Project 2: Part 4: MKDIR, REMOVE and Locking
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intermedia: a System for Linking Multimedia Documents. IRIS
DOCUMENT RESUME ED 296 735 IR 052 399 AUTHOR Yankelovich, Nicole TITLE Intermedia: A System for Linking Multimrdia Documents. IRIS Technical Report 86-2. INSTITUTION Brown Univ., Providence, RI. Inst. for Research in Information and Scholarship. PUB DATE 86 NOTE 19p. PUB TYPE Reports - Descriptive (141) EDRS PRICE MF01/PC01 Plus Postage. D'1CRIPTORS Bibliographic Coupling; *Computer Assisted Instruction; Computer Graphics; *Computer System Design; Higher Education; *Information Retrieval; *Man Machine Systems; *Multimedia Instruction; Word Processing IDENTIFIERS *Hypermedia ABSTRACT "Intermedia" is a hypermedia system which was developed for use in university research and teaching. It provides a framework for object-oriented, direct manipulation editors and applications, and the capability to link together materials created with those applications. Instructors are able to construct exploratory environments for their students as well as use applications for their day-to-day work, research, and writing. This paper provides a discussion of hypermedia systems in general, as well as a description of the Intermedia system which focuses on several important user features, and illustrates the operation of the system thrw,h a sample session. The text is supplemented by 15 figures. (19 references) (Author/EW) *********************************************************************** Reproductions supplied by EDRS are the best that can be made from the original document. *********************************************************************** INTERMEDIA: A System for customizing, visualizing, integratingand 0 Linking Multimedia Documents retrieving information. oi This paper describes Intermedia,one such tool designed for use in theuniversity O Nicole Yankelovich environment. The system, developedat Lid "PERMISSION TO REPRODUCE THIS Brown University's Institute for Researchin MATERIAL HAS BEEN GRANTED BY Information and Scholarship (IRIS),contains U.S. -

Io — I/O Functions
Title stata.com io — I/O functions Contents Description Remarks and examples Reference Also see Contents [M-5] Manual entry Function Purpose Console output printf( ) printf() display sprintf() display into string errprintf( ) errprintf() display error message display( ) display() display text interpreting SMCL displayas( ) displayas() set whether output is displayed displayflush( ) displayflush() flush terminal output buffer liststruct( ) liststruct() list structure’s contents more( ) more() create --more-- condition setmore() query or set more on or off setmoreonexit() set more on or off on exit File directories direxists( ) direxists() whether directory exists dir( ) dir() file list chdir( ) pwd() obtain current working directory chdir() change current working directory mkdir() make new directory rmdir() remove directory File management findfile( ) findfile() find file fileexists( ) fileexists() whether file exists cat( ) cat() read file into string matrix unlink( ) unlink() erase file adosubdir( ) adosubdir() obtain ado-subdirectory for file 1 2 io — I/O functions File I/O fopen( ) fopen() open file fclose() close file fget() read line of ASCII file fgetnl() same, but include newline character fread() read k bytes of binary file fput() write line into ASCII file fwrite() write k bytes into binary file fgetmatrix() read matrix fputmatrix() write matrix fstatus() status of last I/O command ftell() report location in file fseek() seek to location in file ftruncate() truncate file at current position ferrortext( ) ferrortext() error text of file error code freturncode() -
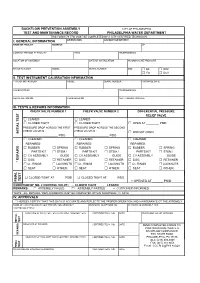
BFP Test Form
BACKFLOW PREVENTION ASSEMBLY CITY OF PHILADELPHIA TEST AND MAINTENANCE RECORD PHILADELPHIA WATER DEPARTMENT THIS FORM (79-770) MUST BE COMPLETED BY A CITY CERTIFIED TECHNICIAN I. GENERAL INFORMATION ORIENTATION ACCOUNT OR METER # NAME OF FACILITY ADDRESS ZIP CONTACT PERSON AT FACILITY TITLE TELEPHONE NO. LOCATION OF ASSEMBLY DATE OF INSTALLATION INCOMING LINE PRESSURE MANUFACTURER MODEL SERIAL NUMBER SIZE □ DS □ RPZ □ FS □ DCV II. TEST INSTRUMENT CALIBRATION INFORMATION TYPE OF INSTRUMENT MODEL SERIAL NUMBER PURCHASE DATE CALIBRATED BY TELEPHONE NO. REGISTRATION NO. CALIBRATED ON NEXT CALIBRATION DUE III. TESTS & REPAIRS INFORMATION CHECK VALVE NUMBER 1 CHECK VALVE NUMBER 2 DIFFERENTIAL PRESSURE RELIEF VALVE □ LEAKED □ LEAKED □ CLOSED TIGHT □ CLOSED TIGHT □ OPEN AT ________ PSID PRESSURE DROP ACROSS THE FIRST PRESSURE DROP ACROSS THE SECOND CHECK VALVE IS : CHECK VALVE IS : INITIAL TEST INITIAL □ DID NOT OPEN ______________________ PSID ______________________ PSID □ CLEANED □ CLEANED □ CLEANED REPAIRED: REPAIRED: REPAIRED: □ RUBBER □ SPRING □ RUBBER □ SPRING □ RUBBER □ SPRING PARTS KIT □ STEM / PARTS KIT □ STEM / PARTS KIT □ STEM / □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ DISC □ RETAINER □ DISC □ RETAINER □ DISC □ RETAINER * REPAIRS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ SEAT □ OTHER: □ SEAT □ OTHER: □ SEAT □ OTHER: □ CLOSED TIGHT AT ______ PSID □ CLOSED TIGHT AT ______ PSID TEST FINAL FINAL □ OPENED AT ______ PSID CONDITION OF NO. 2 CONTROL VALVE : □ CLOSED TIGHT □ LEAKED REMARKS : □ ASSEMBLY FAILED □ ASSEMBLY PASSED □ CUSTOMER INFORMED *NOTE : ALL REPAIRS / REPLACEMENTS MUST BE COMPLETED WITHIN FOURTEEN (14) DAYS IV. APPROVALS * I HEREBY CERTIFY THAT THIS DATA IS ACCURATE AND REFLECTS THE PROPER OPERATION AND MAINTENANCE OT THE ASSEMBLY NAME OF CERTIFIED BACKFLOW PREVENTION ASSEMBLY BUSINESS TELEPHONE NO. -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

This Document Explains How to Copy Ondemand5 Data to Your Hard Drive
Copying Your Repair DVD Data To Your Hard Drive Introduction This document explains how to copy OnDemand5 Repair data to your hard drive, and how to configure your OnDemand software appropriately. The document is intended for your network professional as a practical guide for implementing Mitchell1’s quarterly updates. The document provides two methods; one using the Xcopy command in a DOS window, and the other using standard Windows Copy and Paste functionality. Preparing your System You will need 8 Gigabytes of free space per DVD to be copied onto a hard drive. Be sure you have the necessary space before beginning this procedure. Turn off screen savers, power down options or any other program that may interfere with this process. IMPORTANT NOTICE – USE AT YOUR OWN RISK: This information is provided as a courtesy to assist those who desire to copy their DVD disks to their hard drive. Minimal technical assistance is available for this procedure. It is not recommended due to the high probability of failure due to DVD drive/disk read problems, over heating, hard drive write errors and memory overrun issues. This procedure is very detailed and should only be performed by users who are very familiar with Windows and/or DOS commands. Novice computers users should not attempt this procedure. Copying Repair data from a DVD is a time-consuming process. Depending on the speed of your processor and/or network, could easily require two or more hours per disk. For this reason, we recommend that you perform the actual copying of data during non-business evening or weekend hours. -

AT Command User Guide 80591ST10886A Rev
LN940 SERIES AT Command User Guide 80591ST10886A Rev. 1.4 – 2018-04-05 ] 7 .201 Mod. 0806 2017-01 Rev.6 01 [ SPECIFICATIONS ARE SUBJECT TO CHANGE WITHOUT NOTICE NOTICES LIST While reasonable efforts have been made to assure the accuracy of this document, Telit assumes no liability resulting from any inaccuracies or omissions in this document, or from use of the information obtained herein. The information in this document has been carefully checked and is believed to be reliable. However, no responsibility is assumed for inaccuracies or omissions. Telit reserves the right to make changes to any products described herein and reserves the right to revise this document and to make changes from time to time in content hereof with no obligation to notify any person of revisions or changes. Telit does not assume any liability arising out of the application or use of any product, software, or circuit described herein; neither does it convey license under its patent rights or the rights of others. It is possible that this publication may contain references to, or information about Telit products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that Telit intends to announce such Telit products, programming, or services in your country. COPYRIGHTS This instruction manual and the Telit products described in this instruction manual may be, include or describe copyrighted Telit material, such as computer programs stored in semiconductor memories or other media. Laws in the Italy and other countries preserve for Telit and its licensors certain exclusive rights for copyrighted material, including the exclusive right to copy, reproduce in any form, distribute and make derivative works of the copyrighted material. -

Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red Font Color Or Gray Highlights Indicate Text That Appears in the Instructor Copy Only
Lab - Observing DNS Resolution (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail Servers Background / Scenario The Domain Name System (DNS) is invoked when you type a Uniform Resource Locator (URL), such as http://www.cisco.com, into a web browser. The first part of the URL describes which protocol is used. Common protocols are Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol over Secure Socket Layer (HTTPS), and File Transfer Protocol (FTP). DNS uses the second part of the URL, which in this example is www.cisco.com. DNS translates the domain name (www.cisco.com) to an IP address to allow the source host to reach the destination host. In this lab, you will observe DNS in action and use the nslookup (name server lookup) command to obtain additional DNS information. Work with a partner to complete this lab. Required Resources 1 PC (Windows 7, Vista, or XP with Internet and command prompt access) Part 1: Observe the DNS Conversion of a URL to an IP Address a. Click the Windows Start button, type cmd into the search field, and press Enter. The command prompt window appears. b. At the command prompt, ping the URL for the Internet Corporation for Assigned Names and Numbers (ICANN) at www.icann.org. ICANN coordinates the DNS, IP addresses, top-level domain name system management, and root server system management functions. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Powerview Command Reference
PowerView Command Reference TRACE32 Online Help TRACE32 Directory TRACE32 Index TRACE32 Documents ...................................................................................................................... PowerView User Interface ............................................................................................................ PowerView Command Reference .............................................................................................1 History ...................................................................................................................................... 12 ABORT ...................................................................................................................................... 13 ABORT Abort driver program 13 AREA ........................................................................................................................................ 14 AREA Message windows 14 AREA.CLEAR Clear area 15 AREA.CLOSE Close output file 15 AREA.Create Create or modify message area 16 AREA.Delete Delete message area 17 AREA.List Display a detailed list off all message areas 18 AREA.OPEN Open output file 20 AREA.PIPE Redirect area to stdout 21 AREA.RESet Reset areas 21 AREA.SAVE Save AREA window contents to file 21 AREA.Select Select area 22 AREA.STDERR Redirect area to stderr 23 AREA.STDOUT Redirect area to stdout 23 AREA.view Display message area in AREA window 24 AutoSTOre ..............................................................................................................................