LG V20 and G5 Smartphones
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

In the United States District Court for the Eastern District of Texas Marshall Division
Case 2:18-cv-00343-JRG Document 24 Filed 12/12/18 Page 1 of 32 PageID #: 142 IN THE UNITED STATES DISTRICT COURT FOR THE EASTERN DISTRICT OF TEXAS MARSHALL DIVISION EVS CODEC TECHNOLOGIES, LLC and § SAINT LAWRENCE COMMUNICATIONS, § LLC, § § Plaintiffs, Case No. 2:18-cv-00343-JRG § v. § § JURY TRIAL DEMANDED LG ELECTRONICS, INC., LG § ELECTRONICS U.S.A., INC., and LG ELECTRONICS MOBILECOMM U.S.A., § INC., § § Defendants. § § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Case 2:18-cv-00343-JRG Document 24 Filed 12/12/18 Page 2 of 32 PageID #: 143 EVS Codec Technologies, LLC (“ECT”) and Saint Lawrence Communications, LLC (“SLC”) (collectively “Plaintiffs”) hereby submit this First Amended Complaint for patent infringement against Defendants LG Electronics, Inc. (“LGE”), LG Electronics U.S.A., Inc. (“LGUSA”), and LG Electronics Mobilecomm U.S.A., Inc. (“LGEM”) (collectively “LG” or “Defendants”) and state as follows: THE PARTIES 1. ECT is a Texas limited liability company with a principal place of business at 2323 S. Shepherd, 14th floor, Houston, Texas 77019-7024. 2. SLC is a Texas limited liability company, having a principal place of business at 6136 Frisco Square Blvd., Suite 400, Frisco, Texas 75034. 3. On information and belief, Defendant LGE is a Korean corporation with a principal place of business at LG Twin Towers, 128 Yeoui-daero, Yeongdungpo-gu, Seoul, 07366, South Korea. On information and belief, LGE is the entity that manufactures the LG-branded products sold in the United States, including the accused products in this case. On information and belief, in addition to making the products, LGE is responsible for research and development, product design, and sourcing of components. -

Tarifas De Servicio/ Deducibles T-Mobile®
Tarifas de servicio/ deducibles T-Mobile® Las tarifas de servicio/deducibles a continuación se aplican a los siguientes programas: JUMP! Plus™ Protección Premium Plus para Dispositivos Nivel 1 Nivel 2 Nivel 3 Tarifa de servicio: $20 por reclamo Tarifa de servicio: $20 por reclamo Tarifa de servicio: $20 por reclamo para daño accidental para daño accidental para daño accidental Deducible: $20 por reclamo Deducible: $50 por reclamo Deducible: $100 por reclamo para pérdida y robo para pérdida y robo para pérdida y robo Cargo por equipo no recuperado: Cargo por equipo no recuperado: Cargo por equipo no recuperado: hasta $200 hasta $300 hasta $500 ALCATEL A30 ALCATEL ONETOUCH Fierce XL LG G Stylo ALCATEL Aspire ALCATEL ONETOUCH POP 7 Samsung Galaxy Tab A 8.0 ALCATEL GO FLIP HTC Desire 530 Samsung Gear S2 ALCATEL LinkZone Hotspot HTC Desire 626s ALCATEL ONETOUCH POP Astro LG G Pad F Coolpad Catalyst LG G Pad X 8.0 Coolpad Rogue LG K10 Kyocera Rally LG K20 LG 450 LG Stylo 3 Plus LG Aristo LG Stylo Plus LG K7 Kyocera Hydro Wave C6740 LG Leon LTE Microsoft Lumia 640 Microsoft Lumia 435 Samsung Galaxy Core Prime T-Mobile LineLink Samsung Galaxy Grand Prime ZTE Avid Plus Samsung Galaxy J3 Prime ZTE Avid Trio Samsung Galaxy J7 ZTE Cymbal Samsung Galaxy Tab E ZTE Falcon Z-917 Hotspot ZTE SyncUp DRIVE ZTE Obsidian ZTE Quartz ZTE Zmax Pro Nivel 4 Nivel 5 Tarifa de servicio: $99 por reclamo Tarifa de servicio: $99 por reclamo para daño accidental para daño accidental Deducible: $150 por reclamo Deducible: $175 por reclamo para pérdida y robo para pérdida -

Case 5:18-Cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11
Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. 3:18-cv-00560-DCG § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. and § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their First Amended Complaint against defendant, LG Electronics U.S.A. (“LGE”), Inc., LG Electronics Mobilecomm U.S.A., Inc., and LG Electronics, Inc., (“LG Korea”) (together “LG”), allege as follows:1 THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 1 An amended complaint supersedes the original complaint and renders it of no legal effect, King v. Dogan, 31 F.3d 344. 346 (5th Cir. 1994), rendering a motion to dismiss the original complaint moot. See, e.g., Mangum v. United Parcel Services, No. 3:09-cv-0385, 2009 WL 2700217 (N.D. Tex. Aug. 26, 2009). 2988606.v1 Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 2 of 11 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. -

4 Connect the Battery to the LG CAM Plus By
GETTING STARTED Plug into your Slide in the CAM Plus for more control when taking shots, and get a grip on the ins and outs of setup and usage. HOW TO CONNECT THE CAM PLUS TO YOUR LG G5 2 1 ® Turn off the LG G5 and hold it with the screen Press the module release button (1) and Disconnect the battery from the module by 1 facing you. 2 pull the battery module out to remove it from 3 pulling it in an outward arc. your phone (2). Connect the battery to the LG CAM Plus by Carefully slide the battery and the LG CAM 4 lining up the arrows and snapping it in. 5 Plus module into the phone until it’s closed. You should hear a slight click when it’s secured. Notes: The LG CAM Plus will not operate normally if your LG G5 and LG CAM Plus are supported by different countries or operators. Please ensure your LG CAM Plus matches your service provider. (Module # 720 – AT&T; Module # 700 – Sprint, Verizon, ACG, T-Mobile, U.S. Cellular) All materials in this instruction sheet including, without limitation, the design and the text are the property of LG Electronics MobileComm U.S.A., Inc. Copyright © 2016 LG Electronics MobileComm U.S.A., Inc. ALL RIGHTS RESERVED. LG, LG Life’s Good, and the LG Logo are registered trademarks of LG Corp. Other trademarks and trade names are those of their respective owners. Screen shots are simulated and subject to change. All features, functionality, and other product specifications are subject to change without notice. -

User Guide. Guía Del Usuario
MFL69395901(1.0) ME MFL69395901(1.0) Guía del usuario. User guide. User User guide. User This booklet is made from 98% post-consumer recycled paper. This booklet is printed with soy ink. Printed in Mexico Copyright©2016 LG Electronics, Inc. All rights reserved. LG and the LG logo are registered trademarks of LG Corp. G5 is a trademark of LG Electronics, Inc. All other trademarks are the property of their respective owners. Important Customer Information 1 Before you begin using your new phone Included in the box with your phone are separate information leaflets. These leaflets provide you with important information regarding your new device. Please read all of the information provided. This information will help you to get the most out of your phone, reduce the risk of injury, avoid damage to your device, and make you aware of legal regulations regarding the use of this device. It’s important to review the Product Safety and Warranty Information guide before you begin using your new phone. Please follow all of the product safety and operating instructions and retain them for future reference. Observe all warnings to reduce the risk of injury, damage, and legal liabilities. 2 Table of Contents Important Customer Information...............................................1 Table of Contents .......................................................................2 The Basics...................................................................................5 Phone Overview ................................................................................................... -

Lg G5 “Friends” Companion Devices Launch in Us
www.LG.com LG G5 “FRIENDS” COMPANION DEVICES LAUNCH IN US Available Now, LG CAM Plus, LG 360 CAM, LG 360 VR, LG TONE via Carriers, Retailers and on LG.COM ENGLEWOOD CLIFFS, N.J., May 24 2016 — Beginning today, LG Electronics’ (LG) customers in the US can get their hands on the highly anticipated LG G5 “Friends” companion devices, including the LG CAM Plus, LG 360 CAM, LG 360 VR and LG TONE Platinum™ on LG.com. The recently launched LG G5 smartphone showcases a new modular design that lets owners easily add LG Friends to transform the G5 into a DSLR-inspired camera, mobile virtual reality viewer and even a 360 video camera. The LG Friends are available now via major US carriers and at retail locations as well as the expanded LG online store – a destination to find great products that help customers get the most out of their favorite LG smartphones. LG.com will also serve as a way to order LG G5 batteries and new charging cradles in the coming weeks – which can be used to charge the G5. In addition, the online store offers batteries and charging cradles for beloved products such as the LG G3, LG G4, and LG V10*. For a limited time only, the store will be rewarding loyal customers with several promotions to celebrate some of LG’s most successful products and innovations. Consumers can take advantage of deep discounts including up to 70 percent off MSRP for, G4 and V10 battery and charger bundles starting for as low as $20.** “The LG ‘Friends’ make the G5 so much more than any other phone on the market. -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

California Proposition 65
AT&T Wireless Handsets, Tablets, Wearables and other Connected Wireless Products California Proposition 65 If you received a Proposition 65 warning on your receipt, packing slip or email confirmation document, please see the following list of products to determine which product you purchased is subject to the warning. Manufacturer SKU Marketing Name and/or model # ASUS 6588A ASUS PadFone X mini Black ASUS 6593A ASUS PadFone X mini Black ASUS 6594A ASUS PadFone X mini Black ASUS R588A ASUS PadFone X mini Black - certified like new ASUS R593A ASUS PadFone X mini Black - certified like new ASUS R594A ASUS PadFone X mini Black - certified like new ASUS S588A ASUS PadFone X mini Black - warranty replacement ASUS S593A ASUS PadFone X mini Black - warranty replacement ASUS S594A ASUS PadFone X mini Black - warranty replacement ASUS 6768A ASUS ZenFone 2E White ASUS 6769A ASUS ZenFone 2E White ASUS 6770A ASUS ZenFone 2E White ASUS R768A ASUS ZenFone 2E White - certified like new ASUS R769A ASUS ZenFone 2E White - certified like new ASUS R770A ASUS ZenFone 2E White - certified like new ASUS S768A ASUS ZenFone 2E White - warranty replacement ASUS S769A ASUS ZenFone 2E White - warranty replacement ASUS S770A ASUS ZenFone 2E White - warranty replacement ASUS 6722A ASUS MeMO Pad 7 LTE (ME375CL) -BLK ASUS 6723A ASUS MeMO Pad 7 LTE (ME375CL) -BLK ASUS 6725A ASUS MeMO Pad 7 LTE (ME375CL) -BLK May 18, 2016 © 2016 AT&T Intellectual Property. All rights reserved. AT&T and the Globe logo are registered trademarks of AT&T Intellectual Property. AT&T Wireless -

Qualcomm® Quick Charge™ Technology Device List
One charging solution is all you need. Waiting for your phone to charge is a thing of the past. Quick Charge technology is ® designed to deliver lightning-fast charging Qualcomm in phones and smart devices featuring Qualcomm® Snapdragon™ mobile platforms ™ and processors, giving you the power—and Quick Charge the time—to do more. Technology TABLE OF CONTENTS Quick Charge 5 Device List Quick Charge 4/4+ Quick Charge 3.0/3+ Updated 09/2021 Quick Charge 2.0 Other Quick Charge Devices Qualcomm Quick Charge and Qualcomm Snapdragon are products of Qualcomm Technologies, Inc. and/or its subsidiaries. Devices • RedMagic 6 • RedMagic 6Pro Chargers • Baseus wall charger (CCGAN100) Controllers* Cypress • CCG3PA-NFET Injoinic-Technology Co Ltd • IP2726S Ismartware • SW2303 Leadtrend • LD6612 Sonix Technology • SNPD1683FJG To learn more visit www.qualcomm.com/quickcharge *Manufacturers may configure power controllers to support Quick Charge 5 with backwards compatibility. Power controllers have been certified by UL and/or Granite River Labs (GRL) to meet compatibility and interoperability requirements. These devices contain the hardware necessary to achieve Quick Charge 5. It is at the device manufacturer’s discretion to fully enable this feature. A Quick Charge 5 certified power adapter is required. Different Quick Charge 5 implementations may result in different charging times. Devices • AGM X3 • Redmi K20 Pro • ASUS ZenFone 6* • Redmi Note 7* • Black Shark 2 • Redmi Note 7 Pro* • BQ Aquaris X2 • Redmi Note 9 Pro • BQ Aquaris X2 Pro • Samsung Galaxy -

T-Mobile® Service Fee and Deductible Schedule
T-Mobile® Service Fee and Deductible Schedule The service fees/deductibles apply to the following programs: JUMP! Plus Premium Device Protection Plus Tier 1 Tier 3 Tier 5 Service Fee: $20 per claim for accidental damage Service Fee: $20 per claim for accidental damage Service Fee: $99 per claim for accidental damage Deductible: $20 per claim for loss and theft Deductible: $100 per claim for loss and theft Deductible: $175 per claim for loss and theft Unrecovered Equipment Fee: up to $200 Unrecovered Equipment Fee: up to $500 Unrecovered Equipment Fee: up to $900 ALCATEL A30 LG G Stylo Apple iPad Air 2 - 16 / 64 / 128GB ALCATEL Aspire LG G Pad X2 8.0 Plus Apple iPad mini 4 - 64 / 128GB ALCATEL GO FLIP Samsung Galaxy Tab A 8.0 Apple iPad Pro 9.7-inch - 32 / 128 / 256GB ALCATEL LinkZone Hotspot Samsung Gear S2 Apple iPad Pro 10.5-inch - 128GB ALCATEL ONETOUCH POP Astro Apple iPad Pro 12.9-inch - 256GB Coolpad Catalyst Apple iPhone 6s - 16 / 32 / 64 / 128GB Coolpad Rogue Apple iPhone 6s Plus - 16 / 32 / 64 / 128GB Kyocera Rally Apple iPhone 7 - 32 / 128 / 256GB LG Aristo Apple iPhone 7 Plus - 32 / 128 / 256GB LG K7 Apple iPhone 8 - 64 / 256GB LG K20 Apple iPhone 8 Plus - 64 / 256GB LG Leon LTE Apple Watch Series 3 Stainless Steel Case Microsoft Lumia 435 BlackBerry Priv Samsung Galaxy J3 Prime HTC One M9 T-Mobile LineLink HTC 10 T-Mobile REVVL LG G4 ZTE Avid Plus LG G5 ZTE Avid Trio LG G6 ZTE Cymbal LG V10 ZTE Falcon Z-917 Hotspot LG V30 ZTE Obsidian moto z2 force ZTE Zmax Pro Samsung Galaxy Note 5 - 32 / 64GB Samsung Galaxy Note 7 - 64GB -
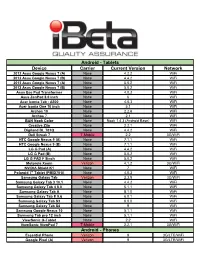
Device Carrier Current Version Network Android
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel 3 XL None 9 3G/LTE/WiFi HTC Desire (International) -

Amazon Amazon Fire Apple Iphone 5, Ipad 4, Ipad Mini, Iphone 5C
Amazon Amazon Fire Apple iPhone 5, iPad 4, iPad Mini, iPhone 5c, iPhone 5s, iPad Air, iPad Mini 2/3, iPad Air 2, iPhone 6 Plus, iPhone 6, iPhone 6s, iPhone 6s Plus, iPhone SE, iPhone 7, iPhone 7 Plus, iPhone 8, iPhone 8 Plus, iPhone X BlackBerry Storm II / 9550, Flip 8220/8230, 8900, Curve 8520 / 8530, Curve 9360, Curve 9380, Bold 9790, Curve 9370, Curve 9310, Z10, Q10, Z30, Tour 9630, Classic Google Pixel 4, Pixel 4 XL HTC Nexus One, Trophy, Droid Incredible 2, Inspire 4G, Merge, myTouch 4G, Sensation 4G, Wildfire, Wildfire S, Titan, Rhyme, Sensation XE, Vivid, Rezound, One S, Windows Phone 8X, One X, Evo 4G LTE, Droid DNA, One SV, One VX, One, One Mini, EVO 4G, EVO Shift 4G, HD2, Desire, EVO 3D, HD7, One (E8), One Remix/One Mini 2, One M8 LG Lotus, Revolution, Thrive, Optimus M MS690, Optimus S LS670, Optimus T P509, Optimus U US670, Optimus V VM670, Select MN180, UX-300, Vortex VS660, Revere, Thrill/ Optimus 3D, Optimus Hub, Marquee, Ignite, Nitro HD, Optimus 2, Optimus LTE, Optimus Slider, Optimus Sol, Optimus One, Spectrum, Connect 4G, Venice, Intuition, Nexus 4, Lucid, Lucid 2, Optimus F7, Optimus Zone, Enact, G2, Nexus 5, LG G3, LG G4, LG G5 Motorola Defy MB525, Droid 2 Global, DROID BIONIC XT865, Droid Pro A957, Droid RAZR, DROID RAZR MAXX, DROID 4, Motoluxe, Photon Q, Droid RAZR HD, Droid RAZR MAXX HD, Droid RAZR M, Droid Mini, Droid Ultra, Droid Maxx, Moto X, Electrify M, Electrify 2, Moto G, Devour A555, ATRIX 4G MB860, Backflip, Moto E, Droid Turbo, Google Nexus 6 Nokia E71, E72, N78, N81, N85, N86 8MP, N900, E63, 800, 710,