Powershell Commands
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Word Processing Tool
WORD PROCESSING 3 TOOL Objectives I like the computer because it keeps giving you After completing this Chapter, the options. What if I do this? You try it, and if you student will be able to: don't like it you undo it. The original can always be resurrected. It raises the idea of working on • work with any word processing program, one painting your whole life, saving it and working on it again and again. • create, save and open a Elliott Green document using a word Research Associate and Tutorial Fellow, Oxford University processor, • format a document inserting bullets/numbering, tables, pictures, etc., Introduction • set custom tabs and apply styles, We have to submit a project as part of our course • prepare a document for printing, evaluation. We will perhaps take a chart paper • enhance the features of the and design the project, write a report and submit document inserting graphics, it to our teacher. That’s the way we have done it tables, pictures, charts, etc., and all along? Have we ever thought of typing the entire using different formatting styles, project report using a computer and submitting it • modify document using various in a nicely designed printed form? Ever reflected editing and formatting features on getting information from the Internet and within or across documents, presenting it neatly for the project? Now that’s • produce documents for various the way things are being done! And if we are already purposes and thinking of it, it’s time to discover some document creation software, i.e., word processing tool to get • apply mail merge facility to send a document to different the job done. -

Operator Overloading ______
Chapter 10: Operator Overloading _________________________________________________________________________________________________________ Consider the following C++ code snippet: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; Here, we create a vector<string> of a certain size, then iterate over it concatenating “Now longer!” to each of the strings. Code like this is ubiquitous in C++, and initially does not appear all that exciting. However, let's take a closer look at how this code is structured. First, let's look at exactly what operations we're performing on the iterator: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; In this simple piece of code, we're comparing the iterator against myVector.end() using the != operator, incrementing the iterator with the ++ operator, and dereferencing the iterator with the * operator. At a high level, this doesn't seem all that out of the ordinary, since STL iterators are designed to look like regular pointers and these operators are all well-defined on pointers. But the key thing to notice is that STL iterators aren't pointers, they're objects, and !=, *, and ++ aren't normally defined on objects. We can't write code like ++myVector or *myMap = 137, so why can these operations be applied to vector<string>::iterator? Similarly, notice how we're concatenating the string “Now longer!” onto the end of the string: vector<string> myVector(kNumStrings); for(vector<string>::iterator itr = myVector.begin(); itr != myVector.end(); ++itr) *itr += "Now longer!"; Despite the fact that string is an object, somehow C++ “knows” what it means to apply += to strings. -
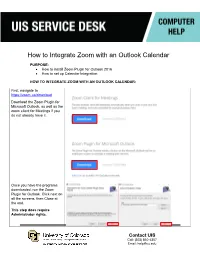
How to Integrate Zoom with an Outlook Calendar
How to Integrate Zoom with an Outlook Calendar PURPOSE: • How to install Zoom Plugin for Outlook 2016 • How to set up Calendar Integration HOW TO INTEGRATE ZOOM WITH AN OUTLOOK CALENDAR: First, navigate to https://zoom.us/download Download the Zoom Plugin for Microsoft Outlook, as well as the zoom client for Meetings if you do not already have it. Once you have the programs downloaded, run the Zoom Plugin for Outlook. Click next on all the screens, then Close at the end. This step does require Administrator rights. Contact UIS Call: (303) 860-4357 Email: [email protected] Restart Outlook, then you will see it in the top menu. Next, navigate to https://cusystem.zoom.us, choose SSO and login with your CU credentials Contact UIS Call: (303) 860-4357 Email: [email protected] On the left side, choose My Meeting Settings Under My Meeting Settings, scroll down until you find Calendar Integration. Click the toggle on the right side. Under Calendar Integration, for the Exchange login username or UPN enter your CU username followed by @ad.cu.edu. Under password, enter your CU password. For Exchange version, select Exchange 2013. In the EWS URL, enter https://exchange.cu.edu/ EWS/Exchange.asmx After that, click Authorize and you should be set! Keep in mind this isn’t a perfect integration, it will only create new meetings for meetings created after this has been done, and changing or deleting meetings will not necessarily reflect in Outlook. The Zoom desktop client will be the best place to check for updated meetings. -

Attacker Antics Illustrations of Ingenuity
ATTACKER ANTICS ILLUSTRATIONS OF INGENUITY Bart Inglot and Vincent Wong FIRST CONFERENCE 2018 2 Bart Inglot ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Rock Climber ◆ Globetrotter ▶ From Poland but live in Singapore ▶ Spent 1 year in Brazil and 8 years in the UK ▶ Learning French… poor effort! ◆ Twitter: @bartinglot ©2018 FireEye | Private & Confidential 3 Vincent Wong ◆ Principal Consultant at Mandiant ◆ Incident Responder ◆ Baby Sitter ◆ 3 years in Singapore ◆ Grew up in Australia ©2018 FireEye | Private & Confidential 4 Disclosure Statement “ Case studies and examples are drawn from our experiences and activities working for a variety of customers, and do not represent our work for any one customer or set of customers. In many cases, facts have been changed to obscure the identity of our customers and individuals associated with our customers. ” ©2018 FireEye | Private & Confidential 5 Today’s Tales 1. AV Server Gone Bad 2. Stealing Secrets From An Air-Gapped Network 3. A Backdoor That Uses DNS for C2 4. Hidden Comment That Can Haunt You 5. A Little Known Persistence Technique 6. Securing Corporate Email is Tricky 7. Hiding in Plain Sight 8. Rewriting Import Table 9. Dastardly Diabolical Evil (aka DDE) ©2018 FireEye | Private & Confidential 6 AV SERVER GONE BAD Cobalt Strike, PowerShell & McAfee ePO (1/9) 7 AV Server Gone Bad – Background ◆ Attackers used Cobalt Strike (along with other malware) ◆ Easily recognisable IOCs when recorded by Windows Event Logs ▶ Random service name – also seen with Metasploit ▶ Base64-encoded script, “%COMSPEC%” and “powershell.exe” ▶ Decoding the script yields additional PowerShell script with a base64-encoded GZIP stream that in turn contained a base64-encoded Cobalt Strike “Beacon” payload. -

Powershell Integration with Vmware View 5.0
PowerShell Integration with VMware® View™ 5.0 TECHNICAL WHITE PAPER PowerShell Integration with VMware View 5.0 Table of Contents Introduction . 3 VMware View. 3 Windows PowerShell . 3 Architecture . 4 Cmdlet dll. 4 Communication with Broker . 4 VMware View PowerCLI Integration . 5 VMware View PowerCLI Prerequisites . 5 Using VMware View PowerCLI . 5 VMware View PowerCLI cmdlets . 6 vSphere PowerCLI Integration . 7 Examples of VMware View PowerCLI and VMware vSphere PowerCLI Integration . 7 Passing VMs from Get-VM to VMware View PowerCLI cmdlets . 7 Registering a vCenter Server . .. 7 Using Other VMware vSphere Objects . 7 Advanced Usage . 7 Integrating VMware View PowerCLI into Your Own Scripts . 8 Scheduling PowerShell Scripts . 8 Workflow with VMware View PowerCLI and VMware vSphere PowerCLI . 9 Sample Scripts . 10 Add or Remove Datastores in Automatic Pools . 10 Add or Remove Virtual Machines . 11 Inventory Path Manipulation . 15 Poll Pool Usage . 16 Basic Troubleshooting . 18 About the Authors . 18 TECHNICAL WHITE PAPER / 2 PowerShell Integration with VMware View 5.0 Introduction VMware View VMware® View™ is a best-in-class enterprise desktop virtualization platform. VMware View separates the personal desktop environment from the physical system by moving desktops to a datacenter, where users can access them using a client-server computing model. VMware View delivers a rich set of features required for any enterprise deployment by providing a robust platform for hosting virtual desktops from VMware vSphere™. Windows PowerShell Windows PowerShell is Microsoft’s command line shell and scripting language. PowerShell is built on the Microsoft .NET Framework and helps in system administration. By providing full access to COM (Component Object Model) and WMI (Windows Management Instrumentation), PowerShell enables administrators to perform administrative tasks on both local and remote Windows systems. -

Run-Commands-Windows-10.Pdf
Run Commands Windows 10 by Bettertechtips.com Command Action Command Action documents Open Documents Folder devicepairingwizard Device Pairing Wizard videos Open Videos Folder msdt Diagnostics Troubleshooting Wizard downloads Open Downloads Folder tabcal Digitizer Calibration Tool favorites Open Favorites Folder dxdiag DirectX Diagnostic Tool recent Open Recent Folder cleanmgr Disk Cleanup pictures Open Pictures Folder dfrgui Optimie Drive devicepairingwizard Add a new Device diskmgmt.msc Disk Management winver About Windows dialog dpiscaling Display Setting hdwwiz Add Hardware Wizard dccw Display Color Calibration netplwiz User Accounts verifier Driver Verifier Manager azman.msc Authorization Manager utilman Ease of Access Center sdclt Backup and Restore rekeywiz Encryption File System Wizard fsquirt fsquirt eventvwr.msc Event Viewer calc Calculator fxscover Fax Cover Page Editor certmgr.msc Certificates sigverif File Signature Verification systempropertiesperformance Performance Options joy.cpl Game Controllers printui Printer User Interface iexpress IExpress Wizard charmap Character Map iexplore Internet Explorer cttune ClearType text Tuner inetcpl.cpl Internet Properties colorcpl Color Management iscsicpl iSCSI Initiator Configuration Tool cmd Command Prompt lpksetup Language Pack Installer comexp.msc Component Services gpedit.msc Local Group Policy Editor compmgmt.msc Computer Management secpol.msc Local Security Policy: displayswitch Connect to a Projector lusrmgr.msc Local Users and Groups control Control Panel magnify Magnifier -

Foundation API Client Library PHP – Usage Examples By: Juergen Rolf Revision Version: 1.2
Foundation API Client Library PHP – Usage Examples By: Juergen Rolf Revision Version: 1.2 Revision Date: 2019-09-17 Company Unrestricted Foundation API Client Library PHP – Installation Guide Document Information Document Details File Name MDG Foundation API Client Library PHP - Usage Examples_v1_2 external.docx Contents Usage Examples and Tutorial introduction for the Foundation API Client Library - PHP Author Juergen Rolf Version 1.2 Date 2019-09-17 Intended Audience This document provides a few examples helping the reader to understand the necessary mechanisms to request data from the Market Data Gateway (MDG). The intended audience are application developers who want to get a feeling for the way they can request and receive data from the MDG. Revision History Revision Date Version Notes Author Status 2017-12-04 1.0 Initial Release J. Rolf Released 2018-03-27 1.1 Adjustments for external J. Rolf Released release 2019-09-17 1.2 Minor bugfixes J. Ockel Released References No. Document Version Date 1. Quick Start Guide - Market Data Gateway (MDG) 1.1 2018-03-27 APIs external 2. MDG Foundation API Client Library PHP – Installation 1.2 2019-09-17 Guide external Company Unrestricted Copyright © 2018 FactSet Digital Solutions GmbH. All rights reserved. Revision Version 1.2, Revision Date 2019-09-17, Author: Juergen Rolf www.factset.com | 2 Foundation API Client Library PHP – Installation Guide Table of Contents Document Information ............................................................................................................................ -

Property Mapping: a Simple Technique for Mobile Robot Programming
Property Mapping: a simple technique for mobile robot programming Illah R. Nourbakhsh The Robotics Institute, Carnegie Mellon University Pittsburgh, PA 15213 [email protected] Abstract In this paper we present robot observability as a The mobile robot programming problem is a software predictor for diagnostic transparency. Then, we present a engineering challenge that is not easily conquered using language-independent technique called property mapping contemporary software engineering best practices. We for constructing robot programs that are diagnostically propose robot observability as a measure of the diagnostic transparent and thereby achieve high degrees of transparency of a situated robot program, then describe reliability. property mapping as a simple, language-independent approach to implementing reliable robot programs by maximizing robot observability. Examples from real- The Robot Programming Problem world, working robots are given in Lisp and Java. A mobile robot is a situated automata, or a module that comprises one part of a closed system together with the Introduction environment. Fig. 1 shows the standard depiction of a robot, with its outputs labeled as actions and the outputs The recent availability of inexpensive, reliable robot of the environment in turn labeled as percepts. chassis (e.g. ActivMedia Pioneer, IS-Robotics Magellan, Nomad Scout) has broadened the accessibility of mobile robotics research. Because these robots consist of fixed E hardware out-of-the-box, this technology is shifting the actions A P percepts emphasis of mobile robot research from a joint hardware and software design process toward hardware-unaware R mobile robot programming. This is a software design problem, and yet software Figure 1: The standard view of an embedded robot engineering best practices are not very helpful. -

View the Slides (Smith)
Network Shells Michael Smith Image: https://commons.wikimedia.org/wiki/File:Network-connections.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png What does a Shell give us? ● A REPL ● Repeatability ● Direct access to system operations ● User-focused design ● Hierarchical context & sense of place Image: https://upload.wikimedia.org/wikipedia/commons/8/84/Bash_demo.png Management at a distance (netsh) Netsh: Configure DHCP servers with netsh -r RemoteMachine -u domain\username [RemoteMachine] netsh>interface [RemoteMachine] netsh interface>ipv6 [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (netsh) Netsh: Configure DHCP servers with netsh Location-r RemoteMachine -u domain\username Hierarchical [RemoteMachine] netsh>interfacecontext Simpler [RemoteMachine] netsh interface>ipv6 commands [RemoteMachine] netsh interface ipv6>show interfaces Reference: https://docs.microsoft.com/en-us/windows-server/networking/technologies/netsh/netsh-contexts Management at a distance (WSMan) WSMan (in Powershell): Manage Windows remotely with Set-Location -Path WSMan:\SERVER01 Get-ChildItem -Path . Set-Item Client\TrustedHosts *.domain2.com -Concatenate Reference: https://docs.microsoft.com/en-us/powershell/module/microsoft.wsman.management/about/about_wsman_provider -

C++ Properties -- a Library Solution
Document Number: SC22/WG21/N1615=04-0055 Date: 2004-04-09 Author: Lois Goldthwaite Email: [email protected] C++ Properties -- a Library Solution N1600 is a summary of the "property" language extension that is proposed for C++/CLI. I can't help feeling that this is an effort to impose an alien idiom on C++. There is too much of "the compiler will perform black magic behind your back" in it. There are too many ways in which the programmer must be aware that some [pseudo-]data members must be handled in different ways from [real] data members. The C++/CLI draft spec (N1608)says in 8.8.4 and 18.4 that "A property is a member that behaves as if it were a field." I think "behaves" is absolutely the wrong word to use here. A property is behavior that pretends to be state. From an OO design point of view, I think this is A Bad Idea. Behaviour should be visible; state should not. Further on, the document continues, "the X and Y properties can be read and written as though they were fields. In the example above, the properties are used to implement data hiding within the class itself." The subtle advantage of "hiding" a private data member by treating it as a public data member escapes me. Properties are just syntactic saccharine for getter and setter member functions for individual fields. C++ experts have spent years trying to educate people NOT to use public data, to use member functions instead, and now we propose to introduce something that looks just like public data? Do we really want to try to teach people that public fields are still bad, but properties are good, even though they look just the same from outside the class? Moreover, these public fields have side effects! There is a danger that too many novice programmers will prototype their designs using public fields, with the intent of changing them to properties later, if and when it proves necessary, and the general quality of code will suffer because of it. -

Office 365 Exchange Online Using Powershell
Relay Calendar Setup 1 Create a new room mailbox resource. If your room already has a calendar, you can skip this step. a. Log in to the Microsoft 365 admin center. b. Go to Resources › Rooms & equipment. c. Select + Add a resource mailbox. d. Fill out the New Resource form. This guide will assume an email address of [email protected]. No license is needed for the resource. e. Click Save. 2 Connect to Office 365 Exchange Online using PowerShell. This will let you configure room resource calendars in the next step. a. Allow signed scripts by opening Windows PowerShell as an administrator and running Set-ExecutionPolicy RemoteSigned b. Open a non-admin Windows PowerShell and log in by running $UserCredential = Get-Credential $Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https:// outlook.office365.com/powershell-liveid/ -Credential $UserCredential -Authentication Basic -AllowRedirection Import-PSSession $Session For more information, refer to the Exchange Online PowerShell documentation. 3 Create a distribution group for your rooms. This restricts Relay to only read specific calendars in your organization. a. Create the group. New-DistributionGroup -Name bluejeans-relay -Type Security -Notes "Rooms from which Relay can read calendars." b. Grant the Relay app access to the group. New-ApplicationAccessPolicy -AppId 5a75b6b1-f653-40b1-ab48-6ec9cea91b36 -PolicyScopeGroupId bluejeans-relay -AccessRight RestrictAccess -Description "Relay can only read calendars from mailboxes in this group." If you get a CommandNotFoundException, or if only your user appears in Get-Mailbox, then log in to Exchange Online Powershell as an admin. 4 Share the calendar with Relay. Do not skip this. -

Using the Calendar Outlook
Using the Calendar Microsoft Outlook Web App Copyright © 2019 KSU Division of University Information Technology Services This document may be downloaded, printed, or copied for educational use without further permission of the University Information Technology Services Division (UITS), provided the content is not modified and this statement is not removed. Any use not stated above requires the written consent of the UITS Division. The distribution of a copy of this document via the Internet or other electronic medium without the written permission of the KSU - UITS Division is expressly prohibited. Published by Kennesaw State University – UITS 2019 The publisher makes no warranties as to the accuracy of the material contained in this document and therefore is not responsible for any damages or liabilities incurred from UITS use. University Information Technology Services Using the Calendar Microsoft Outlook Web App Table of Contents Introduction ................................................................................................................................................ 5 Learning Objectives ..................................................................................................................................... 5 The Calendar Interface ................................................................................................................................ 6 Accessing the Calendar ..............................................................................................................................