Differentiate and Deliver: Leveraging Your Partners (CEO Panel)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
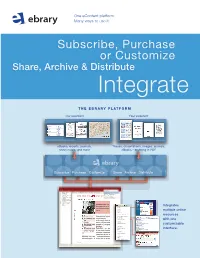
The EBRARY Platform
One eContent platform. Many ways to use it. Subscribe, Purchase or Customize Share, Archive & Distribute Integrate THE EBRARY PLatFORM Our eContent Your eContent eBooks, reports, journals, Theses, dissertations, images, journals, sheet music, and more eBooks – anything in PDF Subscribe Purchase Customize Share Archive Distribute SULAIR Select Collections SUL EBRARY COLLECTIONS Select Collections TABLE OF CONTENTS Infotools All ebrary Collections CONTRIBUTORS Byron Hoyt Sheet Music (Browse) INTRODUCTION Immigration Commision Reports (Dillingham) Contents BUSINESS: A USER’S GUIDE Women and Child Wage Earners in the U.S. CSLI Linguistics and Philosophy BEST PRACTICE SUL Books in the Public Domain MANAGEMENT CHECKLISTS Medieval and Modern Thought Text Project ACTIONLISTS MANAGEMENT LIBRARY BUSINESS THINKERS AND MANA DICTIONARY WORLD BUSINESS ALMANAC Highlights Notes BUSINESS INFORMATION SOURC INDEX CREDITS InfoTools Integrates Define Explain Locate multiple online Translate Search Document... resources Search All Documents... Search Web Search Catalog with one Highlight Add to Bookshelf customizable Copy Text... Copy Bookmark interface. Print... Print Again Toggle Automenu Preferences... Help About ebrary Reader... EASY TO USE. Subscribe, Purchase AFFORDABLE. or Customize your ALW ay S AVAILABLE. eBook selection NO CHECK-OUTS. Un I Q U E S U B SC R I B E T O G R OWI ng E B O O K D ataba S E S W I T H SIMULtanEOUS, MULTI-USER ACCESS. RESEARCH TOOLS. ACADEMIC DATABASES Academic Complete includes all academic databases listed below. FREE MARCS. # of # of Subject Titles* Subject Titles* Business & Economics 6,300 Language, Literature 3,400 & Linguistics “ebrary’s content is Computers & IT 2,800 Law, International Relations 3,800 multidisciplinary and Education 2,300 & Public Policy Engineering & Technology 3,700 supports our expanding Life Sciences 2,000 (includes Biotechnolgy, History & Political Science 4,800 Agriculture, and (also includes a bonus selection faculty and curriculum. -

Program Review Department of Computer Science
PROGRAM REVIEW DEPARTMENT OF COMPUTER SCIENCE UNIVERSITY OF NORTH CAROLINA AT CHAPEL HILL JANUARY 13-15, 2009 TABLE OF CONTENTS 1 Introduction............................................................................................................................. 1 2 Program Overview.................................................................................................................. 2 2.1 Mission........................................................................................................................... 2 2.2 Demand.......................................................................................................................... 3 2.3 Interdisciplinary activities and outreach ........................................................................ 5 2.4 Inter-institutional perspective ........................................................................................ 6 2.5 Previous evaluations ...................................................................................................... 6 3 Curricula ................................................................................................................................. 8 3.1 Undergraduate Curriculum ............................................................................................ 8 3.1.1 Bachelor of Science ................................................................................................. 10 3.1.2 Bachelor of Arts (proposed) ................................................................................... -

A Modeling Framework for Network Processor Systems
A Modeling Framework for Network Processor Systems Patrick Crowley & Jean-Loup Baer Department of Computer Science & Engineering University of Washington Seattle, WA 98195-2350 pcrowley, baer ¡ @cs.washington.edu Abstract cation W at the target line rate and number of inter- faces? This paper introduces a modeling framework for network ¢ If not, where are the bottlenecks? processing systems. The framework is composed of inde- ¢ If yes, can S support application W’ (that is, application pendent application, system and traffic models which de- W plus some new task) under the same constraints? scribe router functionality, system resources/organization ¢ Will a given hardware assist improve system perfor- and packet traffic, respectively. The framework uses the mance relative to a software implementation of the Click Modular router to describe router functionality. Click same task? modules are mapped onto an object-based description of ¢ How sensitive is system performance to input traffic? the system hardware and are profiled to determine maxi- mum packet flow through the system and aggregate resource The framework is composed of independent application, utilization for a given traffic model. This paper presents system and traffic models which describe router function- several modeling examples of uniprocessor and multipro- ality, system resources/organization and packet traffic, re- cessor systems executing IPv4 routing and IPSec VPN en- spectively. The framework uses the Click Modular router cryption/decryption. Model-based performance estimates to describe router functionality. Click modules are mapped are compared to the measured performance of the real sys- onto an object-based description of the system hardware tems being modeled; the estimates are found to be accurate and are profiled and simulated to determine maximum within 10%. -

Deepmatch: Practical Deep Packet Inspection in the Data Plane Using Network Processors
DeepMatch: Practical Deep Packet Inspection in the Data Plane using Network Processors Joel Hypolite John Sonchack Shlomo Hershkop The University of Pennsylvania Princeton University The University of Pennsylvania [email protected] [email protected] [email protected] Nathan Dautenhahn André DeHon Jonathan M. Smith Rice University The University of Pennsylvania The University of Pennsylvania [email protected] [email protected] [email protected] ABSTRACT Server Security Server ApplianceSecurity Restricting data plane processing to packet headers precludes anal- ApplianceSecurity 1 ysis of payloads to improve routing and security decisions. Deep- Applications DPIAppliance Applications DPI filtering DPI Match delivers line-rate regular expression matching on payloads Scalabilityfiltering IDS rules using Network Processors (NPs). It further supports packet re- DPI Challenge 2 rules ordering to match patterns in flows that cross packet boundaries. smartNIC Bottleneck Our evaluation shows that an implementation of DeepMatch, on a DeepMatch 40 Gbps Netronome NFP-6000 SmartNIC, achieves up to line rate for smartNIC + P4 streams of unrelated packets and up to 20 Gbps when searches span P4 DPI rules multiple packets within a flow. In contrast with prior work, this Header Header rules throughput is data-independent and adds no burstiness. DeepMatch 3 Network rules opens new opportunities for programmable data planes. Figure 1: DPI today (left and network) is limited by per- CCS CONCEPTS formance, scalability, and programming/management com- • Networks → Deep packet inspection; Programming inter- plexities (shaded red) inherent to the underlying deploy- faces; Programmable networks; ment models. DeepMatch (right) pushes DPI into the com- modity SmartNICs currently used to accelerate header fil- KEYWORDS tering and integrates DPI with P4, which improves perfor- Network processors, Programmable data planes, P4, SmartNIC mance and scalability while enabling a simpler deployment ACM Reference Format: model. -

Wavelets: a Primer
Wavelets A Primer Wavelets A Primer Christian Blatter Departement Mathematik ETH Zentrum Zurich, Switzerland Boca Raton London New York CRC Press is an imprint of the Taylor & Francis Group, an informa business AN A K PETERS BOOK First published 1998 by Ak Peters, Ltd. Published 2018 by CRC Press Taylor & Francis Group 6000 Broken Sound Parkway NW, Suite 300 Boca Raton, FL 33487-2742 © 1998 by Taylor & Francis Group, LLC CRC Press is an imprint of Taylor & Francis Group, an Informa business No claim to original U.S. Government works ISBN 13: 978-1-56881-195-6 (pbk) ISBN 13: 978-1-56881-095-9 (hbk) This book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders ifpermission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmitted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. For permission to photocopy or use material electronically from this work, please access www. -

Taylor & Francis
Taylor & Francis E-Book-Erwerbungsoptionen auf einen Blick Stand: Mai 2021 Plattform Taylor & Francis eBooks Imprints: AOCS Publishing - A K Peters/CRC Press - Apple Academic Press - Auerbach Publications - Blackwell - Burleigh Dodds Science Publishing - Birkbeck Law Press - Chapman and Hall - CRC Press - David Fulton Pulblishers - EPFL Press - Hakulyt Society - Informa Law from Routledge - Jennifer Stanford Publishing - Productivity Press - Psychology Press - RFF Press - RIBA Publishing - Routledge - Routledge India - Routledge-Cavendish - Spon Press- Taylor & Francis - Tecton NewMedia - UCL Press - Willan - W.W. Norton & Company Former Imprints: Ashgate -Focal Press - Elsevier - Landes Bioscience - Radcliff - Informa Healthcare - Pearson HE List/ Pearson (US) - Pearson - Nickel - Pyrczak - Speechmark - Earthscan - Acumen Publishing - Left Coast Press - Pickering & Chatto - Hodder Education - Longman - Garland - Routhledge Falmer - Brunner/Mazel - ME Sharp - Paradigm - Planners Press - Theatre Arts - Kegan Paul - Eye on Education - Transaction Publishing - St Jerome - Architectural Press - Harrington Park Press - GSER - Baywood - Bibliomotion - Westview Press - Karnac Books - Noordhof - Frank Cass - Accelerated Development - Brunner Routledge - James & James - Routledge Curca Flexible Angebotsformen für Ihre Bibliothek Einzeltitel Keine Mindestbestellmenge mehr. Pick & Choose Größere Bestellungen werden jedoch von den Verlagen bevorzugt. DRM-free-E-Books Wie gewohnt bietet Taylor & Francis weiterhin DRM-freie E-Books mit unlimitierten -

Software Self-Healing Using Error Virtualization
Software Self-healing Using Error Virtualization Stylianos Sidiroglou Submitted in partial fulfillment of the Requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2008 c 2008 Stylianos Sidiroglou All Rights Reserved ABSTRACT Stylianos Sidiroglou Software Self-healing Using Error Virtualization Despite considerable efforts in both research and development strategies, software errors and subsequent security vulnerabilities continue to be a significant problem for computer systems. The accepted wisdom is to approach the problem with a multitude of tools such as diligent software development strategies, dynamic bug finders and static analysis tools in an attempt to eliminate as many bugs as possible. Unfortunately, history has shown that it is very hard to achieve bug-free software. The situation is further exacerbated by the exorbitant cost of system down-time which some estimates place at six million dollars per hour. In the absence of perfect software, retrofitting error toleration and recovery techniques, in systems not designed to deal with failures, becomes a necessary complement to proactive approaches. Towards this goal, this dissertation introduces and evaluates a set of techniques for recovering program execution in the presence of faults by effectively retrofitting legacy applications with exception handling techniques, Error Virtualization and AS- SURE . The main premise of the approach is that there is a mapping between faults that may occur during program execution and a finite set of errors that are explicitly handled by the program’s code. Experimental results are presented to support our hypothesis. The results demonstrate that our techniques can recover program execu- tion in the case of failures in 80 to 90% of the examined cases, based on the technique used. -

CRC Press Catalogue 2020 July - December New and Forthcoming Titles
TAYLOR & FRANCIS CRC Press Catalogue 2020 July - December New and Forthcoming Titles www.routledge.com Welcome THE EASY WAY TO ORDER Book orders should be addressed to the Welcome to the July - December 2020 CRC Press catalogue. Taylor & Francis Customer Services Department at Bookpoint, or the appropriate In this catalogue you will find new and forthcoming CRC Press titles overseas offices. publishing across all subject areas including Life Sciences, Engineering, Food and Nutrition, Environmental Sciences, Mathematics and Statistics, Physics and Material Sciences, Computer Science, Agriculture, Biomedicine and Forensics Science and Homeland Security. Contacts UK and Rest of World: Bookpoint Ltd We welcome your feedback on our publishing programme, so please do Tel: +44 (0) 1235 400524 not hesitate to get in touch – whether you want to read, write, review, Email: [email protected] adapt or buy, we want to hear from you, so please visit our website below USA: or please contact your local sales representative for more information. Taylor & Francis Tel: 800-634-7064 Email: [email protected] www.crcpress.com Asia: Taylor & Francis Asia Pacific Tel: +65 6508 2888 Email: [email protected] China: Taylor & Francis China Tel: +86 10 58452881 Prices are correct at time of going to press and may be subject to change without Email: [email protected] notice. Some titles within this catalogue may not be available in your region. India: Taylor & Francis India Tel: +91 (0) 11 43155100 Email: [email protected] eBooks Partnership Opportunities at We have over 50,000 eBooks available across the Routledge Humanities, Social Sciences, Behavioural Sciences, At Routledge we always look for innovative ways to Built Environment, STM and Law, from leading support and collaborate with our readers and the Imprints, including Routledge, Focal Press and organizations they represent. -

Enhanced OS-9 Release Notes 58 Networking Notes 58 Protocol Modules 58 Utilities 59 Drivers 60 MAUI Notes 61 SNMP Notes 62 OS-9 Utilities Notes 62 Enhancements
Microware OS-9 Release Notes Version 3.2 www.radisys.com World Headquarters 5445 NE Dawson Creek Drive • Hillsboro, OR 97124 USA Phone: 503-615-1100 • Fax: 503-615-1121 Toll-Free: 800-950-0044 International Headquarters Gebouw Flevopoort • Televisieweg 1A NL-1322 AC • Almere, The Netherlands Phone: 31 36 5365595 • Fax: 31 36 5365620 RadiSys Microware Communications Software Division, Inc. 1500 N.W. 118th Street Des Moines, Iowa 50325 515-223-8000 Revision A December 2001 Copyright and publication information Reproduction notice This manual reflects version 3.2 of Microware OS-9. The software described in this document is intended to Reproduction of this document, in part or whole, by be used on a single computer system. RadiSys Corpo- any means, electrical, mechanical, magnetic, optical, ration expressly prohibits any reproduction of the soft- chemical, manual, or otherwise is prohibited, without written permission from RadiSys Microware ware on tape, disk, or any other medium except for Communications Software Division, Inc. backup purposes. Distribution of this software, in part or whole, to any other party or on any other system may Disclaimer constitute copyright infringements and misappropria- The information contained herein is believed to be tion of trade secrets and confidential processes which accurate as of the date of publication. However, are the property of RadiSys Corporation and/or other RadiSys Corporation will not be liable for any damages parties. Unauthorized distribution of software may including indirect or consequential, from use of the cause damages far in excess of the value of the copies OS-9 operating system, Microware-provided software, involved. -

Where to Find More Information About Computer Graphics and Related Topics
Where to Find More Information about Computer Graphics and Related Topics Mike Bailey Oregon State University 1. References 1.1 General Computer Graphics SIGGRAPH Online Bibliography Database: http://www.siggraph.org/publications/bibliography Edward Angel and Dave Shreiner, Interactive Computer Graphics: A Top-down Approach with OpenGL, 6th Edition, Addison-Wesley, 2011. Francis Hill and Stephen Kelley, Computer Graphics Using OpenGL, 3rd Edition, Prentice Hall, 2006. Steve Cunningham, Computer Graphics: Programming in OpenGL for Visual Communication, Prentice- Hall, 2007 Alan Watt, 3D Computer Graphics, 3rd Edition, Addison-Wesley, 2000. Peter Shirley, Fundamentals of Computer Graphics, 2nd Edition, AK Peters, 2005. Andrew Glassner, Graphics Gems, Academic Press, 1990. James Arvo, Graphics Gems 2, Academic Press, 1991. David Kirk, Graphics Gems 3, Academic Press, 1992. Paul Heckbert, Graphics Gems 4, Academic Press, 1994. Alan Paeth, Graphics Gems 5, Academic Press, 1995. Jim Blinn, A Trip Down the Graphics Pipeline, Morgan Kaufmann, 1996. Jim Blinn, Dirty Pixels, Morgan Kaufmann, 1998. David Rogers, Procedural Elements for Computer Graphics, McGraw-Hill, 1997. SIGGRAPH Conference Final program. 1.2 Math and Geometry Michael Mortenseon, Geometric Transformations for 3D Modeling, 2nd Edition, Industrial press, 2007. Michael Mortenson, Geometric Modeling, John Wiley & Sons, 2006. Eric Lengyel, Mathematics for 3D Game Programming and Computer Graphics, Charles River Media, 1 2002. Jean Gallier, Curves and Surfaces in Geometric Modeling, Morgan Kaufmann, 2000. Walter Taylor, The Geometry of Computer Graphics, Wadsworth & Brooks/Cole, 1992. Gerald Farin, Curves and Surfaces for Computer Aided Geometric Design, 3rd Edition, Academic Press, 2001. Gerald Farin and Dianne Hansford, The Geometry Toolbox for Graphics and Modeling, AK Peters, 1998. -

Foundations of Hybrid and Embedded Systems and Software
FINAL REPORT FOUNDATIONS OF HYBRID AND EMBEDDED SYSTEMS AND SOFTWARE NSF/ITR PROJECT – AWARD NUMBER: CCR-0225610 UNIVERSITY OF CALIFORNIA, BERKELEY November 26, 2010 PERIOD OF PERFORMANCE COVERED: November 14, 2002 – August 31, 2010 1 Contents 1 Participants 3 1.1 People ....................................... 3 1.2 PartnerOrganizations: . ... 9 1.3 Collaborators:.................................. 9 2 Activities and Findings 14 2.1 ProjectActivities ............................... .. 14 2.1.1 ITREvents ................................ 16 2.1.2 HybridSystemsTheory . .. .. 16 2.1.3 DeepCompositionality . 16 2.1.4 RobustHybridSystems . .. .. 16 2.1.5 Hybrid Systems and Systems Biology . .. 16 2.2 ProjectFindings................................. 16 3 Outreach 16 3.1 Project Training and Development . .... 16 3.2 OutreachActivities .............................. .. 16 3.2.1 Curriculum Development for Modern Systems Science (MSS)..... 16 3.2.2 Undergrad Course Insertion and Transfer . ..... 16 3.2.3 GraduateCourses............................. 16 4 Publications and Products 16 4.1 Technicalreports ................................ 16 4.2 PhDtheses .................................... 16 4.3 PhDtheses .................................... 16 4.4 Conferencepapers................................ 16 4.5 Books ....................................... 16 4.6 Journalarticles ................................. 16 4.6.1 The 2009-2010 Chess seminar series . ... 16 4.6.2 WorkshopsandInvitedTalks . 16 4.6.3 GeneralDissemination . 16 4.7 OtherSpecificProducts -

IXP1200 Hardware Reference Manual
Intel® IXP1200 Network Processor Family Hardware Reference Manual December 2001 Part Number: 278303-009 Intel® IXP1200 Network Processor Family Revision History Revision Date Revision Description 8/30/99 001 Beta 1 release. 10/29/99 002 Beta 3 release. 3/2/00 003 Beta 4 release. 6/5/00 004 Version 1.0 release. 9/27/00 005 Version 1.1 release. 12/20/00 006 Version 1.2 release. 6/1/01 007 Version 1.3 SDK release. 8/10/01 008 Version 2.0 SDK release. Miscellaneous changes. 12/07/01 009 Version 2.01 SDK release. Miscellaneous changes. Information in this document is provided in connection with Intel® products. No license, express or implied, by estoppel or otherwise, to any intellectual property rights is granted by this document. Except as provided in Intel’s Terms and Conditions of Sale for such products, Intel assumes no liability whatsoever, and Intel disclaims any express or implied warranty, relating to sale and/or use of Intel products including liability or warranties relating to fitness for a particular purpose, merchantability, or infringement of any patent, copyright or other intellectual property right. Intel products are not intended for use in medical, life saving, or life sustaining applications. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked “reserved” or “undefined.” Intel reserves these for future definition and shall have no responsibility whatsoever for conflicts or incompatibilities arising from future changes to them. The IXP1200 may contain design defects or errors known as errata which may cause the product to deviate from published specifications.