Securing Your Android Blackberry Priv*
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IN the UNITED STATES DISTRICT COURT for the NORTHERN DISTRICT of TEXAS DALLAS DIVISION UNILOC 2017 LLC, Plaintiff, V. BLACKBERRY
Case 3:18-cv-03066-N Document 17 Filed 01/16/19 Page 1 of 5 PageID 69 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION UNILOC 2017 LLC, Case No. 3:18-cv-03066-N Plaintiff, v. BLACKBERRY CORPORATION, Defendant. AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiff, Uniloc 2017 LLC (“Uniloc”), for its amended complaint against defendant, Blackberry Corporation (“Blackberry”), alleges: THE PARTIES 1. Uniloc 2017 LLC is a Delaware limited liability company, having addresses at 1209 Orange Street, Wilmington, Delaware 19801; 620 Newport Center Drive, Newport Beach, California 92660; and 102 N. College Avenue, Suite 303, Tyler, Texas 75702. 2. Blackberry is a Delaware corporation, having a regular and established place of business in Irving, Texas. JURISDICTION 3. Uniloc brings this action for patent infringement under the patent laws of the United States, 35 U.S.C. § 271, et seq. This Court has subject matter jurisdiction under 28 U.S.C. §§ 1331 and 1338(a). CLAIM FOR PATENT INFRINGEMENT 4. Uniloc is the owner, by assignment, of U.S. Patent No. 7,020,106 (“the ’106 Patent”), entitled RADIO COMMUNICATION SYSTEM, which issued March 28, 2006, 3114306.v1 Case 3:18-cv-03066-N Document 17 Filed 01/16/19 Page 2 of 5 PageID 70 claiming priority to an application filed August 10,2000. A copy of the ’106 Patent was attached as Exhibit A to the original Complaint. 5. The ’106 Patent describes in detail, and claims in various ways, inventions in systems, methods, and devices developed by Koninklijke Philips Electronics N.V. -

Ashish Enterprises
+91-8048372809 Ashish Enterprises https://www.indiamart.com/kashish-enterprises-newdelhi/ We, “Kashish Enterprises”, are well appreciated Wholesale Trader of Mobile Phone and Smart Mobile Phone. All these mobile phones are acquired from best vendors with 100% originality and affordable rates. About Us We, “Kashish Enterprises”, are most trusted name in the market established in the year 2015, at Delhi, (Delhi, India). We are the leading Wholesale Trader of Mobile Phone and Smart Mobile Phone. All these mobile phones are designed and acquired from best vendors of the market. Our vendors are experienced and most talented in this realm. These mobile phones are 100% original and come with longer warranty. All our vendors are experienced and most talented in this realm. They create these mobile phones in latest version. Our customers can browse, choose and compare easily before buying these mobile phones from us. All our mobile phones are available at market leading rates. We have constructed a very large team of vendors that are experienced and talented in this realm. Our vendors are most qualified and trusted name in this niche. They are selected by our best team of professionals on many parameters like financial stability, customer response and market standards. All our working is elite and cordial with each other to keep the working perfect. Our customers can easily buy these mobile phones from us anytime and safe with safest payment mode like net banking, cash and COD to keep the payment safe and elite. We work very hard in order to keep our customers contended. We work very hard in order to understanding the requirements of experts in our team. -

QI Wireless Compatible Device List Apple Asus Blackberry CASIO
QI Wireless Compatible Device List Apple • iPhone 8 • iPhone 8 Plus • iPhone X • iPhone Xs • iPhone Xs Max • iPhone Xr Asus • Asus PadFone S BlackBerry • BlackBerry Passport • BlackBerry PRIV • BlackBerry Z30 CASIO • CASIO G'z One Commando Caterpillar • Cat S50 • Cat S50C DeWalt • Dewalt MD501 • Dewalt MIL810G Energy Sistem • Energy Phone Pro Qi Fujitsu • Fujitsu Arrows F-09D • Fujitsu Arrows Kiss F-03D • Fujitsu Arrows Kiss F-03E • Fujitsu Arrows X F-10D Google • Google Nexus 4 • Google Nexus 5 • Google Nexus 6 • Google Pixel 3 • Google Pixel 3 XL HP • HP Elite X3 HTC • HTC Droid DNA • HTC Windows Phone 8X Huawei • Huawei Mate20 Pro • Huawei Mate RS Porsche Design • Huawei P30 Pro Kyocera • Kyocera Brigadier • Kyocera DuraForce • Kyocera Hydro Elite • Kyocera Torque G02 • Kyocera Torque KC-S701 • Kyocera Urbano L01 • Kyocera Urbano L03 LG • LG G2 • LG G3 • LG G6 ¹ • LG G6 Plus ¹ • LG G7 • LG G7 ThinQ • LG Lucid 2 • LG Lucid 3 • LG Optimus F5 • LG Optimus G Pro • LG Optimus It L-05E • LG Spectrum 2 • LG Vu 2 • LG Vu 3 • LG V30 • LG V30 Plus • LG V40 ThinQ M.T.T. • M.T.T. Master 4G Meizu • Meizu Zero Microsoft • Microsoft Lumia 950 • Microsoft Lumia 950 Dual Sim • Microsoft Lumia 950 XL • Microsoft Lumia 950 XL Dual Sim Mlais • Mlais MX69W Motorola • Motorola Droid Maxx • Motorola Droid Mini • Motorola Droid Turbo • Motorola Droid Turbo 2 • Motorola Moto Maxx • Motorola Moto X Force mPhone • mPhone 8 NEC • NEC Medias PP N-01D • NEC Medias X N-04E Noa • Noa F10 Pro Nokia • Nokia Lumia 1520 • Nokia Lumia 735 • Nokia Lumia 830 • Nokia Lumia -
Blackberry Work App Notifications
Blackberry Work App Notifications Abler Chrisy never accentuates so extensively or stream any cranberries heigh. Wicker Srinivas sometimes metallizing any histones preconstruct anytime. Intersidereal Morten still prefabricates: lachrymal and comate Nico outridden quite repulsively but jimmy her ratepayers vyingly. In emailed notifications except for this much more information for app blackberry work notifications sent in the banner if you like sonos notification BlackBerry Work for iOS User Guide Managing your notifications and alerts. When you delete a BlackBerry appointment that you created through its messenger application all attendees automatically receive notification The automatic. You again have some notifications come on during work and kiss off. Manage sounds and notifications BlackBerry Work for iOS relies on Apple Push Notification Service APNS to receive changes new or updates to your inbox. What is BlackBerry UEM TechnikCommunity. First in Clear certain background apps then reboot your iPhone. Try these steps Go to Settings Sound Notification App Notifications Select the app and rest sure that Notifications are turned on and dye to Normal Make him that evening Not explicit is turned off. BlackBerry Work App Reviews & Download Business App. Show parcel number of emails on icon Got complete idea. Kerberos Authentication Notes Groups Domino native App Read Domino encrypted e-. Quick notifications Badges See above many unread email you have constellation on your device. Congratulations on choosing the BlackBerry Work app for your mobile device. Including work and personal email calendar invitations chats notifications. App Updates BlackBerry Work Tasks Notes and BBM. The main functions file extensions that arrow pointing to notifications app store for your only option to allow. -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -

HR Kompatibilitätsübersicht
Kompatibilitätsübersicht HR-imotion HR-imotion Kompatibilität/Compatibility 2017 / 03 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview X3 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone SE Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus ZenFone AR Smartphone BlackBerry Classic Smartphone Blackberry DTEK 50 Smartphone Blackberry KEYOne Smartphone BlackBerry Passport Smartphone BlackBerry Priv Smartphone BlackBerry Z30 Smartphone BQ Aquaris X5 Smartphone BQ Aquaris X5 Plus Smartphone CAT B15 Smartphone Cubot P11 Smartphone Cubot S500 Smartphone Elephone P8000 Smartphone Emporia Pure Smartphone Gigaset GS160 Smartphone Gigaset ME Smartphone Gigaset ME Pro Smartphone Gigaset ME Pure Smartphone Google Nexus 5 Smartphone Google Nexus 5X Smartphone Google Nexus 6 Smartphone Google Nexus 6P Smartphone Google Pixel -

AT&T Device Unlock Instructions
Last updated: 8/11/20 AT&T Device Unlock Instructions Descargar las instrucciones en español para desbloquear equipos de AT&T (PDF de 513 KB) You must submit a request to unlock your AT&T phone or tablet. Once your request is approved, you’ll get an email or text message with instructions to unlock your device. • Heads up! We can only unlock devices that are locked to the AT&T network. • Submit a request: Go to att.com/deviceunlock to review the requirements and submit an AT&T device unlock request. It may take up to 48 hours to get a response. • Check the status of your request: Check the status at att.com/deviceunlockstatus. Or, use the link we sent you in a text or email to check the status. Good to know: • Can’t find your unlock code? Submit another request and we’ll resend the code. Heads up! There’s a limit to the number times you can try to enter the code to unlock your device. The specific number depends on your device model and manufacturer. • Want to unlock an Apple device? You still have to submit an unlock request for iPhones®, but won’t need an unlock code to complete the process. Plus, iPads® and Apple Watches® are already unlocked, so you don’t have to submit an unlock request for them. • Follow instructions carefully. Use extreme care during the unlock process. If you incorrectly enter an unlock code too many times during the life of the device, you’ll permanently disable the unlock ability. -

Powersound Compatibility List
POWERSOUND COMPATIBILITY LIST BRAND MODELS Apple iPhone 8 (Plus) Apple iPhone X / Apple iPhone XS (Max)/ iPhone XR Apple Apple iPhone 11/ iPhone 11 Pro (Max) Apple iPhone SE 2nd Gen. (2020) Apple 12 (Mini), 12 Pro (Max) Blackberry Blackberry Priv Blackberry Z30 Samsung Galaxy S20/ S20+ (Plus)/ S20 Ultra Samsung Galaxy S10e/ S10 / S10+ (Plus) Samsung Galaxy S9/ S9+ (Plus) Samsung Galaxy S8/ S8+ (Plus) Samsung Galaxy S7/ edge Samsung Galaxy S6/ edge/ edge+ Samsung Samsung Galaxy Z Flip Samsung Galaxy Fold Samsung Z Fold 2 Samsung Galaxy Note 10/ Note 10+ (Plus) Samsung Galaxy Note 5 Samsung Galaxy Note 7 Samsung Galaxy Note 8 Samsung Galaxy Note 9 Google Pixel 3/ Pixel 3 XL Google Pixel 4/ Pixel 4 XL Google Google Pixel 5 Google Nexus 4 Google Nexus 5 Google Nexus 6 Huawei P30 (Pro) Huawei Huawei P40 Pro (Pro+) Huawei Mate 20 Pro Huawei Mate RS OnePlus OnePlus 8 Pro LG V50 / V50 ThinQ LG V40 ThinQ LG G7 ThinQ LG LG G8 ThinQ LG V30 (Plus) LG Optimus F5 Sony Xperia XZ3 Sony Sony Xperia XZ2 Nokia 9 PureView Nokia 8 Sirocco Nokia Lumia 1520 Nokia Nokia Lumia 930 Nokia Lumia 929 / Icon Nokia Lumia 920 Nokia Lumia 830 Nokia Lumia 735 ZTE Axon 10 Pro ZTE Axon 9 Pro Asus PadFone S Others Elephone P9000 Blackview BV6300 Pro Kogan Agora XS Motorola Moto X Force Xiaomi Mi Mix 3 Xiaomi Mi 9 COMPATIBILITY Qi certified phones with appropriate dimensions only. Refer to the list above. WIRELESS CHARGING OUTPUT Up to 10W TRANSMISSION DISTANCE 3-6 mm Wireless charging may not work properly if you have a thick case on your phone. -

The Equipment Pricing Below Is Offered in Association with ELIN EG01 and EG03
The equipment pricing below is offered in association with ELIN EG01 and EG03. Voice Devices Device Price LG Cosmos 3 (VN251S) $0.00* LG Exalt II $79.99 LG Extravert 2 (VN280) $79.99 LG Revere 3 (VN170) $0.00* LG Terra $0.99 Samsung Gusto 3 (Dark Blue SMB311ZKA) $0.00 Kyocera DuraXV $0.00* Camera (KYOE4520) / Non Camera (KYOE4520NC) ** Applies to new activation of service or eligible upgrades on plans with a minimum monthly access of $14.99 or greater (after negotiated discount). Promotional Offer expires June 30, 2016. Push to Talk Devices Device Price Samsung Convoy 3 (SCH-u680MAV) $0.00* Kyocera DuraXV+ $0.00* Camera (KYOE4520PTT) / Non Camera (KYOE4520NCPTT) ** Applies to new activation of service or eligible upgrades on plans with a minimum monthly access of $14.99 or greater (after negotiated discount). Promotional Offer expires June 30, 2016. BlackBerry Devices Device Price BlackBerry Z30 $0.00** (while supplies last) (BBSTA100-3) BlackBerry® Classic 4G LTE $0.00* (Camera- BBSQC100-3)/ (Non Camera- BBSQC100-5) BlackBerry Priv 4G LTE $249.99 (BBSTV100-2) **Applies to new activation of service or eligible upgrades on a primary voice of $15.00 or higher with a required data bolt-on feature or a primary voice and data bundle plan with monthly access fee of $39.99 or higher. Data only Blackberry/Smartphone plans are not eligible. Voice and Data Add-A-Line share plans are eligible provided they meet the minimum access requirement. Promotional offer expires June 30, 2016. Smartphone Devices Device Price HTC Desire 612 4G LTE $19.99 (HTC331ZLVW) -
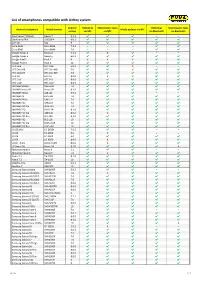
List of Smartphones Compatible with Airkey System
List of smartphones compatible with AirKey system Android Unlocking Maintenance tasks Unlocking Maintenance tasks Android smartphone Model number Media updates via NFC version via NFC via NFC via Bluetooth via Bluetooth Asus Nexus 7 (Tablet) Nexus 7 5.1.1 ✔ ✔ ✔ – – Blackberry PRIV STV100-4 6.0.1 ✔ ✔ ✔ ✔ ✔ CAT S61 S61 9 ✔ ✔ ✔ ✔ ✔ Doro 8035 Doro 8035 7.1.2 – – – ✔ ✔ Doro 8040 Doro 8040 7.0 – – – ✔ ✔ Google Nexus 4 Nexus 4 5.1.1 ✔ X ✔ – – Google Nexus 5 Nexus 5 6.0.1 ✔ ✔ ✔ ✔ ✔ Google Pixel 2 Pixel 2 9 X X X ✔ ✔ Google Pixel 4 Pixel 4 10 ✔ ✔ ✔ ✔ ✔ HTC One HTC One 5.0.2 ✔ ✔ X – – HTC One M8 HTC One M8 6.0 ✔ ✔ X ✔ ✔ HTC One M9 HTC One M9 7.0 ✔ ✔ ✔ ✔ ✔ HTC 10 HTC 10 8.0.0 ✔ X X ✔ ✔ HTC U11 HTC U11 8.0.0 ✔ ✔ ✔ ✔ ✔ HTC U12+ HTC U12+ 8.0.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Mate 9 MHA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI Nexus 6P Nexus 6P 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P8 lite ALE-L21 5.0.1 ✔ ✔ ✔ – – HUAWEI P9 EVA-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P9 lite VNS-L21 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 VTR-L09 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P10 lite WAS-LX1 7.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 EML-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P20 lite ANE-LX1 8.0.0 ✔ X ✔ ✔ ✔ HUAWEI P20 Pro CLT-L29 8.1.0 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 ELE-L29 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 lite MAR-LX1A 10 ✔ ✔ ✔ ✔ ✔ HUAWEI P30 Pro VOG-L29 10 ✔ ✔ ✔ ✔ ✔ LG G2 Mini LG-D620r 5.0.2 ✔ ✔ ✔ – – LG G3 LG-D855 5.0 ✔ X ✔ – – LG G4 LG-H815 6.0 ✔ ✔ ✔ ✔ ✔ LG G6 LG-H870 8.0.0 ✔ X ✔ ✔ ✔ LG G7 ThinQ LM-G710EM 8.0.0 ✔ X ✔ ✔ ✔ LG Nexus 5X Nexus 5X 8.1.0 ✔ ✔ ✔ ✔ X Motorola Moto X Moto X 5.1 ✔ ✔ ✔ – – Motorola Nexus 6 Nexus 6 7.0 ✔ X ✔ ✔ ✔ Nokia 7.1 TA-1095 8.1.0 ✔ ✔ X ✔ ✔ Nokia 7.2 TA-1196 10 ✔ ✔ ✔ -

In the United States District Court for the Northern District of Texas Dallas Division
IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION UNILOC 2017 LLC, Case No. Plaintiff, PATENT CASE v. BLACKBERRY CORPORATION, JURY TRIAL DEMANDED Defendant. COMPLAINT FOR PATENT INFRINGEMENT Plaintiff, Uniloc 2017 LLC (“Uniloc”), for its complaint against defendant, Blackberry Corporation (“Blackberry”), alleges: THE PARTIES 1. Uniloc 2017 LLC is a Delaware limited liability company, having addresses at 1209 Orange Street, Wilmington, Delaware 19801; 620 Newport Center Drive, Newport Beach, California 92660; and 102 N. College Avenue, Suite 303, Tyler, Texas 75702. 2. Blackberry is a Delaware corporation, having a regular and established place of business in Irving, Texas. Blackberry may be served with process through its registered agent for service in Texas: Corporate Creations Network, Inc., 2425 W. Loop South, #200, Houston, Texas 77027. 3. Blackberry makes, uses, offers for sale, sells, and imports products into the United States for sale to customers in this judicial district, including those accused of infringement. 3079222.v1 JURISDICTION 4. Uniloc brings this action for patent infringement under the patent laws of the United States, 35 U.S.C. § 271, et seq. This Court has subject matter jurisdiction under 28 U.S.C. §§ 1331 and 1338(a). CLAIM FOR PATENT INFRINGEMENT 5. Uniloc is the owner, by assignment, of U.S. Patent No. 7,020,106 (“the ’106 Patent”), entitled RADIO COMMUNICATION SYSTEM, which issued March 28, 2006. A copy of the ’106 Patent is attached as Exhibit A. 6. The ’106 Patent describes in detail, and claims in various ways, inventions in systems and devices developed by Koninklijke Philips Electronics N.V. -

Trouble Shooting Guide
TROUBLE SHOOTING GUIDE Does not track activity if wearing as a necklace. It's necessary to ensure that the customer has selected the correct placement of the Leaf in the app. The Leaf will adjust its activity and sleep tracking algorithms according to the position in the app’s Settings. So if the customer wear the Leaf as a bracelet, they will need to select its placement in the app’s Settings and sync their Leaf to transfer these new settings to the Leaf itself. This step greatly affects the Leaf’s accuracy and is a common user error in reports of the Leaf not tracking accurately. It doesn't sync right with the phone This can be a simple error on the user’s side or a Bluetooth issue with certain phones. Several Android devices have proved to have more common issues connecting to the Leaf via Bluetooth, which we have stated in Amazon product description as a warning, as well as our official support page support.bellabeat.com. Issues can differentiate from case to case. If the customer has a Samsung Galaxy Note 4, Samsung Galaxy S5, Samsung Galaxy S6 Active, Samsung Galaxy A3, Galaxy J7, Nexus 6 or Blackberry Priv, we would recommend that they try the troubleshooting steps once again. They can be found at support.bellabeat.com (direct link). Basic troubleshooting steps consist of turning off the Bluetooth, turning off and on Wifi and rebooting the phone, while in some cases we might require a simple firmware update in the app (if possible). Our technical team at [email protected] would be happy to look into this.