Enhancing Silverlight Video Experiences with Contextual Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ironpython in Action
IronPytho IN ACTION Michael J. Foord Christian Muirhead FOREWORD BY JIM HUGUNIN MANNING IronPython in Action Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> IronPython in Action MICHAEL J. FOORD CHRISTIAN MUIRHEAD MANNING Greenwich (74° w. long.) Download at Boykma.Com Licensed to Deborah Christiansen <[email protected]> For online information and ordering of this and other Manning books, please visit www.manning.com. The publisher offers discounts on this book when ordered in quantity. For more information, please contact Special Sales Department Manning Publications Co. Sound View Court 3B fax: (609) 877-8256 Greenwich, CT 06830 email: [email protected] ©2009 by Manning Publications Co. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by means electronic, mechanical, photocopying, or otherwise, without prior written permission of the publisher. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in the book, and Manning Publications was aware of a trademark claim, the designations have been printed in initial caps or all caps. Recognizing the importance of preserving what has been written, it is Manning’s policy to have the books we publish printed on acid-free paper, and we exert our best efforts to that end. Recognizing also our responsibility to conserve the resources of our planet, Manning books are printed on paper that is at least 15% recycled and processed without the use of elemental chlorine. -

Bloomberg Professional Services MENU
Software Compatibility Matrix English 16 July 2020 Version: 24.0 This document should be used in conjunction with the Bloomberg® Workstation Requirements and Bloomberg® Transport and Security document. Please see our website or BBPC<GO> on the Terminal for more information. The information provided in this document outlines the Microsoft® platforms that are compatible with the Bloomberg Terminal® and its associated software. These requirements should be taken into consideration when determining the overall suitability of the users’ workstation to successfully utilize all available functionality. Please keep the latest Bloomberg specifications in mind when planning workstation upgrades. Extended support end date* Minimum Product Comments Microsoft Bloomberg Requirements Operating Systems Windows 7 Home Premium *Only 64-Bit versions are supported. Ultimate *Windows 7 Starter Edition is not supported. Professional Service Pack 1 *Customers installing Bloomberg Terminal® software 14-Jan-20 31-Jan-22 Enterprise newly must install Microsoft .NET Framework 4.0 or higher. 64-Bit only Windows 8/8.1 *Only 64-Bit versions are supported. Pro *Customers must install Microsoft Silverlight in order to 10-Jan-23 *TBA* Enterprise run multimedia functions and the BMAP function. *Only 64-Bit versions are supported. Windows 10 *Windows 10 Mobile / Mobile Enterprise are not Home supported. *TBA* *TBA* Pro *Windows 10 in S mode is not supported. Education *Customers must install Microsoft Silverlight in order to Enterprise run multimedia functions and the BMAP function. Microsoft Office Versions Office 2010 Service Pack 2 *Office Starter 2010 is not supported. 13-Oct-20 30-Apr-21 Version 14.0.x Office Professional Service Pack 1 11-Apr-23 *TBA* 2013 Version 15.0.x Office 365 *Office 365 ProPlus must be installed on the local Service Pack 1 computer. -

Workspace Desktop Edition Developer's Guide
Workspace Desktop Edition Developer's Guide Best Practices for Views 10/3/2021 Contents • 1 Best Practices for Views • 1.1 Keyboard Navigation • 1.2 Branding • 1.3 Localization • 1.4 Parameterization • 1.5 Internationalization • 1.6 Screen Reader Compatibility • 1.7 Themes • 1.8 Loosely-coupled Application Library and Standard Controls • 1.9 Views Workspace Desktop Edition Developer's Guide 2 Best Practices for Views Best Practices for Views Purpose: To provide a set of recommendations that are required in order to implement a typical view within Workspace Desktop Edition. Workspace Desktop Edition Developer's Guide 3 Best Practices for Views Keyboard Navigation TAB Key--Every control in a window has the ability to have focus. Use the TAB key to move from one control to the next, or use SHIFT+TAB to move the previous control. The TAB order is determined by the order in which the controls are defined in the Extensible Application Markup Language (XAML) page. Access Keys--A labeled control can obtain focus by pressing the ALT key and then typing the control's associated letter (label). To add this functionality, include an underscore character (_) in the content of a control. See the following sample XAML file: [XAML] <Label Content="_AcctNumber" /> Focus can also be given to a specific GUI control by typing a single character. Use the WPF control AccessText (the counterpart of the TextBlock control) to modify your application for this functionality. For example, you can use the code in the following XAML sample to eliminate having to press the ALT key: [XAML] <AccessText Text="_AcctNumber" /> Shortcut Keys--Trigger a command by typing a key combination on the keyboard. -

RIA Development with Silverlight &
RIA Development with Silverlight & WPF James Chittenden UX Evangelist Public Sector Why RIA? WPF Silverlight “A line-of-business application is one of the set of critical computer applications that are vital to running an enterprise ” – Wikipedia http://en.wikipedia.org/wiki/Line_of_business Deployable & Maintainable We don’t have a designer Employees don’t care what it looks like If it ain’t broke… Return on investment Don’t have the budget “ Design matters. But design is not about decoration or about ornamentation. Design is about making communication as easy and clear for the viewer as possible.” – Garr Reynolds http://www.presentationzen.com 1 Simplicity 2 Visibility 3 Metaphor 4 Natural Mappings 5 Constraints 6 Error Prevention 7 Consistency WPF Silverlight Microsoft .NET Application Platform Deliver applications across the UX Continuum Consistent Tools & Application Model Develop Deploy Design Browser User Experience Continuum Client • Unify UI, media, graphics and documents • Take full advantage of the graphical power of the PC • Easy, low-impact deployment options • Integration with Office and Windows • Compatibility with Silverlight for web and devices Key WPF Platform Concepts Element Lookless XAML Composition Controls Composited Data Binding Visuals XAML: Declarative Programming for Windows • Markup – Build applications in simple declarative statements • Code and content are separate – Streamline collaboration between designers and developers • Easy for tools to consume and generate <Button Width="100">OK Button b1 = new Button(); -
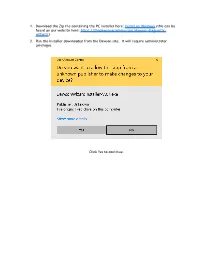
Dawson Install for Windows Users-V01
1. Download the Zip file containing the PC installer here: Install on Windows (this can be found on our website here: https://thedawsonacademy.com/dawson-diagnostic- wizard/) 2. Run the installer downloaded from the Dawson site. It will require administrator privileges. Click Yes to continue. 3. You will see the installer unpacking files and then see a message box letting you know that the installation will proceed. 4. Next, Microsoft Silverlight will be installed. Silverlight is the engine that runs the Dawson Wizard App. Click OK Uncheck the Bing and MSN boxes unless you want this, and click “Install now”. Note that any box that’s left check, will have that feature enabled for ALL your installed Browsers on your computer. Silverlight will proceed with the Install and you will see this window. Click “Close” to Continue. If Silverlight requires any additional configuration, you will see this window which will automatically close and take you to the next step when completed. 5. The next message window lets you know that the Dawson Wizard App installation step is about to proceed. After clicking OK, a Browser window will open where you will log into your account and the Dawson Wizard App will be downloaded and installed on your computer. Enter Credentials Wait for Download to finish Click “Install Application” and you will get another Install Window. Click “Install”: 6. Once the Install finishes, you’ll see the Dawson Wizard App running and a message box saying that the Install was successful. Click OK on the message box and log into the Dawson Wizard App with your credentials. -

Salesforce CLI Plug-In Developer Guide
Salesforce CLI Plug-In Developer Guide Salesforce, Winter ’22 @salesforcedocs Last updated: July 21, 2021 © Copyright 2000–2021 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark of salesforce.com, inc., as are other names and marks. Other marks appearing herein may be trademarks of their respective owners. CONTENTS Salesforce CLI Plug-In Developer Guide . 1 Salesforce CLI Plug-Ins . 1 Salesforce CLI Architecture . 3 Get Started with Salesforce CLI Plug-In Generation . 5 Naming and Messages for Salesforce CLI Plug-Ins . 7 Customize Your Salesforce CLI Plug-In . 13 Test Your Salesforce CLI Plug-In . 32 Debug Your Salesforce CLI Plug-In . 33 Best Practices for Salesforce CLI Plug-In Development . 33 Resources for Salesforce CLI Plug-In Development . 35 SALESFORCE CLI PLUG-IN DEVELOPER GUIDE Discover how to develop your own plug-ins for Salesforce CLI. Explore the Salesforce CLI architecture. Learn how to generate a plug-in using Salesforce Plug-In Generator, use Salesforce’s libraries to add functionality to your plug-in, and debug issues. Learn about our suggested style guidelines for naming and messages and our recommended best practices for plug-ins. Salesforce CLI Plug-Ins A plug-in adds functionality to Salesforce CLI. Some plug-ins are provided by Salesforce and are installed by default when you install the CLI. Some plug-ins, built by Salesforce and others, you install. When you have a requirement that an existing plug-in doesn’t meet, you can build your own using Node.js. Salesforce CLI Architecture Before you get started with adding functionality to Salesforce CLI, let’s take a high-level look at how the CLI and its dependencies and plug-ins work together. -

(RUNTIME) a Salud Total
Windows 7 Developer Guide Published October 2008 For more information, press only: Rapid Response Team Waggener Edstrom Worldwide (503) 443-7070 [email protected] Downloaded from www.WillyDev.NET The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This guide is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft. Microsoft may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place or event is intended or should be inferred. -

Internet Explorer Users Are Required to Add the Portal URL to Trusted Sites
CLA Client Portal Browser and Silverlight FAQs 1. Question: I am receiving an “Error 500” when clicking the link to access the CLA Document Portal. Resolution: Verify with your IT department that the portal is not blocked by any internal monitoring or protection applications. 2. Question: How do I know if my computer has Microsoft Silverlight Installed? Resolution: The first time you try and login to the portal you will be prompted to install Silverlight from Microsoft’s website if you don’t have it already installed. The installation typically takes less than one minute and is completely safe. http://www.microsoft.com/getsilverlight/Get-Started/Install/Default.aspx If you cannot, or prefer not to, install Silverlight on your machine, a simplified version of the document portal that does not require Silverlight is available. Click on the Take me to the non- Silverlight login on the CLA Document Portal page (www.claconnect.com/docportal). 3. Question: I cannot access the CLA Document Portal. (Server error/Page not found) Resolution: Check that you are using a Microsoft Silverlight 4 compatible browser on all PC’s or MAC. A complete list of browsers and operating systems that support Silverlight 4 can be found at http://www.microsoft.com/getsilverlight/locale/en-us/html/installation-win-SL4.html Please note: Internet Explorer users are required to add the portal URL to Trusted Sites. Adding to Trusted Sites Internet Explorer settings 1. Open Internet Explorer and browse to https://portal.cchaxcess.com/Portal/. 2. In Internet Explorer, select Tools / Internet Options; then select the Security tab and click Trusted Sites and then Sites. -

Spread for ASP.NET Developer's Guide
Spread for ASP.NET Developer’s Guide 0 Developer's Guide This guide provides introductory conceptual material and how-to explanations for routine tasks for developers using Spread for ASP.NET. It describes how an application developer would use the properties and methods in Spread to create spreadsheets and grids on Web Forms, bind to databases, and customize the component for your application. Getting Started Understanding the Product Working with the Spread Designer Customizing the Appearance Customizing User Interaction Customizing with Cell Types Managing Data Binding Managing Data in the Component Managing Formulas Managing File Operations Using Sheet Models Maintaining State Working with the Chart Control Using Touch Support with the Component For complete API reference information, refer to the Assembly Reference (on-line documentation). For a complete list of documentation, refer to the Spread for ASP.NET Documentation (on-line documentation). Copyright © GrapeCity, inc. All rights reserved. Spread for ASP.NET Developer’s Guide 1 1 Table of Contents Developer's Guide 0 1. Table of Contents 1-16 Getting Started 17 Handling Installation 17 Installing the Product 17 Licensing a Trial Project after Installation 17 End-User License Agreement 17-18 Creating a Build License 18-19 Handling Redistribution 19-20 Product Requirements 20 Handling Variations In Windows Settings 20-21 Working with the Component 21 Adding a Component to a Web Site using Visual Studio 2015 or 2017 21-24 Adding a Component to a Web Site using Visual Studio 2013 -

Automation Anywhere Version A2019.14 On-Premises Automation Anywhere - Contents
07/09/2020 Automation Anywhere Version A2019.14 On-Premises Automation Anywhere - Contents Contents Explore.......................................................................................................................................................................................7 Enterprise A2019 Release Notes...........................................................................................................................8 Enterprise A2019.14 Release Notes.........................................................................................................8 Enterprise A2019.13 Release Notes.......................................................................................................22 Enterprise A2019.12 Release Notes.......................................................................................................33 Enterprise A2019.11 Release Notes....................................................................................................... 45 Enterprise A2019.10 Release Notes.......................................................................................................55 Enterprise Version A2019 (Build 2094) Release Notes.................................................................... 62 Enterprise Version A2019 (Builds 1598 and 1610) Release Notes.................................................68 Enterprise Version A2019 (Builds 1082 and 1089) Release Notes................................................ 74 Enterprise A2019 (Build 550) Release Notes......................................................................................80 -

Visual Studio 2010 Tools for Sharepoint Development
Visual Studio 2010 for SharePoint Open XML and Content Controls COLUMNS Toolbox Visual Studio 2010 Tools for User Interfaces, Podcasts, Object-Relational Mappings SharePoint Development and More Steve Fox page 44 Scott Mitchell page 9 CLR Inside Out Profi ling the .NET Garbage- Collected Heap Subramanian Ramaswamy & Vance Morrison page 13 Event Tracing Event Tracing for Windows Basic Instincts Collection and Array Initializers in Visual Basic 2010 Generating Documents from SharePoint Using Open XML Adrian Spotty Bowles page 20 Content Controls Data Points Eric White page 52 Data Validation with Silverlight 3 and the DataForm John Papa page 30 Cutting Edge Data Binding in ASP.NET AJAX 4.0 Dino Esposito page 36 Patterns in Practice Functional Programming Core Instrumentation Events in Windows 7, Part 2 for Everyday .NET Developers MSDN Magazine Dr. Insung Park & Alex Bendetov page 60 Jeremy Miller page 68 Service Station Building RESTful Clients THIS MONTH at msdn.microsoft.com/magazine: Jon Flanders page 76 CONTRACT-FIRST WEB SERVICES: Schema-Based Development Foundations with Windows Communication Foundation Routers in the Service Bus Christian Weyer & Buddihke de Silva Juval Lowy page 82 TEST RUN: Partial Anitrandom String Testing Concurrent Affairs James McCaffrey Four Ways to Use the Concurrency TEAM SYSTEM: Customizing Work Items Runtime in Your C++ Projects Rick Molloy page 90 OCTOBER Brian A. Randell USABILITY IN PRACTICE: Getting Inside Your Users’ Heads 2009 Charles B. Kreitzberg & Ambrose Little Vol 24 No 10 Vol OCTOBER 2009 VOL 24 NO 10 OCTOBER 2009 VOLUME 24 NUMBER 10 LUCINDA ROWLEY Director EDITORIAL: [email protected] HOWARD DIERKING Editor-in-Chief WEB SITE MICHAEL RICHTER Webmaster CONTRIBUTING EDITORS Don Box, Keith Brown, Dino Esposito, Juval Lowy, Dr. -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . ..