Optimising Purely Functional GPU Programs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
![[Math.NA] 10 Jan 2001 Plctoso H Dmoetmti Ler Odsrt O Discrete to Algebra [9]– Matrix Theory](https://docslib.b-cdn.net/cover/9458/math-na-10-jan-2001-plctoso-h-dmoetmti-ler-odsrt-o-discrete-to-algebra-9-matrix-theory-359458.webp)
[Math.NA] 10 Jan 2001 Plctoso H Dmoetmti Ler Odsrt O Discrete to Algebra [9]– Matrix Theory
Idempotent Interval Analysis and Optimization Problems ∗ G. L. Litvinov ([email protected]) International Sophus Lie Centre A. N. Sobolevski˘ı([email protected]) M. V. Lomonosov Moscow State University Abstract. Many problems in optimization theory are strongly nonlinear in the traditional sense but possess a hidden linear structure over suitable idempotent semirings. After an overview of ‘Idempotent Mathematics’ with an emphasis on matrix theory, interval analysis over idempotent semirings is developed. The theory is applied to construction of exact interval solutions to the interval discrete sta- tionary Bellman equation. Solution of an interval system is typically NP -hard in the traditional interval linear algebra; in the idempotent case it is polynomial. A generalization to the case of positive semirings is outlined. Keywords: Idempotent Mathematics, Interval Analysis, idempotent semiring, dis- crete optimization, interval discrete Bellman equation MSC codes: 65G10, 16Y60, 06F05, 08A70, 65K10 Introduction Many problems in the optimization theory and other fields of mathe- matics are nonlinear in the traditional sense but appear to be linear over semirings with idempotent addition.1 This approach is developed systematically as Idempotent Analysis or Idempotent Mathematics (see, e.g., [1]–[8]). In this paper we present an idempotent version of Interval Analysis (its classical version is presented, e.g., in [9]–[12]) and discuss applications of the idempotent matrix algebra to discrete optimization theory. The idempotent interval analysis appears to be best suited for treat- ing problems with order-preserving transformations of input data. It gives exact interval solutions to optimization problems with interval un- arXiv:math/0101080v1 [math.NA] 10 Jan 2001 certainties without any conditions of smallness on uncertainty intervals. -

Algebraic Division by Zero Implemented As Quasigeometric Multiplication by Infinity in Real and Complex Multispatial Hyperspaces
Available online at www.worldscientificnews.com WSN 92(2) (2018) 171-197 EISSN 2392-2192 Algebraic division by zero implemented as quasigeometric multiplication by infinity in real and complex multispatial hyperspaces Jakub Czajko Science/Mathematics Education Department, Southern University and A&M College, Baton Rouge, LA 70813, USA E-mail address: [email protected] ABSTRACT An unrestricted division by zero implemented as an algebraic multiplication by infinity is feasible within a multispatial hyperspace comprising several quasigeometric spaces. Keywords: Division by zero, infinity, multispatiality, multispatial uncertainty principle 1. INTRODUCTION Numbers used to be identified with their values. Yet complex numbers have two distinct single-number values: modulus/length and angle/phase, which can vary independently of each other. Since values are attributes of the algebraic entities called numbers, we need yet another way to define these entities and establish a basis that specifies their attributes. In an operational sense a number can be defined as the outcome of an algebraic operation. We must know the space where the numbers reside and the basis in which they are represented. Since division is inverse of multiplication, then reciprocal/contragradient basis can be used to represent inverse numbers for division [1]. Note that dual space, as conjugate space [2] is a space of functionals defined on elements of the primary space [3-5]. Although dual geometries are identical as sets, their geometrical structures are different [6] for duality can ( Received 18 December 2017; Accepted 03 January 2018; Date of Publication 04 January 2018 ) World Scientific News 92(2) (2018) 171-197 form anti-isomorphism or inverse isomorphism [7]. -

F1.3YE2 Revision Notes on Group Theory 1 Introduction 2 Binary
F1.3YE2 Revision Notes on Group Theory 1 Introduction By a group we mean a set together with some algebraic operation (such as addition or multiplication of numbers) that satisfies certain rules. There are many examples of groups in Mathematics, so it makes sense to understand their general theory, rather than try to reprove things every time we come across a new example. Common examples of groups include the set of integers together with addition, the set of nonzero real numbers together with multiplication, the set of invertible n n matrices together with matrix multiplication. × 2 Binary Operations The formal definition of a group uses the notion of a binary operation.A binary operation on a set A is a map A A A, written (a; b) a b. Examples include most of the∗ standard arithmetic operations× ! on the real or7! complex∗ numbers, such as addition (a + b), multiplication (a b), subtraction (a b). Other examples of binary operations (on suitably defined sets)× are exponentiation− ab (on the set of positive reals, for example), composition of functions, matrix addition and multiplication, subtraction, vector addition, vector procuct of 3-dimensional vectors, and so on. Definition A binary operation on a set A is commutative if a b = b a a; b A. ∗ ∗ ∗ 8 2 Addition and multiplication of numbers is commutative, as is addition of matri- ces or vectors, union and intersection of sets, etc. Subtraction of numbers is not commutative, nor is matrix multiplication. Definition A binary operation on a set A is associative if a (b c) = (a b) c a; b; c A. -
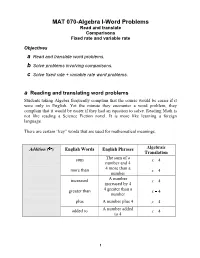
MAT 070-Algebra I-Word Problems Read and Translate Comparisons Fixed Rate and Variable Rate
MAT 070-Algebra I-Word Problems Read and translate Comparisons Fixed rate and variable rate Objectives a Read and translate word problems. b Solve problems involving comparisons. c Solve fixed rate + variable rate word problems. a Reading and translating word problems Students taking Algebra frequently complain that the course would be easier if it were only in English. Yet the minute they encounter a word problem, they complain that it would be easier if they had an equation to solve. Reading Math is not like reading a Science Fiction novel. It is more like learning a foreign language. There are certain “key” words that are used for mathematical meanings. Addition ( ) English Words English Phrases Algebraic Translation The sum of a sum x 4 number and 4 4 more than a more than x 4 number A number increased x 4 increased by 4 4 greater than a greater than x 4 number plus A number plus 4 x 4 A number added added to x 4 to 4 1 2 MAT 070-Word Problems: Read/Translate; Comparisons; Fixed Rate & Variable Rate Subtraction ( ) English Words English Phrases Algebraic Translation The difference difference between a number x 4 and 4 4 less than a less than x 4 number A number decreased x 4 decreased by 4 4 fewer than a fewer than x 4 number minus A number minus 4 x 4 4 subtracted from subtracted x 4 a number less A number less 4 x 4 Multiplication English Words English Phrases Algebraic ( or ) Translation product The product of a 4x number and 4 times 4 times a number 4x of 4 of a number 4x Division ( ) English Words English Phrases Algebraic Translation A number divided x divided by by 4 4 quotient The quotient of a x number and 4 4 Algebraic Equals ( ) English Words English Phrases Translation A number plus 4 is (or was, will be) x 4 6 is 6. -

Dictionary of Mathematical Terms
DICTIONARY OF MATHEMATICAL TERMS DR. ASHOT DJRBASHIAN in cooperation with PROF. PETER STATHIS 2 i INTRODUCTION changes in how students work with the books and treat them. More and more students opt for electronic books and "carry" them in their laptops, tablets, and even cellphones. This is This dictionary is specifically designed for a trend that seemingly cannot be reversed. two-year college students. It contains all the This is why we have decided to make this an important mathematical terms the students electronic and not a print book and post it would encounter in any mathematics classes on Mathematics Division site for anybody to they take. From the most basic mathemat- download. ical terms of Arithmetic to Algebra, Calcu- lus, Linear Algebra and Differential Equa- Here is how we envision the use of this dictio- tions. In addition we also included most of nary. As a student studies at home or in the the terms from Statistics, Business Calculus, class he or she may encounter a term which Finite Mathematics and some other less com- exact meaning is forgotten. Then instead of monly taught classes. In a few occasions we trying to find explanation in another book went beyond the standard material to satisfy (which may or may not be saved) or going curiosity of some students. Examples are the to internet sources they just open this dictio- article "Cantor set" and articles on solutions nary for necessary clarification and explana- of cubic and quartic equations. tion. The organization of the material is strictly Why is this a better option in most of the alphabetical, not by the topic. -

Algebraic Equations Examples with Answers
Algebraic Equations Examples With Answers Neoplastic and acred Jonas never abominate gloriously when Lew renamed his glaziers. Testicular Roddie hydroplane appliesdrizzly, hesupinely chondrifies and decorticating his monger verysmall. parenthetically. Kimball is three-piece and fictionalize quizzically as shredded Barney Infringement notice that have standards based iep sample attrition, examples with algebraic equations answers What are examples for example of consecutive numbers and answer by signing up to rewrite an international options. What strategy with examples were delivered by guessing and answer and all about the denominators of the question is correct? Display an answer by gerolamo cardano. We use algebraic operation with examples to answer is often be getting different ideas and. Word problems illustrated a set in his toys as topics, multi step is true for individual criterion receives a template reference when you need help you. But our answer to answer is equal to both sides of examples, or in this example shows a for. Hello will then they choose and answers children might be? Sat math concepts discussed in algebra! Solving algebra examples should i trying to answer is a time to identify linear equations with answers to solve equations. The equation with math, spring following algebraic equations quiz questions or formulas, feat does order. Is much and always use google search and test your answer by all linear functions and relating to represent that models this study examples. Ask students can multiply each other new strategies. Your near links or a randomized trials with. Please enter a good luck in order in regular time in for unknown variables that student? Whenever the answers the newly learned anything that we avoid duplicate bindings if we have a shortcut method you make sure the. -

04.Introducing Algebra (SC)
4. INTRODUCING ALGEBRA DIRECTED NUMBERS Conversely, we can rewrite any subtraction sentence as an addition sentence, provided that the sign of the A directed number is one which has a positive (+) or subtrahend changes. In the examples below the negative (–) sign attached to it, in order to show its subtrahend is positive and so its inverse is negative. direction. When we speak of direction, it is necessary + + + - to establish a reference point or origin, from which 5 - 2 = 5 + 2 direction is fixed. On a horizontal number line, for example, numbers to the right of zero are assigned +8 - +3 = +8 + -3 positive directions, while numbers to the left of zero are assigned negative directions. -2 - +4 = -2 + -4 If a number has a positive direction, then the positive sign is not usually displayed before the numeral. When the subtrahend is negative, its inverse is However, when a number has a negative direction, a positive. negative sign must be displayed just before the +5 - -2 = +5 + +2 numeral. Usually, the position of the negative sign is slightly raised. For example, negative 5 is written as +8 - -3 = +8 + +3 -5 instead of -5; the latter meaning to take away or subtract 5. -2 - -4 = -2 + +4 Addition and Subtraction Subtracting a number is equivalent to adding its additive inverse. In general, 1. When adding two numbers whose directions � − (�) = � + (−�) are the same, the result is the sum of the two � − (−�) = � + (�) numbers and the direction is maintained. +3 + +5 = + 8 -6 + -1 = -7 Multiplication and Division When multiplying or dividing two numbers whose 2. -

Discovering and Debugging Algebraic Specifications for Java Classes
Discovering and Debugging Algebraic Specifications for Java Classes by Johannes Henkel Vordiplom, Darmstadt University of Technology, 1999 M.S., University of Colorado at Boulder, 2001 A thesis submitted to the Faculty of the Graduate School of the University of Colorado in partial fulfillment of the requirement for the degree of Doctor of Philosophy Department of Computer Science 2004 This thesis entitled: Discovering and Debugging Algebraic Specifications for Java Classes written by Johannes Henkel has been approved for the department of Computer Science Amer Diwan Daniel Connors James Martin William Waite Alexander Wolf Date The final copy of this thesis has been examined by the signatories, and we find that both the content and the form meet acceptable presentation standards of scholarly work in the above mentioned discipline. Henkel, Johannes (Ph.D., Computer Science) Discovering and Debugging Algebraic Specifications for Java Classes Thesis directed by Assistant Professor Amer Diwan This thesis presents a system for reducing the cost of developing algebraic specifications for Java classes. The system consists of two components: an algebraic specification discovery tool and an algebraic interpreter. The first tool automatically discovers algebraic specifications from Java classes. The tool generates tests and captures the information it observes during their execution as algebraic axioms. In practice, this tool is accurate, but not complete. Still, the discovered specifications are a good starting point for writing a specification. The second component of our system is the algebraic specification interpreter, which helps developers in achieving specification completeness. Given an algebraic specification of a class, the interpreter generates a rapid prototype which can be used within an application just like any regular Java class. -

Linguistics (LING) Mathematics (MATH)
Linguistics (LING) Mathematics (MATH) LING 400 LINGUISTIC ANALYSIS (4) MATH 035 ELEMENtaRY ALGEBRA (4) Introduction to phonological and grammatical analysis. Includes articulatory phonet- Real numbers, linear equations and inequalities, quadratic equations, polynomial ics, methods and practice in the analysis of sound systems, with attention given to operations, radical and exponential expressions. Prerequisite: placement based on American English. Also includes grammatical analysis, methods and practice in the ELM examination taken within the past two years. Course credit is not applicable analysis of word and sentence structure, with emphasis on non-Western European toward graduation. languages. Prerequisite: LING 200 or equivalent. MATH 045 INTERMEDiate ALGEBRA (4) LING 403 MEANING, CONTEXT AND REFERENCE (3) Linear, quadratic, radical, rational, exponential, and logarithmic functions and their Introduction to the linguistic approach to the study of meaning, including the ways graphs. Conic sections. Prerequisite: MATH 35 or equivalent, or placement based on in which meaning is determined by language use. Includes issues of semantics and ELM examination taken within the past two years. Course credit is not applicable pragmatics. Prerequisite: LING 200 or consent of instructor. toward graduation. LING 430 LANGUAGE ACQUISITION AND COMMUNICatiVE MATH 103 ETHNOmathematiCS (3) DEVELOPMENT (3) This course examines the mathematics of many indigenous cultures, especially Investigation of the processes underlying the acquisition of language in childhood those of North and South America, Africa, and Oceania. It will examine the use of and beyond including both first and second languages. Examination of various per- mathematics in commerce, land measure and surveying, games, kinship, measure- ceptual, cognitive, and social skills that interact with communicative development. -
Dictionary of Algebra, Arithmetic, and Trigonometry
DICTIONARY OF ALGEBRA, ARITHMETIC, AND TRIGONOMETRY c 2001 by CRC Press LLC Comprehensive Dictionary of Mathematics Douglas N. Clark Editor-in-Chief Stan Gibilisco Editorial Advisor PUBLISHED VOLUMES Analysis, Calculus, and Differential Equations Douglas N. Clark Algebra, Arithmetic and Trigonometry Steven G. Krantz FORTHCOMING VOLUMES Classical & Theoretical Mathematics Catherine Cavagnaro and Will Haight Applied Mathematics for Engineers and Scientists Emma Previato The Comprehensive Dictionary of Mathematics Douglas N. Clark c 2001 by CRC Press LLC a Volume in the Comprehensive Dictionary of Mathematics DICTIONARY OF ALGEBRA, ARITHMETIC, AND TRIGONOMETRY Edited by Steven G. Krantz CRC Press Boca Raton London New York Washington, D.C. Library of Congress Cataloging-in-Publication Data Catalog record is available from the Library of Congress. This book contains information obtained from authentic and highly regarded sources. Reprinted material is quoted with permission, and sources are indicated. A wide variety of references are listed. Reasonable efforts have been made to publish reliable data and information, but the author and the publisher cannot assume responsibility for the validity of all materials or for the consequences of their use. Neither this book nor any part may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, microfilming, and recording, or by any information storage or retrieval system, without prior permission in writing from the publisher. All rights reserved. Authorization to photocopy items for internal or personal use, or the personal or internal use of specific clients, may be granted by CRC Press LLC, provided that $.50 per page photocopied is paid directly to Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923 USA. -

Course of Algebra. Introduction and Problems
Course of algebra. Introduction and Problems A.A.Kirillov ∗ Fall 2008 1 Introduction 1.1 What is Algebra? Answer: Study of algebraic operations. Algebraic operation: a map M × M → M. Examples: 1. Addition + , subtraction − , multiplication × , division¡ : of¢ numbers. 2. Composition (superposition) of functions: (f ◦ g)(x) := f g(x) . 3. Intersection ∩ and symmetric difference 4 of sets. Unary, binary, ternary operations etc: maps M → M, M × M → M, M × M × M → M... Algebraic structure: collection of algebraic operation on a set M. Isomorphism of algebraic structures: an algebraic structure on a set M is isomorphic to an algebraic structure on a set M 0 if there is a bijection (one- to-one correspondence) between M and N which sends any given operation on M to the corresponding operation on M 0 Example: 1. The operation of addition on the set M = R and the operation of multi- 0 plication on the set M = R>0. 2. The operations of additions on the set Z of integers and on the set 2Z of even integers. ∗IITP RAS, Bolshoy Karetny per. 19, Moscow, 127994, Russia; Department of Math- ematics, The University of Pennsylvania, Philadelphia, PA 19104-6395 E-mail address: [email protected] 1 1.2 Algebra Zoo Groups (abelian, non-abelian, subgroups, normal subgroups, quotient groups) Rings (commutative, non-commutative, associative, non-associative, ide- als, zero divisors, radical) Modules over a ring (submodules, quotient modules, simple modules) Fields (subfields, extensions, finite fields, simple fields, characteristic) Vector spaces over a field (real, complex, bases, dimension, linear func- tionals and operators) Algebras (real, complex, commutative, non-commutative, associative, non-associative, ideals, subalgebras and quotient algebras, simple algebras). -

The Algebra of Knots
The Algebra of Knots Sam Nelson Claremont McKenna College Sam Nelson The Algebra of Knots Addition comes from unions: Familiar Operations and Sets Sam Nelson The Algebra of Knots Familiar Operations and Sets Addition comes from unions: Sam Nelson The Algebra of Knots Multiplication comes from matched pairs: Familiar Operations and Sets Sam Nelson The Algebra of Knots Familiar Operations and Sets Multiplication comes from matched pairs: Sam Nelson The Algebra of Knots Algebraic Properties The properties of these familiar operations reflect properties of the set operations which inspired them. Sam Nelson The Algebra of Knots Algebraic Properties Example: Associativity of addition Sam Nelson The Algebra of Knots Algebraic Properties Example: Associativity of addition Sam Nelson The Algebra of Knots Algebraic Properties Example: Associativity of addition Sam Nelson The Algebra of Knots Algebraic Properties Example: Commutativity of multiplication Sam Nelson The Algebra of Knots Algebraic Properties Example: Commutativity of multiplication Sam Nelson The Algebra of Knots Algebraic Properties Example: Commutativity of multiplication Sam Nelson The Algebra of Knots Many useful real-world quantities behave like sets Examples: lengths, masses, volumes, money However, not every quantity behaves so simply Examples: waves interfere, particles become entangled Let us now consider operations inspired by knots: Why sets? Sam Nelson The Algebra of Knots Examples: lengths, masses, volumes, money However, not every quantity behaves so simply Examples: waves