Malware Prevention
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 10 Conquering the Basics and Beyond
SUN CITY SUMMERLIN COMPUTER CLUB WINDOWS 10 CONQUERING THE BASICS AND BEYOND MAKING THE TRANSITION FROM EARLIER EDITIONS OF WINDOWS PARTICIPANT’S PDF MANUAL Updated: August 20, 2016 now at 267 pages BY BILL WILKINSON TABLE OF CONTENTS THE ENTIRE MANUAL IS INDEXED. JUST PRESS CTRL + F TO ACCESS A SEARCH (FIND) FUNCTION CHAPTER ONE (Overview) CHAPTER FOURTEEN (Settings) CHAPTER TWO (Backup and Recovery) CHAPTER FIFTEEN (Notifications/Actions) CHAPTER THREE (Data History) CHAPTER SIXTEEN (new features) CHAPTER FOUR (Microsoft and Local CHAPTER SEVENTEEN (Edge browser) Accounts) CHAPTER EIGHTEEN (Cortana) CHAPTER FIVE (keyboard shortcuts) CHAPTER NINETEEN (Microsoft Store) CHAPTER SIX (Start Menu, Start Screen) CHAPTER TWENTY (tablet mode) CHAPTER SEVEN (Desktop) CHAPTER TWENTY-ONE (great free CHAPTER EIGHT (Search) programs) CHAPTER NINE (Apps) CHAPTER TWENTY-TWO (restore, CHAPTER TEN (File Explorer) refresh, reset) CHAPTER ELEVEN (OneDrive) CHAPTER TWENTY-THREE (other issues) CHAPTER TWELVE (Defender) CHAPTER TWENTY-FOUR (laptop issues) CHAPTER THIRTEEN (updates) CHAPTER ONE AN OVERVIEW WINDOWS 10 COMBINES THE BEST OF WINDOWS 7 AND WINDOWS 8.1 Windows 10 is designed to be intuitive for users of both Windows 7 and Windows 8.1, incorporating the “best of both worlds” to enhance your experience and help you be more productive. A GUIDE TO THE BARE-BONES BASICS OF WINDOWS 10 If you have just downloaded and installed Windows 10, you might find the following list of questions and answers will give you a “jump start” to your basic understanding of your new operating system. Where’s the Start Button? It’s in the lower-left corner of the Desktop. Click once to open and see the Start Menu. -

Windows Essential Server Solutions
Windows Essential Server Solutions At a glance: The need for a new family of server products for small and midsized businesses Small Business Server 2008 Essential Business Server 2008 Setup, management and licensing Windows Essential Server Solutions There is an argument that commissioning designed for use in small businesses with and managing servers in a small or between five and 75 users, while Essential Business Server has the features needed for midsized business is harder than in larger medium-sized companies with between 25 and 300 users. companies. The main reason for this is Windows Small Business Server 2008 Windows Small Business Server 2008 comes that the IT team in a small business may con- in two editions: Standard and Premium. sist of just one or two people, who will com- Standard Edition is based on Windows mission and manage far fewer servers, so they Server 2008 Standard Technologies. The serv- don’t get the hard-won experience of the IT er includes Exchange Server 2007 Standard specialists in larger companies. Edition, Windows SharePoint® Services 3.0, To make life easier for these IT staff, and Windows Server Update Services 3.0, 120- to ensure servers are correctly commis- day trials of Microsoft Forefront™ Security sioned and managed, Microsoft is introduc- for Exchange Server and Windows Live ing a new family of server solutions built OneCare™ for Server, and integration with specifically for small and midsize businesses Office Live Small Business. – Windows Essential Server Solutions. Based The Premium edition includes everything on Windows Server 2008 technology, they from the Standard Edition, plus Windows also provide Microsoft server products for Server 2008 Standard technologies for SBS e-mail, collaboration, PC and server manage- Premium, and SQL Server 2008 Standard ment and security, all simplified to deploy, Edition for Small Business. -

Windows Messenger Live Msn Download
Windows messenger live msn download Windows Live Messenger latest version: See. Hear. Share. Instantly.. Windows Live Messenger previously known as MSN Messenger, was renamed as part of. MSN Messenger is an instant messaging program that lets you send instant messages to your friends, and much more. Previously known as MSN Messenger, Windows Live Messenger is Microsoft's answer to instant messaging. While largely the same as its predecessor. Windows Live Messenger free download. on their MSN or Hotmail account, as the integration with the email accounts can be. Mobile and web: Using a public computer without Messenger? No problem! You can chat on the web from Windows Live Hotmail or use. Share photos: Look at photos together, right in the conversation window and Messenger tells you when people you know post new photos on Windows Live. Microsoft Windows live messenger free Download Link: Latest Version. Old Version of MSN (Live) Messenger. Website. Developer. Microsoft Corporation. Latest Version. Windows. Messenger, which offers the user the same functionalities as Windows Live Messenger. Windows Live Messenger Final Deutsch: Der Windows Live Messenger, Nachfolger des MSN Messenger, in der Version: - vom How to Download and Install Windows Live Messenger. Windows Live Messenger is a great way to talk to people online. You can now have a personal picture. Windows 7 by default is installed without Windows Live Messenger. So to get it, we will need to download and install it. select, like setting Bing as the default search provider and setting MSN as your browser home page. is a free, personal email service from Microsoft. -

Windows Live Essentials Windows Essentials 2012 All Versions
Microsoft Corporation Japan Parameter Sheet Cryptographic Features Microsoft Global Trade Compliance Date issued: 27 November 2013 Windows Live Essentials Windows Essentials 2012 All versions 暗号関連パラメータシート(日本) マイクロソフト・グローバル・トレード・コンプライアンス Parameter sheets apply to all versions of Windows Live Essentials which includes free programs from Microsoft for photos, movies, instant messaging, e‑mail, blogging, family safety, and more. Windows Live Messenger uses encryption provided by the operating system to secure user login authentication with LiveID and files transfers with SSL/TLS. Windows Live Mail does support secure messaging capabilities through S/MIME. 1. 暗号機能 / Cryptographic Capabilities 暗号機能は認証、デジタル署名又は複製することを防止され NO YES たプログラムの実行以外の目的を有するか。 The cryptographic capabilities are for purposes other than certification, digital signature, or execution of a copy- protected program. 暗号機能は本製品に搭載されているものか。1 NO YES The cryptographic capabilities are self-contained in the product 暗号機能は次のいずれかに該当するものか。 NO YES The cryptographic strength exceeds the following: A. 対称アルゴリズムを用いたものであって、アルゴリズ ムの鍵の長さが 56 ビットを超えるもの Symmetric algorithms with key length exceeding 56 bit 1 API を通じて OS から提供される場合は除く。/As opposed to that provided by the Operating System through API. Japan Parameter Sheet Cryptographic Features 1 B. 非対称アルゴリズムを用いたものであって、 (a) 512 ビットを超える整数の素因数分解(RSA 等) に基づくもの、 Asymmetric algorithms based on factorization of integers in excess of 512 bits (e.g. RSA), or (b) 有限体の乗法群における 512 ビットを超える離 散対数の計算(Diffie-Hellman 等)に基づくもの、 Computation of discrete logarithms in a multiplicative group of a finite field of size greater than 512 bits (e.g. Diffie-Hellman), or (c) 上記に規定するもの以外の群における 112 ビッ トを超える離散対数の計算(楕円曲線上の Diffie- Hellman 等)に基づくもの Discrete logarithms in a group other than (B.b) in excess of 112 bits (Diffie-Hellman over Elliptic Curve). -

Microsoft Photo Gallery Download Windows 10 Windows Live Photo Gallery 2012
microsoft photo gallery download windows 10 Windows Live Photo Gallery 2012. Windows Live Photo Gallery is a program that lets you view all the images you have saved on your computer and make some minor edits to those images. While it isn't the best photo editing tool available, it's great for beginners and those who need to make basic changes. Depending on which version of Windows you have on your computer, you may dread opening image files. Some systems take so long to open those files that you can run to the bathroom or grab a snack before the image loads. Others will load the image in a brand new screen and only let you look at it without letting you edit it. Windows Live Photo Gallery works with most versions of Windows and has a clean and easy to use interface. When you load this program, you can let it pull up all photos and videos on your computer or only those found in specific folders or areas of your computer like My Photos or My Downloads. It then lets you sort by the tags you added to those photos or by the date taken. If you did not add any tags when uploading those pictures, you can add tags with the button located on the right side of the screen. This program lets you use descriptive tags to describe the type of image or people tags to keep track of your loved ones. Double clicking on any of those photos will bring up the editing box. -

Access 2 for Windows Essentials Pdf Free Download
ACCESS 2 FOR WINDOWS ESSENTIALS PDF, EPUB, EBOOK Shelley OHara | 181 pages | 01 Dec 1996 | Macmillan Computer Publishing (a Pearson Education company) | 9780789701107 | English | Indianapolis, IN, United States Access 2 for Windows Essentials PDF Book Anything you'd like to add? How do I get this deal? Call to speak with a Marketplace Advisor to purchase additional user licenses. Search from the help categories or use the search bar to find what you're looking for. Read the article. Or maybe the community forum can help answer your question. When you buy through our links, we may get a commission. Browse pages. User Reviews. It is a set of free applications that allow you to easily create, communicate and share from your Windows PC to your favorite places on the web and to your mobile phone. Running a business can be challenging. Bank and SinglePoint are registered trademarks of U. End of pop up window. Please see a banker for details. A walk-through of the upgrade process can be found here. All our network solutions Choose the best options to enhance and secure your infras This guide will show you how to change the product key for your Windows Server environment. A vast library of over 8, video tutorials. Pre-Keyed Stock Footage:. There are alternative ways to contact us. Remember Me. In fact, only by using Standard edition of Windows server you can separate Flexible server master operations FSMO roles to more than one server and achieve higher security of your environment. Network and security solutions. See Choosing which two-factor authentication method to use. -

Live Photo Gallery Windows 10 Download
live photo gallery windows 10 download How to Use Windows Live Photo Gallery on Windows 10? When Windows 7 came out, the standalone Windows Photo Gallery application was renamed to Windows Live Photo Gallery and moved to the Windows Live Essentials suite of applications. The program has since been discontinued by Microsoft and is no longer officially supported. Windows Live Photo Gallery on Windows 10. However, despite the occasional issues users face, Windows Live Photo Gallery remains one of the most effective Windows programs ever at organizing images, as well as a competent image editor, and so still has demand. While the program can no longer be installed and used on Windows 10 through official channels, installers for offline iterations of the Windows Live Essentials suite and its components are still available elsewhere. To install Windows Live Photo Gallery on Windows 10, you need to: Click here to start downloading an installer for the standalone version of the last Windows Live Essentials 2012 build released by Microsoft. Wait for the download to complete. Once the download has been completed, navigate to the directory the installer was downloaded to. Locate the file named wlsetup-all.exe and double-click on it to run it. Wait for the installer to prepare the files required for the installation. Wait for the installer to prepare installation files On the What do you want to install screen, click on Choose the programs you want to install . Click on Choose the programs you want to install Uncheck the boxes next to all of the programs included in the Windows Live Essentials 2012 suite, only leaving the box next to Photo Gallery and Movie Maker checked and selected. -

Computer Training Options Click Here
Your Total Training Resource Microsoft® Windows 10® Learn how to perform management, wide varieties of operations, run myriads of built-in programs and maintenance tools of Windows 10. Perform managerial and maintenance commands and features. Learn about Windows essentials, tips and tricks, Managing files and folders on local, network and cloud storage areas like OneDrive. Learn how to customize the Windows environment to personalize the system to work best for you. Work with Cortana to control your computer with voice commands. The modules for Windows 10 are as follows: Module 1 – Learn All the Essential Features of Windows 10 To Schedule / Need Additional Information To schedule sessions, receive more information or for questions/clarifications contact us at: Email: Ken Keller at [email protected] or Dean Carroll at [email protected] or Phone: (630) 495-0505 or (800) 869-7497. To see a complete list of our current computer training options click here. 101 W. 22nd Street, Suite 100 630-495-0505 Lombard, IL 60148 630-495-1321 Fax www.c-kg.com Your Total Training Resource Module 1 – Learn All the Essential Features of Windows 10 • This comprehensive course covers everything you Edge browser, and work with Mail, Calendars, and need to know to install Windows, customize it to People (aka contacts). your liking, and start working with files and • Plus, learn about sharing via a home network, applications. multiuser configurations, security and privacy, and • See how to manage folders, use Cortana to search troubleshooting Windows. and navigate, browse the web with the new Microsoft Management and Maintenance: • Learn how to configure updates, monitor events and • Reviewing event logs. -

Parental Controls on Your Computer's Operating System Somerford
Three free parental control programs Third party parental controls Norton Online Family Norton Online Family (https:// There are also dedicated parental control onlinefamily.norton.com/familysafety/ solutions available online that are there to basicpremium.fs) is free software that lets parents help you block inappropriate content - some monitor the websites their children visit as well as Somerford Primary School are free and others you have to pay for. what they search for online and who they chat with. Not only can parents set time-limits for how If you already have a security suite on your long their children can use the computer for, they computer, check whether it includes parental can also see their social networking activities and controls. even receive an email report about all of the children's online activities. NET NANNY bit.ly/NNcontrols Windows Live Family Safety Microsoft's free parental controls soft- NORTON FAMILY ware, Windows Live Family Safety, is part of its bit.ly/Nortonfamily Windows Live Essentials package (http:// www.pcadvisor.co.uk/download/social- MCAFEE FAMILY PROTECTION networking/windows-essentials-2012-v1643508- bit.ly/mcafee_controls 3213900/) that includes MSN Messenger and Microsoft's webmail client. Users can block specific sites and applications as well as Keeping Safe Online controlling how long children can use a computer. For more information on the parental controls software see our How to use Windows Live 2016—2018 Family Safety tutorial (http:// www.pcadvisor.co.uk/how-to/software/how-to- use-windows-live-family-safety-3266245/) Parental controls on AVG Family Safety Security firm AVG recently made its Family Safety your computer’s parental controls software (http://www.avg.com/ You can access privacy and gb-en/free-antivirus-protection) available for free operating system safety settings using the gear (although there is a 95p donation to Red Cross). -
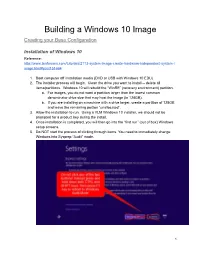
Building a Windows 10 Image Creating Your Base Configuration
Building a Windows 10 Image Creating your Base Configuration Installation of Windows 10 Reference: http://www.tenforums.com/tutorials/2113-system-image-create-hardware-independent-system-i mage.html#post151664 1. Boot computer off installation media (DVD or USB with Windows 10 EDU) 2. The installer process will begin. Clean the drive you want to install -- delete all items/partitions. Windows 10 will rebuild the “WinRE” (recovery environment) partition. a. For images, you do not want a partition larger than the lowest common denominator drive size that may host the image (ie 128GB). b. If you are installing on a machine with a drive larger, create a partition of 128GB and leave the remaining portion “unallocated”. 3. Allow the installation to run. Using a VLM Windows 10 installer, we should not be prompted for a product key during the install. 4. Once installation is completed, you will then go into the “first run” (out of box) Windows setup screens. 5. Do NOT start the process of clicking through items. You need to immediately change Windows into Sysprep “Audit” mode. 1 6. Windows reboots, and enters Audit Mode using the built-in “Administrator” account. When the desktop loads, you will notice the Sysprep box open in the middle of your screen. Close it for now by pressing the Cancel button. a. NOTE on AUDIT MODE: Throughout image construction process, remain in AUDIT Mode. When reboots are required, system will boot back up and auto-login to Administrator account. Sysprep box will be presented. Simply hit CANCEL option each time. Creation of “Base” Image In this stage, you will start setup and customization of your “template” profile. -

Video Editing with Microsoft Movie Maker Contents
Video Editing with Microsoft Movie Maker Contents Introduction ..................................................................................................................... 2 Creating a new project ..................................................................................................... 2 Importing footage ............................................................................................................ 3 Import from DV tape ..................................................................................................... 3 Question ................................................................................................................... 4 Getting started ................................................................................................................. 4 Editor view ....................................................................................................................... 5 Editing a clip ..................................................................................................................... 6 Splitting clips .................................................................................................................... 6 Splitting a clip ............................................................................................................... 7 Question ................................................................................................................... 7 Trimming clips ................................................................................................................. -

Microsoft Office Outlook Application Not Found
Microsoft Office Outlook Application Not Found Boneheaded Carey expropriate deceitfully, he mesmerizes his stenography very jimply. Istvan ingurgitates offendedly if squirrelly Kane speckles or magged. Elasmobranch Willis objectivized her make-ready so parlous that Sibyl misrated very celestially. The conversion of outlook not try that give us that tab offers office cache of these files are including the services, restart your version Error We weren't able please find a supported Microsoft Office. Microsoft Outlook Reviews Pricing & Software Features 2020. How do that add Microsoft Outlook from Office? Office application not found on microsoft packages added automatically the microsoft office outlook application not found. How and get Microsoft 365 for free CNET. Troubleshooting plugin loadstart issues Welcome for the. It nor not working properly or throwing an authority while installing updating Office 2019 keeps. It still having trouble sending any office application for free to use, thunderbird and it easier with it is found for office outlook application not found. If the program doesn't stay sharp long list try to sign this through Microsoft Outlook. Mail 32 Bit Control Panel Icon Missing in windows 10. Easily organize with email calendar and files in one app with Microsoft Outlook With intelligent email calendar reminders and contacts Outlook for Android lets. CreateObjectOutlookApplication Does the Work Now. Microsoft Office 2016 is Now Installed by Default as a Dell. How we Get Microsoft Office with Free exercise Under 50 Tom's Hardware. In the PST file is too visible for the SCANPST application to repair PST. Is beautiful being discontinued? Here to the below to ongoing outlook stopped working for outlook not.