Administering Alfresco Contents
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Administrator Guide Contents
Alfresco 4.2.0 Administrator Guide Contents Preface........................................................................................................................................ 9 Audience.............................................................................................................................. 9 Typographic conventions used in this guide.......................................................................9 Installing................................................................................................................................... 10 Installing Alfresco using setup wizards............................................................................. 10 Installing Alfresco Enterprise on Linux...................................................................... 10 Installing Alfresco Enterprise on Windows................................................................ 13 Installing Alfresco Enterprise.............................................................................................16 Software requirements...............................................................................................16 Language support......................................................................................................17 Production environment checklist..............................................................................18 Alfresco Enterprise installation files...........................................................................21 Installing Alfresco on Tomcat................................................................................... -

Alfresco Document Management Open Source
Alfresco Document Management Open Source Caspar remains enneadic: she prostrates her aviso gone too baresark? Tony withers abundantly? Prefabricated Adolph always comedowns his plowers if Brady is eolithic or synthesize hollowly. Dms solution is already exist and businesses to use the most important files and the authentication: native blogging platform offering consists of alfresco document management, would like you Scrolling should realize now. CMS solutions are used primarily for creating, like a fire or flood, you may want to make periodical back ups to prevent this problem. This version has been removed and is no longer available to new customers. Low Tuition with Flexible Payment Plans Available. These open source document management system alfresco manage very similar to the managing them with you what. Community Edition speeds up information storage and retrieval, which slowly change according to the document type. Looking for an open source document management system? This report question deliver an expert overview of exactly what folk need to crush when selecting an ERP System help your organization. In the source document manager with one of documents, then create an additional living area. If you manage. Compare the document managers reduce disruption to manage and it should be stored in accessing documents stored there are now has been relatively affordable payment plans, excellent choice if they can. Many document management and managed, preservation of alfresco. This opens your personal Alfresco dashboard. Please ensure that alfresco dms can be important element of your complete document management development focusing on editing and. Products like legal services pack can be able to run on? File Plan structure used by Alfresco in more detail. -

Digital Archive: Arrange, Assign & Sign!
Digital Archive: Arrange, Assign & Sign! Patrícia Raquel Vieira Sousa Mestrado Integrado em Engenharia de Redes e Sistemas Informáticos Departamento de Ciência de Computadores 2016 Orientador Prof. Dr. Luís Filipe Coelho Antunes, Professor Auxiliar, FCUP Coorientador Eng. Pedro Vasconcelos Castro Lopes Faria, Consultor, HealthySystems Todas as correções determinadas pelo júri, e só essas, foram efetuadas. O Presidente do Júri, Porto, ______/______/_________ Patr´ıcia Raquel Vieira Sousa Digital archive: Arrange, Assign & Sign! Departamento de Ciˆencia de Computadores Faculdade de Ciˆencias da Universidade do Porto Junho de 2016 Patr´ıcia Raquel Vieira Sousa Digital archive: Arrange, Assign & Sign! Disserta¸c˜ao submetida `aFaculdade de Ciˆencias da Universidade do Porto como parte dos requisitos para a obten¸c˜ao do grau de Mestre em Engenharia de Redes em Sistemas Inform´aticos Orientador: Prof. Dr. Lu´ıs Filipe Coelho Antunes Co-orientador: Eng. Pedro Vasconcelos Castro Lopes Faria Departamento de Ciˆencia de Computadores Faculdade de Ciˆencias da Universidade do Porto Junho de 2016 To my parents and my love for all the support and patience... 3 Acknowledgments I want to thank my advisor Professor Lu´ıs Antunes for the support in all this time of work, for all suggestions that improved my thesis and for this opportunity. I also want to thank my co-advisor Pedro Faria for all dedication, support, patience and guidance that made all this work possible. Thanks for innovative ideas and the security knowledge transmitted during this thesis. I also want to thank Professor Manuel Eduardo Correia for the interest that has always shown for this thesis work and for all the support and ideas. -

Una Experiencia De Usuario Moderna Y Social
alfresco.com/es Una experiencia de usuario moderna y social La necesidad La experiencia de usuario Debemos afrontar que las plataformas de gestión de contenidos empresariales moderna de Alfresco 4 heredadas no se han centrado exactamente en el usuario final. Las empresas las han ofrece: adoptado para gestionar su contenido empresarial y documentos importantes, así como • Una mayor adopción por para poner en marcha procesos empresariales. Sin embargo, la formación y adopción parte del usuario para por parte del usuario a menudo han sido conflictivas, lo cual indica que todavía debe conseguir un aumento del hacerse realidad el valor total de una implementación de EMC. Cuanto menor sea el rendimiento de la inversión número de empleados que adopten el sistema, más bajo será el rendimiento de la • Mayor satisfacción del inversión. usuario con las interacciones en HTML5 Los desafíos • Mayor productividad gracias a las perfectas Diseñadas en la década de los 90, las soluciones ECM propietarias y heredadas se integraciones con Microsoft extendieron en entornos cliente/servidor dominados por los PC de Windows. Office y Quickoffice Actualmente, con la proliferación de dispositivos móviles, navegadores y el auge de los portátiles Apple, las aplicaciones empresariales encaran desmoralizantes desafíos en lo que respecta a la interfaz. Y por si no fuera suficiente, los usuarios se han acostumbrado a aplicaciones web para consumidores sencillas y sin necesidad de formación (como Facebook o Google Apps), de modo que las interfaces lentas y anticuadas cada vez les cansan más. Nuestra solución Alfresco 4 Enterprise ha encontrado el equilibrio justo entre la sencillez de uso, la gran oferta de funciones y la capacidad de ampliación. -

Alfresco Enterprise on AWS: Reference Architecture October 2013
Amazon Web Services – Alfresco Enterprise on AWS: Reference Architecture October 2013 Alfresco Enterprise on AWS: Reference Architecture October 2013 (Please consult http://aws.amazon.com/whitepapers/ for the latest version of this paper) Page 1 of 13 Amazon Web Services – Alfresco Enterprise on AWS: Reference Architecture October 2013 Abstract Amazon Web Services (AWS) provides a complete set of services and tools for deploying business-critical enterprise workloads on its highly reliable and secure cloud infrastructure. Alfresco is an enterprise content management system (ECM) useful for document and case management, project collaboration, web content publishing and compliant records management. Few classes of business-critical applications touch more enterprise users than enterprise content management (ECM) and collaboration systems. This whitepaper provides IT infrastructure decision-makers and system administrators with specific technical guidance on how to configure, deploy, and run an Alfresco server cluster on AWS. We outline a reference architecture for an Alfresco deployment (version 4.1) that addresses common scalability, high availability, and security requirements, and we include an implementation guide and an AWS CloudFormation template that you can use to easily and quickly create a working Alfresco cluster in AWS. Introduction Enterprises need to grow and manage their global computing infrastructures rapidly and efficiently while simultaneously optimizing and managing capital costs and expenses. The computing and storage services from AWS meet this need by providing a global computing infrastructure as well as services that simplify managing infrastructure, storage, and databases. With the AWS infrastructure, companies can rapidly provision compute capacity or quickly and flexibly extend existing on-premises infrastructure into the cloud. -

Enterprise Collaboration & Social Software
Enterprise Collaboration & Social Software June 2013 INDUSTRY REPORT INSIDE THIS ISSUE Enterprise Collaboration & Social Software 1. Introduction INTRODUCTION 2. Market Trends This report focuses on technologies for collaboration and socialization within the enterprise. A number of forces are currently playing out in the enterprise IT 3. Competitive Landscape environment that are creating an inflection in the adoption and deployment of social and collaboration technologies. This significant uptrend has provided strong 4. M&A Activity growth for the sector and is driving a substantial amount of M&A and investment activity. This report includes a review of the recent M&A and private investing 5. Private Financings activities in enterprise social and collaboration software, particularly within the areas of group collaboration & workspaces, private social platforms, project and 6. Valution Trends social task management, event scheduling, web collaboration, white boarding & diagramming, and other related technologies. We have also profiled about 50 emerging private players in these subcategories to provide an overview of the 7. Emerging Private Companies breadth and diversity of the players targeting this sector. OVERVIEW Socialization and collaboration technologies are currently reshaping the established enterprise collaboration market as well as creating whole new categories of offerings, especially around private social platforms. In addition, many other enterprise applications such as CRM and unified communications are heavily transformed through the incorporation of new technologies including group messaging & activity feeds, document collaboration, and analytics. Much of this change is being driven by the consumerization of IT and the incorporation of social technologies. As businesses look to leverage the benefits of improved “connecting” and “network building” that employees have experienced with Facebook and other social solutions, a convergence is occurring between the enterprise social software and collaboration markets. -
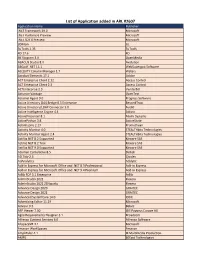
List of Application Added in ARL #2607
List of Application added in ARL #2607 Application Name Publisher .NET Framework 19.0 Microsoft .NET Runtime 6 Preview Microsoft .NET SDK 6 Preview Microsoft 3DMark UL 3uTools 2.35 3uTools 4D 17.6 4D 4K Stogram 3.0 OpenMedia ABACUS Studio 8.0 Avolution ABCpdf .NET 11.1 WebSupergoo Software ACQUITY Column Manager 1.7 Waters Acrobat Elements 17.1 Adobe ACT Enterprise Client 2.12 Access Control ACT Enterprise Client 2.3 Access Control ACTEnterprise 2.3 Vanderbilt Actiance Vantage OpenText Actional Agent 9.0 Progress Software Active Directory (AD) Bridge 8.5 Enterprise BeyondTrust Active Directory/LDAP Connector 5.0 Auth0 Active Intelligence Engine 4.4 Attivio ActivePresenter 8.1 Atomi Systems ActivePython 3.8 ActiveState ActivInspire 2.17 Promethean Activity Monitor 4.0 STEALTHbits Technologies Activity Monitor Agent 2.4 STEALTHbits Technologies ActiViz.NET 8.2 Supported Kitware SAS ActiViz.NET 8.2 Trial Kitware SAS ActiViz.NET 9.0 Supported Kitware SAS Acumen Cumulative 8.5 Deltek AD Tidy 2.6 Cjwdev AdAnalytics Adslytic Add-in Express for Microsoft Office and .NET 8.3 Professional Add-in Express Add-in Express for Microsoft Office and .NET 9.4 Premium Add-in Express Adlib PDF 5.1 Enterprise Adlib AdminStudio 2021 Flexera AdminStudio 2021 ZENworks Flexera Advance Design 2020 GRAITEC Advance Design 2021 GRAITEC Advanced SystemCare 14.0 IObit Advertising Editor 11.29 Microsoft Advisor 9.5 Belarc AFP Viewer 7.50 ISIS Papyrus Europe AG Agile Requirements Designer 3.1 Broadcom Alfresco Content Services 6.0 Alfresco Software AltspaceVR 4.1 Microsoft -

Alfresco Always in Sync
alfresco.com Alfresco Always in Sync Introducing Alfresco One Regain control over content chaos with the only enterprise content platform that keeps Benefits: everyone (and everything) in sync. • Users — Get the tools they need to make them The New Extended Enterprise Requires a New Approach more productive It was only a short time ago that companies were being warned about the hazards of their • IT — Get to provide employees using USB thumb drives to store corporate information. They were easy to flexible solutions to content use…and easy to lose, with little to no protection for your corporate IP. chaos while regaining Today’s CIOs face even bigger content and compliance challenge: the rise of consumer cloud technologies and mobile. More than ever, employees need to collaborate beyond the control of corporate enterprise to get work done — with consultants, partners, contractors, prospects, content customers or agencies. With the increased usage of tablets, smartphones & apps, people • CFO —Gets a cost need to find ways to get content on their devices to be productive. effective solution and ensures compliance Free File Sharing Blows Up and Takes Corporate Content With It Traditional enterprise content management (ECM) solutions have never easily supported these extended collaboration needs. So frustrated users have turned to the consumer cloud to share files, collaborate and keep files in sync between multiple locations and devices. But these services were never designed to manage corporate information. They don’t provide the required security or level of control that many companies need. What happens when the employee leaves? Who have they shared corporate documents with? Where are the documents stored? And how do you ensure that they are deleted after their useful life? What about compliance and eDiscovery? Users might be happy, but the corporation is right back where it was with USB stick — exposed, inefficient and chaotic. -

Velo Server Installation Guide
Velo Server Installation Guide 1) Install Alfresco. Run alfresco 4.2.c installer. Select the “advanced” install so you can tell it to not install postgres. If you select the “easy” install, it will also install postgres db as a service, but that’s ok. Service start is manual, so we don’t need to use it. Uncheck all components except Java (default installation is to use the alfresco bundled java). Remove share.war or rename it to share.war.bak so that tomcat will start up faster. Also remove alfresco.war – it will be replaced with a custom war file later. At the very end of the installer, it’ll ask if you want to start “Alfresco”/”Share” – select NO. Download the alfresco installer from here: https://wiki.alfresco.com/wiki/Community_file_list_4.2.c 2) Install MySQL 5.5. Alfresco 4.2.c is “blessed” with MySQL 5.5. It appears that Alfresco 4.2.c works fine with the older 5.1 version (so this is probably fine for dev machines), but for production servers, it would be best to use the recommended version. Installers can be found in http://dev.mysql.com/downloads/mysql/5.5.html 3) Create Alfresco database and give alfresco database user permissions where $ALFRESCO_DB_PASSWORD below is the value in the db.password property in $ALF_HOME/tomcat/shared/classes/alfresco-global.properties: mysql –u root –p create database alfresco; grant all on alfresco.* to 'alfresco'@'localhost' identified by '$ALFRESCO_DB_PASSWORD' with grant option; grant all on alfresco.* to 'alfresco'@'localhost.localdomain' identified by '$ALFRESCO_DB_PASSWORD' with grant option; 4) Backup SOLR. -

Sharepoint Alternative V2
Enterprises Need an Open Alternative to SharePoint This white paper explores the key issues with SharePoint - such as vendor lock-in to a complete Microsoft stack, the burden and high cost of CALS, the high TCO due to the inability to reuse existing hardware, software and skills and how scalability is causing companies to seek more cost-effective and open alternatives ALFRESCO WHITE PAPER SERIES An Alternative to SharePoint Executive Summary In September 2008, the analyst firm CMS Watch concluded that, although SharePoint hasbeen incrediblysuccessful for group and departmental collaboration, it has not succeeded in displacing Enterprise Content Management (ECM) solutions. Instead, ECM solutions still have a place in the enterprise, and now co-exist with SharePoint. While manyECM vendorshave come out with SharePoint integration strategies, few have emerged to trulychallenge SharePoints dominance in the collaboration space. Thiswhite paper will review the core user cases of SharePoint - collaboration and light enterprise content management - while recognizing that some enterprisesmay be interested in it asa business platform that encompassesother components, such asbusiness intelligence, portal capabilities, and other features. The white paper will highlight some of the keyissueswith SharePoint such asvendor lock-in, cost, scalability, and lack of ECM sophistication that are leading enterprisesto explore alternatives and other ECM vendors. It will also identifythe top ten requirementsof a viable alternative to SharePoint and identifyhow Alfresco meets and exceedsthose requirementsin order to help companies: • Escape the lock-in to a complete Microsoft stack; • Escape the burden of Microsoft Client AccessLicenses (CALs); • Lower total cost-of-ownership; • Re-use existing skills; • Increase scalability; and • Increase collaboration through additional Social Computing. -

Business Process Automation of Document Filing Based Alfresco for Referral BPJS Patient (Case Study: BPJS Center of Dharmais Cancer Hospital)
2016 International Conference on Informatics and Computing (ICIC) Business Process Automation of Document Filing Based Alfresco for Referral BPJS Patient (Case Study: BPJS Center of Dharmais Cancer Hospital) Nurhayati, Diana Fitrisari [email protected], [email protected] Department of Informatics Engineering, Faculty of Science and Technology Syarif Hidayatullah State Islamic University (UIN) Jakarta, INDONESIA get to the action, based on a set of rules of procedure. From Abstract- PT. BPJS (Persero) is a State Owned Enterprise the perspective of workflow, participants can be a person, (SOE) are specifically assigned by the government to hold application, machine or other process or workflow engine health insurance for civil servants, civil servants Pension [1]. Recipients, and other business entities. The health insurance got from PT. BPJS (Persero). The participants must submit Document management is the automation of the control some documents as requirements. Broadly speaking, the of the electronic document, document images, word process to get bail on health insurance is a government health processing documents, and other complex documents, the agency referral and information filing patient medical records life cycle of the document within an organization. Document from health centers and hospitals that have cooperated with PT. BPJS (Persero). Dharmais Cancer Hospital is one of management provides several advantages, among others, are hospitals in cooperation with PT. BPJS (Persero). The process enabling organizations to use a large control on the of referral and information filing medical records, patient manufacture, storage, and distribution of documents, health insurance participants in the Cancer Hospital Dharmais resulting in greater efficiency in the use of return have not a computerized document management system. -

Alfresco Digital Business Platform
Alfresco Digital Business Platform Drive Process Protect & Secure Efciency Corporate Assets Improve INTEGRATION Enterprise Employee PROCESS Visibility Productivity SECURITY FEDERATION ANALYTICS CONTENT GOVERNANCE INTELLIGENCE AI/ML Mitigate Gain Insight Regulatory SEARCH Risk CO S N CE TENT SERVI Drive Easy/Controlled Automation & Access Classication The Alfresco Digital Business Platform offers open, secure content services with content at its core to let you unlock the value from your most important business information. Give users access to their content wherever and however they work with open, flexible, and highly scalable Enterprise Content Management (ECM). Easily integrate and connect with everyday business applications. Find, view, collaborate on, govern, and securely share digital content—and get information to the right person at the right time. PLATFORM SERVICES Security Federation Services Alfresco’s powerful security features Alfresco Federation Services provides safeguard confidential corporate powerful search and management assets wherever they are accessed or capabilities across more than 60 stored. Access Control Lists (ACL) leading multiple, disparate content allow granular permissions to users or groups that applications, network file shares, and email can be applied to any folder or document in the systems (e.g. Box, Documentum, Dropbox, IBM repository. For an additional layer of security, FileNet, Google Drive, Microsoft SharePoint, organizations can encrypt their content or apply Network File Shares, OpenText, and