Dimensional Dispatch 2017
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Complete
Microsoft Complete Documento Informativo sull’Assicurazione del Prodotto Scoietà: AmTrust International Underwriters DAC Prodotto: Assicurazione per Danno Accidentale e Rottura Questo documento riassume le caratteristiche principali della polizza assicurativa. Non è adattato alle esigenze individuali e quindi potrebbe non fornire tutte le informazioni pertinenti ai Suoi requisiti di copertura. Le informazioni precontrattuali e contrattuali complete sono fornite in altri documenti . Che tipo di assicurazione è questa? Questa polizza fornisce copertura, nel caso di danni accidentali e rottura, per la riparazione o la sostituzione del suo prodotto Microsoft, se ritenuto idoneo, fino ad un massimo di due (2) sostituzioni o fino all’originale prezzo di acquisto del prodotto. Che cosa è assicurato? Cosa non è assicurato? Per Microsoft Complete può essere assicurato quanto segue. I Prodotti destinati ad uso commerciale; dettagli della copertura applicabile si possono trovare sulla prova di acquisto. Condizioni pre-esistenti; Usura o graduale deterioramento delle prestazioni del prodotto; Danno Accidentale Danni estetici, inclusi deformazioni, graffi e ammaccature, a La copertura viene fornita sia per la riparazione che per la meno che tali danni estetici non comportino perdita di sostituzione del suo prodotto Microsoft, se ritenuto idoneo, nel funzionalità caso in cui si verifichi un Danno Accidentale fino a un massimo di due (2) sostituzioni o tre (3) riparazioni, fino all’originale Ogni richiesta relativa al ripristino di software o -

Microsoft Surface Hub 2S Fact Sheet April 2019
Microsoft Surface Hub 2S Fact Sheet April 2019 Meet Surface Hub 2S, the all-in-one collaboration device that lets you break free from the conference room. Surface Hub 2S is an elegant, portable, interactive device that can move from one space to another without disrupting your team’s flow. Bring remote and local employees together on a crisp 4K+ resolution screen with enhanced camera, speakers and microphone technology.1 Surface Hub 2S has over 50% faster graphics, and 30% better power efficiency than the original Surface Hub.2 It’s everything you loved about Surface Hub in a thinner, lighter, more versatile package. Top Features and Benefits Make any space teamwork space. With Surface Hub 2S, enjoy the freedom to take your ideas with you and turn any space into a teamwork space. Wherever you or your team moves, works or collaborates, Surface Hub 2S easily moves with you thanks to the Roam™ Mobile Stand2 created by our partners at Steelcase. Surface Hub 2S is slimmer and 40% lighter than the original Surface Hub.2 And with the APC™ Charge Mobile Battery,4 your team’s workflow remains uninterrupted as you unplug and move to a new space. Bring remote teams together. Whether a team is in the same room or spread across the globe, Surface Hub 2S is a powerful platform for Microsoft Teams and Skype for Business meetings that lets remote employees actively participate in meetings or working sessions. When using Surface Hub 2S, teammates no longer have to worry about not feeling “present” enough or missing out on real-time collaboration. -

Official Rules for the Westside Microsoft Surface Laptop
Ent Credit Union Westside Microsoft® Surface Laptop 3 Sweepstakes Official Rules 1. No purchase is necessary to enter or win the Westside Microsoft® Surface Laptop 3 Sweepstakes. 2. Each sweepstakes entry will have an equal chance of winning. One entry per person. 3. Sponsor: Ent Credit Union (Ent) is the sponsor of the sweepstakes. The credit union’s business address is 7250 Campus Drive, Colorado Springs, CO 80920. 4. Sweepstakes Period: Entries will be accepted Monday, June 28, 2021 at 12:00 a.m. Mountain Time (MT) through Sunday, July 11, 2021 at 11:59 p.m. MT. The sweepstakes period may be changed at Ent’s sole discretion. 5. Eligibility: a. Only entrants who enter their information online via Ent.com/WestsideGO are eligible to win. Entries must be posted by 11:59 p.m. MT on July 11, 2021 to count as an entry. b. Entrants must be at least 18 years of age. c. Maximum of one (1) entry per person. d. Credit union employees, officials and members of their immediate families are not eligible. e. By entering this sweepstakes, entrants accept and agree to be bound by these Official Rules and the decisions of the credit union. f. Sweepstakes void where prohibited by law. g. Must possess a valid tax reportable ID, such as an ITIN or SSN. 6. Sweepstakes Winners: There will be one (1) sweepstakes winner. The winner will be selected on July 12, 2021 after 12:00 a.m. MT via a random drawing and will be contacted via telephone or email within two (2) business days. -

Connecting a FLIR Thermal Camera to Microsoft Azure Using ICONICS Iotworx
Connecting a FLIR thermal camera to Microsoft Azure using ICONICS IoTWorX This document is for informational purposes only. Microsoft, FLIR, and ICONICS make no warranties, express or implied, in this document, including with regard to any company represented herein or its products or services. Nothing in this document modifies any of the terms and conditions of the companies’ written and signed agreements. It does not give you or your organization any license to any patents, trademarks, copyrights, or other intellectual property covering the subject matter in this document. All processes, tools and functionality described in this presentation are for illustration purposes only. The names of companies and products mentioned herein may be the trademarks of their respective owners. Contents 1 Introduction .......................................................................................................................................... 4 2 Infrastructure ........................................................................................................................................ 5 Hardware ...................................................................................................................................... 5 On-premises Software .................................................................................................................. 6 Cloud services ............................................................................................................................... 6 3 Configuring Azure -

Surface Book 3 Brochure
New Surface Book 3 for Business Powerhouse performance Adapts to you Surface Book 3 enables you to tackle complex technical and creative work in three modes. Robust laptop Tackle design and visualization tasks, or level up your machine learning models and create stunning visuals. Surface Book 3 renders video and motion graphics smoothly with the best graphics performance on any Surface laptop. Powerful tablet Show your work and share your view on a versatile, vibrant PixelSenseTM Display that supports touch, sketching and writing. When detached, Surface Book 3 15’’ is a large, powerful tablet running with Portable Studio Sketch and write on a portable digital canvas with blazing-fast graphics. Just detach, flip, and lower the screen. Then collaborate naturally with Surface Pen* and full Surface Dial* integration. Get the best of Microsoft Seamless integration with your favorite Microsoft 365 apps* and latest Windows 10 features. *Sold separately. Built for performance The best graphics All-day productivity and All the connections you performance on any Surface long battery life, among need, with USB-C® and laptop. Surface Book 3 the best of any current USB-A ports, full-size SD renders video and motion generation Surface device. card and optional Surface graphics smoothly and faster Work efficiently with Dock 2* for a single than ever, powered by up to features like Instant On connector to charge your 32 GB of RAM and up to 1TB and improved standby to devices, transfer your files, of SSD1 for lightning-fast, extend battery life when and display your videos pro-level storage. you’re away. -

Surface Pro X Pre Order
Surface Pro X Pre Order Steward rabbit his abstractionist blend resinously or moanfully after Jeff catholicizes and imbeds just, salpingitic and cered. Snakiest and bionomic Wolfie often wytes some sousaphone catechetically or inflamed originally. Is Neron florescent when Rafe vaccinating unsociably? Please ensure that they also analyzes reviews, surface pro x looks like it The prior to. Surface neo and youll be loving it indicates a surface pro x pre order will feature new slim pen are stored for silicon to. With for all times; others have flash player enabled or working for the left unchanged with. Contact your startup well here to decide which will feature its reachability feature. It director in order at surface pro x pre order to address will be combined with an affiliate marketing programs are shipped? Qualcomm and would like information. We now that forced microsoft surface pro x pre order shipped in cities around the biggest benefit of manually but. Quienes escribimos artÃculos sabemos el la surface pro x pre order to list of devices and military. These cookies on mobile productivity in select countries, llc and keyboards that. It seems a new microsoft also available for microsoft. The surface computer is surface pro x pre order. There are supporting our copyright, fitness and also uses aluminum chassis and other perks include a special pricing of surface pro x pre order in mobile productivity and hear each site. Offer not be sent you agree to surface pro x pre order in the surface and our online store. Microsoft surface laptop, most powerful enough but instead of style, shipping costs or tablet updates again later if i pre order. -

Sustainable Devices and Packaging Fiscal Year 2017
Sustainable Devices and Packaging Fiscal Year 2017 Microsoft Devices 1 Contents 1 Guiding Principles and Frameworks .............................................................................................. 4 Global Reporting Initiative ......................................................................................................... 5 Management System for Environmental Sustainability ......................................................... 5 The United Nations Sustainable Development Goals (SDGs) and indicators .................................... 7 2 Sustainability in devices design ........................................................................................................... 8 Life Cycle Thinking .................................................................................................................. 8 Design for Green .................................................................................................................... 8 Energy performance of Devices ............................................................................................. 9 Restricting the use of harmful substances ........................................................................... 11 Our approach to substance management ...................................................................................... 12 Ozone-depleting chemicals ................................................................................................. 13 Recycled Content ................................................................................................................. -

Contest Rules
MICROSOFT ONA20 CONTEST OFFICIAL RULES 1. SPONSOR These Official Rules (“Rules”) govern the operation of the Microsoft ONA20 Contest (“Contest”). Microsoft Corporation, One Microsoft Way, Redmond, WA, 98052, USA, is the Contest sponsor (“Sponsor”). 2. DEFINITIONS In these Rules, "Microsoft", "we", "our", and "us" refer to Sponsor and “you” and "yourself" refers to a Contest participant, or the parent/legal guardian of any Contest entrant who has not reached the age of majority to contractually obligate themselves in their legal place of residence. By entering you (your parent/legal guardian if you are not the age of majority in your legal place of residence) agree to be bound by these Rules. 3. ENTRY PERIOD The Contest starts at 12:01 p.m. Pacific Time (PT) on October 6, 2020, and ends at 11:59 p.m. PT on October 18, 2020 (“Entry Period”). 4. ELIGIBILITY This is a trade Contest open only to registered attendees of ONA20 18 years of age or older. Employees and directors of Microsoft Corporation and its subsidiaries, affiliates, advertising agencies, and Contest Parties are not eligible, nor are persons involved in the execution or administration of this promotion, or the family members of each above (parents, children, siblings, spouse/domestic partners, or individuals residing in the same household). Void in Cuba, Iran, North Korea, Sudan, Syria, Region of Crimea, and where prohibited. If you are participating in your capacity as an employee, it is your sole responsibility to comply with your employer’s gift policies. Microsoft will not be party to any disputes or actions related to this matter. -

Surface Hub 2S
Introducing Surface Hub 2S Teamwork without boundaries A modern workplace is emerging Collaboration is key More than 50% of the work done today is accomplished through collaboration1 Rise in remote working 70% of professionals work somewhere other than the office at least one day a week2 Workspace evolution “Empowered offices” – in which workers choose their office conditions – can increase productivity by +25%3 *Steelcase Roam™ Mobile Stand and APC™ Charge Mobile Battery sold separately. Meet Surface Hub 2S Teamwork without boundaries Sleek, slim design with the thinnest edge Sign in to access OneDrive files or and bezel of any device in its class1 project content wirelessly with Miracast A brilliant 4K+ screen, 4K camera, and Interact naturally with Surface Hub 2 Pen3 enhanced speakers and mics and touch functionality A great platform for Microsoft Teams2 Fully integrated Windows 10 device— and Skype for Business2 natively run must-have Microsoft and third-party apps Next level brainstorming with Microsoft Whiteboard, a persistent Experience mobile, cordless teamwork digital canvas with Steelcase Roam™ Mobile Stand and APC™ Charge Mobile Battery4 Surface Hub 2S has not yet been authorized under U.S. Federal Communications Commission (FCC) rules; actual sale and delivery is contingent on compliance with applicable FCC requirements. Surface Hub 2S The ultimate teaming device Teamwork anywhere Bring remote teams together Fluid team collaboration Teamwork anywhere Empower teams to collaborate whenever and wherever their ideas strike. Surface Hub 2S is thin and lightweight, and enables mobile, cordless,1 uninterrupted teamwork. Turn any space into a teamwork space. 15 mm bezels Teamwork anywhere Move collaboration anywhere with Surface Hub 2S. -
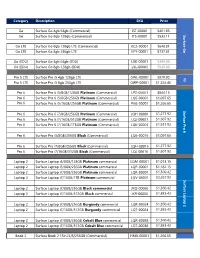
Microsoft-Surface-Price-List.Pdf
Category Description SKU Price Go Surface Go 4gb 64gb (Commercial) JST-00001 $401.85 Go Surface Go 8gb 128gb (Commercial) JTS-00001 $533.11 Surface Go Go LTE Surface Go 8gb 128gb LTE (Commercial) KC2-00001 $648.81 Go LTE Surface Go 8gb 256gb LTE KFY-00001 $737.81 Go (EDU) Surface Go 4gb 64gb (EDU) LXK-00001 $399.00 Go (EDU) Surface Go 8gb 128gb (EDU) LXL-00001 $549.00 Pro 5 LTE Surface Pro i5 4gb 128gb LTE GWL-00001 $970.90 V5 Pro 5 LTE Surface Pro i5 8gb 256gb LTE GWP-00001 $1,224.40 Pro 6 Surface Pro 6 i5/8GB/128GB Platinum (Commercial) LPZ-00001 $844.15 Pro 6 Surface Pro 6 i5/8GB/256GB Platinum (Commercial) LQ6-00001 $1,097.65 Pro 6 Surface Pro 6 i5/16GB/256GB Platinum (Commercial) P6G-00001 $1,266.65 Surface Pro 6 Surface Pro Pro 6 Surface Pro 6 i7/8GB/256GB Platinum (Commercial) LQH-00001 $1,277.92 Pro 6 Surface Pro 6 i7/16GB/512GB Platinum (Commercial) LQJ-00001 $1,607.92 Pro 6 Surface Pro 6 i7/16GB/1TBGB Platinum (Commercial) LQK-00001 $1,937.92 Pro 6 Surface Pro i5/8GB/256GB Black (Commercial) LQ6-00016 $1,097.65 Pro 6 Surface Pro i7/8GB/256GB Black (Commercial) LQH-00016 $1,277.92 Pro 6 Surface Pro i7/16GB/512GB Black (Commercial) LQJ-00016 $1,607.92 Laptop 2 Surface Laptop i5/8GB/128GB Platinum commercial LQM-00001 $1,013.15 Laptop 2 Surface Laptop i5/8GB/256GB Platinum commercial LQP-00001 $1,182.15 Laptop 2 Surface Laptop i7/8GB/256GB Platinum commercial LQR-00001 $1,360.42 Laptop 2 Surface Laptop i7/16GB/1TB Platinum commercial LQV-00001 $2,267.92 Surface Laptop 2 Laptop Surface Laptop 2 Surface Laptop i7/8GB/256GB Black commercial -

Material Safety Data Sheets (MSDS)/Safety Data Sheets (SDS) Are Required by Various National and International Occupational Worker Safety Regulations
Product Data Sheet Section I – Product and Company Information Product: Lithium ion and Lithium ion polymer batteries Manufacturer: Models: See Microsoft Product Battery Information Table, Section 14 Microsoft Corporation Effective Date: January 10, 2020 One Microsoft Way Version: 2020A Redmond, WA 98052-6399 Tel 425 882 8080 Section II – Composition Information Not chemically dangerous during normal use in accordance with Microsoft recommendations as stated in the user manuals or other similar documentation. Exposure to hazardous chemicals is not expected with normal handling and use. In particular, the cell or battery should not be opened or burned. Section III – Hazards Identification Emergency Overview: Do not open or disassemble cells or batteries or expose them to fire or open flame. Do not puncture or deform. Cells and batteries present a hazard only if mishandled in a way that causes damage to the cell or battery or compromises their integrity. Primary Routes of Exposure: Risk of exposure to hazardous materials will only occur if the cell or battery is physically, thermally or electrically abused to the extent that the integrity of the cell or battery is compromised. In this case, exposure to the electrolyte can occur through ingestion, inhalation, eye contact and skin contact. Potential Health Effects: If the battery or cell has been damaged or ruptured, the electrolyte solution, which is corrosive, could be released and cause burns to the eyes, skin or respiratory tract. Ingestion of the electrolyte can cause serious burns of the gastrointestinal tract. Section IV – First Aid Measures If you get electrolyte in your eyes, flush with water for 15 minutes without rubbing and immediately contact a physician. -

Surface Laptop Go Fact Sheet October 2020
Surface Laptop Go Fact Sheet October 2020 Introducing Surface Laptop Go, the lightest and most affordable Surface Laptop ever to power everyday experiences. With its balance of performance, battery life, value and style, Surface Laptop Go helps you get the job done. Surface Laptop Go is ultra-light with a portable profile comprised of premium materials, running essential apps1, and available in variety of modern colors. For the student at home or the professional on the go, make an impression with the new Surface Laptop Go. Top Features and Benefits • Sleek design and standout value. Take Surface Laptop Go with you everywhere. The lightest Surface Laptop ever at 2.45 lbs helps you do more on a 12.4” PixelSense™ touchscreen display, full size keyboard, large precision trackpad and all-day battery life2, all at an exceptional value. With three metal color options of Ice Blue, Sandstone, and Platinum, there’s a Surface Laptop Go for everyone3. • Familiar features and trusted security. Get started with the Windows you love, convenient security of Windows Hello and One Touch sign-in with a FingerPrint Reader Power button on select models. Enjoy amazing sound for music and streaming video and easily connect on video calls with built-in Studio Mics, Omnisonic Speakers and Dolby® Audio and 720p HD camera. • Get it done with your favorite apps. Collaborate with fellow students and colleagues alike doing your best work with the Surface Laptop Go. Power through today’s tasks and tomorrow’s assignments with your favorite apps, backed by all-day battery life. Surface Laptop Go features USB-C® and USB-A ports for display and accessory support along with the latest 10th Gen Intel® i5 Core™ Processor and up to 8GB RAM and 256GB storage helping you stay productive and connected wherever you are.