What Is Unix?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated Time: 30 Min.)
Fundamentals of UNIX Lab 5.4.6 – Listing Directory Information (Estimated time: 30 min.) Objectives: • Learn to display directory and file information • Use the ls (list files) command with various options • Display hidden files • Display files and file types • Examine and interpret the results of a long file listing • List individual directories • List directories recursively Background: In this lab, the student will use the ls command, which is used to display the contents of a directory. This command will display a listing of all files and directories within the current directory or specified directory or directories. If no pathname is given as an argument, ls will display the contents of the current directory. The ls command will list any subdirectories and files that are in the current working directory if a pathname is specified. The ls command will also default to a wide listing and display only file and directory names. There are many options that can be used with the ls command, which makes this command one of the more flexible and useful UNIX commands. Command Format: ls [-option(s)] [pathname[s]] Tools / Preparation: a) Before starting this lab, the student should review Chapter 5, Section 4 – Listing Directory Contents b) The student will need the following: 1. A login user ID, for example user2, and a password assigned by their instructor. 2. A computer running the UNIX operating system with CDE. 3. Networked computers in classroom. Notes: 1 - 5 Fundamentals UNIX 2.0—-Lab 5.4.6 Copyright 2002, Cisco Systems, Inc. Use the diagram of the sample Class File system directory tree to assist with this lab. -

Application Program Interface Guide
APPLICATION PROGRAM INTERFACE GUIDE VWS-2001, VWS-2002 V WS-2001 V WS-2002 API GUIDE 24/7 TECHNICAL SUPPORT AT 1.877.877.2269 OR VISIT BLACKBOX.COM RemoteRemote Command Command Line Line Status Configure Status Client connected Enabled Monitor Client authorized Settings… Client disconnected Client authorized “C:\Program Files (x86)\Wall Control\wallctl.exe”- Active Server Telnet Command Lin — — — OK Cancel Apply Help NEED HELP? LEAVE THE TECH TO US LIVE 24/7 TABLE OF CONTENTS TECHNICAL SUPPORT 1.877.877.2269 1. INTRODUCTION ............................................................................................................................................................................. 3 1.1 API Programs ................................................................................................................................................................................................................3 1.2 Nomenclature ...............................................................................................................................................................................................................3 2. LAYOUTS ........................................................................................................................................................................................ 4 2.1 Example Usage ............................................................................................................................................................................................................4 -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -
Administering Unidata on UNIX Platforms
C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta UniData Administering UniData on UNIX Platforms UDT-720-ADMU-1 C:\Program Files\Adobe\FrameMaker8\UniData 7.2\7.2rebranded\ADMINUNIX\ADMINUNIXTITLE.fm March 5, 2010 1:34 pm Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Beta Notices Edition Publication date: July, 2008 Book number: UDT-720-ADMU-1 Product version: UniData 7.2 Copyright © Rocket Software, Inc. 1988-2010. All Rights Reserved. Trademarks The following trademarks appear in this publication: Trademark Trademark Owner Rocket Software™ Rocket Software, Inc. Dynamic Connect® Rocket Software, Inc. RedBack® Rocket Software, Inc. SystemBuilder™ Rocket Software, Inc. UniData® Rocket Software, Inc. UniVerse™ Rocket Software, Inc. U2™ Rocket Software, Inc. U2.NET™ Rocket Software, Inc. U2 Web Development Environment™ Rocket Software, Inc. wIntegrate® Rocket Software, Inc. Microsoft® .NET Microsoft Corporation Microsoft® Office Excel®, Outlook®, Word Microsoft Corporation Windows® Microsoft Corporation Windows® 7 Microsoft Corporation Windows Vista® Microsoft Corporation Java™ and all Java-based trademarks and logos Sun Microsystems, Inc. UNIX® X/Open Company Limited ii SB/XA Getting Started The above trademarks are property of the specified companies in the United States, other countries, or both. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names as designated by the companies who own or market them. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license and with the inclusion of the copyright notice. -

System Calls System Calls
System calls We will investigate several issues related to system calls. Read chapter 12 of the book Linux system call categories file management process management error handling note that these categories are loosely defined and much is behind included, e.g. communication. Why? 1 System calls File management system call hierarchy you may not see some topics as part of “file management”, e.g., sockets 2 System calls Process management system call hierarchy 3 System calls Error handling hierarchy 4 Error Handling Anything can fail! System calls are no exception Try to read a file that does not exist! Error number: errno every process contains a global variable errno errno is set to 0 when process is created when error occurs errno is set to a specific code associated with the error cause trying to open file that does not exist sets errno to 2 5 Error Handling error constants are defined in errno.h here are the first few of errno.h on OS X 10.6.4 #define EPERM 1 /* Operation not permitted */ #define ENOENT 2 /* No such file or directory */ #define ESRCH 3 /* No such process */ #define EINTR 4 /* Interrupted system call */ #define EIO 5 /* Input/output error */ #define ENXIO 6 /* Device not configured */ #define E2BIG 7 /* Argument list too long */ #define ENOEXEC 8 /* Exec format error */ #define EBADF 9 /* Bad file descriptor */ #define ECHILD 10 /* No child processes */ #define EDEADLK 11 /* Resource deadlock avoided */ 6 Error Handling common mistake for displaying errno from Linux errno man page: 7 Error Handling Description of the perror () system call. -

13-DUALOSS-MV Commercial Grade In-Wall Occupancy/Vacancy Sensor
13-DUALOSS-MV Commercial Grade In-Wall Occupancy/Vacancy Sensor APPLICATIONS This Multi-Technology Wall Switch Sensor combine advanced passive infrared (PIR) and ultrasonic technologies into one unit. The combined technologies helps eliminate false triggering even in difficult applications. Selectable operating modes allow the sensor to turn a load on, and hold it on as long as either or both technologies detect occupancy . After no movement is detected for the selected time delay, the lights switch off. A "walk-through" mode can turn lights off after only 3 minutes, if no activity is detected after 30 seconds following an occupancy detection. This sensor also contains a light level sensor. If adequate daylight is present, the sensor holds the load OFF until light levels drop, even if the area is occupied. MODEL #: 13-DUALOSS-MV FEATURES • Integrated PIR and Ultrasonic sensor technology to detect very fine COVERAGE AREA motion and provide accurate motion sensing Top View • Allows to choose triggering when both technologies detect motion or when only PIR detects motion 20' • Less false trigger, fast ON/OFF; commercial grade sensor for closet, garage, hotels, meeting room, work places 10' • Adjustable timeout from 15 seconds to 30 minutes; Walk-Through mode: 3 minutes if no activity after first 30 seconds SPECIFICATIONS 10' • Voltage: 120/277VAC, 50/60Hz • Incandescent: 800W-120VAC, 50/60Hz • Fluorescent: 800VA-120VAC, 1600VA-277VAC, 50/60Hz 20' • Resistive: 800W-120VAC, 50/60Hz • Motor: 1/4 HP-120VAC, 50/60Hz • Adjustment Time Delay: 5 Sec to 30 Mins 5' • Walk-Through Mode: 3-minutes if no activity after 30 sec. -

PS TEXT EDIT Reference Manual Is Designed to Give You a Complete Is About Overview of TEDIT
Information Management Technology Library PS TEXT EDIT™ Reference Manual Abstract This manual describes PS TEXT EDIT, a multi-screen block mode text editor. It provides a complete overview of the product and instructions for using each command. Part Number 058059 Tandem Computers Incorporated Document History Edition Part Number Product Version OS Version Date First Edition 82550 A00 TEDIT B20 GUARDIAN 90 B20 October 1985 (Preliminary) Second Edition 82550 B00 TEDIT B30 GUARDIAN 90 B30 April 1986 Update 1 82242 TEDIT C00 GUARDIAN 90 C00 November 1987 Third Edition 058059 TEDIT C00 GUARDIAN 90 C00 July 1991 Note The second edition of this manual was reformatted in July 1991; no changes were made to the manual’s content at that time. New editions incorporate any updates issued since the previous edition. Copyright All rights reserved. No part of this document may be reproduced in any form, including photocopying or translation to another language, without the prior written consent of Tandem Computers Incorporated. Copyright 1991 Tandem Computers Incorporated. Contents What This Book Is About xvii Who Should Use This Book xvii How to Use This Book xvii Where to Go for More Information xix What’s New in This Update xx Section 1 Introduction to TEDIT What Is PS TEXT EDIT? 1-1 TEDIT Features 1-1 TEDIT Commands 1-2 Using TEDIT Commands 1-3 Terminals and TEDIT 1-3 Starting TEDIT 1-4 Section 2 TEDIT Topics Overview 2-1 Understanding Syntax 2-2 Note About the Examples in This Book 2-3 BALANCED-EXPRESSION 2-5 CHARACTER 2-9 058059 Tandem Computers -

Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO
Filesystems HOWTO Filesystems HOWTO Table of Contents Filesystems HOWTO..........................................................................................................................................1 Martin Hinner < [email protected]>, http://martin.hinner.info............................................................1 1. Introduction..........................................................................................................................................1 2. Volumes...............................................................................................................................................1 3. DOS FAT 12/16/32, VFAT.................................................................................................................2 4. High Performance FileSystem (HPFS)................................................................................................2 5. New Technology FileSystem (NTFS).................................................................................................2 6. Extended filesystems (Ext, Ext2, Ext3)...............................................................................................2 7. Macintosh Hierarchical Filesystem − HFS..........................................................................................3 8. ISO 9660 − CD−ROM filesystem.......................................................................................................3 9. Other filesystems.................................................................................................................................3 -

Unix for Newbies from Duane A
Content borrowed and updated (with permission) Unix for Newbies from Duane A. Bailey’s guidelines from 2007. Getting help on unix: Some Tips To Make Your UNIX Life More Reasonable man <command-name>!!Get full description of command man -k <keyword>!! ! List command mentioning keyword in title 0. Walk away from the machine. If you’re not making progress, don’t waste time banging your head (literally or Logging in and out of a system: figuratively) against the machine. Save your files, print the buggy output, or logout!!!!Terminate session create a backup and walk away. Find someone to talk to about something else. Your exit!!!!Terminate current “shell” mind will work on the problem while you go get a snack and take a break. ssh <username>@<remote host>!Login securely as username to remote host 1. Read man pages. File Manipulation: Realize that you don’t know everything. Take the time to learn how man pages are emacs <file>!!!Edit a text file (See the emacs cheatsheet) structured and what they can teach you. You find answers to many questions on the mv <old> <new>!!!Move or rename <old> file as <new> file internet, but you learn even more by finding and reading the man pages. Better, rm <file(s)>!!!Delete file(s) from filesystem you learn elegant solutions to questions you didn’t think to ask. cp <orig> <duplicate>!!Copy <orig> to file named <duplicate> sftp <remote host>!!Secure batch file transfers between machines 2. Learn the emacs keystrokes. scp host:<orig> host:<dub>!Securely transfer files between machines It will save you time when you work on a machine whose mouse or arrow keys aren’t cat <file>!!!Display or catenate file contents to screen working, and the keystrokes often work in other editors. -
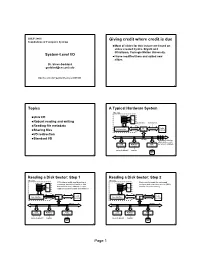
System-Level I/O I Have Modified Them and Added New Slides
JDEP 284H Giving credit where credit is due Foundations of Computer Systems Most of slides for this lecture are based on slides created by Drs. Bryant and O’Hallaron, Carnegie Mellon University. System-Level I/O I have modified them and added new slides. Dr. Steve Goddard [email protected] http://cse.unl.edu/~goddard/Courses/JDEP284 2 Topics A Typical Hardware System CPU chip register file Unix I/O ALU Robust reading and writing system bus memory bus Reading file metadata I/O main bus interface Sharing files bridge memory I/O redirection Standard I/O I/O bus Expansion slots for other devices such USB graphics disk as network adapters. controller adapter controller mouse keyboard monitor disk 3 4 Reading a Disk Sector: Step 1 Reading a Disk Sector: Step 2 CPU chip CPU chip CPU initiates a disk read by writing a Disk controller reads the sector and register file command, logical block number, and register file performs a direct memory access (DMA) destination memory address to a port transfer into main memory. ALU ALU (address) associated with disk controller. main main bus interface bus interface memory memory I/O bus I/O bus USB graphics disk USB graphics disk controller adapter controller controller adapter controller mouse keyboard monitor mouse keyboard monitor disk disk 5 6 Page 1 Reading a Disk Sector: Step 3 Unix Files CPU chip When the DMA transfer completes, the register file disk controller notifies the CPU with an A Unix file is a sequence of m bytes: interrupt (i.e., asserts a special “interrupt” B , B , ... -

The Intercal Programming Language Revised Reference Manual
THE INTERCAL PROGRAMMING LANGUAGE REVISED REFERENCE MANUAL Donald R. Woods and James M. Lyon C-INTERCAL revisions: Louis Howell and Eric S. Raymond Copyright (C) 1973 by Donald R. Woods and James M. Lyon Copyright (C) 1996 by Eric S. Raymond Redistribution encouragedunder GPL (This version distributed with C-INTERCAL 0.15) -1- 1. INTRODUCTION The names you are about to ignore are true. However, the story has been changed significantly.Any resemblance of the programming language portrayed here to other programming languages, living or dead, is purely coincidental. 1.1 Origin and Purpose The INTERCAL programming language was designed the morning of May 26, 1972 by Donald R. Woods and James M. Lyon, at Princeton University.Exactly when in the morning will become apparent in the course of this manual. Eighteen years later (give ortakeafew months) Eric S. Raymond perpetrated a UNIX-hosted INTERCAL compiler as a weekend hack. The C-INTERCAL implementation has since been maintained and extended by an international community of technomasochists, including Louis Howell, Steve Swales, Michael Ernst, and Brian Raiter. (There was evidently an Atari implementation sometime between these two; notes on it got appended to the INTERCAL-72 manual. The culprits have sensibly declined to identify themselves.) INTERCAL was inspired by one ambition: to have a compiler language which has nothing at all in common with anyother major language. By ’major’ was meant anything with which the authors were at all familiar,e.g., FORTRAN, BASIC, COBOL, ALGOL, SNOBOL, SPITBOL, FOCAL, SOLVE, TEACH, APL, LISP,and PL/I. For the most part, INTERCAL has remained true to this goal, sharing only the basic elements such as variables, arrays, and the ability to do I/O, and eschewing all conventional operations other than the assignment statement (FORTRAN "="). -

After the Wall: the Legal Ramifications of the East German Border Guard Trials in Unified Germany Micah Goodman
Cornell International Law Journal Volume 29 Article 3 Issue 3 1996 After the Wall: The Legal Ramifications of the East German Border Guard Trials in Unified Germany Micah Goodman Follow this and additional works at: http://scholarship.law.cornell.edu/cilj Part of the Law Commons Recommended Citation Goodman, Micah (1996) "After the Wall: The Legal Ramifications of the East German Border Guard Trials in Unified Germany," Cornell International Law Journal: Vol. 29: Iss. 3, Article 3. Available at: http://scholarship.law.cornell.edu/cilj/vol29/iss3/3 This Note is brought to you for free and open access by Scholarship@Cornell Law: A Digital Repository. It has been accepted for inclusion in Cornell International Law Journal by an authorized administrator of Scholarship@Cornell Law: A Digital Repository. For more information, please contact [email protected]. NOTES After the Wall: The Legal Ramifications of the East German Border Guard Trials in Unified Germany Micah Goodman* Introduction Since the reunification of East and West Germany in 1990, the German government' has tried over fifty2 former East German soldiers for shooting and killing East German citizens who attempted to escape across the East- West German border.3 The government has also indicted a dozen high- ranking East German government officials.4 The German government charged and briefly tried Erich Honecker, the leader of the German Demo- cratic Republic (G.D.R.) from 1971 to 1989, for giving the orders to shoot escaping defectors. 5 While on guard duty at the border between the two * Associate, Rogers & Wells; J.D., Cornell Law School, 1996; B.A., Swarthmore College, 1991.