS! — καλλιχτι — ALL HAIL DISCORDIA! Eristroduction You should have put that in there...”I found out I was dying, and used my last days to create a Discordian Manual...” Prince MuChao, Private correspodance, January 2002 Of course, I was wrong, Little Deluded Dupe that I am. Seven days before I was scheduled for Surgery, that quiet voice which I imagine also talks to Zen monks, Sufi mullahs and other Disreputable Persons at the End, rapped sharply on my skull and told me to get my shit in order within the week. -

MUSIC NOTES: Exploring Music Listening Data As a Visual Representation of Self
MUSIC NOTES: Exploring Music Listening Data as a Visual Representation of Self Chad Philip Hall A thesis submitted in partial fulfillment of the requirements for the degree of: Master of Design University of Washington 2016 Committee: Kristine Matthews Karen Cheng Linda Norlen Program Authorized to Offer Degree: Art ©Copyright 2016 Chad Philip Hall University of Washington Abstract MUSIC NOTES: Exploring Music Listening Data as a Visual Representation of Self Chad Philip Hall Co-Chairs of the Supervisory Committee: Kristine Matthews, Associate Professor + Chair Division of Design, Visual Communication Design School of Art + Art History + Design Karen Cheng, Professor Division of Design, Visual Communication Design School of Art + Art History + Design Shelves of vinyl records and cassette tapes spark thoughts and mem ories at a quick glance. In the shift to digital formats, we lost physical artifacts but gained data as a rich, but often hidden artifact of our music listening. This project tracked and visualized the music listening habits of eight people over 30 days to explore how this data can serve as a visual representation of self and present new opportunities for reflection. 1 exploring music listening data as MUSIC NOTES a visual representation of self CHAD PHILIP HALL 2 A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF: master of design university of washington 2016 COMMITTEE: kristine matthews karen cheng linda norlen PROGRAM AUTHORIZED TO OFFER DEGREE: school of art + art history + design, division -

NEW RELEASE GUIDE September 3 September 10 ORDERS DUE JULY 30 ORDERS DUE AUGUST 6
ada–music.com @ada_music NEW RELEASE GUIDE September 3 September 10 ORDERS DUE JULY 30 ORDERS DUE AUGUST 6 2021 ISSUE 19 September 3 ORDERS DUE JULY 30 SENJUTSU LIMITED EDITION SUPER DELUXE BOX SET Release Date: September 3, 2021 INCLUDES n Standard 2CD Digipak with 28-page booklet n Blu-Ray Digipak • “The Writing On The Wall” • Making Of “The Writing On The Wall” • Special Notes from Bruce Dickinson • 20-page booklet n 3 Illustrated Art Cards n 3D Senjutsu Eddie Lenticular n Origami Sheet with accompanying instructions to produce an Origami version of Eddie’s Helmet, all presented in an artworked envelope n Movie-style Poster of “The Writing On The Wall” n All housed in Custom Box made of durable board coated with a gloss lamination TRACKLIST CD 1 1. Senjutsu (8:20) 2. Stratego (4:59) 3. The Writing On The Wall (6:23) 4. Lost In A Lost World (9:31) 5. Days Of Future Past (4:03) 6. The Time Machine (7:09) CD 2 7. Darkest Hour (7:20) 8. Death of The Celts (10:20) 9. The Parchment (12:39) 10. Hell On Earth (11:19) BLU-RAY • “The Writing On The Wall” Video • “The Writing On The Wall” The Making Of • Special notes from Bruce Dickinson LIMITED EDITION SUPER DELUXE BOX SET List Price: $125.98 | Release Date: 9/3/21 | Discount: 3% Discount (through 9/3/21) Packaging: Super Deluxe Box | UPC: 4050538698114 Returnable: YES | Box Lot: TBD | Units Per Set: TBD | File Under: Rock SENJUTSU Release Date: September 3, 2021 H IRON MAIDEN Take Inspiration From The East For Their 17th Studio Album, SENJUTSU H Brand new double album shows band maintain -

Apocrypha Discordia.Pdf
To the Prettiest One and to Blade, without whom. and in honour: Mal2 and Omar; Greg and Kerry; A couple of guys, A couple of saints. Dance with the Goddess (Jiggy-Jiggy) ILLUMINATIONS BY POPE PHIL WLODARCZYK III Content and Layout The Rev DrJon Swabey & a whole bunch of other Erisians, Discordians and Weirdos far too many to list here on this tiny page (sorry). Where identified, they’re all credited in the text. All effort has been made to verify the (K) status of individual items, however in the event of non - (K) items being accidentally included, please notify, and said items will be removed in subsequent editions. ( K ) 2001 ALL RITES REVERSED REPRINT WHAT YOU LIKE Second Edition 2002 3 5 7 9 8 6 4 2 Apocrypha Discordia with ILLUMINATIONS by Pope Phil Wlodarczyk III Assembled by His Wholiness the Rev DrJon on behalf of The Committee for Public Safety Approved for abuse in schools Give me your tired, your poor, Your huddled masses yearning to be free The wretched refuse of your teeming shore This country always needs more Soylent Green HAIL ERIS! — καλλιχτι — ALL HAIL DISCORDIA! Eristroduction You should have put that in there...”I found out I was dying, and used my last days to create a Discordian Manual...” Prince MuChao, Private correspodance, January 2002 Of course, I was wrong, Little Deluded Dupe that I am. Seven days before I was scheduled for Surgery, that quiet voice which I imagine also talks to Zen monks, Sufi mullahs and other Disreputable Persons at the End, rapped sharply on my skull and told me to get my shit in order within the week. -

Easter Eggs: Hidden Tracks and Messages in Musical Mediums
Proceedings ICMC|SMC|2014 14-20 September 2014, Athens, Greece Easter Eggs: Hidden Tracks and Messages in Musical Mediums Jonathan Weinel, Darryl Griffiths and Stuart Cunningham Creative & Applied Research for the Digital Society (CARDS) Glyndŵr University Plas Coch Campus, Mold Road, Wrexham, LL11 2AW, Wales +44 1978 293070 {j.weinel | Griffiths.d | s.cunningham}@glyndwr.ac.uk ABSTRACT the programmers’ office, in the style of the video game Doom [2]. The hidden game features credits and digital ‘Easter eggs’ are hidden components that can be found in images of the programmers. It is accessed by carrying computer software and various other media including out a particular series of actions on the 95th row of a music. In this paper the concept is explained, and various blank spreadsheet upon opening Excel. examples are discussed from a variety of mediums in- cluding analogue and digital audio formats. Through this discussion, the purpose of including easter eggs in musi- cal mediums is considered. We propose that easter eggs can serve to provide comic amusement within a work, but can also serve to support the artistic message of the art- work. Concealing easter eggs in music is partly depend- ent on the properties of the chosen medium; vinyl records Figure 1. Screenshots from the ‘hall of tortured souls’, in Mi- may use techniques such as double grooves, while digital crosoft Excel 95. formats such as CD may feature hidden tracks that follow long periods of empty space. Approaches such as these This paper will consider the purpose and realisation of and others are discussed. -

Artificial Intelligence, Ovvero Suonare Il Corpo Della Macchina O Farsi Suonare? La Costruzione Dell’Identità Audiovisiva Della Warp Records
Philomusica on-line 13/2 (2014) Artificial Intelligence, ovvero suonare il corpo della macchina o farsi suonare? La costruzione dell’identità audiovisiva della Warp Records Alessandro Bratus Dipartimento di Musicologia e Beni Culturali Università di Pavia [email protected] § A partire dai tardi anni Ottanta la § Starting from the late 1980s Warp Records di Sheffield (e in seguito Sheffield (then London) based Warp Londra) ha avuto un ruolo propulsivo Records pushed forward the extent nel mutamento della musica elettronica and scope of electronic dance music popular come genere di musica che well beyond its exclusive focus on fun non si limita all’accompagna-mento del and physical enjoinment. One of the ballo e delle occasioni sociali a esso key factors in the success of the label correlate. Uno dei fattori chiave nel was the creative use of the artistic successo dell’etichetta è stato l’uso possibilities provided by technology, creativo delle possibilità artistiche which fostered the birth of a di- offerte dalla tecnologia, favorendo la stinctive audiovisual identity. In this formazione di un’identità ben ca- respect a crucial role was played by ratterizzata, in primo luogo dal punto the increasing blurred boundaries di vista audiovisivo. Sotto questo profilo between video and audio data, su- un ruolo fondamentale ha giocato la bjected to shared processes of digital possibilità di transcodifica tra dati transformation, transcoding, elabora- audio e video nell’era digitale, poten- tion and manipulation. zialmente soggetti agli stessi processi di Although Warp Records repeatedly trasformazione, elaborazione e mani- resisted the attempts to frame its polazione. artistic project within predictable Nonostante la Warp Records abbia lines, its production –especially mu- ripetutamente resistito a ogni tentativo sic videos and compilations– suggests di inquadrare il proprio progetto arti- the retrospective construction of a stico entro coordinate prevedibili, i suoi consistent imagery. -
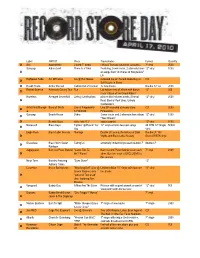
Label ARTIST Piece Tracks/Notes Format Quantity
Label ARTIST Piece Tracks/notes Format Quantity Sire Against Me! 2 song 7" single I Was A Teenage Anarchist (acoustic) 7" vinyl 2500 Sub-pop Album Leaf There Is a Wind Featuring 2 new tracks, 2 alternate takes 12" vinyl 1000 on songs from "A Chorus of Storytellers" LP Righteous Babe Ani DiFranco live @ Bull Moose recorded live on Record Store Day at CD Bull Moose in Maine Rough Trade Arthur Russell Calling Out of Context 12 new tracks Double 12" set 2000 Rocket Science Asteroids Galaxy Tour Fun Ltd edition vinyl of album with bonus 12" 250 track "Attack of the Ghost Riders" Hopeless Avenged Sevenfold Unholy Confessions picture disc includes tracks (Eternal 12" vinyl 2000 Rest, Eternal Rest (live), Unholy Confessions Artist First/Shangri- Band of Skulls Live at Fingerprints Live EP recorded at record store CD 2000 la 12/15/2009 Fingerprints Sub-pop Beach House Zebra 2 new tracks and 2 alternate from album 12" vinyl 1500 "Teen Dream" Beastie Boys white label 12" super surprise 12" vinyl 1000 Nonesuch Black Keys Tighten Up/Howlin' For 12" vinyl contains two new songs 45 RPM 12" Single 50000 You Vinyl Eagle Rock Black Label Society Skullage Double LP look at the history of Zakk Double LP 180 Wylde and Black Label Society Gram GREEN vinyl Graveface Black Moth Super Eating Us extremely limited foil pressed double LP double LP Rainbow Jagjaguwar Bon Iver/Peter Gabriel "Come Talk To Bon Iver and Peter Gabriel cover each 7" vinyl 2000 Me"/"Flume" other. Bon Iver track is EXCLUSIVE to this release Ninja Tune Bonobo featuring "Eyes -

User Manual HOFA CD-Burn.DDP.Master (Plugin) V2.0.0
User Manual HOFA CD-Burn.DDP.Master (Plugin) V2.0.0 Content Introduction .......................................................................................................................................... 3 Installation ............................................................................................................................................ 4 Activation ......................................................................................................................................... 4 Limitations of the evaluation version .............................................................................................. 4 Note for Windows XP and Vista users ............................................................................................. 4 Quick Start ............................................................................................................................................ 5 Step by step ........................................................................................................................................... 6 The Track List ....................................................................................................................................... 9 Copy time of selected marker to clipboard .................................................................................... 12 The Control Panel ............................................................................................................................... 13 Marker Edit Buttons ...................................................................................................................... -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

The Clash and Mass Media Messages from the Only Band That Matters
THE CLASH AND MASS MEDIA MESSAGES FROM THE ONLY BAND THAT MATTERS Sean Xavier Ahern A Thesis Submitted to the Graduate College of Bowling Green State University in partial fulfillment of the requirements for the degree of MASTER OF ARTS August 2012 Committee: Jeremy Wallach, Advisor Kristen Rudisill © 2012 Sean Xavier Ahern All Rights Reserved iii ABSTRACT Jeremy Wallach, Advisor This thesis analyzes the music of the British punk rock band The Clash through the use of media imagery in popular music in an effort to inform listeners of contemporary news items. I propose to look at the punk rock band The Clash not solely as a first wave English punk rock band but rather as a “news-giving” group as presented during their interview on the Tom Snyder show in 1981. I argue that the band’s use of communication metaphors and imagery in their songs and album art helped to communicate with their audience in a way that their contemporaries were unable to. Broken down into four chapters, I look at each of the major releases by the band in chronological order as they progressed from a London punk band to a globally known popular rock act. Viewing The Clash as a “news giving” punk rock band that inundated their lyrics, music videos and live performances with communication images, The Clash used their position as a popular act to inform their audience, asking them to question their surroundings and “know your rights.” iv For Pat and Zach Ahern Go Easy, Step Lightly, Stay Free. v ACKNOWLEDGMENTS This thesis would not have been possible without the help of many, many people.