Upgrading Your Android, Elevating My Malware: Privilege Escalation Through Mobile OS Updating
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Value Transformation: Relevant Video Clips and Additional Reading
Value Transformation: Relevant Video Clips and Additional Reading By Dr. Lynn W. Phillips, Reinventures and Duke CE Executive educator, coach, and consultant to leading companies worldwide on business reinvention and the successful execution of their global growth strategies. Former award-winning faculty at Stanford Business School (12 years), Harvard, Rice, Northwestern, and University of California at Berkeley Graduate Schools of Business; also a current member of Duke’s Corporate Education Global Faculty Network working in Africa, Asia, India, and Europe. After our sessions together, many participants ask for links to the videos and articles that are cited in my presentation, as well as additional reading for those who are hungry to learn more. I’m happy to oblige; the following list should supply you with plenty of edifying viewing and reading. Enjoy! Video Clips and Films: United Breaks my guitar: as featured on CNN: http://www.youtube.com/watch?v=-QDkR-Z-69Y&feature=results_video&playnext=1&list=PL81712254DA6CA060 GEICO caveman spots: Original Geico caveman commercial: http://www.youtube.com/watch?v=e8aj1AlYvxI Geico caveman, venting to his therapist: http://www.youtube.com/watch?feature=endscreen&v=qSHxHlRwmcI&NR=1 Progressive insurance commercial comparing rates—shows actual competitors: http://www.youtube.com/watch?v=oOzoD9hR1I4 “I’m a Mac; I’m a PC” ad campaign: “I’m a Mac; I’m a PC” ad campaign: “Out of the box” spot: sums up the “easy” angle nicely: http://www.youtube.com/watch?v=YAwtBa2C4ts “I’m a Mac; I’m a PC” ad campaign: -

2(D) Citation Watch – Google Inc Towergatesoftware Towergatesoftware.Com 1 866 523 TWG8
2(d) Citation Watch – Google inc towergatesoftware towergatesoftware.com 1 866 523 TWG8 Firm/Corresp Owner (cited) Mark (cited) Mark (refused) Owner (refused) ANDREW ABRAMS Google Inc. G+ EXHIBIA SOCIAL SHOPPING F OR Exhibía OY 85394867 G+ ACCOUNT REQUIRED TO BID 86325474 Andrew Abrams Google Inc. GOOGLE CURRENTS THE GOOGLE HANDSHAKE Goodway Marketing Co. 85564666 85822092 Andrew Abrams Google Inc. GOOGLE TAKEOUT GOOGLEBEERS "Munsch, Jim" 85358126 86048063 Annabelle Danielvarda Google Inc. BROADCAST YOURSELF ORR TUBE BROADCAST MYSELF "Orr, Andrew M" 78802315 85206952 Annabelle Danielvarda Google Inc. BROADCAST YOURSELF WEBCASTYOURSELF Todd R Saunders 78802315 85213501 Annabelle Danielvarda Google Inc. YOUTUBE ORR TUBE BROADCAST MYSELF "Orr, Andrew M" 77588871 85206952 Annabelle Danielvarda Google Inc. YOUTUBE YOU PHOTO TUBE Jorge David Candido 77588871 85345360 Annabelle Danielvarda Google Inc. YOUTUBE YOUTOO SOCIAL TV "Youtoo Technologies, Llc" 77588871 85192965 Building 41 Google Inc. GMAIL GOT GMAIL? "Kuchlous, Ankur" 78398233 85112794 Building 41 Google Inc. GMAIL "VOG ART, KITE, SURF, SKATE, "Kruesi, Margaretta E." 78398233 LIFE GRETTA KRUESI WWW.GRETTAKRUESI.COM [email protected]" 85397168 "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP PAY BUMPTOPAY Nexus Taxi Inc 85549958 86242487 1 Copyright 2015 TowerGate Software Inc 2(d) Citation Watch – Google inc towergatesoftware towergatesoftware.com 1 866 523 TWG8 Firm/Corresp Owner (cited) Mark (cited) Mark (refused) Owner (refused) "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP BUMP.COM Bump Network 77701789 85287257 "BUMP TECHNOLOGIES, INC." GOOGLE INC. BUMP BUMPTOPAY Nexus Taxi Inc 77701789 86242487 Christine Hsieh Google Inc. GLASS GLASS "Border Stylo, Llc" 85661672 86063261 Christine Hsieh Google Inc. GOOGLE MIRROR MIRROR MIX "Digital Audio Labs, Inc." 85793517 85837648 Christine Hsieh Google Inc. -

A Technology Wish List for 2013 4 January 2013, by Deborah Netburn and Salvador Rodriguez
A technology wish list for 2013 4 January 2013, by Deborah Netburn And Salvador Rodriguez As we ring in the new year, let's raise a virtual decided to delay the Nexus Q in July and add more glass to all the tech that is yet to come. features. That was probably a good move, but we haven't heard anything about the Q since. Here's We're hoping for waterproof gadgets, bendable hoping we see it again in 2013, with more features smartphones, a closer look at Google Inc.'s and a smaller price tag. revamped Nexus Q TV box, and - God willing - a new way to watch television that involves just one 6. The universal waterproofing of gadgets: At the remote. International Consumer Electronics Show last year, we saw an iPhone get dunked in a tank of water Here's our list of the technology we can't wait to and emerge just fine, thanks to a water-repellent obsess over, write about and try out in 2013. coating called Liquipel. This year, we'd like to see water-repellent coatings come standard in all of our 1. IEverything: We already know Apple Inc. will gadgets. come out with new versions of all its mobile devices, as it always does, but that doesn't make 7. The Amazon, Microsoft and Motorola phones: the announcements any less exciting. Some Amazon.com Inc. and Microsoft Corp. launched rumors have said the next iPhone will come in large-size tablets this year to take on the iPad, and many colors, the iPad will be skinnier and the iPad rumors have said the two companies will launch mini will get Apple's high-resolution Retina display. -
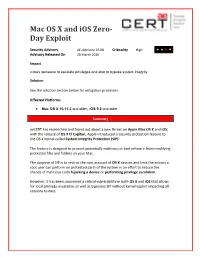
Mac OS X and Ios Zero- Day Exploit
Mac OS X and iOS Zero- Day Exploit Security Advisory AE-Advisory 16-08 Criticality High Advisory Released On 28 March 2016 Impact Allows someone to escalate privileges and also to bypass system integrity Solution See the solution section below for mitigation processes. Affected Platforms Mac OS X 10.11.3 and older, iOS 9.2 and older Summary aeCERT has researched and found out about a new threat on Apple Mac OS X and iOS; with the release of OS X El Capitan, Apple introduced a security protection feature to the OS X kernel called System Integrity Protection (SIP). The feature is designed to prevent potentially malicious or bad software from modifying protected files and folders on your Mac. The purpose of SIP is to restrict the root account of OS X devices and limit the actions a root user can perform on protected parts of the system in an effort to reduce the chance of malicious code hijacking a device or performing privilege escalation. However, it has been uncovered a critical vulnerability in both OS X and iOS that allows for local privilege escalation as well as bypasses SIP without karnel exploit impacting all versions to date. Threat Details The zero day vulnerability is a Non-Memory Corruption bug that allows hackers to execute arbitrary code on any targeted machine, perform remote code execution (RCE) or sandbox escapes. The attacker then escalates the malware's privileges to bypass System Integrity Protection SIP, alter system files, and then stay on the infected system. By default, System Integrity Protection or SIP protects these folders: /System. -

Is Android the New Embedded Linux?
Is Android the new Embedded Linux? AnDevCon 2013 Karim Yaghmour [email protected] 1 These slides are made available to you under a Creative Commons Share- Delivered and/or customized by Alike 3.0 license. The full terms of this license are here: https://creativecommons.org/licenses/by-sa/3.0/ Attribution requirements and misc., PLEASE READ: ● This slide must remain as-is in this specific location (slide #2), everything else you are free to change; including the logo :-) ● Use of figures in other documents must feature the below “Originals at” URL immediately under that figure and the below copyright notice where appropriate. ● You are free to fill in the “Delivered and/or customized by” space on the right as you see fit. ● You are FORBIDEN from using the default “About” slide as-is or any of its contents. rd ● You are FORBIDEN from using any content provided by 3 parties without the EXPLICIT consent from those parties. (C) Copyright 2013, Opersys inc. These slides created by: Karim Yaghmour Originals at: www.opersys.com/community/docs 2 About ● Author of: ● Introduced Linux Trace Toolkit in 1999 ● Originated Adeos and relayfs (kernel/relay.c) ● Training, Custom Dev, Consulting, ... 3 1. Why are we asking this question? ● Android is based on Linux ● Android is “embedded” ● Android is extremely popular ● Android enjoys good support from SoC vendors Mostly - The trends are there 4 1.1. Why did Embedded Linux rise? ● EETimes 2005 survey ... http://www.embedded.com/electronics-blogs/- include/4025539/Embedded-systems-survey-Operating- systems-up-for-grabs ● EETimes 2013 survey http://www.slideshare.net/MTKDMI/2013-embedded-market- study-final http://www.eetimes.com/electronics-news/4407897/Android-- FreeRTOS-top-EE-Times--2013-embedded-survey 5 1.2. -
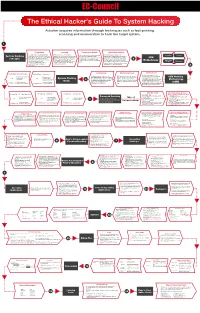
Download the Ethical Hacker's Guide to System Hacking
The Ethical Hacker's Guide To System Hacking Attacker acquires information through techniques such as foot printing, scanning and enumeration to hack the target system. 1 Footprinting Scanning Enumeration Module Vulnerability Analysis It is the process of accumulating data Vulnerability Assessment is an This is a procedure for identifying This is a method of intrusive probing, Footprinting Scanning System Hacking regarding a specific network environment. active hosts, open ports, and unnecessary through which attackers gather examination of the ability of a system or In this phase, the attacker creates a profile services enabled on ports. Attackers use information such as network user lists, application, including current security CEH concepts of the target organization, obtaining different types of scanning, such as port routing tables, security flaws, and procedures, and controls to with stand 2 information such as its IP address range, scanning network scanning, and simple network protocol data (SNMP) assault. Attackers perform this analysis Methodology Vulnerability namespace and employees. Enumeration vulnerability, scanning of target networks data. to identify security loopholes, in the target Analysis Footprinting eases the process of or systems which help in identifying organization’s network, communication system hacking by revealing its possible vulnerabilities. infrastructure, and end systems. vulnerabilities 3 Clearing Logs Maintaining Access Gaining Access Hacking Stage Escalating Privileges Hacking Stage Gaining Access It involves gaining access to To maintain future system access, After gaining access to the target low-privileged user accounts by To acquire the rights of To bypass access CEH Hacking attackers attempt to avoid recognition system, attackers work to maintain cracking passwords through Goal another user or Goal controls to gain System Hacking by legitimate system users. -

Android Exploits Commanding Higher Price Than Ever Before
Memo 10/09/2019 - TLP:WHITE Android exploits commanding higher price than ever before Reference: Memo [190910-1] – Version: 1.0 Keywords: Android, iOS, exploit, vulnerability Sources: Zerodium, Google, Wired Key Points The price of android exploits exceeds the price of iOS exploits for the first time This is possibly because Android security is improving over iOS The release of Android 10 is also a likely cause for the price hike Summary Zerodium1, a cyber security exploit broker dealing in zero-day vulnerabilities, has published its most recent price list. It indicates that the price of an Android full-chain exploit with persistence can fetch the developer up to 2,500,000 dollars. The going rate for a similar exploit for Apple’s iOS has gone down by 500,000 dollars and is now worth 2,000,000. This is the first confirmed time when Android exploits are valued more than iOS. Zerodium payouts for mobile devices Up to $2,500,000 Android zero click full compromise chain with persistence. Up to $2,000,000 iOS zero click full compromise chain with persistence. Up to $1,500,000 WhatsApp zero click remote code execution with iMessage remote code execution with local local privilege escalation on iOS or Android. privilege escalation. Up to $1,000,000 WhatsApp remote code execution with local privilege SMS/MMS remote code execution with local escalation on iOS or Android. privilege escalation on iOS or Android. Comments Zero-click exploits do not require interaction from the user. This is very difficult to achieve and thus commands the highest prices. -

Microsoft Overhauls, the Apple Way Consolidating Units to Harmonize Technology, As Its Rivals Have
The New York Times Replica Edition - The New York Times - 12 Jul 201... http://nytimes.newspaperdirect.com/epaper/showarticle.aspx?article=94c... Previous Article Next Article 12 Jul 2013 The New York Times By NICK WINGFIELD Microsoft Overhauls, the Apple Way Consolidating Units to Harmonize Technology, as Its Rivals Have SEATTLE — A couple of years ago, a satirical set of diagrams depicting the organization of Amazon, Apple, Facebook and other technology companies made the rounds on the Internet. The chart for Microsoft showed several isolated pyramids representing its divisions, each with a cartoon pistol aimed at the other. MANU CORNET A satirical set of diagrams from 2011 illustrating technology companies’ structures made the rounds on the Internet. The illustrator works at Google. Printed and distributed by NewpaperDirect | www.newspaperdirect.com | Copyright and protected by applicable law. Previous Article Next Article 1 of 2 7/17/2013 2:19 PM The New York Times Replica Edition - The New York Times - 12 Jul 201... http://nytimes.newspaperdirect.com/epaper/showarticle.aspx?article=94c... 2 of 2 7/17/2013 2:19 PM Microsoft Overhauls, the Apple Way - NYTimes.com http://www.nytimes.com/2013/07/12/technology/microsoft-revamps-struc... July 11, 2013 Microsoft Overhauls, the Apple Way By NICK WINGFIELD SEATTLE — A couple of years ago, a satirical set of diagrams depicting the organization of Amazon, Apple, Facebook and other technology companies made the rounds on the Internet. The chart for Microsoft showed several isolated pyramids representing its divisions, each with a cartoon pistol aimed at the other. Its divisions will war no more, Microsoft said on Thursday. -
Macledger 09.13
SEPTEMBER 2013 MacLedger Newsletter of the New Jersey Macintosh Users Group, Inc iPhone 5s With the launch of the new iPhone 5s, the most forward-thinking smartphone in the world, iPhone 5c, the most colorful iPhone yet and iOS 7, the most significant iOS update since the original iPhone the, Apple is ushering in next gen- eration of mobile computing, deliv- ering an incredible new hardware and software experience that only Apple could create. Apple Introduces iPhone 5c— The Most Colorful iPhone Yet All-New Design, Packed with Incredible Features in Five Gorgeous Colors Visit iPhone website Apple News OSX MAVERICKS ITUNES RADIO IPAD The MacLedger—Newsletter of the New Jersey Macintosh Users Group, Inc Gotta Mac, iPhone, or iPad? EDITORS NOTE Congratulations! You are a Hello Everyone, fellow Mac/Apple user! You own one or more because they have the Welcome to the new MacLedger! friendliest interface; they have the best apps, and they’re used by the nicest people! The newsletter will connect you, with articles of interest, to the Inter- Do you need help? Questions answered? Come join us at our regular monthly meetings. net. NJMUG is a collection of diverse people, with The MacLedger will also have room vast experience in the Macintosh/Apple world. for any original articles you may wish If there is a question to be answered, NJMUG is just the place to ask it. We are happy to share The deadline, for publication to submit. our knowledge and experience. in “MacLedger,” is the fourth Tuesday of each month for the next month’s issue. -

Extreme Privilege Escalation on Windows 8/UEFI Systems
Extreme Privilege Escalation on Windows 8/UEFI Systems C o r e y K a l l e n b e r g @ c o r e y k a l X e n o K o v a h @ x e n o k o v a h John Butterworth @jwbutterworth3 Sam Cornwell @ssc0rnwell © 2014 The MITRE Corporation. All rights reserved. | 2 | Introduction . Who we are: – Trusted Computing and firmware security researchers at The MITRE Corporation . What MITRE is: – A not-for-profit company that runs six US Government "Federally Funded Research & Development Centers" (FFRDCs) dedicated to working in the public interest – Technical lead for a number of standards and structured data exchange formats such as CVE, CWE, OVAL, CAPEC, STIX, TAXII, etc – The first .org, !(.mil | .gov | .com | .edu | .net), on the ARPANET © 2014 The MITRE Corporation. All rights reserved. | 3 | Attack Model (1 of 2) . We’ve gained administrator access on a victim Windows 8 machine . But we are still constrained by the limits of Ring 3 © 2014 The MITRE Corporation. All rights reserved. | 4 | Attack Model (2 of 2) . As attackers we always want – More Power – More Persistence – More Stealth © 2014 The MITRE Corporation. All rights reserved. | 5 | Typical Post-Exploitation Privilege Escalation . Starting with x64 Windows vista, kernel drivers must be signed and contain an Authenticode certificate . In a typical post-exploitation privilege escalation, attacker wants to bypass the signed driver requirement to install a kernel level rootkit . Various methods to achieve this are possible, including: – Exploit existing kernel drivers – Install a legitimate (signed), but vulnerable, driver and exploit it . -

Towards Taming Privilege-Escalation Attacks on Android
Towards Taming Privilege-Escalation Attacks on Android Sven Bugiel1, Lucas Davi1, Alexandra Dmitrienko3, Thomas Fischer2, Ahmad-Reza Sadeghi1;3, Bhargava Shastry3 1CASED/Technische Universitat¨ Darmstadt, Germany 2Ruhr-Universitat¨ Bochum, Germany fsven.bugiel,lucas.davi,[email protected] thomas.fi[email protected] 3Fraunhofer SIT, Darmstadt, Germany falexandra.dmitrienko,ahmad.sadeghi,[email protected] Abstract 1. Introduction Android’s security framework has been an appealing sub- Google Android [1] has become one of the most popular ject of research in the last few years. Android has been operating systems for various mobile platforms [23, 3, 31] shown to be vulnerable to application-level privilege esca- with a growing market share [21]. Concerning security and lation attacks, such as confused deputy attacks, and more privacy aspects, Android deploys application sandboxing recently, attacks by colluding applications. While most of and a permission framework implemented as a reference the proposed approaches aim at solving confused deputy at- monitor at the middleware layer to control access to system tacks, there is still no solution that simultaneously addresses resources and mediate application communication. collusion attacks. The current Android business and usage model allows developers to upload arbitrary applications to the Android In this paper, we investigate the problem of designing and app market1 and involves the end-user in granting permis- implementing a practical security framework for Android to sions to applications at install-time. This, however, opens protect against confused deputy and collusion attacks. We attack surfaces for malicious applications to be installed on realize that defeating collusion attacks calls for a rather users’ devices (see, for instance, the recent DroidDream system-centric solution as opposed to application-dependent Trojan [6]). -

By Zohaib & Vlad
Follow the slides: goo.gl/bvmYgb Privilege Escalation in Windows OS by Zohaib & Vlad Follow the slides: goo.gl/bvmYgb What is Privilege Escalation? An act of exploiting a bug, design flaw or configuration oversight with the goal to gain elevated access to application resources ● Gives the ability to perform unauthorized actions in software, web apps, operating systems What is Privilege Escalation? Vertical Horizontal Accesses to functions that are Accesses functions that are reserved for higher privilege users accessible by other normal users. or applications. ● gaining administrative privileges ● Accessing accounts on the same user level ● Jailbreaking Devices ● Lock Screen Bypass ● Stealing usernames/passwords Vertical: Cross-zone scripting A web browser exploit that takes advantage of a zone-based vulnerability http://windowsupdate.microsoft.com%2f.example.com/ Windows Permission Structure ● root is “Local System” Account ● Windows UAC (User Account Control) ○ disabled admin account, instead uses UAC ● “sudo” is “runas” to run with privileges Types of Accounts: ● Local User ● Domain User ● The LocalSystem Windows with User Access Control ● All users run as an unprivileged user by default, even when logged on as an Administrator. ● Once running, the privilege of an application cannot be changed. ● Users are prompted to provide explicit consent before using elevated privilege, which then lasts for the life of the process. Windows OS Privilege Escalation ● replacing “screensaver” binary ● scan the registry for ○ logon Information ○ network