Microsoft Surface
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

“MICROSOFT COMPLETE” Service Contract Terms & Conditions
“MICROSOFT COMPLETE” Service Contract Terms & Conditions Thank You for purchasing “Microsoft Complete”! Please keep this important terms and conditions Contract document and Proof of Purchase together in a safe place, as these will be needed at time of a Claim. The information contained in this Contract document is intended to serve as a valuable reference guide to help You determine and understand “WHAT IS COVERED” under Your Contract. BE SURE TO REGISTER YOUR SERVICE CONTRACT ONLINE! In order to maximize Your benefits, please go to https://devicesupport.microsoft.com/ and register Your Service Contract within 10 days of purchase. Failure to do so may result in significant service delays when You have a Claim. For any questions regarding the information contained in this Contract document, or Your Coverage in general, please call Us toll-free at the following, as applicable to Your purchased Plan: For “SURFACE PLAN” or “STUDIO PLAN”: 1-855-425-8900 For “XBOX PLAN”: 1-877-696-7786 You can also visit https://support.microsoft.com/en-us/devices for online web support. CONSUMER RIGHTS: FOR CONSUMERS IN TERRITORIES THAT HAVE THE BENEFIT OF CONSUMER PROTECTION LAWS OR REGULATIONS, THE BENEFITS CONFERRED BY THIS SERVICE CONTRACT ARE IN ADDITION TO ALL RIGHTS AND REMEDIES PROVIDED UNDER SUCH LAWS AND REGULATIONS. NOTHING IN THIS SERVICE CONTRACT SHALL PREJUDICE CONSUMER RIGHTS GRANTED BY APPLICABLE MANDATORY LAWS, INCLUDING CONSUMER’S RIGHT TO THE REMEDIES UNDER STATUTORY WARRANTY LAW AND TO SEEK DAMAGES IN THE EVENT OF TOTAL OR PARTIAL NON-PERFORMANCE OR INADEQUATE PERFORMANCE BY US OF ANY OF OUR CONTRACTUAL OBLIGATIONS. -

Copy on Write Based File Systems Performance Analysis and Implementation
Copy On Write Based File Systems Performance Analysis And Implementation Sakis Kasampalis Kongens Lyngby 2010 IMM-MSC-2010-63 Technical University of Denmark Department Of Informatics Building 321, DK-2800 Kongens Lyngby, Denmark Phone +45 45253351, Fax +45 45882673 [email protected] www.imm.dtu.dk Abstract In this work I am focusing on Copy On Write based file systems. Copy On Write is used on modern file systems for providing (1) metadata and data consistency using transactional semantics, (2) cheap and instant backups using snapshots and clones. This thesis is divided into two main parts. The first part focuses on the design and performance of Copy On Write based file systems. Recent efforts aiming at creating a Copy On Write based file system are ZFS, Btrfs, ext3cow, Hammer, and LLFS. My work focuses only on ZFS and Btrfs, since they support the most advanced features. The main goals of ZFS and Btrfs are to offer a scalable, fault tolerant, and easy to administrate file system. I evaluate the performance and scalability of ZFS and Btrfs. The evaluation includes studying their design and testing their performance and scalability against a set of recommended file system benchmarks. Most computers are already based on multi-core and multiple processor architec- tures. Because of that, the need for using concurrent programming models has increased. Transactions can be very helpful for supporting concurrent program- ming models, which ensure that system updates are consistent. Unfortunately, the majority of operating systems and file systems either do not support trans- actions at all, or they simply do not expose them to the users. -

Protocols: 0-9, A
Protocols: 0-9, A • 3COM-AMP3, on page 4 • 3COM-TSMUX, on page 5 • 3PC, on page 6 • 4CHAN, on page 7 • 58-CITY, on page 8 • 914C G, on page 9 • 9PFS, on page 10 • ABC-NEWS, on page 11 • ACAP, on page 12 • ACAS, on page 13 • ACCESSBUILDER, on page 14 • ACCESSNETWORK, on page 15 • ACCUWEATHER, on page 16 • ACP, on page 17 • ACR-NEMA, on page 18 • ACTIVE-DIRECTORY, on page 19 • ACTIVESYNC, on page 20 • ADCASH, on page 21 • ADDTHIS, on page 22 • ADOBE-CONNECT, on page 23 • ADWEEK, on page 24 • AED-512, on page 25 • AFPOVERTCP, on page 26 • AGENTX, on page 27 • AIRBNB, on page 28 • AIRPLAY, on page 29 • ALIWANGWANG, on page 30 • ALLRECIPES, on page 31 • ALPES, on page 32 • AMANDA, on page 33 • AMAZON, on page 34 • AMEBA, on page 35 • AMAZON-INSTANT-VIDEO, on page 36 Protocols: 0-9, A 1 Protocols: 0-9, A • AMAZON-WEB-SERVICES, on page 37 • AMERICAN-EXPRESS, on page 38 • AMINET, on page 39 • AN, on page 40 • ANCESTRY-COM, on page 41 • ANDROID-UPDATES, on page 42 • ANET, on page 43 • ANSANOTIFY, on page 44 • ANSATRADER, on page 45 • ANY-HOST-INTERNAL, on page 46 • AODV, on page 47 • AOL-MESSENGER, on page 48 • AOL-MESSENGER-AUDIO, on page 49 • AOL-MESSENGER-FT, on page 50 • AOL-MESSENGER-VIDEO, on page 51 • AOL-PROTOCOL, on page 52 • APC-POWERCHUTE, on page 53 • APERTUS-LDP, on page 54 • APPLEJUICE, on page 55 • APPLE-APP-STORE, on page 56 • APPLE-IOS-UPDATES, on page 57 • APPLE-REMOTE-DESKTOP, on page 58 • APPLE-SERVICES, on page 59 • APPLE-TV-UPDATES, on page 60 • APPLEQTC, on page 61 • APPLEQTCSRVR, on page 62 • APPLIX, on page 63 • ARCISDMS, -

Citrix Netscaler Deployment Guide for Microsoft Exchange 2010
Citrix NetScaler Deployment Guide for Microsoft Exchange 2010 Table of Contents Citrix NetScaler Deployment Guide for Microsoft Exchange 2010 ................................................................... 1 Introduction .................................................................................................................................................................. 3 Solution Requirements ................................................................................................................................................ 3 Prerequisites .................................................................................................................................................................. 3 Deployment Overview ................................................................................................................................................ 4 Network Diagram ................................................................................................................................................... 7 NetScaler Deployment ................................................................................................................................................ 7 Client Access Server ............................................................................................................................................... 7 Configuring NetScaler for Outlook Web App (OWA) ................................................................................ 9 Configuring NetScaler for -

Activesync Configuration for Watchguard® SSL
ActiveSync Configuration for ® WatchGuard SSL 100 October 2009 Introduction With ActiveSync, users get push functionality to keep email, calendar, tasks, and contacts up to date on a mobile device. It is possible to securely run ActiveSync over SSL through the WatchGuard® SSL 100 appliance without having to install or start the Access Client on the mobile devices. To sync a mobile client it is necessary that an ActiveSync client is installed. How Exchange ActiveSync Works Exchange ActiveSync (EAS) is an HTTP/HTTPS‐based communication between the client and the server. The client uses a virtual directory “/Microsoft‐Server‐ActiveSync” on the IIS server to access EAS. There are no files in this directory; any request is handled by MASSYNC.DLL. MASSYNC needs access to the user’s mailbox. MASSYNC uses only Outlook Web Access, not MAPI, CDO, or any other hidden connection. Define a New Device Type for ActiveSync The ActiveSync client on a mobile device does not support authentication through the HTML form. Therefore, the SSL 100 needs to be able to identify them as devices that only support Basic Authentication. That can be achieved by defining a new device type: 1. Select Manage System in the main menu and click Device Definition in the left‐hand menu. 2. Click the Add Device Definition link. 3. Enter a display name. 4. In the definition text field add: uri = *Microsoft‐Server‐ActiveSync* 5. Click Save. WatchGuard Technologies www.watchguard.com 6. Select Resource Access in the main menu and click the Global Resource Settings link. 7. Click on the Client Access tab and then click on the Add Device Setting link. -

30,000 Mailbox Resiliency Solution for Microsoft Exchange 2013 Using Lenovo Converged HX7510 Appliances and Hyper-V
30,000 Mailbox Resiliency Solution for Microsoft Exchange 2013 using Lenovo Converged HX7510 Appliances and Hyper-V Last update: 30 August 2016 Provides a technical overview Contains performance results of Lenovo Converged HX using Microsoft ESRP Storage Solution for Microsoft Program Exchange 2013 Uses HX7510 appliances with Shows class-leading Microsoft 2012 R2 Hyper-V hyper-converged performance hypervisor of HX7510 appliance Pawan Sharma Mike Perks i 30,000 Mailbox Resiliency Solution for Microsoft Exchange 2013 using Lenovo Converged HX7510 Appliances Table of Contents 1 Overview .................................................................................................... 1 1.1 Disclaimer ................................................................................................................ 1 2 Technical overview of HX Series appliances ......................................... 2 2.1 Server Components ................................................................................................. 2 2.2 Software components .............................................................................................. 2 2.3 Networking components .......................................................................................... 5 2.4 Reliability and performance features ........................................................................ 8 3 Microsoft Exchange ................................................................................ 12 3.1 Solution overview .................................................................................................. -

Windows 10-New Features & Apps
Windows 10-New Features & Apps By Tom Krauser This article discusses some of the new features and apps that come packaged in Windows 10. It is only a brief summary of these features. For more information you can search the internet or check YouTube for instructional videos on your topic of interest. The following links provide some good basic information on Windows 10 and should be helpful to you. https://support.microsoft.com/en-us/products/windows?os=windows-10 https://support.microsoft.com/en-us/help/4043948/windows-10-whats-new-in-fall-creators-update-1709 The following article from PC World Magazine provides articles on a lot of new features in Windows 10. https://www.pcworld.com/tag/windows10/ The following article by CNET discusses some of new features in the latest update to Windows 10. https://www.cnet.com/how-to/windows-10-tips-best-features/ Alarms & Clocks: A combination of alarm clock, world clock, timer, and stopwatch. Set alarms and reminders, check times around the world, and time your activities, including laps and splits. The following link discusses how to set timers, alarms, and stopwatches: https://www.howtogeek.com/225211/how-to-set-timers-alarms-and-stopwatches-in-windows-10/ Camera: Many modern devices with Windows include a webcam and, to use it, you need an app that helps you take pictures, record videos or stream video while video chatting. For this purpose, Microsoft has built an app called Camera, which is available by default in Windows 10. Connect: Use Connect App to Cast Your Smartphone Screen to Your PC. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Surface Hub 2S Admin Guide
Surface Hub 2S Admin Guide Surface Hub 2S coming soon; Pre-release products shown; products and features subject to regulatory certification/approval, may change, and may vary by country/region. Surface Hub 2S has not yet been authorized under U.S. Federal Communications Commission (FCC) rules; actual sale and delivery is contingent on compliance with applicable FCC requirements. This documentation is an early release of the final documentation, which may be changed prior to final commercial release and is confidential and proprietary information of Microsoft Corporation. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. © 2019. Microsoft Corporation. All rights reserved Introduction .................................................................................................................................................. 1 Welcome to Surface Hub 2S ......................................................................................................................... 1 New User Experience and Features ........................................................................................................................ 1 Microsoft Teams ..................................................................................................................................................... 1 New form factor and hardware changes ................................................................................................................ 2 Surface -

Tablets in the Enterprise: Comparing the Total Cost of Ownership
TABLETS IN THE ENTERPRISE: COMPARING THE TOTAL COST OF OWNERSHIP EXECUTIVE SUMMARY Windows 8 tablets provide a PC experience, which for many workers is essential to maintaining productivity. With Windows 8, users can run familiar desktop applications, maintaining productivity without having to find new ways to carry out their tasks. They can read, edit, and print their emails and Office documents—tasks that can be a challenge on other tablets. In addition to these productivity advantages, Intel Core i5 processor and Windows 8 tablets can provide enterprises with total cost of ownership (TCO) savings of up to 18 percent compared to other tablets. We expect additional TCO savings with Intel Core vPro™ processor-based tablets due to their additional manageability capabilities. We estimate tablets with Intel Architecture and Windows 8 will have lower TCO than other tablets, primarily due to the following: reduced software costs lower management costs improved end-user productivity JANUARY 2013 A PRINCIPLED TECHNOLOGIES WHITE PAPER Commissioned by Intel Corp. TOTAL COST OF OWNERSHIP OF TABLETS IN THE ENTERPRISE In this paper, we first present a TCO analysis for a hypothetical enterprise considering four major categories of tablets for their employees: Microsoft Windows 8 tablets, Windows RT tablets, Android tablets, and Apple iPads. Because the ranges of prices and capabilities differ among models within each category, we selected a single representative model for each. Following this analysis, we discuss the dominant issues in enterprise tablet computing as of this writing. We base our TCO analysis on the primary assumptions in Figure 1. Tablets must be nine inches or larger with 64 GB of storage and Wi-Fi support. -

Android Support for Microsoft Exchange in Pure Google Devices
Android support for Microsoft Exchange in pure Google devices Note: The information presented here is intended for Microsoft Exchange administrators who are planning and implementing support for any of these pure Google devices running Android. Android support by version and device The following AndroidTM versions support Microsoft Exchange information services and security policies: ● Android 4.0.4 (Ice Cream Sandwich) ● Android 4.1 and later (Jelly Bean) The following “pure Google” devices support the Microsoft Exchange services and policies: ● Galaxy Nexus phones running Android ● Nexus S phones running Android ● Motorola Xoom tablets running Android ● Nexus 4 phones running Android ● Nexus 7 tablets running Android ● Nexus 10 tablets running Android Requirements To support Android 4.0 running on pure Google devices, you must be running one of the following versions of Microsoft Exchange: ● Exchange Server 2010 SP1 with Exchange ActiveSync 14.1 ● Exchange Server 2010 with Exchange ActiveSync 14.0 ● Exchange Server 2007 SP1 with Exchange ActiveSync 12.1 ● Exchange Server 2007 with Exchange ActiveSync 12.0 ● Exchange Server 2003 SP2 with Exchange ActiveSync 2.5 The following information applies to the Android platform, including the Settings, Email, Calendar, People, and related apps as built by Google. If a device manufacturer has modified these apps on its own devices, contact the manufacturer for information about support for Exchange features. Supported information services Users can add Microsoft Exchange accounts to their pure Google devices by using the Account & Sync settings available from the Settings or Email app. Android supports the following Exchange information services: ● Adding Exchange user accounts (via an ActiveSync server), and enforcement of some mailbox policies (as described in “Supported security policies,” next). -
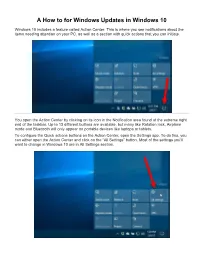
A How to for Windows Updates in Windows 10
A How to for Windows Updates in Windows 10 Windows 10 includes a feature called Action Center. This is where you see notifications about the items needing attention on your PC, as well as a section with quick actions that you can initiate. You open the Action Center by clicking on its icon in the Notification area found at the extreme right end of the taskbar. Up to 13 different buttons are available, but many like Rotation lock, Airplane mode and Bluetooth will only appear on portable devices like laptops or tablets. To configure the Quick actions buttons on the Action Center, open the Settings app. To do this, you can either open the Action Center and click on the “All Settings” button. Most of the settings you'll want to change in Windows 10 are in All Settings section. or you can open the Start menu and click the “Settings” button on the lower-left side of the menu. Windows settings is organized into various categories: System, Devices, Network & Internet, Personalization, Apps, Accounts, Time & language, Ease of Access, Privacy, and Update & security. You click on a category to view and change more settings for that category. Settings in Windows 10 – alternatively use Win () + I key combination. The Settings app from Windows 10 holds almost all the settings governing the way your computer or device works. The traditional way of getting to one setting or to another is to open the appropriate settings category and browse through it until you find what you’re looking for. The Setting app from Windows 10 is very well organized, a lot better than the old Control Panel used to be.