Hardening the Browser Protecting Patron Privacy on the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

Google Docs Accessibility (Pdf)
Google Docs Accessibility (A11y) Building Accessible Google Docs • Heading Styles • Images • Table of Contents • Captioning • Columns and Lists • Tables A11y • Tab Stops • Color Contrast • Paragraph Spacing • Headers and Footers • Meaningful Link Text • Accessibility Checker What is Assistive Technology? Assistive Technology (AT) are “products, equipment, and systems that enhance learning, working, and daily living for persons with disabilities.” Magnification Speech Screen Readers Software Recognition Trackball Mouse Keyboard Zoom Text Braille Computer Keyboard Captions/Subtitles Captioned Telephone Video Relay Services Captioning Videos Per federal and state law, and CSU policy, instructional media (e.g., videos, captured lectures, recorded presentations) must have captions. This includes instructional media used in classrooms, posted on websites or shared in Canvas. • All students who are enrolled in a course must be able to access the content in the course. • Faculty: Funding is available to help faculty generate captions and transcripts for instructional media. Materials should be submitted at least six weeks in advance of their use in instruction. • Staff: For CSUN staff who do not provide classroom material, there is a cost through chargeback. For information on the chargeback, email [email protected]. csun.edu/captioning What are Screen Readers Screen readers are a form of assistive technology (AT) software that enables access to a computer, and all the things a computer does, by attempting to identify and interpret what is being displayed on the computer screen using text-to-speech. Screen readers can only access and process live text (fully editable or selectable text). • Provides access to someone who is visually impaired, mobility or has a learning disability to access text on the screen. -
Quick Start Guide: Migrating to Always-On
QUICK START GUIDE: MIGRATING TO ALWAYS-ON SSL Now that Google has added a rank boost for Always-On SSL (AOSSL), it makes sense to enable HTTPS across your entire Website. But where do you start? DigiCert created this guide to give you an in-depth look on how AOSSL can help you and to get you started with implementing AOSSL on your own Website. GET YOUR COMPANY ON TOP WITH AOSSL We know you’re always looking for new ways to users immediately recognize them to mean security. make your company stick out—whether that’s in By ranking higher in Google, you will be driving search engine rankings or in your customer’s minds. more traffic; and with the added security benefits of And with Google’s recent announcement that HTTPS SSL your new users will feel confident on your site, everywhere is a factor in their ranking algorithm, SSL positively affecting conversion rates. can be part of your solution. HOW AOSSL BENEFITS YOU Unlike many of the ranking factors in Google’s search The HTTPS everywhere ranking signal is standalone algorithm that are vague or difficult to measure, and is independent from any of Google’s other ranking having HTTPS everywhere is a guaranteed way to get signals or algorithms. As soon as a new HTTPS page your site ranked above your competitors. And though is indexed by Google, you get a boost in your search it’s starting out as a lightweight signal, Google has ranking just because of the HTTPS URL. While this promised that the weight of SSL as a ranking factor doesn’t mean that your page will automatically jump will increase once webmasters have time to migrate up a few ranks in search results, it does mean that you their sites. -

Designing Secure Systems That People Can
15- SSL, PKIs, and Secure Communication Engineering & Public Policy Lorrie Cranor, Blase Ur, and Rich Shay March 3, 2015 05-436 / 05-836 / 08-534 / 08-734 Usable Privacy and Security 1 Today! • An introduction to SSL/TLS • An introduction to PKIs • Recent developments in this area • Usability issues • An activity to make it better 2 Overview • Secure Sockets Layer (SSL) and its successor, Transport Layer Security (TLS) enable secure communication • Frequently encountered with web browsing (HTTPS) and more behind the scenes in app, VOIP, etc. 3 What we want to defend against • People snooping on our communications – The contents of what we’re sending – Session tokens (see, e.g., Firesheep) • Man-in-the-middle attacks – We want to authenticate that we are talking to the right site, not an imposter – Use certificates inside a public-key infrastructure 4 How we could obtain trust • Web of trust – People you already trust introduce you to people they trust – Can get complicated, doesn’t scale well – Less frequently seen in practice • Public-Key Infrastructure (PKI) – Certificates are issued by certificate authorities that bind cryptographic keys to identities 5 Public-Key Infrastucture • Binding of keys to identities can be done automatically or by humans 6 What does SSL look like to users? • Compare, e.g., the following: – https://www.google.com (normal certificate) – Go to Google images and then click on an image and see what happens (mixed content) – https://otalliance.org (EV certificate) 7 What does PKI look like to browsers? • Hundreds -

Technical Intelligence ISSUE: 19.04.21
Technical Intelligence ISSUE: 19.04.21 The CyberScotland Technical Threat Intelligence Bulletin is designed to provide you with information about updates, exploits and countermeasures. We hope that you benefit from this resource and we ask that you circulate this information to your networks, adapting where you see fit. Jump To TECHNICAL THREAT AWARENESS AND HUNTING Microsoft Patch Tuesday (April 2021) Adobe Patches Slew of Critical Security Bugs Patch Chrome to Remediated In-The-Wild 0-Day Exploits F5 urges customers to patch critical BIG-IP pre-auth RCE bug Wordpress Privilege-Escalation and Authentication Bypass Apple rushes to patch zero‑day flaw in iOS, iPadOS Cisco Will Not Patch Critical RCE Flaw Affecting End-of-Life Business Routers Threat Intelligence Bulletin Technical Threat Awareness and Hunting Microsoft Patch Tuesday (April 2021) Microsoft released its monthly security update Tuesday 13th April 2021, disclosing 114 vulnerabilities across its suite of products1. Four new remote code execution vulnerabilities in Microsoft Exchange Server are included, beyond those that were release out-of-band last month. The detection of the vulnerabilities which led to these patches has been attributed to the US’s National Security Agency (NSA)2. Given the recent focus on Microsoft Exchange by varying threat actors, NCSC has produced an alert encouraging organisations to install the critical updates immediately3. More patches are likely to follow for Microsoft’s Exchange servers as, at a recent hacking contest called pwn2own a team called DEVCORE combined an authentication bypass and a local privilege escalation to complete take over the Exchange server. As a result they won $200,000.4 In all, there are 20 critical vulnerabilities as part of this release and one considered of “moderate” severity. -
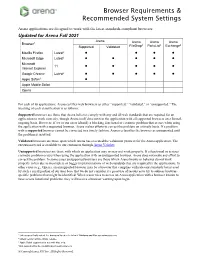
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

Using Replicated Execution for a More Secure and Reliable Web Browser
Using Replicated Execution for a More Secure and Reliable Web Browser Hui Xue Nathan Dautenhahn Samuel T. King University of Illinois at Urbana Champaign huixue2, dautenh1, kingst @uiuc.edu { } Abstract Unfortunately, hackers actively exploit these vulnerabil- ities as indicated in reports from the University of Wash- Modern web browsers are complex. They provide a ington [46], Microsoft [61], and Google [49, 48]. high-performance and rich computational environment Both industry and academia have improved the se- for web-based applications, but they are prone to nu- curity and reliability of web browsers. Current com- merous types of security vulnerabilities that attackers modity browsers make large strides towards improving actively exploit. However, because major browser plat- the security and reliability of plugins by using sandbox- forms differ in their implementations they rarely exhibit ing techniques to isolate plugins from the rest of the the same vulnerabilities. browser [62, 33]. However, these browsers still scatter In this paper we present Cocktail, a system that uses security logic throughout millions of lines of code, leav- three different off-the-shelf web browsers in parallel to ing these systems susceptible to browser-based attacks. provide replicated execution for withstanding browser- Current research efforts, like Tahoma [32], the OP web based attacks and improving browser reliability. Cock- browser [36], the Gazelle web browser [59], and the Illi- tail mirrors inputs to each replica and votes on browser nois Browser Operating System [58] all propose build- states and outputs to detect potential attacks, while con- ing new web browsers to improve security. Although tinuing to run. -

Private Browsing
Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, and Lorrie Faith Cranor, Carnegie Mellon University https://www.usenix.org/conference/soups2018/presentation/habib-prying This paper is included in the Proceedings of the Fourteenth Symposium on Usable Privacy and Security. August 12–14, 2018 • Baltimore, MD, USA ISBN 978-1-939133-10-6 Open access to the Proceedings of the Fourteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, Lorrie Faith Cranor Carnegie Mellon University {htq, jcolnago, vidyag, spearman, thomasjm, acquisti, nicolasc, lorrie}@andrew.cmu.edu ABSTRACT Prior user studies have examined different aspects of private Previous research has suggested that people use the private browsing, including contexts for using private browsing [4, browsing mode of their web browsers to conduct privacy- 10, 16, 28, 41], general misconceptions of how private brows- sensitive activities online, but have misconceptions about ing technically functions and the protections it offers [10,16], how it works and are likely to overestimate the protections and usability issues with private browsing interfaces [41,44]. it provides. To better understand how private browsing is A major limitation of much prior work is that it is based used and whether users are at risk, we analyzed browsing on self-reported survey data, which may not always be reli- data collected from over 450 participants of the Security able. -

Profiles Research Networking Software Installation Guide
Profiles Research Networking Software Installation Guide Documentation Version : July 25, 2014 Software Version : ProfilesRNS_2.1.0 Table of Contents Introduction ..................................................................................................................... 2 Hardware and Operating System Requirements ............................................................. 3 Download Options ........................................................................................................... 4 Installing the Database .................................................................................................... 5 Loading Person Data....................................................................................................... 8 Loading Person Data: Part 1 – Importing SSIS Packages into SQL Server msdb Database ..................................................................................................................... 8 Loading Person Data: Part 2 – Importing Demographic Data .................................... 10 Loading Person Data: Part 3 – Geocoding ................................................................ 15 Loading Person Data: Part 4 – Obtaining Publications .............................................. 16 Loading Person Data: Part 5 – Convert data to RDF ................................................. 19 Scheduling Database Jobs ............................................................................................ 21 Installing the Code........................................................................................................ -

HTTP Cookie - Wikipedia, the Free Encyclopedia 14/05/2014
HTTP cookie - Wikipedia, the free encyclopedia 14/05/2014 Create account Log in Article Talk Read Edit View history Search HTTP cookie From Wikipedia, the free encyclopedia Navigation A cookie, also known as an HTTP cookie, web cookie, or browser HTTP Main page cookie, is a small piece of data sent from a website and stored in a Persistence · Compression · HTTPS · Contents user's web browser while the user is browsing that website. Every time Request methods Featured content the user loads the website, the browser sends the cookie back to the OPTIONS · GET · HEAD · POST · PUT · Current events server to notify the website of the user's previous activity.[1] Cookies DELETE · TRACE · CONNECT · PATCH · Random article Donate to Wikipedia were designed to be a reliable mechanism for websites to remember Header fields Wikimedia Shop stateful information (such as items in a shopping cart) or to record the Cookie · ETag · Location · HTTP referer · DNT user's browsing activity (including clicking particular buttons, logging in, · X-Forwarded-For · Interaction or recording which pages were visited by the user as far back as months Status codes or years ago). 301 Moved Permanently · 302 Found · Help 303 See Other · 403 Forbidden · About Wikipedia Although cookies cannot carry viruses, and cannot install malware on 404 Not Found · [2] Community portal the host computer, tracking cookies and especially third-party v · t · e · Recent changes tracking cookies are commonly used as ways to compile long-term Contact page records of individuals' browsing histories—a potential privacy concern that prompted European[3] and U.S. -

The Tor Browser
TOR By: Qui Hao (Frank) Yu and Haseeb Choudhary Agenda What is Tor? The Tor Browser What does Tor provide its users? Tor with command line apps The history of Tor Tor vs. VPN What makes up the Tor network? What NOT to do with Tor How does Tor work? - Clients perspective - Onion service perspective What is Tor? Tor stands for The Onion Router It is a open source network run by volunteers which provides its users with enhanced privacy and security on the Internet. Guard Middle Exit Node Server Node What does Tor Provide its Users? ● Who are the users of Tor? Anyone who would like to enhance their privacy and security on the Internet ● What does Tor do to provide more privacy and security for its users? ● Tor prevents websites and other services from knowing your location ● Tor prevents someone monitoring your Internet traffic (e.g. ISP, someone on your home network) from learning where you’re going and what you’re receiving from where you go ● Tor routes your traffic through more than one Tor relay so that no single relay will know both who you are and where you’re going The History of Tor ● Principle of “Onion Routing” ○ Developed by Paul Syverson, Michael G. Reed and David Goldschlag at the United States Naval Research Laboratory. ○ Developed in mid-1990’s ○ Purpose: protecting U.S. intelligence communication Online ● Alpha version of Tor - The Onion Routing Project ○ Developed by Roger Dingledine, Paul Syverson, and Nick Mathewson ○ Launched on Sept 20th, 2002 ○ Releases a year later ● The Tor Project, Inc, founded in Dec, 2006 What