Web Compas Minimum Hosting Requirements
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

System Requirements for LWC Connect to Learning
System Requirements for LWC Connect to Learning Run the Adobe Connect Diagnostic to see if you meet the Flash, connection, and add-in minimum requirements https://na3cps.adobeconnect.com/common/help/en/support/meeting_test.htm MINIMUM COMPUTER SYSTEM REQUIREMENTS: Windows • 1.4GHz Intel® Pentium® 4 or faster processor (or equivalent) for Microsoft® Windows® XP, Windows 7 or Windows 8 • Windows 8.1 (32-bit/64-bit), Windows 8 (32-bit/64-bit), Windows 7 (32-bit/64-bit), Windows XP • 512MB of RAM (1GB recommended) for Windows XP, Windows 7 or Windows 8 • Microsoft Internet Explorer 8, 9, 10, 11; Mozilla Firefox; Google Chrome • Adobe® Flash® Player 11.2+ Mac OS • 1.83GHz Intel Core™ Duo or faster processor • 512MB of RAM (1GB recommended) • Mac OS X 10.7.4, 10.8, 10.9 • Mozilla Firefox; Apple Safari; Google Chrome • Adobe Flash Player 11.2+ Linux • Ubuntu 12.04; Red Hat Enterprise Linux 6; OpenSuSE 12.2 • No Add-in support for Linux. Users on Linux can attend meetings in the browser. • Mozilla Firefox • Adobe Flash Player 11.2+ Mobile • Apple supported devices: iPhone 5S, iPhone 5, iPhone 4S, iPad with Retina display, iPad 3, iPad 2, iPad mini, and iPod touch (4th & 5th generations) • Apple supported OS versions summary: iOS 6 and higher • Android supported devices: Motorola DROID RAZR MAXX, Motorola Atrix, Motorola Xoom, Samsung Galaxy Tab 2 10.1, Samsung Galaxy S3 & S4, Nexus 7 tablet • Android supported OS versions summary: 2.3.4 and higher 1 ADDITIONAL REQUIREMENTS • Latest version of Adobe Flash Player installed o Download latest version at http://get.adobe.com/flashplayer/ . -
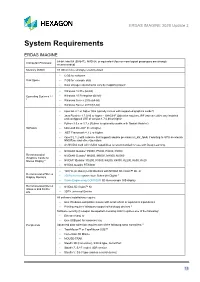
ERDAS IMAGINE 2020 Update 3
ERDAS IMAGINE 2020 Update 3 System Requirements ERDAS IMAGINE 64-bit: Intel 64 (EM64T), AMD 64, or equivalent (four or more logical processors are strongly Computer/ Processor recommended) Memory (RAM) 16 GB or more strongly recommended • 6 GB for software Disk Space • 7 GB for example data • Data storage requirements vary by mapping project1 • Windows 10 Pro (64-bit) Operating Systems 2, 3, • Windows 10 Enterprise (64-bit) 4 • Windows Server 2016 (64-bit) • Windows Server 2019 (64-bit) • OpenGL 2.1 or higher (this typically comes with supported graphics cards 5) • Java Runtime 1.7.0.80 or higher - IMAGINE Objective requires JRE and can utilize any installed and configured JRE of version 1.7.0.80 or higher • Python 3.6.x or 3.7.x (Python is optionally usable with Spatial Modeler) Software • Microsoft DirectX® 9c or higher • .NET Framework 4.7.2 or higher • OpenCL 1.2 with a device that supports double precision (cl_khr_fp64) if wanting to GPU accelerate NNDiffuse and other Operators • An NVIDIA card with CUDA capabilities is recommended for use with Deep Learning. • NVIDIA® Quadro® P6000, P5000, P4000, P2000 Recommended • NVIDIA® Quadro® M6000, M5000, M4000, M2000 Graphics Cards for Stereo Display 6 • NVIDIA® Quadro® K5200, K5000, K4200, K4000, K2200, K600, K420 • NVIDIA Quadro RTX4000 • 120 Hz (or above) LCD Monitors with NVIDIA 3D Vision™ Kit, or Recommended Stereo • 3D PluraView system from Schneider Digital 7 Display Monitors • Vision Engineering CONTOUR 3D stereoscopic GIS display Recommended Stereo • NVIDIA 3D Vision™ Kit Glasses -

Spread for ASP.NET Developer's Guide
Spread for ASP.NET Developer’s Guide 0 Developer's Guide This guide provides introductory conceptual material and how-to explanations for routine tasks for developers using Spread for ASP.NET. It describes how an application developer would use the properties and methods in Spread to create spreadsheets and grids on Web Forms, bind to databases, and customize the component for your application. Getting Started Understanding the Product Working with the Spread Designer Customizing the Appearance Customizing User Interaction Customizing with Cell Types Managing Data Binding Managing Data in the Component Managing Formulas Managing File Operations Using Sheet Models Maintaining State Working with the Chart Control Using Touch Support with the Component For complete API reference information, refer to the Assembly Reference (on-line documentation). For a complete list of documentation, refer to the Spread for ASP.NET Documentation (on-line documentation). Copyright © GrapeCity, inc. All rights reserved. Spread for ASP.NET Developer’s Guide 1 1 Table of Contents Developer's Guide 0 1. Table of Contents 1-16 Getting Started 17 Handling Installation 17 Installing the Product 17 Licensing a Trial Project after Installation 17 End-User License Agreement 17-18 Creating a Build License 18-19 Handling Redistribution 19-20 Product Requirements 20 Handling Variations In Windows Settings 20-21 Working with the Component 21 Adding a Component to a Web Site using Visual Studio 2015 or 2017 21-24 Adding a Component to a Web Site using Visual Studio 2013 -

Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5
Level One Benchmark Windows NT 4.0 Operating Systems V1.0.5 Copyright 2003, The Center for Internet Security www.cisecurity.org Page 2 of 32 Terms of Use Agreement Background. CIS provides benchmarks, scoring tools, software, data, information, suggestions, ideas, and other services and materials from the CIS website or elsewhere (“Products”) as a public service to Internet users worldwide. Recommendations contained in the Products (“Recommendations”) result from a consensus-building process that involves many security experts and are generally generic in nature. The Recommendations are intended to provide helpful information to organizations attempting to evaluate or improve the security of their networks, systems and devices. Proper use of the Recommendations requires careful analysis and adaptation to specific user requirements. The Recommendations are not in any way intended to be a “quick fix” for anyone’s information security needs. No representations, warranties and covenants. CIS makes no representations, warranties or covenants whatsoever as to (i) the positive or negative effect of the Products or the Recommendations on the operation or the security of any particular network, computer system, network device, software, hardware, or any component of any of the foregoing or (ii) the accuracy, reliability, timeliness or completeness of any Product or Recommendation. CIS is providing the Products and the Recommendations “as is” and “as available” without representations, warranties or covenants of any kind. User agreements. By using the Products and/or the Recommendations, I and/or my organization (“we”) agree and acknowledge that: 1. No network, system, device, hardware, software or component can be made fully secure; 2. -

Archiving Geocue Projects in Microsoft SQL Server
CueTip Archiving GeoCue Projects in Microsoft SQL Server GeoCue Group Support January 16, 2015 Revision 2.0 Introduction GeoCue Server runs on top of a SQL database. The database stores all the metadata about projects as well as all internal links to the geospatial data stored in the GeoCue warehouses. The database may be a full SQL database installation or a limited edition of SQL such as Microsoft SQL Server Express (Express) or Microsoft SQL Desktop Engine (MSDE). Express and MSDE are free versions of SQL limited to five concurrent users and a maximum database file size of 10GB (SQL Express 2008 R2 and later) or 2 GB respectively. Note that it is very important to make sure regular GeoCue database backups are integrated with your standard IT backup and archiving policies. Failure to back-up your GeoCue database on a regular basis can result in a significant loss of project data in the case of a hardware or software failure. Once the database size limit will be exceeded GeoCue will no longer be able to store additional metadata about projects as SQL will be unable to allocate additional space in the database - even if the current database size has yet to cross that threshold. Before the file size reaches the database limit of an Express version, it is recommended that a user upgrade to a full version of SQL Server. If a user does not have the ability to upgrade to a full version of SQL Server then the next best option is to delete old or unnecessary projects within the database using project utilities in the GeoCue Client. -

Technology Announcement - SQL Server Database Transition
October 20, 2003 Technology Announcement - SQL Server Database Transition DATAIR currently uses the Microsoft JET (Access) MDB database for its Windows- based products. Due to Microsoft’s announcement that this technology is no longer under active development, DATAIR has decided to transition its products to the Microsoft SQL Server client/server database platform tentatively scheduled to begin late in the first quarter of 2004. Moving to SQL Server will allow us to attain even greater levels of application performance, reliability, and scalability. We have prepared the following summary in Q&A format to help you understand what this change will mean to you, and the steps you may need to take to prepare for this transition. What does this mean to you? First and foremost, SQL Server is a client/server database technology unlike JET. When configured properly, client/server databases can offer higher levels of performance and stability than file based databases. Will my data transfer from my JET database? Yes, we will include a utility to transfer your data from current database to your new one. Do I need to buy SQL Server? Not necessarily. DATAIR will be including a limited version of SQL Server called the Microsoft SQL Desktop Engine (MSDE) that Microsoft allows us to distribute free of charge. Depending on the number of simultaneous users, and the type of work they will be doing, MSDE may be all you need. How many users can MSDE support? MSDE is designed to support a maximum of 5 simultaneous operations. That’s not to be confused with 5 users. -

Dell Openmanage IT Assistant Version 8.9 Release Notes
Dell OpenManage IT Assistant Version 8.9 Release Notes What’s New New major features Now, you can launch the warranty support site and view the current warranty information. In addition to the Express Service Code for PowerEdge servers; now, IT Assistant displays Chassis Express Service code and Chassis Service Tag for PowerEdge Blade servers running OpenManage Server administrator version 6.5 or later. You can also see Enclosure specific Express service code in the Details tab. New OS Support Microsoft Windows 2008 Standard Server NOTE: These operating systems must be WoW64 enabled. Deprecated features The following features are not supported in IT Assistant: Topology view Volume Information Report—As IT Assistant does not support Volume Info Report, this will be removed if you upgrade from previous version to IT Assistant 8.9. Installation For information on Installation, see the Dell OpenManage IT Assistant version 8.9 on support.dell.com/manuals Prerequisites For more information on Operating system, Browser & Consoles, and Minimum hardware Configuration see the Dell Systems Software Support Matrix Version 6.5 on support.dell.com/manuals Database (SQL Server) SQL Server 2008 R2 (This is part of IT Assistant install). Also supports: SQL Server 2000 SQL Server 2005 SP1/SP2 Additional Softwares Navisphere(R) Secure CLI For Dell/EMC storage arrays inventory, ensure your array is FLARE(R) version 19 or above. You should also install Navisphere(R) Secure CLI (version 19 or above) on your management station. NOTE: This CLI software -

Address-Space Randomization for Windows Systems
Address-Space Randomization for Windows Systems∗ Lixin Li and JamesE.Just R.Sekar Global InfoTek, Inc., Reston, VA Stony Brook University, Stony Brook, NY {nli,jjust}@globalinfotek.com [email protected] Abstract Wehntrust [21] and Ozone [20]. In addition, Windows Address-space randomization (ASR) is a promising Vista is going to be shipped with a limited implemen- solution to defend against memory corruption attacks tation of ASR [9]. However, these products suffer from that have contributed to about three-quarters of US- one or more of the following drawbacks: CERT advisories in the past few years. Several tech- • Insufficient range of randomization. Windows Vista niques have been proposed for implementing ASR on randomizes base addresses over a range of 256 possi- Linux, but its application to Microsoft Windows, the ble values. This level of randomization is hardly suf- largest monoculture on the Internet, has not received ficient to defeat targeted attacks: the attacker simply as much attention. We address this problem in this pa- needs to try their attack an average of 128 times be- per and describe a solution that provides about 15-bits fore succeeding. This isn’t likely to significantly slow of randomness in the locations of all (code or data) ob- down self-replicating worms either. Wehntrust and jects. Our randomization is applicable to all processes Ozone provide more randomization, but significantly on a Windows box, including all core system services, less than that of DAWSON in some memory regions as well as applications such as web browsers, office ap- such as the stack. plications, and so on. -
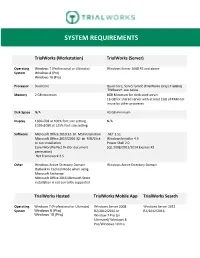
System Requirements
SYSTEM REQUIREMENTS TrialWorks (Workstation) TrialWorks (Server) Operating Windows 7 (Professional or Ultimate) Windows Server 2008 R2 and above System Windows 8 (Pro) Windows 10 (Pro) Processor Dual Core Quad Core, Server Grade Memory 2 GB minimum 8GB Minimum for dedicated server 16 GB for shared server with at least 1GB of RAM not in use by other processes. Disk Space N/A 40 GB minimum Display 1366x768 at 100% font size setting N/A 1920x1080 at 125% font size setting Software Microsoft Office 2010 32-but MSI installation .NET 3.51 Microsoft Office 2013/2016 32-but MSI/Click Windows Installer 4.5 to run installation Power Shell 2.0 Corel WordPerfect 9+ (for document SQL 2008/2012/2014 Express R2 generation) .Net Framework 3.5 Other Windows Active Directory Domain Windows Active Directory Domain Outlook in Cached Mode when using Microsoft Exchange Microsoft Office 2016 Microsoft Store installation is not currently supported TrialWorks Hosted TrialWorks Mobile App TrialWorks Search Operating Windows 7 (Professional or Ultimate) Windows Server 2008 Windows Server 2012 System Windows 8 (Pro) R2/2012/2016 or R2/2012/2016 Windows 10 (Pro) Window 7 Pro (or Ultimate)/ Windows 8 Pro/Windows 10 Pro Processor N/A N/A Server grade, Quad core for dedicated server, hexa core for shared server Clock speed 2.5GHz or above Memory N/A N/A 16 GB minimum Disk Space N/A N/A N/A Display 1366x768 at 100% font size setting Microsoft .NET Framework N/A 1920x1080 at 125% font size setting 4.0 – Extended SQL 2008/2012/2014 Express R2 IIS 6 or later with ASP.Net Software N/A .Net Framework 4.0 (or any .NET 3.51 newer update that is Windows Installer 4.5 backwards compatible with Power Shell 2.0 4.0) Active Directory user TWAPP (member of Domain Users, IIS_WPG/IIS_USRS) Other A computer with a stable internet Static Public IP IIS 7.0 or later connection. -

System Requirements
System Requirements Table of Contents Introduction ................................................................................................................................................... 2 Hardware Requirements ................................................................................................................................ 2 Operating System ...................................................................................................................................... 2 Processor ................................................................................................................................................... 2 RAM .......................................................................................................................................................... 3 Disk ........................................................................................................................................................... 3 Display ...................................................................................................................................................... 3 Peripherals ................................................................................................................................................. 3 Network ........................................................................................................................................................ 4 Internet ..................................................................................................................................................... -

Supported Platforms and Minimum System Requirements
physics on screen Supported platforms and minimum system requirements 1 Supported platforms and minimum system requirements March 09, 2021 Minimum system requirements for BETA_LM_TOOLS v6.4 or later MacOS 32bit 64bit Darwin 8.7.3 or later LINUX AMD Athlon 64, glibc 2.3.2 AMD Athlon, glibc 2.2 AMD Athlon 64FX, glibc 2.3.2 INTEL Pentium IV, glibc 2.2 AMD Opteron, glibc 2.3.2 INTEL Xeon EM64T, glibc 2.3.2 WINDOWS AMD Athlon, Win2K SP3, WinXP SP1 AMD Athlon, WinXP Pro x64, SP1 INTEL Pentium IV, Win2K SP3, WinXP SP1 INTEL Pentium IV, WinXP Pro x64, SP1 Windows Server 2003/2008 Windows Server 2003/2008 Minimum system requirements for ANSA/ META/ META Viewer/ EPILYSIS/ RETOMO/ KOMVOS/ CAD to ANSA translators OS Linux: glibc 2.3.3 or Windows: Windows 7 CPU Intel x64: Intel i5 - 4xxx or AMD x64: AMD Ryzen 1xxx RAM 8GB Disk Space 6GB Resolution 1920x1080 (HD) GPU NVIDIA or AMD GPU OpenGL Version: 3.3 GPU memory: 1GB Optional recommended OpenCL Version: 1.2 2 Supported platforms and minimum system requirements March 09, 2021 Additional requirements for CAD to ANSA translators Windows Microsoft Visual C++ 2005 Redistributable Package Microsoft Visual C++ 2008 Redistributable Package Microsoft Visual C++ 2010 Redistributable Package Minimum system requirements for VR Software Windows: Windows 7 Steam VR (versions released in 2017 or later) CPU Intel x64: Intel i5 - 4590 or AMD x64: AMD FX 8350 or equivalent/ better RAM 8GB (16GB recommended) GPU NVIDIA GeForce GTX1060 or AMD Radeon RX 480 or equivalent/ better Headset (HMD) HTC VIVE or HTC VIVE Pro Oculus Rift Windows Mixed Reality 3 Supported platforms and minimum system requirements March 09, 2021 Recommended system requirements for SPDRM v1.1.0 or later SPDRM Server Hardware 64bit requirements LINUX CPU: 4-core/8-thread intel i7 CPU (e.g. -

Management System UNIVERGE MA4000 Installation Guide (R9.1.0)
UC for Enterprise (UCE) Management System (UNIVERGE MA4000) Installation Guide NEC NEC Corporation October 2010 NDA-30363, Revision 16 Liability Disclaimer NEC Corporation reserves the right to change the specifications, functions, or features, at any time, without notice. NEC Corporation has prepared this document for the exclusive use of its employees and customers. The information contained herein is the property of NEC Corporation and shall not be reproduced without prior written approval from NEC Corporation © 2010 NEC Corporation Microsoft®, Windows®, SQL Server®, and MSDE® are registered trademarks of Microsoft Corporation. All other brand or product names are or may be trademarks or registered trademarks of, and are used to identify products or services of, their respective owners. i Contents Introduction 1-1 MA4000 Overview. 1-1 How This Guide is Organized . 1-2 Getting Started 2-1 Web Server Requirements . 2-2 Web Server Recommendations . 2-3 Internet Information Services Requirements. 2-4 WMI and SNMP Requirements. 2-8 Database Server Requirements . 2-10 Database Storage Requirements . 2-10 SQL Server 2008 Installation Requirements. 2-11 SQL Server 2005 Installation Requirements. 2-12 Authentication Mode Configuration. 2-14 Distributed Transaction Coordinator . 2-15 Remote Database Connections . 2-17 Web Client Requirements . 2-24 Installation 3-1 Installing MA4000 . 3-1 Web Site and Application Pool (Advanced Mode) . 3-8 NEC Centralized Authentication Service Location . 3-9 Database Installation (Advanced Mode) . 3-9 Database Password (Advanced Mode) . 3-12 SQL Server Express Prerequisites . 3-14 Database User Account (Advanced Mode). 3-17 Database Settings (Advanced Mode) . 3-18 Windows User Account (Advanced Mode) .