Uncovering a Persistent Diet Spam Operation on Twitter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Full House Tv Show Episodes Free Online
Full house tv show episodes free online Full House This is a story about a sports broadcaster later turned morning talk show host Danny Tanner and his three little Episode 1: Our Very First Show.Watch Full House Season 1 · Season 7 · Season 1 · Season 2. Full House - Season 1 The series chronicles a widowed father's struggles of raising Episode Pilot Episode 1 - Pilot - Our Very First Show Episode 2 - Our. Full House - Season 1 The series chronicles a widowed father's struggles of raising his three young daughters with the help of his brother-in-law and his. Watch Full House Online: Watch full length episodes, video clips, highlights and more. FILTER BY SEASON. All (); Season 8 (24); Season 7 (24); Season. Full House - Season 8 The final season starts with Comet, the dog, running away. The Rippers no longer want Jesse in their band. D.J. ends a relationship with. EPISODES. Full House. S1 | E1 Our Very First Show. S1 | E1 Full House. Full House. S1 | E2 Our Very First Night. S1 | E2 Full House. Full House. S1 | E3 The. Watch Series Full House Online. This is a story about a sports Latest Episode: Season 8 Episode 24 Michelle Rides Again (2) (). Season 8. Watch full episodes of Full House and get the latest breaking news, exclusive videos and pictures, episode recaps and much more at. Full House - Season 5 Season 5 opens with Jesse and Becky learning that Becky is carrying twins; Michelle and Teddy scheming to couple Danny with their. Full House (). 8 Seasons available with subscription. -
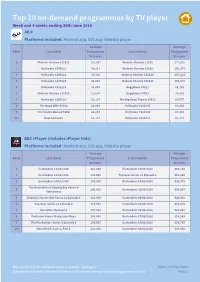
Top 10 On-Demand Programmes by TV Player Week and 4 Weeks Ending 26Th June 2016 All 4 Platforms Included: Android App, Ios App, Website Player
Top 10 on-demand programmes by TV player Week and 4 weeks ending 26th June 2016 All 4 Platforms included: Android app, iOS app, Website player Average Average Rank Last week Programme Last 4 weeks Programme Streams Streams 1 Made In Chelsea S11E11 191,007 Made In Chelsea S11E8 277,592 2 Hollyoaks S25E122 49,911 Made In Chelsea S11E9 252,379 3 Hollyoaks S25E123 44,792 Made In Chelsea S11E10 237,223 4 Hollyoaks S25E124 43,656 Made In Chelsea S11E11 191,070 5 Hollyoaks S25E125 38,009 Gogglebox S7E17 81,725 6 Made In Chelsea S11E10 32,664 Gogglebox S7E16 78,862 7 Hollyoaks S25E126 32,197 The Big Bang Theory S9E22 69,577 8 The Good Wife S7E22 23,663 Hollyoaks S25E107 69,108 9 First Dates Abroad S1E2 22,253 Hollyoaks S25E108 67,253 10 New Girl S5E4 21,712 Hollyoaks S25E111 67,247 BBC iPlayer (includes iPlayer Kids) Platforms included: Android app, iOS app, Website player Average Average Rank Last week Programme Last 4 weeks Programme Streams Streams 1 Eastenders 21/06/2016 361,544 Eastenders 10/06/2016 455,194 2 Eastenders 23/06/2016 298,540 Top Gear Series 23 Episode 1 451,485 3 Eastenders 24/06/2016 295,061 Eastenders 14/06/2016 435,478 The Great British Sewing Bee Series 4 4 145,011 Eastenders 31/05/2016 426,887 Activewear 5 Celebrity Masterchef Series 11 Episode 1 121,993 Eastenders 09/06/2016 424,902 6 Top Gear Series 23 Episode 4 119,397 Eastenders 03/06/2016 415,419 7 Versailles: Episode 4 107,383 Eastenders 02/06/2016 402,052 8 Professor Green: Dangerous Dogs 106,431 Eastenders 17/06/2016 391,289 9 The Musketeers Series 3 Episode 3 103,386 Eastenders 16/06/2016 390,755 10 New Blood: Case 2, Part 1 102,304 Eastenders 30/05/2016 386,901 Only viewing time for audited platforms is included. -

Turning the Page U C
s e r u t l Turning the Page u C l a Gendered Identities in Contemporary u s i V Literary and Visual Cultures d n a The essays in this volume are all selected papers from the y r a conference Gendered Identities in Contemporary Literary and r e t Visual Cultures, organized in June 2015 in Budapest, Hungary, i L by the Narratives of Culture and Identity Research Group. y r The authors deal with a wide array of gender issues in a r modern and postmodern English literature, contemporary o p popular culture, and postcolonial and Eastern European m e t studies. The essays are arranged into three larger chapters n based on their subject matter: “Dissecting Identities” o C n examines gendered identities in various literary contexts; i s “Creating Social Identities” looks at the function of society e i t i and culture in identity formation; and “Reinventing Gender t n Roles” deals with subversive uses of gender representation. e d I The collection displays several applications of gender d e studies as well as the authors’ enthusiastic engagement with r e the many directions in which gender studies can take us. d n e G e g a P e h t g n i n r u T ISBN 978-963-414-385-7 webshop.harmattan.hu Edited by Gyuris • Szép • Vecsernyés TURNING THE PAGE Gendered Identities in Contemporary Literary and Visual Cultures Judit Friedrich Series Editor ELTE PAPERS IN ENGLISH STUDIES Kata Gyuris, Eszter Szép, Dóra Vecsernyés Editors TURNING THE PAGE Gendered Identities in Contemporary Literary and Visual Cultures The publication was supported by Eötvös Loránd University Faculty of Humanities Student Union (BTK HÖK) Budapest, 2018 © Authors, 2018 © Editors, 2018 © L'Harmattan Kiadó, 2018 Series Editor: Judit Friedrich Editors: Kata Gyuris, Eszter Szép Technical Editor: Dóra Vecsernyés Layout Design: Bence Levente Bodó Cover Design: Gergely Oravecz ISSN Number: 2061-5655 ISBN Number: 978-963-414-385-7 Copies may be ordered from: L'Harmattan Könyvesbolt 1053 Budapest, Kossuth L. -

Marnie: I Was Worried Lus Xc Iv
the FAMOUS Marnie: I was worried LUS XC IV about coming“ out, E E E X E C V I L S U Marnie’s tired but now I feel of feeling empowered anxious The Geordie Shore star s peaks about her bisexuality for the first” time hen you’re on drunk and it just happened. To future with her. I’m still a bit Geordie Shore, me, that was different because it hesitant to have a full-blown nothing is private was just me and her. It wasn’t for relationship with a girl, but I do (least of all your any other reason than I wanted to, think it would be a possibility. actual privates) so it made me think differently. Why are you hesitant? – and since It was a friend – I’ve known her Because of the job I’m in. Everyone Marnie Simpson for about two years. has an opinion. It shouldn’t be Wjoined the show in 2013, we’ve seen So, you guys had sex? like that, and I hate the fact that her get intimate with co-stars That was the first time, yeah. I worry about it. And I’m still very Gaz Beadle and Aaron Chalmers I wouldn’t really class it as much attracted to boys as well. and get engaged to TOWIE sex, but we did things. It was Have you been with any star Ricky Rayment (who she about a year ago. women since then? split with in September 2015). How did you feel about I’ve kissed girls and been We’ve also seen her kiss a few girls, it the next morning? messaging girls, but it’s still including housemate Chloe Ferry, I [always] thought I’d wake quite uncomfortable, because so when she tweeted last month, up and be embarrassed, but I’m in the public eye. -

Clemency Newman Looking Into the Popular Reality Show Geordie Shore
From reality television to the hyperreal: How do the pressures of reality shows such as Geordie Shore cause their characters to change their physical appearance? Clemency Newman Abstract Looking into the popular reality show Geordie Shore, I will undertake research to answer why it is that the women who appear on the show change their physical appearance and what connection this has to their celebrity status. I hope to argue that because the women are considered lower class, they have no other power than their perceived attractiveness and are therefore pressured into trying to achieve a hyperreal body, relating to Baudrillard’s theory of Simulacra and Simulation. Introduction Reality television is big business, with over 300 reality format shows on air in the US alone (Washington Post, 2015) from Idol to Big Brother, they rake in millions of viewers every night and have a significant impact on popular culture. These shows present a concentrated, edited and scandalised version of everyday life, wrapped in the guise of being true to the viewer, only more dramatic. Television has the ability to shape our view of the world and now with the ever pervasive aspects of social media, networks such as Bravo can imprint an everlasting impression of what we consider normal. However, even when know what we are watching is completely unreal, we accept it as ‘reality’ and accept the characters into our lives, until they become overthrown by a younger, prettier and more outrageous model. Geordie Shore is one such television show which presents an exaggerated, hyperbolic version of reality, with the cast members performing ridiculous, violent and carnal acts in front of a worldwide audience and being celebrated in the process. -

Gänget I Geordie Shore Är Tillbaka För En Ny Säsong - I Grekland
Gänget i Geordie Shore är tillbaka för en ny säsong - i Grekland Nu är väntan äntligen över! På söndag är Geordie Shore tillbaka i rutan med en helt ny säsong. Denna gång får vi följa med gänget till Greklands partyöar. - Geordie Shore når helt nya höjder denna säsong. Räkna med fler vredesutbrott, tårar och drama än någonsin tidigare, säger Holly Hagan. Geordie Shore hade världspremiär våren 2011 och blev genast en enorm succé med miljoner tittare världen över och har sänts i 10 säsonger. I serien får vi följa ett gäng galna ”Geordies” som bor tillsammans i ett hus i Newcastle, festar, bråkar, skrattar och hamnar i en hel del galna situationer. I den nya säsongen skickas gänget till Grekland på uppdrag av deras chef Anna och vi får följa profilerna när de öhoppar mellan Greklands alla partyöar. - Greklandresan var helt galen! Vi gjorde massa dumma saker och speciellt jag. Jag var i ett förhållande under inspelningsperioden, men det märks inte i huvudtaget, säger Charlotte Crosby I förra säsongen släppte Gaz släppte bomben att han skaffat en seriös flickvän, till Charlottes stora förtvivlan. Holly och Kyle blev bli officiella och Marnie var otrogen mot sin nya pojkvän med Aaron. Dessutom fick vi träffa nya tillskotten Chloe och Nathan som passade perfekt in i skaran efter en hel del ”tashin’ on” och ”kickin’ off”. Hur kommer intrigerna att fortlöpa den här säsongen? Seriens stjärnor denna säsong består av Gary Beadle (Gaz) 27, Charlotte Crosby 25, Holly Hagan 23, Scott Timlin (Scotty-T) 27, Aaron Chalmers 28, Kyle Christie 23, Marnie Simpson 23, Chloe Etherington 20 och Nathan Henry 24. -

'Assassinated' War Correspondent Marie Colvin, Lawsuit Filed by Her Relatives Claims
Feedback Tuesday, Apr 10th 2018 12AM 64°F 3AM 57°F 5-Day Forecast Home U.K. News Sports U.S. Showbiz Australia Femail Health Science Money Video Travel Columnists DailyMailTV Latest Headlines News World News Arts Headlines Pictures Most read Wires Coupons Login ADVERTISEMENT As low as $0.10 ea STUDENT Ribbon Learn More Assad's forces 'assassinated' Site Web Enter your search renowned war correspondent Marie ADVERTISEMENT Colvin and then celebrated after they learned their rockets had killed her, lawsuit iled by her relatives claims President Bashar Assad's forces targeted Marie Colvin and celebrated her death This is according to a sworn statement a former Syrian intelligence oicer made The 55-year-old Sunday Times reporter died in a rocket attack in Homs By JESSICA GREEN FOR MAILONLINE PUBLISHED: 14:25 EDT, 9 April 2018 | UPDATED: 16:14 EDT, 9 April 2018 65 175 shares View comments Syria President Bashar Assad's forces allegedly targeted veteran war correspondent Marie Colvin and then celebrated after they learned their rockets had killed her. This is according to a sworn statement a former Syrian intelligence oicer made in a wrongful death suit iled by her relatives. The 56-year-old Sunday Times reporter died alongside French photographer Remi Ochlik, 28, in a rocket attack on the besieged city of Homs. ADVERTISING Like +1 Daily Mail Daily Mail Follow Follow @DailyMail Daily Mail Follow Follow @dailymailuk Daily Mail FEMAIL TODAY The intelligence defector, code named EXCLUSIVE: Tristan Ulysses, says Assad's military and Thompson caught on intelligence oicials sought to capture or video locking lips with a brunette at NYC club kill journalists and media activists in just days before Khloe Homs. -

Winter 2016 February
Winter 2016 February Monday Tuesday Wednesday Thursday Friday Saturday Sunday Celebrity Style Story McMorris & McMorris 6:00 Grand Benders ( R ) Degrassi (S14) Degrassi (S14) 6:00 Panic Button ( R ) ( R ) Celebrity Style Story 6:30 Grand Benders ( R ) Degrassi (S14) Careless Teens Student Bodies 6:30 ( R ) 7:00 InnerSpace 7:00 The L.A. Complex 7:30 Degrassi High 7:30 8:00 Degrassi (S1- 13) Degrassi (S14) ( R ) 8:00 8:30 Degrassi (S1- 13) Student Bodies ( R ) 8:30 Degrassi (S1-13) 9:00 Teen Mom Reign 9:00 ( R ) ( R ) 9:30 Degrassi (S1-13) 9:30 Grand Benders Degrassi ( S14 ) Celebrity Style Story McMorris & McMorris 10:00 Ridiculousness ( R ) The Shannara 10:00 Panic Button ( R ) ( R ) ( R ) ( R ) ( R ) Chronicles Grand Benders Degrassi ( S14 ) Celebrity Style Story Broke Ass Game Show 10:30 Careless Teens ( R ) 10:30 ( R ) ( R ) ( R ) ( R ) InnerSpace ( R ) Greates Party Story 11:00 Ever ( R ) Teen Wolf 11:00 ( R ) 11:30 Celebrity Style Story McMorris & McMorris Grand Benders The Wild Ride ( R ) 11:30 Grand Benders Degrassi (S14) Celebrity Style Story McMorris & McMorris 12:00 The Challenge 12:00 Panic Button ( R ) ( R ) ( R ) ( R ) ( R ) Grand Benders Degrassi (S14) Celebrity Style Story Careless Teens 12:30 ( R ) 12:30 ( R ) ( R ) ( R ) ( R ) 1:00 InnerSpace ( R ) 1:00 1:30 Degrassi High ( R ) 1:30 2:00 Degrassi (S1- 13) ( R ) 2:00 2:30 Degrassi (S1- 13) ( R ) 2:30 MTV-A-Thons 3:00 Degrassi (S1-13) ( R ) 3:00 MTV-A-Thons 3:30 Degrassi (S1-13) ( R ) 3:30 4:00 Friendzone 4:00 Fired By Mum & Dad 4:30 Friendzone 4:30 5:00 Ridiculousness -

Ex on the Beach + Geordie Shore = Sant! En Ny Säsong Av Supersåpan Är Här
Ex on the Beach + Geordie Shore = sant! En ny säsong av supersåpan är här Nu är det dags för en ny säsong av succéprogrammet Ex on the Beach med nya singlar. I år förenas det bästa av två världar när Geordie Shore-stjärnan Scott Timlin är en av de åtta sexiga singlarna i Ex On the Beach. Programkonceptet är enkelt – åtta singlar reser till en lyxvilla på en paradisö för att festa, flörta och söka kärleken. Men det är inte så härligt som det låter, en efter en dyker deltagarnas ex upp ur havet och ställer till med trubbel i paradiset. Ex on The Beach var fjolårets mest mest googlade TV-program och i den nya säsongen kan vi förvänta oss ännu mer oväntade händelser. Scott Timlin, en av stjärnorna från Geordie Shore, medverkar och det gör även två av de mest populära deltagarna från säsong tre; Jordan Davies och Megan McKenna, även kända som JEGAN. Scott Timlin, Scotty T, är en Geordie Shore-legend – medlem i “The Buck Squad” och Top Shagger. Han har många ex, och one-night stands, att oroa sig för. Det är inte första gången som en stjärna från Geordie Shore har tvingats möta sina ex i rutan. Vicky Pattinson, Gaz och Charlotte Crosby har alla gästat programmet. Hela listan med alla singlar i säsong 4 av succéprogrammet Ex On The Beach: Scott Timlin Helen Briggs Joe Delaney Lewis Good Nancy-May Turner Naomi Hedman Olivia Walsh Youssef Hassane Ex On The Beach sänds onsdagar kl. 22.00 på MTV. Premiären för säsong 4 är den 20 januari. -

Jersey Shore Family Vacation”
Snooki och resten av gänget från Jersey Shore tillbaka i TV-rutan med MTVs nya “Jersey Shore Family Vacation” Alla minns vi Snooki och hennes Crocodilly, Rohn och Jennies stormiga förhållande och hur Michael ”The Situation” Sorrentino lät alla veta att ”cabs are here”! I det helt nya formatet åker profilerna till Miami på en drömsemester de sent ska glömma. Den klassiska dokusåpan Jersey Shore intar den 6 april TV-rutan på nytt med programmet Jersey Shore Family Vacation. Jersey Shore har lagt grunden för flertalet efterföljande succéprogram, däribland den brittiska versionen Geordie Shore. I Jersey Shore Family Vacation återförenas de ursprungliga profilerna och i första avsnittet får vi se när Deena Nicole Cortese, Paul “Pauly D” Delvecchio,” Jenni “JWOWW” Farley, Vinny Guadagnino, Ronnie Ortiz-Magro, Nicole “Snooki” Polizzi och Mike “The Situation” Sorrentino både återförenas och flyttar in i lyxvillan i Miami som under de kommande veckorna ska bli deras hem. Med rymliga rum, en stor pool och sist men inte minst en välfylld bar känner de sig som hemma – kanske lite för hemma då gamla draman nu får chansen att blossa upp på nytt. Snooki har även en överraskning till gänget som hon knyckt med sig från huset i Jersey. Detta och lite till får vi se i premiäravsnittet som sänds den 6 april kl 02:00 på MTV. Är det efter läggdags så sänds avsnittet även på kvällen den 6 april kl 22:00. Därefter kommer nya avsnitt av Jersey Shore Family Vacation att sändas på MTV på fredagar kl 22:00. MTV har även kunnat avslöja att återföreningen mellan orginaldeltagarna i Jersey Shore får global premiär över Viacoms internationella nätverk av MTV-kanaler i nästan 180 länder. -

Daniel Kemp Avid Editor
Daniel Kemp Avid Editor Profile Daniel is a multi-format television editor with particular experience cutting MTV style reality shows, reality-documentary, music entertainment and short-form. He also knows his way around specialist effects packages. Broadcast Credits Educating Joey Essex: American Reem – Lime Pictures for ITV2 With the US presidential election looming large, Joey Essex heads across the pond to find out more. This three- part series sees Joey explore the history, culture and ultimately politics of this great nation as they head to the poles. Series Producer: Huw Slipper Executive Producer: Phil Harris Celebs Go Dating – Lime Pictures for E4 Six single celebs seeking love join a matchmaking agency and go on nightly dates with non-celebs. Series Producer: James Lassell Executive Producer: Phil Harris Ex on the Beach: Best Bits – Whizz Kid Entertainment for MTV (Additional Editor) Clip-show featuring highlights from the popular MTV series. Educating Joey Essex: What EU sayin? – Lime Pictures for ITV2 Reality Series. With the EU referendum looming, Britain must chose whether to stay in or leave the European Union. But which way will Joey vote? To help him decide, he tours the UK and visits a dairy farm and meets Boris Johnson. Series Producer: Huw Slipper / Executive Producer: Phil Harris Educating Joey Essex: Reem Queen at 90 – Lime Pictures for ITV2 Reality Series. Joey Essex goes on a mission to meet the Queen on her 90th birthday. On his journey, he meets an elocution expert and enlists the help of former royal correspondent Jennie Bond. Series Producer: Huw Slipper / Executive Producer: Phil Harris Tattoo Fixers Series 2 - Studio Lambert for E4 Reality documentary. -

The Case of Bigg Market, Newcastle Upon Tyne
Heritage as a Vehicle for Development: The case of Bigg Market, Newcastle upon Tyne Loes Veldpaus and John Pendlebury School of Architecture Planning and Landscape, Newcastle University, Newcastle upon Tyne, England, UK doi:10.1080/02697459.2019.1637168 Abstract: In this paper we examine the way conservation-planning has changed since the global economic crisis in Newcastle upon Tyne (UK), where austerity is still an all- consuming issue. Focusing upon a recent project around the Bigg Market, a historic public space, we map the new ‘conservation-planning assemblage’ where ‘other-than- public' forms of management have taken hold. We identify impacts of austerity, deregulation and a smaller state ideology, and show how the agency of heritage assets and narratives in urban context is focussed on economic performance and competitiveness. Within the conservation-planning assemblage, roles and responsibilities have changed, and we reflect on the impact this has on conservation policy and practice. Keywords: urban governance; heritage; conservation-planning; austerity, Business Improvement District; Newcastle upon Tyne Bigg Market Banter Mentioning to someone in Newcastle that Bigg Market is the case study we are working on is typically met with a smile followed by raised eyebrows, a wink, or a ‘must be interesting field work…’. The Bigg Market in Newcastle upon Tyne (England, UK) connotes the city’s urban nightlife, as a place with undercurrents of violence, associated with a drinking culture, and a classed and gendered sense of place (Nicholls, 2017, p. 125). As the market area of medieval Newcastle, there is a long history to this, but the explicit connotation has been strengthened in recent history.