Network Tetris an Interactive Peer to Peer Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Studio Showcase
Contacts: Holly Rockwood Tricia Gugler EA Corporate Communications EA Investor Relations 650-628-7323 650-628-7327 [email protected] [email protected] EA SPOTLIGHTS SLATE OF NEW TITLES AND INITIATIVES AT ANNUAL SUMMER SHOWCASE EVENT REDWOOD CITY, Calif., August 14, 2008 -- Following an award-winning presence at E3 in July, Electronic Arts Inc. (NASDAQ: ERTS) today unveiled new games that will entertain the core and reach for more, scheduled to launch this holiday and in 2009. The new games presented on stage at a press conference during EA’s annual Studio Showcase include The Godfather® II, Need for Speed™ Undercover, SCRABBLE on the iPhone™ featuring WiFi play capability, and a brand new property, Henry Hatsworth in the Puzzling Adventure. EA Partners also announced publishing agreements with two of the world’s most creative independent studios, Epic Games and Grasshopper Manufacture. “Today’s event is a key inflection point that shows the industry the breadth and depth of EA’s portfolio,” said Jeff Karp, Senior Vice President and General Manager of North American Publishing for Electronic Arts. “We continue to raise the bar with each opportunity to show new titles throughout the summer and fall line up of global industry events. It’s been exciting to see consumer and critical reaction to our expansive slate, and we look forward to receiving feedback with the debut of today’s new titles.” The new titles and relationships unveiled on stage at today’s Studio Showcase press conference include: • Need for Speed Undercover – Need for Speed Undercover takes the franchise back to its roots and re-introduces break-neck cop chases, the world’s hottest cars and spectacular highway battles. -

Fighting Games, Performativity, and Social Game Play a Dissertation
The Art of War: Fighting Games, Performativity, and Social Game Play A dissertation presented to the faculty of the Scripps College of Communication of Ohio University In partial fulfillment of the requirements for the degree Doctor of Philosophy Todd L. Harper November 2010 © 2010 Todd L. Harper. All Rights Reserved. This dissertation titled The Art of War: Fighting Games, Performativity, and Social Game Play by TODD L. HARPER has been approved for the School of Media Arts and Studies and the Scripps College of Communication by Mia L. Consalvo Associate Professor of Media Arts and Studies Gregory J. Shepherd Dean, Scripps College of Communication ii ABSTRACT HARPER, TODD L., Ph.D., November 2010, Mass Communications The Art of War: Fighting Games, Performativity, and Social Game Play (244 pp.) Director of Dissertation: Mia L. Consalvo This dissertation draws on feminist theory – specifically, performance and performativity – to explore how digital game players construct the game experience and social play. Scholarship in game studies has established the formal aspects of a game as being a combination of its rules and the fiction or narrative that contextualizes those rules. The question remains, how do the ways people play games influence what makes up a game, and how those players understand themselves as players and as social actors through the gaming experience? Taking a qualitative approach, this study explored players of fighting games: competitive games of one-on-one combat. Specifically, it combined observations at the Evolution fighting game tournament in July, 2009 and in-depth interviews with fighting game enthusiasts. In addition, three groups of college students with varying histories and experiences with games were observed playing both competitive and cooperative games together. -
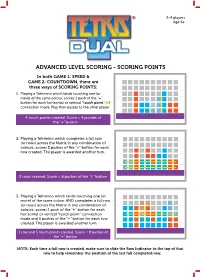
Advanced Level Scoring - Scoring Points
® 2-4 players Age 6+ ADVANCED LEVEL SCORING - SCORING POINTS In both GAME 1: SPEED & GAME 2: COUNTDOWN, there are three ways of SCORING POINTS: 1. Playing a Tetrimino which lands touching one (or more) of the same colour, scores 1 push of the “+” button for each horizontal or vertical “touch point” ( ) connection made. Play then passes to the other player. 4 touch points created. Score = 4 pushes of the “+” button 2. Playing a Tetrimino which completes a full row (or rows) across the Matrix in any combination of colours, scores 3 pushes of the “+” button for each row created. The player is awarded another turn. 2 rows created. Score = 6 pushes of the “+” button 3. Playing a Tetrimino which lands touching one (or more) of the same colour AND completes a full row (or rows) across the Matrix in any combination of colours, scores 1 push of the “+” button for each horizontal or vertical “touch point” connection made and 3 pushes of the “+” button for each row created. The player is awarded another turn. 1 row and 5 touch points created. Score = 8 pushes of the “+” button NOTE: Each time a full row is created, make sure to slide the Row Indicator to the top of that row to help remember the position of the last full completed row. ADVANCED LEVEL SCORING - LOSING POINTS In the advanced game, LOSING POINTS are played exactly as the standard rules. 1. For playing a Tetrimino which lands leaving an unfillable hole(s) below it ( ), the player must press the “-“ button 1 time for EACH hole created. -

Electronic Arts V. Zynga: Real Dispute Over Virtual Worlds Jennifer Kelly and Leslie Kramer
Electronic Arts v. Zynga: Real Dispute Over Virtual Worlds jennifer kelly and leslie kramer Electronic Arts Inc.’s (“EA”) recent lawsuit against relates to these generally accepted categories of Zynga Inc. (“Zynga”) filed in the Northern District of protectable content, thereby giving rise to a claim for California on August 3, 2012 is the latest in a string of infringement, is not as easy as one might think. disputes where a video game owner has asserted that an alleged copycat game has crossed the line between There are a couple of reasons for this. First, copying of lawful copying and copyright infringement. See N.D. games has become so commonplace in today’s game Cal. Case No. 3:12-cv-04099. There, EA has accused industry (insiders refer to the practice as “fast follow”) Zynga of infringing its copyright in The Sims Social, that often it is hard to determine who originated which is EA’s Facebook version of its highly successful the content at issue. A common—and surprisingly PC and console-based game, The Sims. Both The Sims effective—defense is that the potential plaintiff itself and The Sims Social are virtual world games in which copied the expression from some other game (or the player simulates the daily activities of one or perhaps, a book or a film), and thus, has no basis more virtual characters in a household located in the to assert a claim over that content. In this scenario, fictional town of SimCity. In the lawsuit, EA contends whether the alleged similarities between the two that Zynga’s The Ville, released for the Facebook games pertain to protectable expression becomes, platform in June 2012, copies numerous protectable frankly, irrelevant. -

The Game of Tetris in Machine Learning
The Game of Tetris in Machine Learning Simon´ Algorta 1 Ozg¨ ur¨ S¸ims¸ek 2 Abstract proaches to other games and to real-world problems. In the Appendix we provide a table of the algorithms reviewed The game of Tetris is an important benchmark and a description of the features used. for research in artificial intelligence and ma- chine learning. This paper provides a histori- cal account of the algorithmic developments in 2. The Game of Tetris Tetris and discusses open challenges. Hand- Tetris is one of the most well liked video games of all time. crafted controllers, genetic algorithms, and rein- It was created by Alexey Pajitnov in the USSR in 1984. forcement learning have all contributed to good It quickly turned into a popular culture icon that ignited solutions. However, existing solutions fall far copyright battles amid the tensions of the final years of the short of what can be achieved by expert players Cold War (Temple, 2004). playing without time pressure. Further study of the game has the potential to contribute to impor- The game is played on a two-dimensional grid, initially tant areas of research, including feature discov- empty. The grid gradually fills up as pieces of different ery, autonomous learning of action hierarchies, shapes, called Tetriminos, fall from the top, one at a time. and sample-efficient reinforcement learning. The player can control how each Tetrimino lands by rotat- ing it and moving it horizontally, to the left or to the right, any number of times, as it falls one row at a time until one 1. -

Project Design: Tetris
Project Design: Tetris Prof. Stephen Edwards Spring 2020 Arsalaan Ansari (aaa2325) Kevin Rayfeng Li (krl2134) Sooyeon Jo (sj2801) Josh Learn (jrl2196) Introduction The purpose of this project is to build a Tetris video game system using System Verilog and C language on a FPGA board. Our Tetris game will be a single player game where the computer randomly generates tetromino blocks (in the shapes of O, J, L, Z, S, I) that the user can rotate using their keyboard. Tetrominoes can be stacked to create lines that will be cleared by the computer and be counted as points that will be tracked. Once a tetromino passes the boundary of the screen the user will lose. Fig 1: Screenshot from an online implementation of Tetris User input will come through key inputs from a keyboard, and the Tetris sprite based output will be displayed using a VGA display. The System Verilog code will create the sprite based imagery for the VGA display and will communicate with the C language game logic to change what is displayed. Additionally, the System Verilog code will generate accompanying audio that will supplement the game in the form of sound effects. The C game logic will generate random tetromino blocks to drop, translate key inputs to rotation of blocks, detect and clear lines, determine what sound effects to be played, keep track of the score, and determine when the game has ended. Architecture The figure below is the architecture for our project Fig 2: Proposed architecture Hardware Implementation VGA Block The Tetris game will have 3 layers of graphics. -

Newagearcade.Com 5000 in One Arcade Game List!
Newagearcade.com 5,000 In One arcade game list! 1. AAE|Armor Attack 2. AAE|Asteroids Deluxe 3. AAE|Asteroids 4. AAE|Barrier 5. AAE|Boxing Bugs 6. AAE|Black Widow 7. AAE|Battle Zone 8. AAE|Demon 9. AAE|Eliminator 10. AAE|Gravitar 11. AAE|Lunar Lander 12. AAE|Lunar Battle 13. AAE|Meteorites 14. AAE|Major Havoc 15. AAE|Omega Race 16. AAE|Quantum 17. AAE|Red Baron 18. AAE|Ripoff 19. AAE|Solar Quest 20. AAE|Space Duel 21. AAE|Space Wars 22. AAE|Space Fury 23. AAE|Speed Freak 24. AAE|Star Castle 25. AAE|Star Hawk 26. AAE|Star Trek 27. AAE|Star Wars 28. AAE|Sundance 29. AAE|Tac/Scan 30. AAE|Tailgunner 31. AAE|Tempest 32. AAE|Warrior 33. AAE|Vector Breakout 34. AAE|Vortex 35. AAE|War of the Worlds 36. AAE|Zektor 37. Classic Arcades|'88 Games 38. Classic Arcades|1 on 1 Government (Japan) 39. Classic Arcades|10-Yard Fight (World, set 1) 40. Classic Arcades|1000 Miglia: Great 1000 Miles Rally (94/07/18) 41. Classic Arcades|18 Holes Pro Golf (set 1) 42. Classic Arcades|1941: Counter Attack (World 900227) 43. Classic Arcades|1942 (Revision B) 44. Classic Arcades|1943 Kai: Midway Kaisen (Japan) 45. Classic Arcades|1943: The Battle of Midway (Euro) 46. Classic Arcades|1944: The Loop Master (USA 000620) 47. Classic Arcades|1945k III 48. Classic Arcades|19XX: The War Against Destiny (USA 951207) 49. Classic Arcades|2 On 2 Open Ice Challenge (rev 1.21) 50. Classic Arcades|2020 Super Baseball (set 1) 51. -

Full Games List Pandora DX 3000 in 1
www.myarcade.com.au Ph 0412227168 Full Games List Pandora DX 3000 in 1 1. 10-YARD FIGHT – (1/2P) – (1464) 38. ACTION 52 – (1/2P) – (2414) 2. 16 ZHANG MA JIANG – (1/2P) – 39. ACTION FIGHTER – (1/2P) – (1093) (2391) 40. ACTION HOLLYWOOOD – (1/2P) – 3. 1941 : COUNTER ATTACK – (1/2P) – (362) (860) 41. ADDAMS FAMILY VALUES – (1/2P) – 4. 1942 – (1/2P) – (861) (2431) 5. 1942 – AIR BATTLE – (1/2P) – (1140) 42. ADVENTUROUS BOY-MAO XIAN 6. 1943 : THE BATTLE OF MIDWAY – XIAO ZI – (1/2P) – (2266) (1/2P) – (862) 43. AERO FIGHTERS – (1/2P) – (927) 7. 1943 KAI : MIDWAY KAISEN – (1/2P) 44. AERO FIGHTERS 2 – (1/2P) – (810) – (863) 45. AERO FIGHTERS 3 – (1/2P) – (811) 8. 1943: THE BATTLE OF MIDWAY – 46. AERO FIGHTERS 3 BOSS – (1/2P) – (1/2P) – (1141) (812) 9. 1944 : THE LOOP MASTER – (1/2P) 47. AERO FIGHTERS- UNLIMITED LIFE – (780) – (1/2P) – (2685) 10. 1945KIII – (1/2P) – (856) 48. AERO THE ACRO-BAT – (1/2P) – 11. 19XX : THE WAR AGAINST DESTINY (2222) – (1/2P) – (864) 49. AERO THE ACRO-BAT 2 – (1/2P) – 12. 2 ON 2 OPEN ICE CHALLENGE – (2624) (1/2P) – (1415) 50. AERO THE ACRO-BAT 2 (USA) – 13. 2020 SUPER BASEBALL – (1/2P) – (1/2P) – (2221) (1215) 51. AFTER BURNER II – (1/2P) – (1142) 14. 3 COUNT BOUT – (1/2P) – (1312) 52. AGENT SUPER BOND – (1/2P) – 15. 4 EN RAYA – (1/2P) – (1612) (2022) 16. 4 FUN IN 1 – (1/2P) – (965) 53. AGGRESSORS OF DARK KOMBAT – 17. 46 OKUNEN MONOGATARI – (1/2P) (1/2P) – (106) – (2711) 54. -
Downloadable Tetris Game Free Tetris Download
downloadable tetris game free Tetris Download. Types of the game are listed from the simplest to the hardest. Even small kids can play in the Simple Tetris mode, but playing Mutatix and Crazy is for extreme Tetris players in general. You will find friendly interface, nice sounds, music, large High scores table and World Records Table in this Tetris game. Also before writing your name to High Scores you can choose a pleased face from the list of more than 200 funny faces. The goal of the Tetris game is to maximize your score by placing the falling blocks or triangles into lines. Every assembled line that has disappeared increases your score. If you are a Tetris fan, you should download Crazy Tetris game! Free download Tetris and enjoy playing it for hours and even days! Tetris is a really good game for having some rest after work! Tetris Download. Do you want to play Crazy Tetris? Here you can free download Tetris for Windows. To download this action puzzle game click on the link below: Supported Tetris Languages. Crazy Tetris game has multilingual interface. Supported Languages: Bulgarian, Catalan, Chinese, Dutch, English, French, German, Greek, Hungarian, Portuguese (Brazilian), Russian, Spanish, Swedish, Ukrainian. Pentium 166 or better Operating system: Windows 95/98/Me/NT4/2000/XP/Vista/7/8/8.1/10 Video card with high color mode. Distribution. The SHAREWARE version of the Crazy Tetris is free distributed. You may free download and use the SHAREWARE version free of charge for 30 days. If after 30 days you would like to continue using Crazy Tetris game, then you should register Tetris. -

10-Yard Fight 1942 1943
10-Yard Fight 1942 1943 - The Battle of Midway 2048 (tsone) 3-D WorldRunner 720 Degrees 8 Eyes Abadox - The Deadly Inner War Action 52 (Rev A) (Unl) Addams Family, The - Pugsley's Scavenger Hunt Addams Family, The Advanced Dungeons & Dragons - DragonStrike Advanced Dungeons & Dragons - Heroes of the Lance Advanced Dungeons & Dragons - Hillsfar Advanced Dungeons & Dragons - Pool of Radiance Adventure Island Adventure Island II Adventure Island III Adventures in the Magic Kingdom Adventures of Bayou Billy, The Adventures of Dino Riki Adventures of Gilligan's Island, The Adventures of Lolo Adventures of Lolo 2 Adventures of Lolo 3 Adventures of Rad Gravity, The Adventures of Rocky and Bullwinkle and Friends, The Adventures of Tom Sawyer After Burner (Unl) Air Fortress Airwolf Al Unser Jr. Turbo Racing Aladdin (Europe) Alfred Chicken Alien 3 Alien Syndrome (Unl) All-Pro Basketball Alpha Mission Amagon American Gladiators Anticipation Arch Rivals - A Basketbrawl! Archon Arkanoid Arkista's Ring Asterix (Europe) (En,Fr,De,Es,It) Astyanax Athena Athletic World Attack of the Killer Tomatoes Baby Boomer (Unl) Back to the Future Back to the Future Part II & III Bad Dudes Bad News Baseball Bad Street Brawler Balloon Fight Bandai Golf - Challenge Pebble Beach Bandit Kings of Ancient China Barbie (Rev A) Bard's Tale, The Barker Bill's Trick Shooting Baseball Baseball Simulator 1.000 Baseball Stars Baseball Stars II Bases Loaded (Rev B) Bases Loaded 3 Bases Loaded 4 Bases Loaded II - Second Season Batman - Return of the Joker Batman - The Video Game -

Catalogo Nintendo Switch
Inverno 2020/2021 OMAGGIO Che cos'è Nintendo Switch? Nintendo Switch è una console per giocare dove, quando e con chi vuoi La famiglia Nintendo Switch comprende due console Nintendo Switch – pensata per giocare a casa oppure dove vuoi Tre modi di giocare Modalità TV Modalità da tavolo Modalità portatile p.06 ~ p.09 Nintendo Switch Lite pensata per giocare in mobilità p.10 ~ p.11 Dove, quando e con chi vuoi. Tre modalità 1 Modalità TV Nintendo Switch consente tre modalità di gioco. Inserisci Nintendo Switch nella base e gioca in HD sulla tua TV. Collegarlo alla TV è facile La console si accende appena la rimuovi Adattatore AC dalla base. Porta la console con te e Nintendo Switch continua a giocare in modalità portatile. Cavo HDMI Basta collegare l'adattatore AC e il cavo HDMI inclusi nella confezione a ogni uscita. Dove, quando e con chi vuoi. Tre modalità 2 Usa lo stand integrato e condividi il divertimento Modalità da tavolo con un gioco multiplayer. Inserendo i due Joy-Con nell'impugnatura Joy-Con Joy-Con ottieni un controller tradizionale. Nintendo Switch dispone di Senza l'impugnatura, ogni Joy-Con è un controller due controller, uno per lato, che indipendente. funzionano anche insieme. Nintendo Switch consente tre modalità di gioco. Tre modalità 3 Collega i controller Joy-Con alla console e Modalità portatile gioca dove vuoi. Nintendo Switch Lite – Nintendo Switch Lite è una console compatta, leggera e con comandi integrati. pensata per giocare in mobilità Nintendo Switch Lite è compatibile con tutti i software per Nintendo Switch che possono essere giocati in modalità portatile. -

Finding Aid to the Atari Coin-Op Division Corporate Records, 1969-2002
Brian Sutton-Smith Library and Archives of Play Atari Coin-Op Division Corporate Records Finding Aid to the Atari Coin-Op Division Corporate Records, 1969-2002 Summary Information Title: Atari Coin-Op Division corporate records Creator: Atari, Inc. coin-operated games division (primary) ID: 114.6238 Date: 1969-2002 (inclusive); 1974-1998 (bulk) Extent: 600 linear feet (physical); 18.8 GB (digital) Language: The materials in this collection are primarily in English, although there a few instances of Japanese. Abstract: The Atari Coin-Op records comprise 600 linear feet of game design documents, memos, focus group reports, market research reports, marketing materials, arcade cabinet drawings, schematics, artwork, photographs, videos, and publication material. Much of the material is oversized. Repository: Brian Sutton-Smith Library and Archives of Play at The Strong One Manhattan Square Rochester, New York 14607 585.263.2700 [email protected] Administrative Information Conditions Governing Use: This collection is open for research use by staff of The Strong and by users of its library and archives. Though intellectual property rights (including, but not limited to any copyright, trademark, and associated rights therein) have not been transferred, The Strong has permission to make copies in all media for museum, educational, and research purposes. Conditions Governing Access: At this time, audiovisual and digital files in this collection are limited to on-site researchers only. It is possible that certain formats may be inaccessible or restricted. Custodial History: The Atari Coin-Op Division corporate records were acquired by The Strong in June 2014 from Scott Evans. The records were accessioned by The Strong under Object ID 114.6238.