(12) Patent Application Publication (10) Pub. No.: US 2007/0032225A1 Konicek Et Al
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Synaptics Onetouch(TM) Solution Showcased in New LG Chocolate Mobile Phone
Synaptics OneTouch(TM) Solution Showcased in New LG Chocolate Mobile Phone Configurable capacitive solution provides superior tools and support in the design of the LG VX8550 phone's user interface SANTA CLARA, Calif., Aug 27, 2007 /PRNewswire-FirstCall via COMTEX News Network/ -- Synaptics Inc. (Nasdaq: SYNA), a leading developer of capacitive interface solutions for mobile computing, communications and entertainment devices, today announced that its configurable OneTouch solution is shipping in the new LG Chocolate (VX8550) slider phone. The second-generation LG Chocolate phone has a four-button user interface enabled by Synaptics' OneTouch capacitive solution that provides navigation and function keys. Synaptics' technology allows OEMs to create sleek and desirable industrial designs for consumers by enabling thin, flexible and under-plastic solutions. "Synaptics' OneTouch development kit, tools and support greatly reduced the cycle time from design to development to production," said Woo-Young Kwak, head of LG Electronics mobile handset R&D center. "LG strives to bring innovative products to market while ensuring consumer satisfaction through an enjoyable user experience and Synaptics' OneTouch solution allowed us to incorporate a reliable interface in our new chocolate phone that we expect will delight users." With a focus on reliability and usability considerations, Synaptics' OneTouch is a chip-based solution for OEMs wanting to incorporate capacitive touch interfaces in their products. OEMs reduce their time to market as they go from concept to production using Synaptics' best-in-class design tools and expert technical support while taking advantage of superior product features and performance. "Synaptics' OneTouch offering is a complete end-to-end solution, engineered specifically to help our customers design intuitive and superior capacitive interfaces tailored to their products," said RK Parthasarathy, product line director at Synaptics. -

LG-BL40) October 2009
LG Releases New Chocolate Model (LG- BL40) 4 September 2009 “The new LG Chocolate will dramatically change the way we interact with our phones,” said Dr. Skott Ahn, CEO of LG Electronics Mobile Communications Company. “The new Chocolate reflects the originality and sophistication of the Black Label Series and like its predecessor, we are confident that the new Chocolate will create its own legacy and further enhance our standing in the market.” Beginning from the UK, the new LG Chocolate will be released across the Europe in September and will be expanded to the rest of the world from LG Chocolate (LG-BL40) October 2009. Source: LG LG Electronics today announced the worldwide retail release of the highly anticipated new Chocolate (LG-BL40). The stunning fourth handset of the Black Label Series will be available in Europe from mid-September before making its way around the world. With the introduction of this bold new shape, the new Chocolate is essentially reinventing the way consumers view and use mobile phones. Designed with sleek sophistication, the strikingly unconventional 4-inch wide screen opens up an enlarged and more optimal space for “on-the-go” computing, allowing for an entirely new mobile experience that raises the bar of innovation. Users will see things differently with the widened 21:9 panoramic display that establishes a new level of visual comfort for the reading of web pages and e-mail and dramatically brings videos and games to life with cinematic flair. Going wide also allows for the dual screen era to finally be brought to handsets for enhanced usability, which when combined with LG’s upgraded and intuitive S- Class UI brings a whole new meaning to the words “user friendly”. -
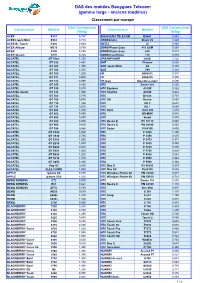
DAS Des Mobiles Bouygues Telecom (Gamme Large - Anciens Modèles) Classement Par Marque
DAS des mobiles Bouygues Telecom (gamme large - anciens modèles) Classement par marque DAS Constructeur DAS Constructeur Constructeur Modèle Constructeur Modèle (W/kg) (W/kg) ACER E101 0,747 BOUYGUES TELECOM BS401 0,542 ACER Liquid Mini E310 0,719 CROSSCALL Shark V2 1,460 ACER Be Touch E400 0,949 DBTEL J6 0,960 ACER Allegro M310 0,780 DORO Phone Easy 410 GSM 0,263 ACER S100 0,725 DORO Phone Easy 610 0,313 ACER Stream S110 0,760 DORO EasyPhone 715 0,389 ALCATEL OT View 1,350 DREAMPHONE G500i 1,120 ALCATEL OT 292 0,487 GHT Chrome 0,636 ALCATEL OT 303 1,300 GHT Jason Mraz G3 0,559 ALCATEL OT 304 1,000 GHT T99 0,316 ALCATEL OT 305 1,200 HP HW6515 0,391 ALCATEL OT 311 0,600 HP HW6915 0,390 ALCATEL OT 332 0,490 HP Ipaq Data Messenger 0,590 ALCATEL OT 355 0,850 HTC Desire 601 0,530 ALCATEL OT 535 0,570 HTC Explorer A310E 0,526 ALCATEL Sénior OT 536 1,090 HTC ChaCha A810E 0,822 ALCATEL OT 565 0,720 HTC Desire 0,752 ALCATEL OT 708 0,660 HTC HD Desire 0,826 ALCATEL OT 710 1,100 HTC HD 2 0,631 ALCATEL OT 735 0,570 HTC HD 7 0,659 ALCATEL OT 800 1,080 HTC Hero Hero 100 1,210 ALCATEL OT 802 0,800 HTC HD-MINI 0,985 ALCATEL OT 808 0,800 HTC Smart 0,990 ALCATEL OT 880 0,900 HTC Desire Z PC 10110 0,863 ALCATEL OT 980 0,640 HTC Desire S PG 88100 0,353 ALCATEL OT 995 0,586 HTC Radar PI 06100 0,400 ALCATEL OT C550 0,560 HTC P 3300 1,100 ALCATEL OT C630 0,790 HTC P 3450 0,635 ALCATEL OT E160 1,000 HTC P 3470 0,371 ALCATEL OT E230 1,000 HTC P 3600 0,980 ALCATEL OT E260 0,530 HTC P 3650 0,890 ALCATEL OT E801 1,000 HTC P 3700 0,854 ALCATEL OT E805 1,000 HTC P -

Datasheet Chocolate Touch LG:Datasheet Chocolate Touch LG Printer 10/2/09 9:50 AM Page 1
Datasheet_chocolate_Touch_LG:Datasheet_chocolate_Touch_LG Printer 10/2/09 9:50 AM Page 1 Meet the new LG Chocolate Touch: the stylish, feature-rich phone with Dolby® Mobile which delivers an BLUETOOTH® GENERAL • Version: 2.1 + EDR (Enhanced Data Rate) • Customizable Font Size and Type for Dialing, Menus, enhanced listening experience with • Save up to 20 Bluetooth Pairings Lists, and Messages • Supported Profiles: headset, handsfree*, dial-up networking, • Charging Screens: Desk Clock, Calendar stereo, phonebook access, basic printing, object push**, • Micro USB/Charging Port sparkling clarity. For music lovers, it’s file transfer, basic imaging, human interface • USB Charging via Computer • Listen to Music with Optional Stereo Bluetooth Headset*** • Clear Images, Text, and Fun Animations through Flash User • Send all Contacts and Calendar Events via Bluetooth Interface Support the sweetest LG Chocolate yet. • Print and Send User Generated Pictures (JPEG) via Bluetooth • GPS Support for Enhanced Location Accuracy *For Bluetooth vehicle/accessory compatibility, go to www.verizonwireless.com/bluetoothchart. • Airplane/Standalone Mode (RF Off) Bluetooth **Phone does not support all OBEX profiles. • Changeable Back Plates: Black and Purple **Accessories sold separately. VOICE/AUDIO SPECIFICATIONS • One-Touch Speakerphone • Technology: CDMA • Speaker-Independent Voice Commands • Frequency: 1.9 GHz CDMA PCS, 800 MHz CDMA (Digital Dual-Band) • Text to Speech • Data Transmission: EVDO† Rev. 0 • Voice-Activated Dialing up to 1,000 Entries • Dimensions: 4.30"(H) x 2.20"(W) x 0.47"(D) • Voice Recording Time: 1 min. or 1 hr.* (standby) for up to 1500 memos • Weight: 4.23 oz. SOUND • MP3 Music Ringer Support (clips from hit songs)† • Display: 262K Color TFT, 400 x 240 Pixels, 3.0" • 28 Unique Ringtones + Vibrate and Silent Modes • Standard Battery: 1,000 mAh • TTY/TDD Support • Usage Time: up to 306 Minutes* • Hearing Aid Compatible (M4/T4 - Rating) • Standby Time: up to 470 Hours* STYLING *Depends on available memory. -

(12) United States Design Patent (10) Patent No.: US D684,571 S Akana Et Al
USOOD684571S (12) United States Design Patent (10) Patent No.: US D684,571 S Akana et al. (45) Date of Patent: Jun. 18, 2013 (54) ELECTRONIC DEVICE (56) References Cited (75) Inventors: Jody Akana, San Francisco, CA (US); U.S. PATENT DOCUMENTS Bartley K. Andre, Menlo Park, CA 2.424,630 A 7, 1947 Perez (US); Jeremy Bataillou, San Francisco, D262,151 S 12/1981 Sussman CA (US); Daniel J. Coster, San (Continued) Francisco, CA (US); Daniele De Iuliis, San Francisco, CA (US); M. Evans FOREIGN PATENT DOCUMENTS Hankey, San Francisco, CA (US); AU 315078 7/2007 Julian Hoenig, San Francisco, CA (US); CA 72548 5, 1993 Richard P. Howarth, San Francisco, CA (Continued) (US); Jonathan P. Ive, San Francisco, CA (US); Duncan Robert Kerr, San OTHER PUBLICATIONS Francisco, CA (US); Shin Nishibori, "A Day in the Life of InfoLink.” Stanford University Libraries, pub Kailua, HI (US); Matthew Dean lished May 1, 2003. Rohrbach, San Francisco, CA (US); Peter Russell-Clarke, San Francisco, (Continued) CA (US); Christopher J. Stringer, Woodside, CA (US); Eugene Antony Primary Examiner — Barbara Fox Whang, San Francisco, CA (US); Rico (74) Attorney, Agent, or Firm — Sterne, Kessler, Zorkendorfer, San Francisco, CA (US) Goldstein & Fox PLLC (57) CLAM (73) Assignee: Apple Inc., Cupertino, CA (US) The ornamental design for an electronic device, as shown and (**) Term: 14 Years described. (21) Appl. No.: 29/431,553 DESCRIPTION FIG. 1 is a bottom front perspective view of an electronic (22) Filed: Sep. 7, 2012 device showing our new design; (51) LOC (9) Cl. .................................................. 14-02 FIG. 2 is a bottom rear perspective view thereof; (52) U.S. -

The Study on the Smartphone Strategies of Samsung and LG
The study on the Smartphone strategies of Samsung and LG before and after the iPhone launch in Korea By Dae-Won Kim THESIS Submitted to KDI School of Public Policy and Management in partial fulfillment of the requirements for the degree of MASTER OF BUSINESS ADMINISTRATION 2010 The study on the Smartphone strategies of Samsung and LG before and after the iPhone launch in Korea By Dae-Won Kim THESIS Submitted to KDI School of Public Policy and Management in partial fulfillment of the requirements for the degree of MASTER OF BUSINESS ADMINISTRATION 2010 Professor Seung-Joo Lee ABSTRACT The study on the Smartphone strategies of Samsung and LG before and after the iPhone launch in Korea By Dae-Won Kim In Korea, domestic mobile phone brands take up almost 90% of market share. Such market dominance was mainly driven by high customer loyalty to Korean brands and advanced technological prowess of Korean handset manufacturers. However, upon its arrival, iPhone started to reshape the market landscape. Smartphones became a new market trend. Hit by so called ‘iPhone shock’, Korean mobile phone makers lost their market hegemony and ended up falling behind the trend. Against this backdrop, this thesis aims to study why Samsung and LG Electronics lost ground to Apple, a newcomer in the mobile phone business, by analyzing the competitiveness of iPhone, the mobile phone industry before and after the launch of iPhone, and relevant policies and the strategies of Samsung and LG. It was the absence of ability to create new market that made them underperform in the smartphone market at the beginning. -

It Is Hard to Miss How Passionate We Are About Technology, Design, the Environment, and Our Neighbors. and Now, That Passion Is Delivering
IT is hard to miss how passionate we are about technology, design, the environment, and our THE PERFECT HARMONY OF neighbors. And now, that passion is delivering... We shipped a record 80.5 million mobile phones in 2007, a remarkable consumers with stylish design and innovations in image capture, user It is hard to think of any consumer 27% improvement that boosted sales 20% to USD 11.2 billion. Operat- interface, and Internet connectivity. ing profit margin also continued to improve, rising from 6.8% to 8.1% electronics field that changes more as our premium handsets won over consumers around the globe. In 2008, many of our new phones will feature touch technology to make During the year, we expanded our product localization strategy from their advanced features easier to use. These will include high-tech rapidly and dramatically than the mobile North America, Europe, and Korea to include the CIS, India, and South handsets with advanced camera and Internet features such as the LG- MC phone space. Models seem to come and and Central America. We also sharpened our cost-competitiveness by KF510, LG-KF600, and LG-KF700. We will also launch the LG Secret, the Mobile Communications strengthening operations, increasing our number of global platforms, third phone in our Black Label series. Designed around the concept of Company and streamlining our global supply chain. In 2008, we are aiming to “style that lasts”, the LG Secret has a timeless and elegant design that is go overnight, and only a precious few grow sales volume, revenue, and operating profit by more than 20% enhanced by stylish materials such as carbon fiber and tempered glass. -

LG Launches Third Black Label Series Handset LG Secret
Media Release Secret Unveiled: LG Launches Third Black Label Series Handset LG Secret Sydney, 24 June 2008: LG Electronics, worldwide leader in mobile communication technology and design, announces the Australian launch of the third LG Black Label Series handset, LG Secret (KF750). Following the success of its predecessors, LG Chocolate and LG Shine, the third model from the LG Black Label Series includes an innovative design and enriched technological features including one of the slimmest profiles for a 5 megapixel camera phone at just 11.8mm. The phone was developed to satisfy the refined tastes of trendsetters who desire a sophisticated design with an enduring elegance. The name Secret symbolises a slender and stylish handset that does not compromise the benefits and convenience of LG’s smart, digital technology. The meaning of the pet name, ‘LG Secret,’ is to tantalise the user with the phones features and explore the inner workings of the handset that will never go out of style. “The success of the previous models in the Black Label Series confirmed that consumers are looking for timeless elegance, personal style and digital sophistication with their mobile phones,” says Carli Wilson, Marketing Manager of LG Electronics Mobile Communications. “LG Secret is designed to diversify the way users interact with their handsets.” Timeless Style LG Secret will always look new thanks to the materials incorporated into the phone. Carbon fibre, one of the strongest composite materials used in aerospace and high- performance automotives, adds to the handset's durability without compromising its sleek design. Tempered glass, adding sheen and strength, shields the front LCD with a polished simplicity and enhances the quality of multimedia experience. -

West Midlands Police Freedom of Information 08/07/15 Ref: SZURN
West Midlands Police Freedom of Information Total number of reported thefts of mobile phones in your jurisdiction over the last three years. Please break the information down yearly , Please provide detail on the make and if possible the model (e.g 760 Samsung Galaxy Phones, 1,500 Apple iPhone 5s stole Make and model of stolen mobile phones Make And Model 2012 2013 2014 Grand Total Apple Iphone 4s 1273 1317 746 3336 Apple Iphone 4 1312 989 567 2868 Apple Iphone 5 99 1393 1036 2528 Samsung Galaxy S3 174 656 437 1267 Blackberry Curve 755 363 89 1207 Unknown 338 326 318 982 Nokia 382 308 248 938 Apple I Phone 386 314 232 932 Samsung 258 311 347 916 Blackberry 370 295 123 788 Samsung Galaxy 302 278 204 784 Samsung Galaxy S4 0 205 515 720 Apple Iphone 5s 0 0 682 682 Samsung Galaxy S2 259 263 103 625 Samsung Galaxy Ace 139 221 121 481 Apple Iphone 5c 0 32 416 448 Htc 155 145 126 426 Apple Iphone 249 93 75 417 Blackberry Bold 267 97 33 397 Apple Iphone 3gs 247 91 25 363 Sony Experia 59 138 149 346 Blackberry Curve 9320 62 205 56 323 Nokia Lumia 52 118 147 317 Htc Desire 155 96 56 307 Blackberry 8520 222 58 17 297 Blackberry Torch 192 56 6 254 Blackberry 9300 163 60 11 234 Apple Iphone 5 16gb 7 141 74 222 Sony Ericsson 115 52 43 210 Htc Wildfire 134 47 13 194 Samsung Galaxy Note 42 98 50 190 Samsung Galaxy S 94 65 28 187 Blackberry Curve 9360 101 68 8 177 Apple Iphone 3g 123 37 6 166 Blackberry Curve 9300 120 34 6 160 Samsung Galaxy Note 2 0 77 74 151 Apple 54 37 56 147 Samsung Galaxy S5 0 0 145 145 Blackberry 9900 63 52 20 135 08/07/15 Ref: SZURN -

Media Release 1
Media Release LG ELECTRONICS REVEALS BIG SIGNING FOR MOBILE BRAND Sydney, 25 June 2008 – Hollywood leading man Chris Noth has been revealed as the Brand Ambassador for LG Mobile – Australia and New Zealand. The Golden Globe-nominated star, best known for his role as Mr Big from Sex & The City, was introduced to celebrities and the media during a glamorous mobile phone launch last night at Sydney’s State Theatre. Guests included former Miss Universe Jennifer Hawkins, television personalities Sara Groen and James Tobin, LG Cronulla Sharks players and MTV presenter Ruby Rose. A highlight of the sophisticated, vibrant evening was a performance by Australian jazz star Carl Riseley. Carli Wilson, LG Marketing Manager Mobile Communications, said LG was delighted to have signed up one of the world’s sexiest men as a brand ambassador. "LG mobiles are fast becoming fashion icons by skilfully integrating smart technology with stylish design,” she said. “We are delighted to associate Mr Noth with the progressive LG brand. His endorsement in Australia and New Zealand reflects the growing popularity of our handsets to a broad yet highly discerning audience.” LG Electronics’ new mobile range features the cutting-edge Touch Series of phones and the much anticipated Secret, the third handset in LG’s Black Label Series. Mr Noth said he had been impressed with the growth of the LG brand in the United States. He said he was delighted to visit Australia and promote the LG brand here. 1 “I am amazed by the rapid pace of the electronics industry, and LG is at the forefront of product innovation,” Mr Noth said. -

Samsung OMNIA, Iphone 3G
APPENDIX A 8 iPhone Killer Alternatives : iPhone Killer Page 1 of 7 iPhone Killer Most comprehensive iPhone Killer information site z Home z About iPhone Killer z Advertise z Ringtones z Sitemap 8 iPhone Killer Alternatives By admin on Jul 21, 2008 in Blackberry Bold 9000, Garmin Nuvifone, HTC Touch Pro, LG Dare, LG Voyager, Nokia N96, Samsung Instinct, Samsung OMNIA, iPhone 3G Information Week has list of 8 iPhone Killers that are alternatives to the iPhone 3G. Their list goes like this 1. Blackberry Bold 2. HTC Touch Pro 3. LG Voyager 4. LG Dare 5. Nokia N96 6. Samsung OMNIA 7. Samsung Instinct 8. Garmin Nuvifone All of these phones can be found on this website for additional information and we even have many of the phones they don’t know about. The original post can be read here. ShareThis Post a Comment Name (required) http://www.iphonekiller.com/2008/07/21/8-iphone-killer-alternatives/ 1/29/2009 Nokia 5800 ExpressMusic reaches 1M shipments : iPhone Killer http://www.iphonekiller.com/2009/01/24/nokia-5800-expressmusic-reach... iPhone Killer Most comprehensive iPhone Killer information site Home About iPhone Killer Advertise Ringtones Sitemap Nokia 5800 ExpressMusic reaches 1M shipments By admin on Jan 24, 2009 in Nokia 5800 1 of 7 1/28/2009 1:32 PM Nokia 5800 ExpressMusic reaches 1M shipments : iPhone Killer http://www.iphonekiller.com/2009/01/24/nokia-5800-expressmusic-reach... Who would’ve thought that this first iPhone Killer from Nokia has already reached 1M shipment in just few short months? The original iPhone took almost a year before it had 1M shipment. -

Hierarchical Multi-Label Classification of Social Text Streams
Hierarchical Multi-Label Classification of Social Text Streams Zhaochun Ren Maria-Hendrike Peetz Shangsong Liang University of Amsterdam University of Amsterdam University of Amsterdam Amsterdam, The Netherlands Amsterdam, The Netherlands Amsterdam, The Netherlands [email protected] [email protected] [email protected] Willemijn van Dolen Maarten de Rijke Business School University of Amsterdam University of Amsterdam Amsterdam, The Netherlands Amsterdam, The Netherlands [email protected] [email protected] ABSTRACT For many social media applications, a document in a social text Hierarchical multi-label classification assigns a document to mul- stream usually belongs to multiple labels that are organized in a tiple hierarchical classes. In this paper we focus on hierarchical hierarchy. This phenomenon is widespread in web forums, ques- multi-label classification of social text streams. Concept drift, com- tion answering platforms, and microblogs [11]. In Fig.1 we show plicated relations among classes, and the limited length of docu- an example of several classes organized in a tree-structured hier- ments in social text streams make this a challenging problem. Our archy, of which several subtrees have been assigned to individual approach includes three core ingredients: short document expan- tweets. The tweet “I think the train will soon stop again because sion, time-aware topic tracking, and chunk-based structural learn- of snow . ” is annotated with multiple hierarchical labels: “Com- ing. We extend each short document in social text streams to a munication,” “Personal experience” and “Complaint.” Faced with more comprehensive representation via state-of-the-art entity link- many millions of documents every day, it is impossible to manually ing and sentence ranking strategies.