Propositional Logic
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Expressive Completeness
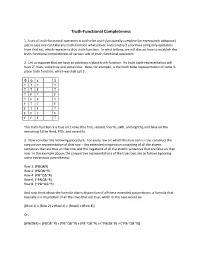
Truth-Functional Completeness 1. A set of truth-functional operators is said to be truth-functionally complete (or expressively adequate) just in case one can take any truth-function whatsoever, and construct a formula using only operators from that set, which represents that truth-function. In what follows, we will discuss how to establish the truth-functional completeness of various sets of truth-functional operators. 2. Let us suppose that we have an arbitrary n-place truth-function. Its truth table representation will have 2n rows, some true and some false. Here, for example, is the truth table representation of some 3- place truth function, which we shall call $: Φ ψ χ $ T T T T T T F T T F T F T F F T F T T F F T F T F F T F F F F T This truth-function $ is true on 5 rows (the first, second, fourth, sixth, and eighth), and false on the remaining 3 (the third, fifth, and seventh). 3. Now consider the following procedure: For every row on which this function is true, construct the conjunctive representation of that row – the extended conjunction consisting of all the atomic sentences that are true on that row and the negations of all the atomic sentences that are false on that row. In the example above, the conjunctive representations of the true rows are as follows (ignoring some extraneous parentheses): Row 1: (P&Q&R) Row 2: (P&Q&~R) Row 4: (P&~Q&~R) Row 6: (~P&Q&~R) Row 8: (~P&~Q&~R) And now think about the formula that is disjunction of all these extended conjunctions, a formula that basically is a disjunction of all the rows that are true, which in this case would be [(Row 1) v (Row 2) v (Row 4) v (Row6) v (Row 8)] Or, [(P&Q&R) v (P&Q&~R) v (P&~Q&~R) v (P&~Q&~R) v (~P&Q&~R) v (~P&~Q&~R)] 4. -

The Method of Proof Analysis: Background, Developments, New Directions
The Method of Proof Analysis: Background, Developments, New Directions Sara Negri University of Helsinki JAIST Spring School 2012 Kanazawa, March 5–9, 2012 Motivations and background Overview Hilbert-style systems Gentzen systems Axioms-as-rules Developments Proof-theoretic semantics for non-classical logics Basic modal logic Intuitionistic and intermediate logics Intermediate logics and modal embeddings Gödel-Löb provability logic Displayable logics First-order modal logic Transitive closure Completeness, correspondence, decidability New directions Social and epistemic logics Knowability logic References What is proof theory? “The main concern of proof theory is to study and analyze structures of proofs. A typical question in it is ‘what kind of proofs will a given formula A have, if it is provable?’, or ‘is there any standard proof of A?’. In proof theory, we want to derive some logical properties from the analysis of structures of proofs, by anticipating that these properties must be reflected in the structures of proofs. In most cases, the analysis will be based on combinatorial and constructive arguments. In this way, we can get sometimes much more information on the logical properties than with semantical methods, which will use set-theoretic notions like models,interpretations and validity.” (H. Ono, Proof-theoretic methods in nonclassical logic–an introduction, 1998) Challenges in modal and non-classical logics Difficulties in establishing analyticity and normalization/cut-elimination even for basic modal systems. Extension of proof-theoretic semantics to non-classical logic. Generality of model theory vs. goal directed developments in proof theory for non-classical logics. Proliferation of calculi “beyond Gentzen systems”. Defeatist attitudes: “No proof procedure suffices for every normal modal logic determined by a class of frames.” (M. -

Designing a Theorem Prover
Designing a Theorem Prover Lawrence C Paulson Computer Laboratory University of Cambridge May 1990 CONTENTS 2 Contents 1 Folderol: a simple theorem prover 3 1.1 Representation of rules :::::::::::::::::::::::::: 4 1.2 Propositional logic :::::::::::::::::::::::::::: 5 1.3 Quanti¯ers and uni¯cation :::::::::::::::::::::::: 7 1.4 Parameters in quanti¯er rules :::::::::::::::::::::: 7 2 Basic data structures and operations 10 2.1 Terms ::::::::::::::::::::::::::::::::::: 10 2.2 Formulae :::::::::::::::::::::::::::::::::: 11 2.3 Abstraction and substitution ::::::::::::::::::::::: 11 2.4 Parsing and printing ::::::::::::::::::::::::::: 13 3 Uni¯cation 14 3.1 Examples ::::::::::::::::::::::::::::::::: 15 3.2 Parameter dependencies in uni¯cation :::::::::::::::::: 16 3.3 The environment ::::::::::::::::::::::::::::: 17 3.4 The ML code for uni¯cation ::::::::::::::::::::::: 17 3.5 Extensions and omissions ::::::::::::::::::::::::: 18 3.6 Instantiation by the environment :::::::::::::::::::: 19 4 Inference in Folderol 20 4.1 Solving a goal ::::::::::::::::::::::::::::::: 21 4.2 Selecting a rule :::::::::::::::::::::::::::::: 22 4.3 Constructing the subgoals :::::::::::::::::::::::: 23 4.4 Goal selection ::::::::::::::::::::::::::::::: 25 5 Folderol in action 27 5.1 Propositional examples :::::::::::::::::::::::::: 27 5.2 Quanti¯er examples :::::::::::::::::::::::::::: 30 5.3 Beyond Folderol: advanced automatic methods ::::::::::::: 37 6 Interactive theorem proving 39 6.1 The Boyer/Moore theorem prover :::::::::::::::::::: 40 6.2 The Automath languages -

TMM023- DISCRETE MATHEMATICS (March 2021)
TMM023- DISCRETE MATHEMATICS (March 2021) Typical Range: 3-4 Semester Hours A course in Discrete Mathematics specializes in the application of mathematics for students interested in information technology, computer science, and related fields. This college-level mathematics course introduces students to the logic and mathematical structures required in these fields of interest. TMM023 Discrete Mathematics introduces mathematical reasoning and several topics from discrete mathematics that underlie, inform, or elucidate the development, study, and practice of related fields. Topics include logic, proof techniques, set theory, functions and relations, counting and probability, elementary number theory, graphs and tree theory, base-n arithmetic, and Boolean algebra. To qualify for TMM023 (Discrete Mathematics), a course must achieve all the following essential learning outcomes listed in this document (marked with an asterisk). In order to provide flexibility, institutions should also include the non-essential outcomes that are most appropriate for their course. It is up to individual institutions to determine if further adaptation of additional course learning outcomes beyond the ones in this document are necessary to support their students’ needs. In addition, individual institutions will determine their own level of student engagement and manner of implementation. These guidelines simply seek to foster thinking in this direction. 1. Formal Logic – Successful discrete mathematics students are able to construct and analyze arguments with logical precision. These students are able to apply rules from logical reasoning both symbolically and in the context of everyday language and are able to translate between them. The successful Discrete Mathematics student can: 1.1. Propositional Logic: 1.1a. Translate English sentences into propositional logic notation and vice-versa. -

Form and Content: an Introduction to Formal Logic
Connecticut College Digital Commons @ Connecticut College Open Educational Resources 2020 Form and Content: An Introduction to Formal Logic Derek D. Turner Connecticut College, [email protected] Follow this and additional works at: https://digitalcommons.conncoll.edu/oer Recommended Citation Turner, Derek D., "Form and Content: An Introduction to Formal Logic" (2020). Open Educational Resources. 1. https://digitalcommons.conncoll.edu/oer/1 This Book is brought to you for free and open access by Digital Commons @ Connecticut College. It has been accepted for inclusion in Open Educational Resources by an authorized administrator of Digital Commons @ Connecticut College. For more information, please contact [email protected]. The views expressed in this paper are solely those of the author. Form & Content Form and Content An Introduction to Formal Logic Derek Turner Connecticut College 2020 Susanne K. Langer. This bust is in Shain Library at Connecticut College, New London, CT. Photo by the author. 1 Form & Content ©2020 Derek D. Turner This work is published in 2020 under a Creative Commons Attribution- NonCommercial-NoDerivatives 4.0 International License. You may share this text in any format or medium. You may not use it for commercial purposes. If you share it, you must give appropriate credit. If you remix, transform, add to, or modify the text in any way, you may not then redistribute the modified text. 2 Form & Content A Note to Students For many years, I had relied on one of the standard popular logic textbooks for my introductory formal logic course at Connecticut College. It is a perfectly good book, used in countless logic classes across the country. -

Section 6.2 Propositional Calculus Propositional Calculus Is the Language of Propositions (Statements That Are True Or False)
Section 6.2 Propositional Calculus Propositional calculus is the language of propositions (statements that are true or false). We represent propositions by formulas called well-formed formulas (wffs) that are constructed from an alphabet consisting of Truth symbols: T (or True) and F (or False) Propositional variables: uppercase letters. Connectives (operators): ¬ (not, negation) ∧ (and, conjunction) ∨ (or, disjunction) → (conditional, implication) Parentheses symbols: ( and ). A wff is either a truth symbol, a propositional variable, or if V and W are wffs, then so are ¬ V, V ∧ W, V ∨ W, V → W, and (W). Example. The expression A ¬ B is not a wff. But each of the following three expressions is a wff: A ∧ B → C, (A ∧ B) → C, and A ∧ (B → C). Truth Tables. The connectives are defined by the following truth tables. P Q ¬P P "Q P #Q P $ Q T T F T T T T F F F T F F T T F T T F F T F F T 1 ! Semantics The meaning of T (or True) is true and the meaning of F (or False) is false. The meaning of any other wff is its truth table, where in the absence of parentheses, we define the hierarchy of evaluation to be ¬, ∧, ∨, →, and we assume ∧, ∨, → are left associative. Examples. ¬ A ∧ B means (¬ A) ∧ B A ∨ B ∧ C means A ∨ (B ∧ C) A ∧ B → C means (A ∧ B) → C A → B → C means (A → B) → C. Three Classes A Tautology is a wff for which all truth table values are T. A Contradiction is a wff for which all truth table values are F. -

On Truth-Functionality
ZU064-05-FPR truth˙funct˙full˙abs˙final 1 September 2009 11:47 Under consideration for publication in Review of Symbolic Logic 1 ON TRUTH-FUNCTIONALITY DANIEL J. HILL & STEPHEN K. McLEOD University of Liverpool (e-mail: [email protected]; [email protected]) Abstract Benjamin Schnieder has argued that several traditional definitions of truth-functionality fail to cap- ture a central intuition informal characterizations of the notion often capture. The intuition is that the truth-value of a sentence that employs a truth-functional operator depends upon the truth-values of the sentences upon which the operator operates. Schnieder proposes an alternative definition of truth-functionality that is designed to accommodate this intuition. We argue that one traditional definition of ‘truth-functionality’ is immune from the counter-examples that Schnieder proposes and is preferable to Schnieder’s alternative. 1 Schnieder on ‘standard’ accounts of truth-functionality. Quine (1982: 8), quoted by Schnieder (2008: 64), characterizes truth-functionality as fol- lows: ‘a way of forming compound statements from component statements is truth-functional if the compounds thus formed always have matching truth-value as long as their compo- nents have matching truth-value’. Schnieder (2008: 65) writes that on ‘Quine’s characterisation . an operator z [is] truth- functional iff . the truth-value of a complex sentence formed by combining z with the appropriate number of sentences is the value of a function of the truth-values of those sentences’. According to Schnieder (2008: 65), the trouble with this ‘simple proposal’, is that it makes ‘the truth-functionality of some operators dependent upon arbitrary contingent facts’. -

1.2 Truth and Sentential Logic
Chapter 1 I Mathematical Logic 13 69. Assume that B has m left parentheses and m right parentheses and that C has n left parentheses and n right parentheses. How many left parentheses appear in ( B ∧ C)? How many right parentheses appear in ( B ∧ C)? 70. Following the model given in exercise 69, argue that ( B ∨ C), ( B → C), (B ↔ C) each have the same number of left and right parentheses. Conclude from exercises 67–70 that any sentence has the same number of left and right parentheses. 1.2 Truth and Sentential Logic Mathematicians seek to discover and to understand mathematical truth. The five logical connectives of sentential logic play an important role in determining whether a mathematical statement is true or false. Specifically, the truth value of a compound sentence is determined by the interaction of the truth value of its component sentences and the logical connectives linking these components. In this section, we learn a truth table algorithm for computing all possible truth values of any sentence from sentential logic. In mathematics we generally assume that every sentence has one of two truth values: true or false . As we discuss in later chapters, the reality of mathematics is far less clear; some sentences are true, some are false, some are neither, while some are unknown. Many questions can be considered in one of the various interesting and reasonable multi-valued logics. For example, philosophers and physicists have successfully utilized multi-valued logics with truth values “true,” “false,” and “unknown” to model and analyze diverse real-world questions. -

Wittgenstein's Theory of Elementary Propositions
The theory of elementary propositions phil 43904 Jeff Speaks November 8, 2007 1 Elementary propositions . 1 1.1 Elementary propositions and states of affairs (4.2-4.28) . 1 1.2 Truth possibilities of elementary propositions (4.3-4.45) . 2 2 Tautologies and contradictions (4.46-4.4661) . 3 3 The general form of the proposition . 4 3.1 Elementary propositions and other propositions (4.5-5.02) . 4 3.2 Elementary propositions and the foundations of probability (5.1-5.156) . 4 3.3 Internal relations between propositions are the result of truth-functions (5.2-5.32) . 5 3.4 Logical constants (5.4-5.476) . 5 3.5 Joint negation (5.5-5.5151) . 5 3.6 [¯p; ξ;¯ N(ξ¯)] (6-6.031) . 6 1 Elementary propositions The heart of the Tractatus is Wittgenstein's theory of propositions; and the heart of his theory of propositions is his theory of elementary propositions. Beginning in x4.2, Wittgenstein turns to this topic. 1.1 Elementary propositions and states of affairs (4.2-4.28) Given Wittgenstein's repeated reliance on the existence of a correspondence between language and the world, it should be no surprise that his philosophy of language { i.e., his theory of propositions and their constituents { mirrors his metaphysics { i.e., his theory of facts and their constituents. Just as the facts are all determined in some sense by a class of basic facts { states of affairs { so propositions are all, in a sense to be explained, determined by a class of basic propositions { the elementary propositions. -

Truth Functional Connectives
TRUTH FUNCTIONAL CONNECTIVES 1. Introduction.....................................................................................................28 2. Statement Connectives....................................................................................28 3. Truth-Functional Statement Connectives........................................................31 4. Conjunction.....................................................................................................33 5. Disjunction......................................................................................................35 6. A Statement Connective that is not Truth-Functional.....................................37 7. Negation..........................................................................................................38 8. The Conditional...............................................................................................39 9. The Non-Truth-Functional Version of If-Then...............................................40 10. The Truth-Functional Version of If-Then.......................................................41 11. The Biconditional............................................................................................43 12. Complex Formulas..........................................................................................44 13. Truth Tables for Complex Formulas...............................................................46 14. Exercises for Chapter 2...................................................................................54 -

Notes on the Science of Logic 2009
NOTES ON THE SCIENCE OF LOGIC Nuel Belnap University of Pittsburgh 2009 Copyright c 2009 by Nuel Belnap February 25, 2009 Draft for use by friends Permission is hereby granted until the end of December, 2009 to make single copies of this document as desired, and to make multiple copies for use by teach- ers or students in any course offered by any school. Individual parts of this document may also be copied subject to the same con- straints, provided the title page and this page are included. Contents List of exercises vii 1 Preliminaries 1 1A Introduction . 1 1A.1 Aim of the course . 1 1A.2 Absolute prerequisites and essential background . 3 1A.3 About exercises . 4 1A.4 Some conventions . 5 2 The logic of truth functional connectives 9 2A Truth values and functions . 10 2A.1 Truth values . 11 2A.2 Truth functions . 13 2A.3 Truth functionality of connectives . 16 2B Grammar of truth functional logic . 19 2B.1 Grammatical choices for truth functional logic . 19 2B.2 Basic grammar of TF . 21 2B.3 Set theory: finite and infinite . 24 2B.4 More basic grammar . 31 2B.5 More grammar: subformulas . 36 iii iv Contents 2C Yet more grammar: substitution . 38 2C.1 Arithmetic: N and N+ ................... 39 2C.2 More grammar—countable sentences . 43 2D Elementary semantics of TF . 45 2D.1 Valuations and interpretations for TF . 46 2D.2 Truth and models for TF . 51 2D.3 Two two-interpretation theorems and one one-interpretation theorem . 54 2D.4 Quantifying over TF-interpretations . -

4 Truth-Functional Logic
Hardegree, Metalogic, Truth-Functional Logic page 1 of 13 4 Truth-Functional Logic 1. Introduction ..........................................................................................................................2 2. The Language of Classical Sentential Logic.........................................................................2 3. Truth-Values.........................................................................................................................3 4. Truth-Functions ....................................................................................................................5 5. Truth-Functional Semantics for CSL ....................................................................................6 6. Expressive Completeness.....................................................................................................9 7. Exercises............................................................................................................................12 8. Answers to Selected Exercises ..........................................................................................13 Hardegree, Metalogic, Truth-Functional Logic page 2 of 13 1. Introduction In presenting a logic, the customary procedure involves four steps. (1) specify the syntax of the underlying formal language, o, over which the logic is defined; (2) specify the semantics for o, in virtue of which semantic entailment is defined; (3) specify a deductive system for o, in virtue of which deductive entailment is defined; (4) show that semantic