Planning Guide for Cisco Jabber 12.8
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Open Yibo Wu Final.Pdf
The Pennsylvania State University The Graduate School RESOURCE-AWARE CROWDSOURCING IN WIRELESS NETWORKS A Dissertation in Computer Science and Engineering by Yibo Wu c 2018 Yibo Wu Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy May 2018 The dissertation of Yibo Wu was reviewed and approved∗ by the following: Guohong Cao Professor of Computer Science and Engineering Dissertation Adviser, Chair of Committee Robert Collins Associate Professor of Computer Science and Engineering Sencun Zhu Associate Professor of Computer Science and Engineering Associate Professor of Information Sciences and Technology Zhenhui Li Associate Professor of Information Sciences and Technology Bhuvan Urgaonkar Associate Professor of Computer Science and Engineering Graduate Program Chair of Computer Science and Engineering ∗Signatures are on file in the Graduate School. Abstract The ubiquity of mobile devices has opened up opportunities for a wide range of applications based on photo/video crowdsourcing, where the server collects a large number of photos/videos from the public to obtain desired information. How- ever, transmitting large numbers of photos/videos in a wireless environment with bandwidth constraints is challenging, and it is hard to run computation-intensive image processing techniques on mobile devices with limited energy and computa- tion power to identify the useful photos/videos and remove redundancy. To address these challenges, we propose a framework to quantify the quality of crowdsourced photos/videos based on the accessible geographical and geometrical information (called metadata) including the orientation, position, and all other related param- eters of the built-in camera. From metadata, we can infer where and how the photo/video is taken, and then only transmit the most useful photos/videos. -

Test Coverage Guide
TEST COVERAGE GUIDE Test Coverage Guide A Blueprint for Strategic Mobile & Web Testing SUMMER 2021 1 www.perfecto.io TEST COVERAGE GUIDE ‘WHAT SHOULD I BE TESTING RIGHT NOW?’ Our customers often come to Perfecto testing experts with a few crucial questions: What combination of devices, browsers, and operating systems should we be testing against right now? What updates should we be planning for in the future? This guide provides data to help you answer those questions. Because no single data source tells the full story, we’ve combined exclusive Perfecto data and global mobile market usage data to provide a benchmark of devices, web browsers, and user conditions to test on — so you can make strategic decisions about test coverage across mobile and web applications. CONTENTS 3 Putting Coverage Data Into Practice MOBILE RECOMMENDATIONS 6 Market Share by Country 8 Device Index by Country 18 Mobile Release Calendar WEB & OS RECOMMENDATIONS 20 Market Share by Country 21 Browser Index by Desktop OS 22 Web Release Calendar 23 About Perfecto 2 www.perfecto.io TEST COVERAGE GUIDE DATA INTO PRACTICE How can the coverage data be applied to real-world executions? Here are five considerations when assessing size, capacity, and the right platform coverage in a mobile test lab. Optimize Your Lab Configuration Balance Data & Analysis With Risk Combine data in this guide with your own Bundle in test data parameters (like number of tests, analysis and risk assessment to decide whether test duration, and required execution time). These to start testing with the Essential, Enhanced, or parameters provide the actual time a full- cycle or Extended mobile coverage buckets. -
Micromax Remotely Installing Unwanted Apps on Devices
11/16/2016 Micromax Remotely Installing Unwanted Apps on Devices search LOGIN REGISTER plus 0 53861 Your Entries Total Entries Days Win an Android Yoga Book from XDA! January 14, 2015 50 Comments Diamondback Micromax Remotely Installing Unwanted Apps on Devices 8 Ways to Enter Login with: In the recent past, we witnessed quite a few acts of OEMs messing with devices to achieve various goals, such as increasing benchmark results. We also heard about manufacturers and carriers adding Click For a Daily tracing software to their devices, in order to collect data about how the device performs, statistics Bonus Entry about voice and data connectivity between the device and radio towers, or even battery runtime data (CarrierIQ are you listening?). Today, however, reports are coming in that users of certain devices Follow by Indian phone manufacturer Micromax noticed apps being silently installed without their consent @xdadevelopers on or permission. Twitter It appears that even uninstalling these apps won’t help, as shortly after, they will simply re-appear Tweet on Twitter again. Obviously, this is wrong on so many levels, but I’d like to point out a few key problems here Subscribe to XDA TV! anyway: Visit our sponsor (Honor) at Best Buy http://www.xdadevelopers.com/micromaxremotelyinstallingunwantedappsondevices/ 1/14 11/16/2016 Micromax Remotely Installing Unwanted Apps on Devices (Honor) at Best Buy Having no control over which apps are installed on your device poses a huge security risk, as you don’t get to -

Xiaomi Mi Pad Рождение Самурая
Gadgets Guide Гид по гаджетам Выпуск №21 Nokia Lumia 630 и 930 Последний привет Xiaomi Mi Pad Рождение самурая Lenovo S850 Samsung NX mini Сделано со вкусом В центре взгляда Авторский коллектив: Виктор Лавров, Владимир Маркин, Валентина Щербак. Gadgets Guide №21 Речь по поводу От редакции О лете и немного о гаджетах Сегодня совсем немного, потому как лето для гаджетов – мертвый сезон. Все флагманы уже вышли и успели получить свою порцию критики. До сентябрьских премьер и долгожданного увеличения размеров iPhone еще долго. Сейчас придется довольствоваться китайскими вкраплениями и всяческими mini флагманов, которые уже на подходе. В общем, скучно все. Да и головы даже самых отчаянных гаджетоманов заняты сейчас совершенно другим. Лето… Отпуск… Мечты уже рисуют знойный пляж с естественным оазисом в виде пальм и море. Море и снова море. Желательно, конечно, Средиземное, но на крайний случай подойдет и Черное. Солнечная нега, безделье, путешествия, активный отдых. Собственно, зависит все от потребностей и фантазий. Ну и, конечно, от возможностей. Однако, не все лето – отпуск, и об этом не стоит забывать. Здорово , если вы можете позволить себе уволиться и уехать на все лето на Гоа или на Мальдивы, зная, что приедете и сразу найдете работу. Но для большинства из нас отпуск летом – это всего лишь две недели. Этого невыносимо мало, но понимаешь это, только вернувшись в унылые, даже если они всех цветов радуги, стены офиса. Офис – это неизбежное наказание любого расслабившегося отпускника. Но не будем о грустном. И главное. В дневном пляжном блаженстве, в пьяных вечеринках, в спусках по горно-речным порогам, в посиделках возле костра между палатками, в дебрях южной Азии и в благополучной Европе помните о своих любимых гаджетах. -

A Critical Review on Huawei's Trusted Execution Environment
Unearthing the TrustedCore: A Critical Review on Huawei’s Trusted Execution Environment Marcel Busch, Johannes Westphal, and Tilo Müller Friedrich-Alexander-University Erlangen-Nürnberg, Germany {marcel.busch, johannes.westphal, tilo.mueller}@fau.de Abstract to error. In theory, any bug in the feature-rich domain, includ- ing severe kernel-level bugs, cannot affect the integrity and Trusted Execution Environments (TEEs) are an essential confidentiality of a TEE, as TEEs are isolated from the rest building block in the security architecture of modern mo- of the system by means of hardware primitives. As ARM is bile devices. In this paper, we review a TEE implementa- the predominant architecture used for chipsets in mobile de- tion, called TrustedCore (TC), that has been used on Huawei vices, the ARM TrustZone (TZ)[6] provides the trust anchor phones for several years. We unveil multiple severe design for virtually all TEEs in mobile devices, including Huawei and implementation flaws in the software stack of this TEE, models. which affect devices including the popular Huawei P9 Lite, Although TEEs have been extensively used by millions released in 2016, and partially the more recent Huawei P20 of products for years, security analyses targeting these sys- Lite, released in 2018. First, we reverse-engineer TC’s com- tems are rarely discussed in public since all major vendors, ponents, their interconnections, and their integration with the including Huawei, Qualcomm, and Samsung, maintain strict Android system, focusing on security aspects. Second, we ex- secrecy about their individual proprietary implementations. amine the Trusted Application (TA) loader of the TC platform However, the correct implementation of a TEE is complex and reveal multiple design flaws. -
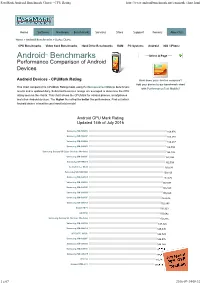
Passmark Android Benchmark Charts - CPU Rating
PassMark Android Benchmark Charts - CPU Rating http://www.androidbenchmark.net/cpumark_chart.html Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device Charts CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone Android TM Benchmarks ----Select A Page ---- Performance Comparison of Android Devices Android Devices - CPUMark Rating How does your device compare? Add your device to our benchmark chart This chart compares the CPUMark Rating made using PerformanceTest Mobile benchmark with PerformanceTest Mobile ! results and is updated daily. Submitted baselines ratings are averaged to determine the CPU rating seen on the charts. This chart shows the CPUMark for various phones, smartphones and other Android devices. The higher the rating the better the performance. Find out which Android device is best for your hand held needs! Android CPU Mark Rating Updated 14th of July 2016 Samsung SM-N920V 166,976 Samsung SM-N920P 166,588 Samsung SM-G890A 166,237 Samsung SM-G928V 164,894 Samsung Galaxy S6 Edge (Various Models) 164,146 Samsung SM-G930F 162,994 Samsung SM-N920T 162,504 Lemobile Le X620 159,530 Samsung SM-N920W8 159,160 Samsung SM-G930T 157,472 Samsung SM-G930V 157,097 Samsung SM-G935P 156,823 Samsung SM-G930A 155,820 Samsung SM-G935F 153,636 Samsung SM-G935T 152,845 Xiaomi MI 5 150,923 LG H850 150,642 Samsung Galaxy S6 (Various Models) 150,316 Samsung SM-G935A 147,826 Samsung SM-G891A 145,095 HTC HTC_M10h 144,729 Samsung SM-G928F 144,576 Samsung -

Terraillon Wellness Coach Supported Devices
Terraillon Wellness Coach Supported Devices Warning This document lists the smartphones compatible with the download of the Wellness Coach app from the App Store (Apple) and Play Store (Android). Some models have been tested by Terraillon to check the compatibility and smooth operation of the Wellness Coach app. However, many models have not been tested. Therefore, Terraillon doesn't ensure the proper functioning of the Wellness Coach application on these models. If your smartphone model does not appear in the list, thank you to send an email to [email protected] giving us the model of your smartphone so that we can activate if the application store allows it. BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED ACER Liquid Z530 acer_T02 Android 4.3+ ACER Liquid Jade S acer_S56 Android 4.3+ ACER Liquid E700 acer_e39 Android 4.3+ ACER Liquid Z630 acer_t03 Android 4.3+ ACER Liquid Z320 T012 Android 4.3+ ARCHOS 45 Helium 4G a45he Android 4.3+ ARCHOS 50 Helium 4G a50he Android 4.3+ ARCHOS Archos 45b Helium ac45bhe Android 4.3+ ARCHOS ARCHOS 50c Helium ac50che Android 4.3+ APPLE iPhone 4S iOS8+ APPLE iPhone 5 iOS8+ APPLE iPhone 5C iOS8+ APPLE iPhone 5S iOS8+ APPLE iPhone 6 iOS8+ APPLE iPhone 6 Plus iOS8+ APPLE iPhone 6S iOS8+ APPLE iPhone 6S Plus iOS8+ APPLE iPad Mini 1 iOS8+ APPLE iPad Mini 2 iOS8+ 1 / 48 www.terraillon.com Terraillon Wellness Coach Supported Devices BRAND MODEL NAME MANUFACTURER MODEL NAME OS REQUIRED APPLE iPad Mini 3 iOS8+ APPLE iPad Mini 4 iOS8+ APPLE iPad 3 iOS8+ APPLE iPad 4 iOS8+ APPLE iPad Air iOS8+ -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

HR Kompatibilitätsübersicht
HR-imotion Kompatibilität/Compatibility 2018 / 11 Gerätetyp Telefon 22410001 23010201 22110001 23010001 23010101 22010401 22010501 22010301 22010201 22110101 22010701 22011101 22010101 22210101 22210001 23510101 23010501 23010601 23010701 23510320 22610001 23510420 Smartphone Acer Liquid Zest Plus Smartphone AEG Voxtel M250 Smartphone Alcatel 1X Smartphone Alcatel 3 Smartphone Alcatel 3C Smartphone Alcatel 3V Smartphone Alcatel 3X Smartphone Alcatel 5 Smartphone Alcatel 5v Smartphone Alcatel 7 Smartphone Alcatel A3 Smartphone Alcatel A3 XL Smartphone Alcatel A5 LED Smartphone Alcatel Idol 4S Smartphone Alcatel U5 Smartphone Allview P8 Pro Smartphone Allview Soul X5 Pro Smartphone Allview V3 Viper Smartphone Allview X3 Soul Smartphone Allview X5 Soul Smartphone Apple iPhone Smartphone Apple iPhone 3G / 3GS Smartphone Apple iPhone 4 / 4S Smartphone Apple iPhone 5 / 5S Smartphone Apple iPhone 5C Smartphone Apple iPhone 6 / 6S Smartphone Apple iPhone 6 Plus / 6S Plus Smartphone Apple iPhone 7 Smartphone Apple iPhone 7 Plus Smartphone Apple iPhone 8 Smartphone Apple iPhone 8 Plus Smartphone Apple iPhone SE Smartphone Apple iPhone X Smartphone Apple iPhone XR Smartphone Apple iPhone Xs Smartphone Apple iPhone Xs Max Smartphone Archos 50 Saphir Smartphone Archos Diamond 2 Plus Smartphone Archos Saphir 50x Smartphone Asus ROG Phone Smartphone Asus ZenFone 3 Smartphone Asus ZenFone 3 Deluxe Smartphone Asus ZenFone 3 Zoom Smartphone Asus Zenfone 5 Lite ZC600KL Smartphone Asus Zenfone 5 ZE620KL Smartphone Asus Zenfone 5z ZS620KL Smartphone Asus -

Android용 Cisco Jabber 12.8 릴리스 노트
Android용 Cisco Jabber 12.8 릴리스 노트 초판: 2020년 1월 22일 릴리스 12.8의 새로운 기능 Android 10 지원 Android 10에 대한 지원을 추가했습니다. Android 장치의 얼굴 인식 지원 이제 얼굴 인식 기능을 사용하여 적절한 Android 장치를 인증할 수 있습니다. 이전 릴리스에서는 사용자가 Android 장치에서 지문을 통해 인증할 수 있었습니다. LocalAuthenticationWithBiometrics 매개 변수를 사용하여 이 기능을 비활성화할 수 있습니다. 이 기능 에 대한 자세한 내용은 Cisco Jabber의 기능 구성에서 생체 인식 인증에 대한 섹션을 참조하십시오. 헌트 그룹 기능 향상 이제 모바일 클라이언트에서 헌트 그룹에 로그인하거나 로그아웃할 수 있습니다. 자세한 내용은 Cisco Jabber 기능 구성의 헌트 그룹 섹션을 참조하십시오. 음성 메일 기능 향상 데스크톱 클라이언트에서 모바일 클라이언트로 릴리스 12.7 음성 메일 기능 향상을 확장했습니다. 사용자는 통화를 하지 않고 음성 메일을 생성하여 하나 이상의 연락처에 음성 메일을 보낼 수 있습니 다. 음성 메일 서버 관리자는 사용자가 음성 메일을 전송할 수 있는 메일 그룹을 만들 수도 있습니다. 사용자는 음성 메일 서버의 카탈로그에서 수신자를 선택할 수 있습니다. 사용자는 음성 메일 또는 해당 메시지의 모든 수신자에게 직접 응답할 수 있습니다. 사용자는 음성 메일을 새 수신자에게 전달할 수도 있습니다. Android 장치에서 강제 업그레이드 관리자는 Google Play에서 ForceUpgradingOnMobile 매개 변수를 사용하여 최신 버전으로 업그레이드 를 시행할 수 있습니다. 팀 메시징 모드에 대한 사용자 정의 연락처 Jabber Team 메시징 모드 배포는 사용자 정의 연락처를 지원합니다. 이제 데스크톱 클라이언트에서 사용자 정의 연락처를 만들고 편집 및 삭제할 수 있습니다. 이 연락처는 모바일 클라이언트에서도 사 Android용 Cisco Jabber 12.8 릴리스 노트 1 요구 사항 용할 수 있습니다. 그러나 모바일 클라이언트에서 사용자 정의 연락처를 만들거나 편집 또는 삭제할 수는 없습니다. Webex 제어 허브를 통한 Jabber 분석 배포에 Webex 제어 허브가 구성되어 있는 경우 제어 허브를 통해 Jabber 분석에 액세스할 수 있습니 다. -
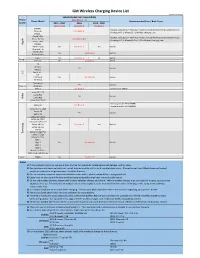
GM Wireless Charging Device List
GM Wireless Charging Device List Revision: Aug 30, 2019 Vehicle Model Year Compatibility Phone ( See Notes 1 - 7) Phone Model Recommended Case / Back Cover Brand 2015 - 2017 2018 2019 - 2020 (See Note 8) (See Note 8) (See Note 9) iPhone 6 ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case iPhone 6s See Note: A ŸAircharge MFi Qi iPhone 6S / 6 Wireless Charging Case iPhone 7 iPhone 6 Plus ŸBEZALEL Latitude [Qi + PMA] Dual-Mode Universal Wireless Charging Receiver Case e iPhone 6s Plus See Note: A & B l ŸAircharge MFi Qi iPhone 6S Plus / 6 Plus Wireless Charging Case p iPhone 7 Plus p A iPhone 8 iPhone X (10) No See Note: C Yes Built-in iPhone Xs / Xr iPhone 8 Plus No See Note: B Built-in iPhone Xs Max Pixel 3 No See Note: C Yes Built-in Google Pixel 3XL No See Note: B Built-in G6 Nexus 4 Yes Built-in Nexus 5 G Spectrum 2 L V30 V40 ThinQ No See Note: B Built-in G7 ThinQ Droid Maxx Yes Built-in Motorola Droid Mini Moto X See Note: A Incipio model: MT231 Lumia 830 / 930 a i Lumia 920 k Yes Built-in o Lumia 928 N Lumia 950 / 950 XL ŸSamsung model: EP-VG900BBU Galaxy S5 See Note: A ŸSamsung model: EP-CG900IBA Galaxy S6 / S6 Edge Galaxy S8 Yes Built-in Galaxy S9 Galaxy S10 / S10e Galaxy S6 Active Galaxy S7 / S7 Active g Galaxy S8 Plus No See Note: C Yes Built-in n u Galaxy S9 Plus s m S10 5G a Galaxy S6 Edge Plus S Galaxy S7 Edge Galaxy S10 Plus Note 5 Note 7 No See Note: B Built-in Note 8 Note 9 Note 10 / 10 Plus Note 10 5G / 10 Plus 5G Xiami MIX2S No See Note: B Built-in Notes: 1) If phone does not charge: remove it from charger for 3 seconds, rotate phone 180 degrees, and try again. -

Nexus-4 User Manual
NeXus-4 User Manual Version 2.0 0344 Table of contents 1 Service and support 3 1.1 About this manual 3 1.2 Warranty information 3 2 Safety information 4 2.1 Explanation of markings 4 2.2 Limitations of use 5 2.3 Safety measures and warnings 5 2.4 Precautionary measures 7 2.5 Disclosure of residual risk 7 2.6 Information for lay operators 7 3 Product overview 8 3.1 Product components 8 3.2 Intended use 8 3.3 NeXus-4 views 9 3.4 User interface 9 3.5 Patient connections 10 3.6 Device label 10 4 Instructions for use 11 4.1 Software 11 4.2 Powering the NeXus-4 12 4.3 Transfer data to PC 12 4.4 Perform measurement 13 4.5 Mobility 13 5 Operational principles 14 5.1 Bipolar input channels 14 5.2 Auxiliary input channel 14 5.3 Filtering 14 6 Maintenance 15 7 Electromagnetic guidance 16 8 Technical specifications 19 2 1 Service and support 1.1 About this manual This manual is intended for the user of the NeXus-4 system – referred to as ‘product’ throughout this manual. It contains general operating instructions, precautionary measures, maintenance instructions and information for use of the product. Read this manual carefully and familiarize yourself with the various controls and accessories before starting to use the product. This product is exclusively manufactured by Twente Medical Systems International B.V. for Mind Media B.V. Distribution and service is exclusively performed by or through Mind Media B.V.