Mobile OS - Features, Concepts and Challenges for Enterprise Environments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

How Ios 7 Stacks Up:Smartphone OS User Experience Shootout
How iOS 7 Stacks Up: Smartphone OS User Experience Shootout a Pfeiffer Report Benchmark Project www.pfeifferreport.com @pfeifferreport Introduction Why is it that the arrival of iOS 7 Whether we like it or not, We do not look at features, we do not smartphones have become a compare cutting-edge options and is necessarily a momentous software game. Take any recent gadgets, we only look at aspects event for the smartphone top-of-the-line smartphone, and you that have a direct impact on the are likely to get a well-designed, fast, day-to-day user experience of an market? Simple: Unlike any other pleasant to use bit of hardware: fluid average, non-technical user. operating system out there, it will operation, responsive interaction, fast The aspects we have surveyed and be in the hands of millions or tens graphics. The difference of user rated are the following: experience, therefore, stems of millions of users within a few cognitive load, efficiency, almost exclusively from the customization, as well as user days after its launch. operating system, the user interface experience friction. Based on And that will make it a force to be design, the application integration, the the results from these benchmarks overall coherence. we have then established an overall reckoned with. This report compares the five Mobile Operating System User major mobile operating systems Experience Index presented at the * The question is, of course: in use today: iOS 7, iOS 6, Android , end of this document. Windows Phone 8, and Blackberry 10, The benchmarks are based on the How good is it really? and rates them in terms of user Pfeiffer Consulting Methodology experience. -

A Survey Onmobile Operating System and Mobile Networks
A SURVEY ONMOBILE OPERATING SYSTEM AND MOBILE NETWORKS Vignesh Kumar K1, Nagarajan R2 (1Departmen of Computer Science, PhD Research Scholar, Sri Ramakrishna College of Arts And Science, India) (2Department of Computer Science, Assistant Professor, Sri Ramakrishna College Of Arts And Science, India) ABSTRACT The use of smartphones is growing at an unprecedented rate and is projected to soon passlaptops as consumers’ mobile platform of choice. The proliferation of these devices hascreated new opportunities for mobile researchers; however, when faced with hundreds ofdevices across nearly a dozen development platforms, selecting the ideal platform is often met with unanswered questions. This paper considers desirable characteristics of mobileplatforms necessary for mobile networks research. Key words:smart phones,platforms, mobile networks,mobileplatforms. I.INTRODUCTION In a mobile network, position of MNs has been changing due todynamic nature. The dynamic movements of MNs are tracked regularlyby MM. To meet the QoS in mobile networks, the various issuesconsidered such as MM, handoff methods, call dropping, call blockingmethods, network throughput, routing overhead and PDR are discussed. In this paper I analyse the five most popular smartphone platforms: Android (Linux), BlackBerry, IPhone, Symbian, and Windows Mobile. Each has its own set of strengths and weaknesses; some platforms trade off security for openness, code portability for stability, and limit APIs for robustness. This analysis focuses on the APIs that platforms expose to applications; however in practice, smartphones are manufactured with different physical functionality. Therefore certain platform APIs may not be available on all smartphones. II.MOBILITY MANAGEMENT IP mobility management protocols proposed by Alnasouri et al (2007), Dell'Uomo and Scarrone (2002) and He and Cheng (2011) are compared in terms of handoff latency and packet loss during HM. -

Sailfish OS Interview Questions and Answers Guide
Sailfish OS Interview Questions And Answers Guide. Global Guideline. https://www.globalguideline.com/ Sailfish OS Interview Questions And Answers Global Guideline . COM Sailfish OS Job Interview Preparation Guide. Question # 1 Tell us what you know about Sailfish OS? Answer:- Sailfish is a Linux-based mobile operating system developed by Jolla in cooperation with the Mer project and supported by the Sailfish Alliance. It is to be used in upcoming smartphones by Jolla and other licencees. Although it is primarily targeted at mobile phones, it is also intended to support other categories of devices. Read More Answers. Question # 2 Explain Sailfish OS Components? Answer:- Jolla has revealed its plans to use the following technologies in Sailfish OS: The Mer software distribution core A custom built user interface HTML5 QML and Qt Read More Answers. Question # 3 Do you know about Sailfish OS software availability? Answer:- Sailfish will be able to run most applications that were originally developed for MeeGo and Android, in addition to native Sailfish applications. This will give it a large catalogue of available apps on launch. Considering upon Jolla's declarations that Sailfish OS is be able to use software from following platforms Sailfish (natively created + ported like from Qt, Symbian, MeeGo - developers have reported that porting a Qt written software with Sailfish SDK takes a few hours only) Android applications are directly running in Sailfish OS. They are compatible as they are in third-party Android stores, with no needed modification (in most cases). MeeGo (because of backward compatibility thanks to MeeGo code legacy included in the Mer core) Unix and Linux (as Sailfish is Linux then using such a software is possible, especially RPM packages, either in terminal/console mode or with limitations implying from using Sailfish UI, if not ported and adjusted) HTML5 Read More Answers. -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

Survey on Security Threats for Various Mobile Operating Systems
International Journal of Scientific Research and Review ISSN NO: 2279-543X SURVEY ON SECURITY THREATS FOR VARIOUS MOBILE OPERATING SYSTEMS D.Roseline Selvarani M.Sc., M.Phil1 A.Thamizh Priya2 I.Roseline Jecintha M.C.A., M.Phil.3 1Assistant Professor, PG&Research Department of Computer Science, Holy Cross College (Autonomous), Trichy. 2M.Phil Scholar Department of Computer Science, St-Joseph’s College of Arts & Science (Autonomous), Cuddalore. 3Assistant Professor, Department of Computer Application, St-Joseph’s College of Arts & Science (Autonomous), Cuddalore. ABSTRACT The main objective of the paper is to propose security policies and mechanisms for mobile phones that fulfil the user expectations ensure the data privacy for mobile users. The main reason of mobile phone growing ratio will be increased in recent years due to improved memory, processor and optimize the size of mobile devices. Nowadays smart phone usage will be increased because of the reason is optimized size, functionality enhancement, capable of host many useful and attractive applications. However, this vast amount of mobile platform usage makes these smart devices a soft target for security attacks and privacy breach. This paper examines the various types of mobile operating systems and its security threats. In this paper comparison of Smartphones like Android, Blackberry, Apple iOS, Symbian, Window Mobile, BADA, PALM OS (Garnet OS), Open WebOs, Maemo and Meego based on the specific evaluation criterions used for assessing the security level. Keywords Smartphone, Security, Malware, Attack, Operating System I.INTRODUCTION A working framework will be introduced for each PC. Customary working frameworks are WindowsOS, macOS, UNIX, and Linux. -

The State of Mobile Apps Created for the Appnation Conference with Insights from the Nielsen Company’S Mobile Apps Playbook by the Nielsen Company
The State Of Mobile Apps Created for the AppNation Conference with Insights from The Nielsen Company’s Mobile Apps Playbook by The Nielsen Company Introduction Most Americans can’t imagine leaving home without their mobile phones. Nearly all adults in the U.S. now have cellphones, with one in four having smartphones, pocket-sized devices more powerful than the computers initially used to send men to the moon. By the end of 2011, Nielsen predicts that the majority of mobile subscribers in the U.S. will have smartphones. With their rich features and capabilities, these devices have been fertile ground for the growth of mobile apps. As of June 2010, 59% of smartphone owners and nearly 9% of feature phone owners report having downloaded a mobile app in the last 30 days. To better understand the growing popularity of mobile apps—and help all players in the mobile ecosystem figure out how to profit from their growth—The Nielsen Company launched the Mobile Apps Playbook in December 2009. The most recent version of the study was released in September 2010 and was based on an August 2010 survey of more than 4,000 mobile subscribers who had reported downloading a mobile app in the previous 30 days. This white paper summarizes some of the findings of the Nielsen App Playbook study and was created for the first-ever AppNation Conference, held in San Francisco in September 2010. Most Popular Apps Games continue to be the most popular category of apps for used apps are popular among users of all operating systems, both feature phone and smartphone users alike. -

Bloomberg Anywhere for Blackberry Smartphones Os 4.6 –
BLOOMBERG ANYWHERE FOR BLACKBERRY SMARTPHONES OS 4.6 – 7.1 BLACKBERRY ENTERPRISE SERVER ADMINISTRATOR’S GUIDE V1.0.1 2 Table of Contents Scope .................................................................................................................................................... 4 Bloomberg Mobile Websites and Related Functions ............................................................................. 5 MOBI<Go> - Self-Overrides and Ending Mobile Sessions .................................................................... 9 Software Release Schedule ................................................................................................................. 11 Software Expiration Policy .................................................................................................................. 12 Upgrade Process ................................................................................................................................ 14 For Expired software ................................................................................................. 14 For software that is still active but old ........................................................................ 14 Software Availability ............................................................................................................................ 16 Bloomberg for Blackberry - Installation ............................................................................................... 17 Install Over-the-Air from the Web ............................................................................. -
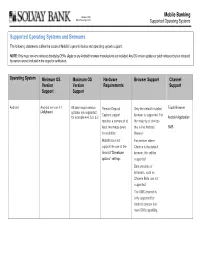
Mobile Banking Supported Operating Systems and Browsers
Member FDIC Mobile Banking Equal Housing Lender Supported Operating Systems Suppo rted Opera tin g Sys tems and Br owse rs The following statements outline the scope of Mobiliti’s general device and operating system support. NOTE: Only major versions released directly by OEMs (Apple or any Android hardware manufacturer) are included. Any OS version updates or patch releases that are released by carriers are not included in the scope for certification. Operating System Minimum OS Maximum OS Hardware Browser Support Channel Version Version Requirements Support Support Support Android Android version 4.1 All later major version Remote Deposit Only the default installed Touch Browser (Jellybean) updates are supported; Capture support browser is supported. For for example 4.4, 5.0, 6.0 Android Application requires a camera of at the majority of devices least two mega-pixels this is the Android SMS in resolution. Browser Mobiliti does not For devices where support the use of the Chrome is the default Android “Developer browser, this will be options” settings supported. Beta versions of browsers, such as Chrome Beta, are not supported. The SMS channel is only supported for Android devices that have SMS capability. Member FDIC Mobile Banking Equal Housing Lender Supported Operating Systems Operating Systems Minimum OS Maximum OS Hardware Browser Support Channel Version Version Requirements Support Support Support iOS- iPhone iOS version 7.0 All later major version None Only the default installed Touch updates are supported; browser is supported . For Browser for example 8.0, 8.1, 9 all iPhone devices this is Beta releases of iOS the Safari Browser iPhone Application will not be supported Beta versions of all until they are publicly browsers, such as SMS released Chrome Beta, are not supported. -

Comparison of Mobile Operating Systems
Not logged in Talk Contributions Create account Log in Article Talk Read Edit View history Search Comparison of mobile operating systems From Wikipedia, the free encyclopedia Main page This is a comparison of mobile operating systems (OS). Only the latest versions are shown in the table below, even though older versions may Contents still be marketed. Featured content Current events Contents [hide] Random article 1 About OS Donate to Wikipedia 2 Advanced controls Wikipedia store 3 Application ecosystem Interaction 4 Basic features Help 5 Browser About Wikipedia 6 Communication and connectivity Community portal 7 Language and inputs Recent changes 8 Maps and navigation Contact page 9 Media playback and controls Tools 10 Peripheral support What links here 11 Photo and video Related changes 12 Productivity Upload file 13 Ringtones and alerts Special pages 14 Security and privacy Permanent link Page information 15 Sound and voice Wikidata item 16 Other features Cite this page 17 See also 18 References Print/export Create a book Download as PDF Printable version About OS [ edit ] Languages Legend 中文 Edit links Yes In later versions Beta Limited Tablet-only 3rd party No open in browser PRO version Are you a developer? Try out the HTML to PDF API pdfcrowd.com About OS Ubuntu Feature iOS Android Firefox OS Windows Phone BlackBerry 10 Tizen Sailfish OS Touch Linux Sailfish Canonical Foundation, Alliance, Mer, Ltd. and Open Handset Mozilla Tizen Jolla and Company Apple Inc. Microsoft BlackBerry Ltd. Ubuntu Alliance Foundation Association, Sailfish -

Mobile OS and Security Aspects
…… Lecture 11 Market Overview of Mobile Operating Systems and Security Aspects Mobile Business I (WS 2015/16) Prof. Dr. Kai Rannenberg . Deutsche Telekom Chair of Mobile Business & Multilateral Security . Johann Wolfgang Goethe University Frankfurt a. M. Overview - Market Overview of Mobile Operating …… Systems and Security Aspects § The Market for mobile devices and mobile OS § Mobile OS unavailable to other device manufacturers § Overview § Palm OS § Apple iOS (Unix-based) § Manufacturer-independent mobile OS § Overview § Symbian platform (by Symbian Foundation) § Embedded Linux § Android (by Open Handset Alliance) § Microsoft Windows CE, Pocket PC, Pocket PC Phone Edition, Mobile § Microsoft Windows Phone 10 . § Firefox OS . § Security features of selected mobile OS . 2 Worldwide Smartphone Sales to End …… Users by Operating System (2009-2015) Market share Market . OS [Statista 2015a] 3 Worldwide Smartphone Sales to End …… Users by Operating System (Q2 2012) Android 64,2% Others 0,6% Symbian 5,9% Bada 2,7% BlackBerry OS 5,2% [Gartner2013] Windows 2,6% . iOS 18,8% . Android iOS Windows BlackBerry OS Bada Symbian Others 4 Worldwide Smartphone Sales to End …… Users by Operating System (Q2 2013) Android 79,0% Others 0,2% Symbian 0,3% Bada 0,4% BlackBerry OS 2,7% Windows 3,3% iOS 14,2% [Gartner2013] . Android iOS Windows BlackBerry OS Bada Symbian Others 5 Worldwide Smartphone Sales to End …… Users by Operating System (Q2 2014) Android 84,7% Others 0,6% BlackBerry OS 0,5% Windows 2,5% iOS 11,7% . Android iOS Windows BlackBerryBlackBerry OS Symbian Bada Others [Statista 2014a] 6 Worldwide Smartphone Sales to End …… Users by Operating System (Q2 2015) Android 82,8% Others 0,4% BlackBerry OS 0,3% Windows 2,6% iOS 13,9% . -

NIELIT Gorakhpur
NIELIT Gorakhpur Course Name: O Level (1st Sem) Subject: ITTNB Topic: operating systems for mobile Date: 01-04-20 phone and tablets [continued] BlackBerry OS (Research In Motion) The BlackBerry OS is a proprietary mobile operating system developed by Research In Motion for use on the company’s popular BlackBerry handheld devices. The BlackBerry platform is popular with corporate users as it offers synchronization with Microsoft Exchange, Lotus Domino, Novell GroupWise email and other business software, when used with the BlackBerry Enterprise Server. iPhone OS / iOS (Apple) Apple's iPhone OS was originally developed for use on its iPhone devices. Now, the mobile operating system is referred to as iOS and is supported on a number of Apple devices including the iPhone, iPad, iPad 2 and iPod Touch. The iOS mobile operating system is available only on Apple's own manufactured devices as the company does not license the OS for third-party hardware. Apple iOS is derived from Apple's Mac OS X operating system. Apple iOS includes the following features: Wi-Fi, Bluetooth and cellular connectivity, along with VPN support; Integrated search support, which enables simultaneous search through files, media, applications and email; Gesture recognition supports -- for example, shaking the device to undo the most recent action; Push email; Safari mobile browser; Integrated front- and rear-facing cameras with video capabilities; Direct access to the Apple App Store and the iTunes catalog of music, podcasts, television shows and movies available to rent or purchase; Compatibility with Apple's cloud service, iCloud; Siri personal assistant; Cross-platform communications between Apple devices through AirDrop; and Apple Pay, which stores users' credit card data and allows them to pay for goods and services directly with an iOS device. -

The Most Common Mobile Operating Systems Are: Android from Google Inc. (Open Source, Apache) Blackberry OS from RIM
The most common mobile operating systems are: Android from Google Inc. (open source, Apache) BlackBerry OS from RIM (closed source, proprietary) iOS from Apple Inc. (closed source, proprietary) Symbian OS from the Symbian Foundation (open public license) Windows Phone from Microsoft (closed source, proprietary) webOS from HP (certain parts open sourced) Android from Google Inc. (open source, Apache) Android was developed by a small startup company that was purchased by Google Inc. Released on November 5th 2007 Android is an open source, Linux-derived OS backed by Google, along with major hardware and software developers (such as Intel, HTC, ARM, Samsung, Motorola and eBay, to name a few) Android releases prior to 2.0 (1.0, 1.5, 1.6) were used exclusively on mobile phones. Android 3.0 was a tablet-oriented release and does not officially run on mobile phones. Android releases are nicknamed after sweets or dessert items like Cupcake (1.5), Frozen Yogurt (2.2), Honeycomb (3.0) and Ice Cream Sandwich (4.0). Most major mobile service providers carry an Android device. 1. What is Android? Android is a software platform and an operating system for mobile devices, The first device running Android is T-Mobile G1 officially released on October 22nd 2008. 2. I want to develop for Android. What are the basics I need to know? Android requires knowledge of Java programming language although it allows other programming languages (C C++for example) to be compiled in the native code. This however is not officially supported by Google. You can download SDK and get all the relevant info at http://code.google.com/android/index.html Make sure to checkout Android Developers forum for more tips at http://androidforums.com/a/ and/or share your experience with us.