Hierarchical Techniques for Visibility Computations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Finding Neighbors in a Forest: a B-Tree for Smoothed Particle Hydrodynamics Simulations
Finding Neighbors in a Forest: A b-tree for Smoothed Particle Hydrodynamics Simulations Aurélien Cavelan University of Basel, Switzerland [email protected] Rubén M. Cabezón University of Basel, Switzerland [email protected] Jonas H. M. Korndorfer University of Basel, Switzerland [email protected] Florina M. Ciorba University of Basel, Switzerland fl[email protected] May 19, 2020 Abstract Finding the exact close neighbors of each fluid element in mesh-free computational hydrodynamical methods, such as the Smoothed Particle Hydrodynamics (SPH), often becomes a main bottleneck for scaling their performance beyond a few million fluid elements per computing node. Tree structures are particularly suitable for SPH simulation codes, which rely on finding the exact close neighbors of each fluid element (or SPH particle). In this work we present a novel tree structure, named b-tree, which features an adaptive branching factor to reduce the depth of the neighbor search. Depending on the particle spatial distribution, finding neighbors using b-tree has an asymptotic best case complexity of O(n), as opposed to O(n log n) for other classical tree structures such as octrees and quadtrees. We also present the proposed tree structure as well as the algorithms to build it and to find the exact close neighbors of all particles. arXiv:1910.02639v2 [cs.DC] 18 May 2020 We assess the scalability of the proposed tree-based algorithms through an extensive set of performance experiments in a shared-memory system. Results show that b-tree is up to 12× faster for building the tree and up to 1:6× faster for finding the exact neighbors of all particles when compared to its octree form. -

Skip-Webs: Efficient Distributed Data Structures for Multi-Dimensional Data Sets
Skip-Webs: Efficient Distributed Data Structures for Multi-Dimensional Data Sets Lars Arge David Eppstein Michael T. Goodrich Dept. of Computer Science Dept. of Computer Science Dept. of Computer Science University of Aarhus University of California University of California IT-Parken, Aabogade 34 Computer Science Bldg., 444 Computer Science Bldg., 444 DK-8200 Aarhus N, Denmark Irvine, CA 92697-3425, USA Irvine, CA 92697-3425, USA large(at)daimi.au.dk eppstein(at)ics.uci.edu goodrich(at)acm.org ABSTRACT name), a prefix match for a key string, a nearest-neighbor We present a framework for designing efficient distributed match for a numerical attribute, a range query over various data structures for multi-dimensional data. Our structures, numerical attributes, or a point-location query in a geomet- which we call skip-webs, extend and improve previous ran- ric map of attributes. That is, we would like the peer-to-peer domized distributed data structures, including skipnets and network to support a rich set of possible data types that al- skip graphs. Our framework applies to a general class of data low for multiple kinds of queries, including set membership, querying scenarios, which include linear (one-dimensional) 1-dim. nearest neighbor queries, range queries, string prefix data, such as sorted sets, as well as multi-dimensional data, queries, and point-location queries. such as d-dimensional octrees and digital tries of character The motivation for such queries include DNA databases, strings defined over a fixed alphabet. We show how to per- location-based services, and approximate searches for file form a query over such a set of n items spread among n names or data titles. -

Octree Generating Networks: Efficient Convolutional Architectures for High-Resolution 3D Outputs
Octree Generating Networks: Efficient Convolutional Architectures for High-resolution 3D Outputs Maxim Tatarchenko1 Alexey Dosovitskiy1,2 Thomas Brox1 [email protected] [email protected] [email protected] 1University of Freiburg 2Intel Labs Abstract Octree Octree Octree dense level 1 level 2 level 3 We present a deep convolutional decoder architecture that can generate volumetric 3D outputs in a compute- and memory-efficient manner by using an octree representation. The network learns to predict both the structure of the oc- tree, and the occupancy values of individual cells. This makes it a particularly valuable technique for generating 323 643 1283 3D shapes. In contrast to standard decoders acting on reg- ular voxel grids, the architecture does not have cubic com- Figure 1. The proposed OGN represents its volumetric output as an octree. Initially estimated rough low-resolution structure is gradu- plexity. This allows representing much higher resolution ally refined to a desired high resolution. At each level only a sparse outputs with a limited memory budget. We demonstrate this set of spatial locations is predicted. This representation is signifi- in several application domains, including 3D convolutional cantly more efficient than a dense voxel grid and allows generating autoencoders, generation of objects and whole scenes from volumes as large as 5123 voxels on a modern GPU in a single for- high-level representations, and shape from a single image. ward pass. large cell of an octree, resulting in savings in computation 1. Introduction and memory compared to a fine regular grid. At the same 1 time, fine details are not lost and can still be represented by Up-convolutional decoder architectures have become small cells of the octree. -

Evaluation of Spatial Trees for Simulation of Biological Tissue
Evaluation of spatial trees for simulation of biological tissue Ilya Dmitrenok∗, Viktor Drobnyy∗, Leonard Johard and Manuel Mazzara Innopolis University Innopolis, Russia ∗ These authors contributed equally to this work. Abstract—Spatial organization is a core challenge for all large computation time. The amount of cells practically simulated on agent-based models with local interactions. In biological tissue a single computer generally stretches between a few thousands models, spatial search and reinsertion are frequently reported to a million, depending on detail level, hardware and simulated as the most expensive steps of the simulation. One of the main methods utilized in order to maintain both favourable algorithmic time range. complexity and accuracy is spatial hierarchies. In this paper, we In center-based models, movement and neighborhood de- seek to clarify to which extent the choice of spatial tree affects tection remains one of the main performance bottlenecks [2]. performance, and also to identify which spatial tree families are Performances in these bottlenecks are deeply intertwined with optimal for such scenarios. We make use of a prototype of the the spatial structure chosen for the simulation. new BioDynaMo tissue simulator for evaluating performances as well as for the implementation of the characteristics of several B. BioDynaMo different trees. The BioDynaMo project [3] is developing a new general I. INTRODUCTION platform for computer simulations of biological tissue dynam- The high pace of neuroscientific research has led to a ics, with a brain development as a primary target. The platform difficult problem in synthesizing the experimental results into should be executable on hybrid cloud computing systems, effective new hypotheses. -

The Peano Software—Parallel, Automaton-Based, Dynamically Adaptive Grid Traversals
The Peano software|parallel, automaton-based, dynamically adaptive grid traversals Tobias Weinzierl ∗ December 4, 2018 Abstract We discuss the design decisions, design alternatives and rationale behind the third generation of Peano, a framework for dynamically adaptive Cartesian meshes derived from spacetrees. Peano ties the mesh traversal to the mesh storage and supports only one element-wise traversal order resulting from space-filling curves. The user is not free to choose a traversal order herself. The traversal can exploit regular grid subregions and shared memory as well as distributed memory systems with almost no modifications to a serial application code. We formalize the software design by means of two interacting automata|one automaton for the multiscale grid traversal and one for the application- specific algorithmic steps. This yields a callback-based programming paradigm. We further sketch the supported application types and the two data storage schemes real- ized, before we detail high-performance computing aspects and lessons learned. Special emphasis is put on observations regarding the used programming idioms and algorith- mic concepts. This transforms our report from a \one way to implement things" code description into a generic discussion and summary of some alternatives, rationale and design decisions to be made for any tree-based adaptive mesh refinement software. 1 Introduction Dynamically adaptive grids are mortar and catalyst of mesh-based scientific computing and thus important to a large range of scientific and engineering applications. They enable sci- entists and engineers to solve problems with high accuracy as they invest grid entities and computational effort where they pay off most. -

The Skip Quadtree: a Simple Dynamic Data Structure for Multidimensional Data
The Skip Quadtree: A Simple Dynamic Data Structure for Multidimensional Data David Eppstein† Michael T. Goodrich† Jonathan Z. Sun† Abstract We present a new multi-dimensional data structure, which we call the skip quadtree (for point data in R2) or the skip octree (for point data in Rd , with constant d > 2). Our data structure combines the best features of two well-known data structures, in that it has the well-defined “box”-shaped regions of region quadtrees and the logarithmic-height search and update hierarchical structure of skip lists. Indeed, the bottom level of our structure is exactly a region quadtree (or octree for higher dimensional data). We describe efficient algorithms for inserting and deleting points in a skip quadtree, as well as fast methods for performing point location and approximate range queries. 1 Introduction Data structures for multidimensional point data are of significant interest in the computational geometry, computer graphics, and scientific data visualization literatures. They allow point data to be stored and searched efficiently, for example to perform range queries to report (possibly approximately) the points that are contained in a given query region. We are interested in this paper in data structures for multidimensional point sets that are dynamic, in that they allow for fast point insertion and deletion, as well as efficient, in that they use linear space and allow for fast query times. Related Previous Work. Linear-space multidimensional data structures typically are defined by hierar- chical subdivisions of space, which give rise to tree-based search structures. That is, a hierarchy is defined by associating with each node v in a tree T a region R(v) in Rd such that the children of v are associated with subregions of R(v) defined by some kind of “cutting” action on R(v). -

Hierarchical Bounding Volumes Grids Octrees BSP Trees Hierarchical
Spatial Data Structures HHiieerraarrcchhiiccaall BBoouunnddiinngg VVoolluummeess GGrriiddss OOccttrreeeess BBSSPP TTrreeeess 11/7/02 Speeding Up Computations • Ray Tracing – Spend a lot of time doing ray object intersection tests • Hidden Surface Removal – painters algorithm – Sorting polygons front to back • Collision between objects – Quickly determine if two objects collide Spatial data-structures n2 computations 3 Speeding Up Computations • Ray Tracing – Spend a lot of time doing ray object intersection tests • Hidden Surface Removal – painters algorithm – Sorting polygons front to back • Collision between objects – Quickly determine if two objects collide Spatial data-structures n2 computations 3 Speeding Up Computations • Ray Tracing – Spend a lot of time doing ray object intersection tests • Hidden Surface Removal – painters algorithm – Sorting polygons front to back • Collision between objects – Quickly determine if two objects collide Spatial data-structures n2 computations 3 Speeding Up Computations • Ray Tracing – Spend a lot of time doing ray object intersection tests • Hidden Surface Removal – painters algorithm – Sorting polygons front to back • Collision between objects – Quickly determine if two objects collide Spatial data-structures n2 computations 3 Speeding Up Computations • Ray Tracing – Spend a lot of time doing ray object intersection tests • Hidden Surface Removal – painters algorithm – Sorting polygons front to back • Collision between objects – Quickly determine if two objects collide Spatial data-structures n2 computations 3 Spatial Data Structures • We’ll look at – Hierarchical bounding volumes – Grids – Octrees – K-d trees and BSP trees • Good data structures can give speed up ray tracing by 10x or 100x 4 Bounding Volumes • Wrap things that are hard to check for intersection in things that are easy to check – Example: wrap a complicated polygonal mesh in a box – Ray can’t hit the real object unless it hits the box – Adds some overhead, but generally pays for itself. -

Spatial Partitioning and Functional Shape Matched Deformation
SPATIAL PARTITIONING AND FUNCTIONAL SHAPE MATCHED DEFORMATION ALGORITHM FOR INTERACTIVE HAPTIC MODELING A dissertation presented to the faculty of the Russ College of Engineering and Technology of Ohio University In partial fulfillment of the requirements for the degree Doctor of Philosophy Wei Ji November 2008 © 2008 Wei Ji. All Rights Reserved. 2 This dissertation titled SPATIAL PARTITIONING AND FUNCTIONAL SHAPE MATCHED DEFORMATION ALGORITHM FOR INTERACTIVE HAPTIC MODELING by WEI JI has been approved for the School of Electrical Engineering and Computer Science and the Russ College of Engineering and Technology by Robert L. Williams II Professor of Mechanical Engineering Dennis Irwin Dean, Russ College of Engineering and Technology 3 Abstract JI, WEI, Ph.D., November 2008, Computer Science SPATIAL PARTITIONING AND FUNCTIONAL SHAPE MATCHED DEFORMATION ALGORITHM FOR INTERACTIVE HAPTIC MODELING (161 pp.) Director of Dissertation: Robert L. Williams II This dissertation focuses on the fast rendering algorithms on real-time 3D modeling. To improve the computational efficiency, binary space partitioning (BSP) and octree are implemented on the haptic model. Their features are addressed in detail. Three methods of triangle assignment with the splitting plane are discussed. The solutions for optimizing collision detection (CD) are presented and compared. The complexities of these partition methods are discussed, and recommendation is made. Then the deformable haptic model is presented. In this research, for the haptic modeling, the deformation calculation is only related to the graphics process because the haptic rendering is invisible and non-deformable rendering saves much computation cost. To achieve the fast deformation computation in the interactive simulation, the functional shape matched deformation (FSMD) algorithm is proposed for the tangential and normal components of the surface deformation. -

1 2 3 1 2 3 This Paper Presents the Design, Implementation and Evaluation of the Etree, a Database-Oriented Method for Large
ETREE — A DATABASE-ORIENTED METHOD FOR GENERATING LARGE OCTREE MESHES ¡ ¢ Tiankai Tu David R. O’Hallaron Julio C. Lopez´ £ Computer Science Department, [email protected] ¤ Computer Science Department and Electrical and Computer Engineering Department, [email protected] ¥ Electrical and Computer Engineering Department, [email protected] Carnegie Mellon University, Pittsburgh, PA, U.S.A. ABSTRACT ¦¨§ © § ! ©#"$&%'© () * ()+,-© ./012/*#3 © ./4.56§ 87:9<;77:%=> -,$? @A.$© B0()§!.+85C.$D*#-"/ ./3@[email protected]() §4"/!,© .$&HJIK3!D( © L©#BM© .8( $ L$L.EG.18 -,$? F N3 E:3!FO 5C.$(P*#* .E./ :,© ./! Q?RFS3 :R!© !"§ -,$? $ /HUT03! WV¨.X -,$? $ E:§! ©#S3 ¨YZ§!*#© !BQS+3 /+$[§!\]@^ .©# !_)$) N.`§ a.E,+ 6.$X!© bHcT0a©#.+3 EUdV=.WV¨. VJE:§! ©#S3 'Ye$3!.B2+© "f-©#.$F)* .EB$*g?*#$ E©#!" .h/ + =§!K E©#*i!B).$5j() §)"/ ,-©#.$&H]kc* ©#()© R 2$$* 3-© ./X 3 "/"$ N ¨§-¨§ a`()§ .+)© 6GlgE© 2f V6R>.5m"/!,© " 2f:RF*#"$h.E() §! hn<op qGrQ\sVU©t§OuBqp v ()© *#* © ./w* ()+ ,x¨.$M)()().R+@W* © ()©tB ( $E,§ © nNu-yz {F\6x:H |[}+~ih/ Ki/-}+}0M}B]j}+-}}'Cj}+ i/-}+}'j4&&C!BCmmCi/¨ Cjfjj]-}+} 1. INTRODUCTION ( $b/a©t= ./ © ? * `. N.`*#"$Q() §! ].$ E./+2f© ./ $* !© b+ Hm¯j-"/`( $© G()().$R)E$ E©t© `E$F .2+©#!K5C@ 5E© 2f>EB$E,§ X5C.$ § >!,1 N.BJ./°!© bH±`4© !@ ¦¨§ © D© $L_E©t©#!"w()./()5.D§ X() §O"/ ,-©#.$ EB BN/I²§!./3!"/§! 3!( $bf ©tD .$ ©#?!* [.M N$( E.$()(3 !©tdRHaQ© bFEB $E© WRw© Q_ * .+!© !"G> !© Eh *#"$ $()./3! K.$5¨ -,X© .[()().R>-Q, Q§ !@ ? ©tU© a * 3 ()()© !"!%VU©t§F"/© "/$?R+ U.$5' N.$,"/B2/© *? * !./$E,§F( $© G()().$RD, N5C`,- H 5.3 !QD§ -

High Quality Interactive Rendering of Massive Point Models Using Multi-Way Kd-Trees
High Quality Interactive Rendering of Massive Point Models using Multi-way kd-Trees Prashant Goswami Yanci Zhang Renato Pajarola Enrico Gobbetti University of Zurich Sichuan University University of Zurich CRS4 Switzerland China Switzerland Italy goswami@ifi.uzh.ch [email protected] [email protected] [email protected] Abstract—We present a simple and efficient technique for sized nodes. Since all blocks are equal sized, on-board out-of-core multiresolution construction and high quality visu- memory management is particularly simple and effective. alization of large point datasets. The method introduces a novel The presented approach results in fast pre-processing and hierarchical LOD data organization based on multi-way kd-trees that simplifies memory management and allows controlling the high quality rendering of massive point clouds at hundreds LOD tree’s height. The technique is incorporated in a full end- of millions of splats/second on modern GPUs, improving to-end system, which is evaluated on complex models made of the quality vs. performance ratio compared to previous large hundreds of millions of points. point data rendering methods. Keywords-point based rendering; gpu-based; multi-way kd- tree; II. RELATED WORK While the use of points as rendering primitives has been I. INTRODUCTION introduced as early as in [1], [2], only over the last decade they have reached the significance of fully established ge- Modern 3D scanning systems can generate massive data ometry and graphics primitives, see also [3]–[5]. Several sets with hundreds of millions of points. Despite the ad- techniques have since been proposed for improving upon vances in point-based modeling and rendering, these models the display quality, LOD rendering, as well as for efficient can still be a challenge to be processed and in particular out-of-core rendering of large point models. -
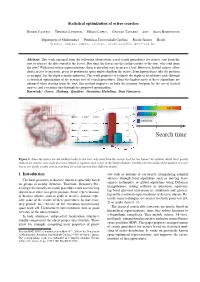
Statistical Optimization of Octree Searches
Statistical optimization of octree searches RENER CASTRO,THOMAS LEWINER,HELIO´ LOPES,GEOVAN TAVARES AND ALEX BORDIGNON Department of Mathematics — Pontif´ıcia Universidade Catolica´ — Rio de Janeiro — Brazil frener, tomlew, lopes, tavares, [email protected]. Abstract. This work emerged from the following observation: usual search procedures for octrees start from the root to retrieve the data stored at the leaves. But since the leaves are the farthest nodes to the root, why start from the root? With usual octree representations, there is no other way to access a leaf. However, hashed octrees allow direct access to any node, given its position in space and its depth in the octree. Search procedures take the position as an input, but the depth remains unknown. This work proposes to estimate the depth of an arbitrary node through a statistical optimization of the average cost of search procedures. Since the highest costs of these algorithms are obtained when starting from the root, this method improves on both the memory footprint by the use of hashed octrees, and execution time through the proposed optimization. Keywords: Octree. Hashing. Quadtree. Geometric Modelling. Data Structures. top down x 104 bottom up 8 statistical 6 1 8 18 4 # leaves Search time 2 0 12 3 4 5 6 7 8 9 10 level Figure 1: Since the leaves are the farthest nodes to the root, why start from the root to look for the leaves? An optimal initial level greatly reduces the search costs: (left) an octree refined to separate each vertex of the Stanford bunny; (middle) the histogram of the number of octree leaves per depth; (right) cost of searching for a leaf starting from different depths. -

Comparison of Nearest-Neighbor-Search Strategies and Implementations for Efficient Shape Registration
Journal of Software Engineering for Robotics 3(1), March 2012, 2-12 ISSN: 2035-3928 Comparison of nearest-neighbor-search strategies and implementations for efficient shape registration Jan Elseberg1,∗ Stephane´ Magnenat2 Roland Siegwart2 Andreas Nuchter¨ 1 1 Automation Group, Jacobs University Bremen gGmbH, 28759 Bremen, Germany 2 Autonomous Systems Lab, ETH Zurich,¨ Switzerland ∗[email protected] Abstract—The iterative closest point (ICP) algorithm is one of the most popular approaches to shape registration currently in use. At the core of ICP is the computationally-intensive determination of nearest neighbors (NN). As of now there has been no comprehensive analysis of competing search strategies for NN. This paper compares several libraries for nearest-neighbor search (NNS) on both simulated and real data with a focus on shape registration. In addition, we present a novel efficient implementation of NNS via k-d trees as well as a novel algorithm for NNS in octrees. Index Terms—shape registration, nearest neighbor search, k-d tree, octree, data structures 1 INTRODUCTION point can be avoided by employing spatial data structures. The average runtime of NNS is then usually in the order Shape registration is the problem of finding the rigid trans- of O(n log m) but is still by far the most computationally formation that, given two shapes, transforms one onto the expensive part of shape registration. This paper gives a other. The given shapes do not need to be wholly identical. comprehensive empirical analysis of NNS algorithms in the As long as a partial overlap is possible, shape registration domain of 3-dimensional shape matching.