Modeling Traffic Shaping and Traffic Policing in Packet-Switched Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Designing Traffic Profiles for Bursty Internet Traffic
Designing Traffic Profiles for Bursty Internet Traffic Xiaowei Yang MIT Laboratory for Computer Science Cambridge, MA 02139 [email protected] Abstract An example of a non-conforming stream is one that has a This paper proposes a new class of traffic profiles that is much higher expected transmission rate than that allowed better suited for metering bursty Internet traffic streams by a traffic profile. than the traditional token bucket profile. A good traffic It is desirable to have a range of traffic profiles for differ- profile should satisfy two criteria: first, it should consider ent classes of traffic, and for differentiation within a class. packets from a conforming traffic stream as in-profile with For example, traffic streams generated by constant bit rate high probability to ensure a strong QoS guarantee; second, video applications have quite different statistics than those it should limit the network resources consumed by a non- generated by web browsing sessions, thus require different conforming traffic stream to no more than that consumed profiles to meet their QoS requirements. It is worth noting by a conforming stream. We model a bursty Internet traffic that the type of traffic we consider in this paper is most of- stream as an ON/OFF stream, where both the ON-period ten generated by document transfers, such as web browsing. and the OFF-period have a heavy-tailed distribution. Our Traditionally, the QoS requirement for such traffic (a.k.a. study shows that the heavy-tailed distribution leads to an elastic traffic) is less obvious than that for the real-time excessive randomness in the long-term session rate distribu- traffic. -

Performance Analysis I
CS 6323 Complex Networks and Systems: Modeling and Inference Lecture 5: Performance Analysis I Prof. Gregory Provan Department of Computer Science University College Cork Slides: Based on M. Yin (Performability Analysis) Overview •Queuing Models •Birth-Death Process •Poisson Process •Task Graphs Complex Networks and Systems 2 Network Modelling • We model the transmission of packets through a network using Queueing Theory • Enables us to determine several QoS metrics • Throughput times, delays, etc. • Predictive Model • Properties of queueing network depends on • Network topology • Performance for each “path” in network • Network interactions Complex Networks and Systems 3 Queuing Networks • A queuing network consists of service centers and customers (often called jobs) • A service center consists of one or more servers and one or more queues to hold customers waiting for service. : customers arrival rate : service rate 1/24/2014 Complex Networks and Systems 4 Interarrival • Interarrival time: the time between successive customer arrivals • Arrival process: the process that determines the interarrival times • It is common to assume that interarrival times are exponentially distributed random variables. In this case, the arrival process is a Poisson process : customers arrival rate : service rate 0 1 2 n 1/24/2014 Complex Networks and Systems 5 Service Time • The service time depends on how much work the customer needs and how fast the server is able to perform the work • Service times are commonly assumed to be independent, identically distributed (iid) random variables. 1/24/2014 Complex Networks and Systems 6 A Queuing Model Example Server Center 1 Server Center 2 cpu1 Disk1 cpu2 queue Disk2 Arriving customers cpu3 servers Server Center 3 Queuing delay Service time Response time 1/24/2014 Complex Networks and Systems 7 Terminology Term Explanations Buffer size The total number of customers allowed at a service center. -

Traffic Management in Multi-Service Access Networks
MARKETING REPORT MR-404 Traffic Management in Multi-Service Access Networks Issue: 01 Issue Date: September 2017 © The Broadband Forum. All rights reserved. Traffic Management in Multi-Service Access Networks MR-404 Issue History Issue Approval date Publication Date Issue Editor Changes Number 01 4 September 2017 13 October 2017 Christele Bouchat, Original Nokia Comments or questions about this Broadband Forum Marketing Draft should be directed to [email protected] Editors Francois Fredricx Nokia [email protected] Florian Damas Nokia [email protected] Ing-Jyh Tsang Nokia [email protected] Innovation Christele Bouchat Nokia [email protected] Leadership Mauro Tilocca Telecom Italia [email protected] September 2017 © The Broadband Forum. All rights reserved 2 of 16 Traffic Management in Multi-Service Access Networks MR-404 Executive Summary Traffic Management is a widespread industry practice for ensuring that networks operate efficiently, including mechanisms such as queueing, routing, restricting or rationing certain traffic on a network, and/or giving priority to some types of traffic under certain network conditions, or at all times. The goal is to minimize the impact of congestion in networks on the traffic’s Quality of Service. It can be used to achieve certain performance goals, and its careful application can ultimately improve the quality of an end user's experience in a technically and economically sound way, without detracting from the experience of others. Several Traffic Management mechanisms are vital for a functioning Internet carrying all sorts of Over-the-Top (OTT) applications in “Best Effort” mode. Another set of Traffic Management mechanisms is also used in networks involved in a multi-service context, to provide differentiated treatment of various services (e.g. -

A Passive Approach to Detection of Traffic Shaping
A Passive Approach to Detection of Traffic Shaping Mark Norman and John Leis Electrical, Electronic and Computer Engineering, University of Southern Queensland, Australia, E-mail: [email protected] Abstract—Internet service providers often alter the profile of Shapers delay some or all of the packets in data traffic, a practice referred to as “shaping”. This may be a traffic stream in order to bring the stream into done in order to comply with a service contract, or for the compliance with a traffic profile. A shaper usually provisioning of services with real-time delivery constraints. This means that the effective throughput to the customer is reduced has a finite-size buffer, and packets may be discarded in some way, either for all traffic, or for one or more individual if there is not sufficient buffer space to hold the flows. The presence of traffic shaping may be controversial in delayed packets. some circumstances, particularly when certain classes of traffic are shaped (thus altering the traffic profile). The detection of Shaping is usually implemented in practice via a buffer- the existence of traffic shaping on a particular connection or ing algorithm – the so-called “leaky bucket” or the “token flow is desirable, but technically it is a nontrivial problem. This bucket”, depending on the requirements. Both algorithms are is especially so if the end-user has limited or no knowledge well-known. In this work, we do not assume any particular of the outside network conditions. In this paper, we propose a “blind” traffic shaping detection algorithm, and investigate its algorithmic implementation of the shaping itself. -

Design of Traffic Shaper / Scheduler for Packet Switches and Diffserv Networks : Algorithms and Architectures
New Jersey Institute of Technology Digital Commons @ NJIT Dissertations Electronic Theses and Dissertations Spring 5-31-2001 Design of traffic shaper / scheduler for packet switches and DiffServ networks : algorithms and architectures Surong Zeng New Jersey Institute of Technology Follow this and additional works at: https://digitalcommons.njit.edu/dissertations Part of the Electrical and Electronics Commons Recommended Citation Zeng, Surong, "Design of traffic shaper / scheduler for packet switches and DiffServ networks : algorithms and architectures" (2001). Dissertations. 491. https://digitalcommons.njit.edu/dissertations/491 This Dissertation is brought to you for free and open access by the Electronic Theses and Dissertations at Digital Commons @ NJIT. It has been accepted for inclusion in Dissertations by an authorized administrator of Digital Commons @ NJIT. For more information, please contact [email protected]. Copyright Warning & Restrictions The copyright law of the United States (Title 17, United States Code) governs the making of photocopies or other reproductions of copyrighted material. Under certain conditions specified in the law, libraries and archives are authorized to furnish a photocopy or other reproduction. One of these specified conditions is that the photocopy or reproduction is not to be “used for any purpose other than private study, scholarship, or research.” If a, user makes a request for, or later uses, a photocopy or reproduction for purposes in excess of “fair use” that user may be liable for copyright -

Market for Parking Access Services
ITS America The Intelligent Transportation Society of America (ITS America) Connected Vehicle Insights Fourth Generation Wireless Vehicle and Highway Gateways to the Cloud An evaluation of Long Term Evolution (LTE) and other wireless technologies’ impact to the transportation sector Steven H. Bayless Technology Scan Series 2011-2012 0 Connected Vehicle Insights: 4G Wireless: Vehicle and Highway Gateways to the Cloud ITS America INTRODUCTION With Fourth Generation cellular (4G), we will see the complete extension of the internet suite of protocols to the wireless environment. 4G likely represents the end of the traditional siloed telecommunications approach that has been the result of decades of investment in single-application “purpose built” wireless technologies (e.g. radio, TV, land mobile, and cellular) and regulatory practice. Current investment patterns in infrastructure provide a strong indication of what will be available and provided in what quantities, quality, and cost beyond 2015 for both terminal devices and network infrastructure. This paper examines how next generation wide-area cellular such as 4G will be able to support vehicular applications, and how transportation infrastructure may mesh with wireless networks. Specifically, it suggests that automotive electronics engineers will need to be cognizant of how application data is treated by 4G Long Term Evolution (LTE) networks, and how innovations such as self-organizing femto-cells, “traffic shaping” and heterogeneous or “vertical roaming” across different radio access technologies may improve the performance of off-board or “cloud” -based vehicular applications Furthermore, the paper suggests that over the long term, vehicles will serve as wireless gateways that manage and collect data a number of devices or sensors deployed in vehicles and highway infrastructure, utilizing 4G cellular as the last-mile wide-area connection to the cloud. -

A Novel Simulation Based Methodology for the Congestion Control in ATM Networks
A Novel Simulation Based Methodology for the Congestion Control in ATM Networks Heven Patel, Hardik Patel, Aditya Jagannath, Syed Rizvi, Khaled Elleithy Computer Science and Engineering Department University of Bridgeport, Bridgeport, CT Abstract- In this project, we use the OPNET simulation tool client server and source destination networks with various for modeling and analysis of packet data networks. Our project protocol parameters and service categories. We also is mainly focused on the performance analysis of simulate a policing mechanism for ATM networks .In this Asynchronous transfer mode (ATM) networks. Specifically, in section we simulate the performance of the FDDI this project, we simulate two types of high-performance protocol. We consider network throughput, link networks namely, Fiber Distributed Data Interface (FDDI) utilizations, and end-to-end delay by varying network and Asynchronous Transfer Mode (ATM). In the first type of network, we examine the performance of the FDDI protocol by parameters in two network configurations. The leaky varying network parameters in two network configurations. In bucket mechanism limits the difference between the the second type, we build a simple ATM network model and negotiated mean cell rate (MCR) parameter and the actual measure its performance under various ATM service cell rate of a traffic source. It can be viewed as a bucket, categories. Finally, we develop an OPNET process model for placed immediately after each source. Each cell generated leaky bucket congestion control algorithm and examine its by the traffic source carries token and attempts to place it performance and its relative effect on the traffic patterns (loss in the bucket. -
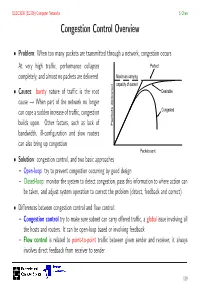
Congestion Control Overview
ELEC3030 (EL336) Computer Networks S Chen Congestion Control Overview • Problem: When too many packets are transmitted through a network, congestion occurs At very high traffic, performance collapses Perfect completely, and almost no packets are delivered Maximum carrying capacity of subnet • Causes: bursty nature of traffic is the root Desirable cause → When part of the network no longer can cope a sudden increase of traffic, congestion Congested builds upon. Other factors, such as lack of Packets delivered bandwidth, ill-configuration and slow routers can also bring up congestion Packets sent • Solution: congestion control, and two basic approaches – Open-loop: try to prevent congestion occurring by good design – Closed-loop: monitor the system to detect congestion, pass this information to where action can be taken, and adjust system operation to correct the problem (detect, feedback and correct) • Differences between congestion control and flow control: – Congestion control try to make sure subnet can carry offered traffic, a global issue involving all the hosts and routers. It can be open-loop based or involving feedback – Flow control is related to point-to-point traffic between given sender and receiver, it always involves direct feedback from receiver to sender 119 ELEC3030 (EL336) Computer Networks S Chen Open-Loop Congestion Control • Prevention: Different policies at various layers can affect congestion, and these are summarised in the table • e.g. retransmission policy at data link layer Transport Retransmission policy • Out-of-order caching -

RFC 6349 Testing with Truespeed™ from JDSU—Experience Your
RFC 6349 Testing with TrueSpeed™ from JDSU— Experience Your Network as Your Customers Do RFC 6349 is the new transmission control protocol (TCP) throughput test methodology that JDSU co-authored along with representatives from Bell Canada and Deutsche Telecom. Recently issued by the Internet Engineering Task Force (IETF) organization, RFC 6349 provides a repeatable test method for TCP throughput analysis with systematic processes, metrics, and guidelines to optimize the network and server performance. This application note summarizes RFC 6349, “Framework for TCP Throughput Testing,” and highlights the automated and fully compliant JDSU RFC 6349 implementation, TrueSpeed, now available on the JDSU T-BERD®/MTS-6000A Multi-Services Application Module (MSAM) and T-BERD/MTS-5800 Handheld Network Tester. This application note also discusses the integration of TrueSpeed RFC 6349 with the ITU Y.1564 Ethernet service activation standard. This powerful testing combination provides a comprehensive means to ensure an optimized end-customer experience in multi-service (such as triple play) environments. RFC 6349 TCP Test Methodology RFC 6349 specifies a practical methodology for measuring end-to-end TCP throughput in a managed IP network with a goal of providing a better indication of the user experience. In the RFC 6349 framework, TCP and IP parameters are also specified to optimize TCP throughput. RFC 6349 recommends always conducting a Layer 2/3 turn-up test before TCP testing. After verifying the network at Layer 2/3, RFC 6349 specifies conducting -

The Local and Global Effects of Traffic Shaping in the Internet
The Local and Global Effects of Traffic Shaping in the Internet Massimiliano Marcon Marcel Dischinger Krishna P. Gummadi Amin Vahdat MPI-SWS MPI-SWS MPI-SWS UCSD [email protected] [email protected] [email protected] [email protected] Abstract—The Internet is witnessing explosive growth in traf- ISPs limit the aggregate bandwidth consumed by bulk flows fic, in large part due to bulk transfers. Delivering such traffic is to a fixed value, independently of the current level of link expensive for ISPs because they pay other ISPs based on peak utilization [16]. A few ISPs even resort to blocking entire utilization. To limit costs, many ISPs are deploying ad-hoc traffic shaping policies that specifically target bulk flows. However, there applications [12]. So far, these policies are not supported by is relatively little understanding today about the effectiveness of an understanding of their economic benefits relative to their different shaping policies at reducing peak loads and what impact negative impact on the performance of bulk transfers, and thus these policies have on the performance of bulk transfers. their negative impact on customer satisfaction. In this paper, we compare several traffic shaping policies with respect to (1) the achieved reduction in peak network traffic Against this backdrop, this paper poses and answers two and (2) the resulting performance loss for bulk transfers. We questions: identified a practical policy that achieves peak traffic reductions of up to 50% with only limited performance loss for bulk 1. What reduction in peak utilization can an ISP achieve transfers. However, we found that the same policy leads to large by traffic shaping only bulk flows, and how much do performance losses for bulk transfers when deployed by multiple ISPs along a networking path. -

Experience the Network As Your Customers Do— Closing the Turn-Up Gap
Experience the Network as Your Customers Do— Closing the Turn-up Gap Traditionally, Layer 2/3 turn-up tests such as RFC 2544 have been conducted when installing Ethernet services. After providers “certify” their networks with either an RFC 2544 test or the new Y.1564 test, they can still receive complaints of poor application performance from business-end customers using video conferencing, YouTube, Facebook, or cloud-based applications. The gap in installation testing, namely the omission of transmission control protocol (TCP)-layer testing, which is key to optimal end-customer application layer performance, is the cause for this disconnect. Figure 1 portrays a simplified view of the protocol stack and the gap between current turn-up testing methodologies and the end-user experience. End User applications (Facebook, YouTube) TCP Testing gap is TCP IP/Ethernet Tested by RFC 2544 and Y.1564 Figure 1. Simplified protocol stack showing the gap between turn-up testing and the end-user experience This testing gap does not let network providers experience network performance like their customers, so they need a solution that can verify TCP-layer performance before end-customer activation. Testing at the TCP layer can eliminate additional truck rolls, tech support calls, and customer churn which provides substantially positive implications to providers’ operating expenses (OpEx). White Paper This white paper: y Briefly introduces the TCP protocol y Summarizes some common customer-premises equipment (CPE) and network issues that can adversely affect TCP and application performance y Introduces the new IETF RFC 6349 TCP test methodology y Demonstrates the benefits to network providers who conduct RFC 6349-based TCP-layer installation testing Network and CPE Issues that Adversely Affect TCP TCP operates at open system interconnection (OSI) Layer 4 and resides on top of the IP Layer 3. -

Traffic Management Strategies for Operators
Traffic Management Strategies for Operators QUALCOMM, Incorporated January 2011 For more information on Qualcomm innovations: http://www.qualcomm.com/innovation/research/feature_project/femtocells.html Traffic Offload Table of Contents [1] Executive Summary ......................................................................... 1 [2] Overview of the Traffic Management Problem ................................ 2 [3] Traffic Management in Macro cellular Network ............................... 4 3.1 Innovations in Connection Management ................................. 4 3.2 Enhanced Cell_FACH Mechanism .......................................... 6 3.3 Dynamic QoS Control .............................................................. 7 3.4 SIPTO Techniques ................................................................ 10 [4] Traffic Offload via Microcells and Pico Cells .................................. 11 4.1 Performance Gains with Microcells ....................................... 13 4.2 Analysis ................................................................................. 14 [5] Traffic Offload via Femto Deployments ......................................... 16 5.1 Performance Results ............................................................. 17 5.2 Femtocells Key Challenges and Solutions ............................ 20 5.3 Femtocell Transmit Power Self Calibration ........................... 20 [6] Traffic Offload via Wi-Fi Access Points .......................................... 21 [7] Conclusions ...................................................................................